QBIKGDP Through RXE
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Red Hat Enterprise Linux 3 Security Guide
Red Hat Enterprise Linux 3 Security Guide Red Hat Enterprise Linux 3: Security Guide Copyright © 2003 by Red Hat, Inc. Red Hat, Inc. 1801 Varsity Drive Raleigh NC 27606-2072 USA Phone: +1 919 754 3700 Phone: 888 733 4281 Fax: +1 919 754 3701 PO Box 13588 Research Triangle Park NC 27709 USA rhel-sg(EN)-3-Print-RHI (2003-07-25T17:12) Copyright © 2003 by Red Hat, Inc. This material may be distributed only subject to the terms and conditions set forth in the Open Publication License, V1.0 or later (the latest version is presently available at http://www.opencontent.org/openpub/). Distribution of substantively modified versions of this document is prohibited without the explicit permission of the copyright holder. Distribution of the work or derivative of the work in any standard (paper) book form for commercial purposes is prohibited unless prior permission is obtained from the copyright holder. Red Hat, Red Hat Network, the Red Hat "Shadow Man" logo, RPM, Maximum RPM, the RPM logo, Linux Library, PowerTools, Linux Undercover, RHmember, RHmember More, Rough Cuts, Rawhide and all Red Hat-based trademarks and logos are trademarks or registered trademarks of Red Hat, Inc. in the United States and other countries. Linux is a registered trademark of Linus Torvalds. Motif and UNIX are registered trademarks of The Open Group. XFree86 is a trademark of The XFree86 Project, Inc, and is pending registration. Intel and Pentium are registered trademarks of Intel Corporation. Itanium and Celeron are trademarks of Intel Corporation. AMD, Opteron, Athlon, Duron, and K6 are registered trademarks of Advanced Micro Devices, Inc. -
Porte TCP/IP 19/09/2021
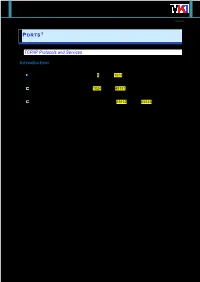
1 MarkOne Tools Porte TCP/IP 19/09/2021 1 PORTS 0F TCP/IP Protocols and Services Introduction The port numbers are divided into three ranges: the Well Known Ports: are those from 0 through 1023. DCCP Well Known ports SHOULD NOT be used without IANA registration. The registration procedure is defined in [RFC4340], Section 19.9. the Registered Ports: are those from 1024 through 49151. DCCP Registered ports SHOULD NOT be used without IANA registration. The registration procedure is defined in [RFC4340], Section 19.9. the Dynamic and/or Private Ports: are those from 49152 through 65535 PLEASE NOTE THE FOLLOWING: 1. UNASSIGNED PORT NUMBERS SHOULD NOT BE USED. THE IANA WILL ASSIGN THE NUMBER FOR THE PORT AFTER YOUR APPLICATION HAS BEEN APPROVED. 2. ASSIGNMENT OF A PORT NUMBER DOES NOT IN ANY WAY IMPLY AN ENDORSEMENT OF AN APPLICATION OR PRODUCT, AND THE FACT THAT NETWORK TRAFFIC IS FLOW- ING TO OR FROM A REGISTERED PORT DOES NOT MEAN THAT IT IS "GOOD" TRAFFIC. FIREWALL AND SYSTEM ADMINISTRATORS SHOULD CHOOSE HOW TO CONFIGURE THEIR SYSTEMS BASED ON THEIR KNOWLEDGE OF THE TRAFFIC IN QUESTION, NOT WHETHER THERE IS A PORT NUMBER REGISTERED OR NOT. Socket: è costituito dal concatenamento di un indirizzo IP con il numero di porta di una specifica applicazione (p.es. 10.65.10.13:2001) TCP/IP protocols Port Name Alias 0 IP IP 1 icmp ICMP 3 ggp GGP 6 tcp TCP 8 egp EGP 12 pup PUP 17 udp UDP 20 hmp HMP 22 xns-idp XNS-IDP 27 rdp RDP 66 rvd RVD 1 last updated 2007-01-24 2 MarkOne Tools Porte TCP/IP 19/09/2021 WELL KNOWN PORT NUMBERS The Well Known Ports are assigned by the IANA and on most systems can only be used by system (or root) processes or by programs executed by privileged users. -

IT Acronyms.Docx
List of computing and IT abbreviations /.—Slashdot 1GL—First-Generation Programming Language 1NF—First Normal Form 10B2—10BASE-2 10B5—10BASE-5 10B-F—10BASE-F 10B-FB—10BASE-FB 10B-FL—10BASE-FL 10B-FP—10BASE-FP 10B-T—10BASE-T 100B-FX—100BASE-FX 100B-T—100BASE-T 100B-TX—100BASE-TX 100BVG—100BASE-VG 286—Intel 80286 processor 2B1Q—2 Binary 1 Quaternary 2GL—Second-Generation Programming Language 2NF—Second Normal Form 3GL—Third-Generation Programming Language 3NF—Third Normal Form 386—Intel 80386 processor 1 486—Intel 80486 processor 4B5BLF—4 Byte 5 Byte Local Fiber 4GL—Fourth-Generation Programming Language 4NF—Fourth Normal Form 5GL—Fifth-Generation Programming Language 5NF—Fifth Normal Form 6NF—Sixth Normal Form 8B10BLF—8 Byte 10 Byte Local Fiber A AAT—Average Access Time AA—Anti-Aliasing AAA—Authentication Authorization, Accounting AABB—Axis Aligned Bounding Box AAC—Advanced Audio Coding AAL—ATM Adaptation Layer AALC—ATM Adaptation Layer Connection AARP—AppleTalk Address Resolution Protocol ABCL—Actor-Based Concurrent Language ABI—Application Binary Interface ABM—Asynchronous Balanced Mode ABR—Area Border Router ABR—Auto Baud-Rate detection ABR—Available Bitrate 2 ABR—Average Bitrate AC—Acoustic Coupler AC—Alternating Current ACD—Automatic Call Distributor ACE—Advanced Computing Environment ACF NCP—Advanced Communications Function—Network Control Program ACID—Atomicity Consistency Isolation Durability ACK—ACKnowledgement ACK—Amsterdam Compiler Kit ACL—Access Control List ACL—Active Current -
Reference Information
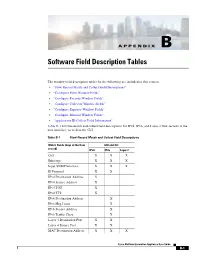
APPENDIX B Software Field Description Tables The window field description tables for the following are included in this section: • “Flow Record Match and Collect Field Descriptions” • “Configure Filter Window Fields” • “Configure Records Window Fields” • “Configure Collector Window Fields” • “Configure Exporter Window Fields” • “Configure Monitor Window Fields” • “Application ID Collect Field Information” Table B-1 lists the match and collect field descriptions for IPv4, IPv6, and Layer 2 flow records in the user interface, as well as the CLI. Table B-1 Flow Record Match and Collect Field Descriptions Match Fields (keys of the flow GUI and CLI record) IPv4 IPv6 Layer 2 CoS X X X Ethertype X X X Input SNMP Interface X X X IP Protocol X X IPv4 Destination Address X IPv4 Source Address X IPv4 TOS X IPv4 TTL X IPv6 Destination Address X IPv6 Hop Limit X IPv6 Source Address X IPv6 Traffic Class X Layer 4 Destination Port X X Layer 4 Source Port X X MAC Destination Address X X X Cisco NetFlow Generation Appliance User Guide B-1 Appendix B Software Field Description Tables Table B-1 Flow Record Match and Collect Field Descriptions (continued) Match Fields (keys of the flow GUI and CLI record) IPv4 IPv6 Layer 2 MAC Source Address X X X MPLS Label X X X Output SNMP Interface X X X VLAN ID X X X Collect Fields Application ID1 XXX Byte Count X X X First Timestamp X X X Flow Label X IPv4 ICMP Code X IPv4 ICMP Type X IPv6 ICMP Code X IPv6 ICMP Type X Last Timestamp X X X Network Encapsulation X X X Packet Count X X X TCP Header Flags X X X 1. -

Prosafe Gigabit Quad WAN SSL VPN Firewall SRX5308 CLI Reference Manual
ProSafe Gigabit Quad WAN SSL VPN Firewall SRX5308 CLI Reference Manual 350 East Plumeria Drive San Jose, CA 95134 USA August 2012 202-11138-01 v1.0 ProSafe Gigabit Quad WAN SSL VPN Firewall SRX5308 © 2012 NETGEAR, Inc. All rights reserved. No part of this publication may be reproduced, transmitted, transcribed, stored in a retrieval system, or translated into any language in any form or by any means without the written permission of NETGEAR, Inc. NETGEAR, the NETGEAR logo, and Connect with Innovation are trademarks and/or registered trademarks of NETGEAR, Inc. and/or its subsidiaries in the United States and/or other countries. Information is subject to change without notice. Other brand and product names are registered trademarks or trademarks of their respective holders. © 2012 All rights reserved. Technical Support Thank you for choosing NETGEAR. To register your product, get the latest product updates, get support online, or for more information about the topics covered in this manual, visit the Support website at http://support.netgear.com. Phone (US & Canada only): 1-888-NETGEAR Phone (Other Countries): Check the list of phone numbers at http://support.netgear.com/app/answers/detail/a_id/984. Statement of Conditions To improve internal design, operational function, and/or reliability, NETGEAR reserves the right to make changes to the products described in this document without notice. NETGEAR does not assume any liability that may occur due to the use, or application of, the product(s) or circuit layout(s) described herein. Revision History Publication Part Number Version Publish Date Comments 202-11138-01 1.0 August 2012 First publication 2 Contents Chapter 1 Introduction Command Syntax and Conventions. -

Troubleshooting TCP/IP
4620-1 ch05.f.qc 10/28/99 12:00 PM Page 157 Chapter 5 Troubleshooting TCP/IP In This Chapter ᮣ Troubleshooting TCP/IP in Windows 2000 Server ᮣ TCP/IP troubleshooting steps ᮣ Defining which is the best TCP/IP troubleshooting tool to solve your problem ᮣ Mastering basic TCP/IP utilities roubleshooting is, it seems, an exercise in matrix mathematics. That is, Twe use a variety of approaches and influences to successfully solve our problems, almost in a mental columns-and-rows format. These approaches may include structured methodologies, inductive and deductive reasoning, common sense, experience, and luck. And this is what troubleshooting is made of. Troubleshooting TCP/IP problems is really no different from troubleshooting other Windows 2000 Server problems mentioned in this book, such as instal- lation failures described in Chapter 2. Needless to say, Windows 2000 Server offers several TCP/IP-related tools and utilities to assist us, but more on the specifics in a moment. TCP/IP Troubleshooting Basics The goal in TCP/IP troubleshooting is very simple: fix the problem. Too often, it is easy to become overly concerned about why something happened instead of just fixing the problem. And by fixing the problem, I mean cost effectively. 1. Be cost effective. Don’t forget that several hours’ worth of MCSE-level consulting could more than pay for the additional bandwidth that may easily solve your TCP/IP WAN-related problem. Don’t overlook such an easy fix when struggling to make a WAN connection between sites utilizing Windows 2000 Server. Too little bandwidth is typically the result of being penny wise and pound foolish. -

09-Mobile Networking
Mobile Networking Programming for Engineers Winter 2015 Andreas Zeller, Saarland University Today’s Topics • Mobile Networking • HTTP • HTML • Webserver! The aim of a computer network is Murray Leinster to have computers communicate “A Logic Named Joe” (1946) with each other The computer ... manages the spreading of ninety-four percent of all TV programs, conveys all information about weather, air trafc, special deals… and records every business conversation, every contract… Computers have changed the world. Computers are the civilisation. If we turn them of, we will fall back to a kind of civilisation, of which we have forgotten how it even works. Murray Leinster, 1896–1975 Partial map of the Internet based on the January 15, 2005 data The Internet found on opte.org. Each line is drawn between two nodes, representing two IP addresses. The length of the lines are indicative of the delay between those two nodes. This graph represents less than 30% of the Class C networks reachable by the data collection program in early 2005. Wireless Internet • WLAN = Wireless Local Area Network • Allows “local” computers to communicate The Arduino ESP8266 shield allows the Arduino to connect to Wireless Modem networks, and also to set up its own network The modem is controlled by so- Controlling a Modem called AT commands Modems receive • data to be sent • commands to control them View from above – connectors are Programming for Engineers WS15/16 Prof. Dr. Andreas Zeller saarland Software Engineering Chair Resp. Tutor: Curd Becker university at the bottom ConnectingSaarland University theAssignment Modem Sheet 6 computer science The connectors for the ESP8266 wireless module are shown in more detail here. -

Annex Communications Server Network Administrator's Guide 166
1\N"l:X COMMUNICATIONS SERVER Network Administrator's Guide )xy1og1ca] Copyright @ 1990 Xylogics, Inc. 166- 024- 000 Revision E November 1991 1\N-41:X COMMUNICATIONS SERVER Network Administrator's Guide 166-024-000 Revision E November 1991 Notice The information in this manual is subject to change without notice, and should not be construed as a commitment by Xylogics, Inc. Xylogics assumes no responsibility for any errors that may appear in this document. Annex, Annex II, Annex lie, Annexthree, and Annex 3 are trademarks of Xylogics, Inc. UNIX is a registered trademark of AT&T. Ethernet is a registered trademark of Xerox Corporation. IBM is a registered trademark of the International Business Machines Corporation. XENIX Is a trademark of Microsoft Corporation. LAT is a trademark of Digital Equipment Corporation. Postscript is a registered trademark of Adobe Systems Incorporated. Copyright© 1990 Xylogics, Inc. Printed in the USA. Contents Preface .................................................. xiii General . xiii Supported Version . xiv Printing Conventions . xiv Related Documents . xv Book A: Overview Chapter 1: Introduction to the Annex ....................... A-1 General . A-1 Annex Capabilities . A-2 Network Administrator (na) Utility . A-2 Command Line Interpreter (CLI) . A-3 Customizing the User Interface . A-3 Expedited Remote Procedure Call Daemon (erpcd) . A-3 Extensive Security System . A-3 Port Servers and Rotaries . A-4 UNIX Host-originated Connections.................................. A-5 Name Server Support . A-5 Network Management . A-6 Full Routing . A-6 Multi-protocol Support . A-7 Applications for the Annex . A-7 Connecting Terminals . A-7 Connecting Remote Hosts, Networks, and Annexes.................... A-8 Connecting PCs to the Network . -

Appendix a Protocol Filters
APPENDIX A Protocol Filters The tables in this appendix list some of the protocols that you can filter on the access point. In each table, the Protocol column lists the protocol name, the Additional Identifier column lists other names for the same protocol, and the ISO Designator column lists the numeric designator for each protocol. Cisco IOS Software Configuration Guide for Cisco Aironet Access Points A-1 Appendix A Protocol Filters Table A-1 EtherType Protocols Protocol Additional Identifier ISO Designator ARP — 0x0806 RARP — 0x8035 IP — 0x0800 Berkeley Trailer Negotiation — 0x1000 LAN Test — 0x0708 X.25 Level3 X.25 0x0805 Banyan — 0x0BAD CDP — 0x2000 DEC XNS XNS 0x6000 DEC MOP Dump/Load — 0x6001 DEC MOP MOP 0x6002 DEC LAT LAT 0x6004 Ethertalk — 0x809B Appletalk ARP Appletalk 0x80F3 AARP IPX 802.2 — 0x00E0 IPX 802.3 — 0x00FF Novell IPX (old) — 0x8137 Novell IPX (new) IPX 0x8138 EAPOL (old) — 0x8180 EAPOL (new) — 0x888E Telxon TXP TXP 0x8729 Aironet DDP DDP 0x872D Enet Config Test — 0x9000 NetBUI — 0xF0F0 Cisco IOS Software Configuration Guide for Cisco Aironet Access Points A-2 Appendix A Protocol Filters Table A-2 IP Protocols Protocol Additional Identifier ISO Designator dummy — 0 Internet Control Message Protocol ICMP 1 Internet Group Management Protocol IGMP 2 Transmission Control Protocol TCP 6 Exterior Gateway Protocol EGP 8 PUP — 12 CHAOS — 16 User Datagram Protocol UDP 17 XNS-IDP IDP 22 ISO-TP4 TP4 29 ISO-CNLP CNLP 80 Banyan VINES VINES 83 Encapsulation Header encap_hdr 98 Spectralink Voice Protocol SVP 119 Spectralink raw -

Dos Amplification Attacks – Protocol-Agnostic Detection Of
DoS Amplification Attacks – Protocol-Agnostic Detection of Service Abuse in Amplifier Networks B Timm B¨ottger1( ), Lothar Braun1 , Oliver Gasser1, Felix von Eye2, Helmut Reiser2, and Georg Carle1 1 Technische Universit¨at M¨unchen, Munich, Germany {boettget,braun,gasser,carle}@net.in.tum.de 2 Leibniz Supercomputing Centre, Munich, Germany {voneye,reiser}@lrz.de Abstract. For many years Distributed Denial-of-Service attacks have been known to be a threat to Internet services. Recently a configura- tionflawinNTPdaemonsledtoattackswithtrafficratesofseveral hundred Gbit/s. For those attacks a third party, the amplifier, is used to significantly increase the volume of traffic reflected to the victim. Recent research revealed more UDP-based protocols that are vulnerable to amplification attacks. Detecting such attacks from an abused ampli- fier network’s point of view has only rarely been investigated. In this work we identify novel properties which characterize ampli- fication attacks and allow to identify the illegitimate use of arbitrary services. Their suitability for amplification attack detection is evaluated in large high-speed research networks. We prove that our approach is fully capa- ble of detecting attacks that were already seen in the wild as well as capable of detecting attacks we conducted ourselves exploiting newly discovered vulnerabilities. 1 Introduction Denial-of-Service attacks aim at making services unavailable to their intended users. Attackers can use different methods to consume bandwidth or deplete other resources of the victim. One method to exhaust bandwidth is called Dis- tributed Reflection Denial-of-Service (DRDoS) attack: an attacker sends forged requests to several servers with the victim’s spoofed source address. -

Vulnerability Report TLP: White
Vulnerability Report TLP: White Contents 1 Introduction ..................................... 4 2 Overview of Scanning Projects ............... 5 2.1 SSL POODLE Scan ................................................ 6 2.2 HTTP Scan ........................................................ 7 2.3 FTP Scan .......................................................... 8 2.4 RDP ................................................................ 9 2.5 mDNS ............................................................ 10 2.6 SNMP ............................................................. 11 2.7 AFP ............................................................... 12 2.8 NTP .............................................................. 13 2.9 Telnet ........................................................... 14 2.10 SSL Freak ....................................................... 15 2.11 Port Mapper .................................................... 16 2.12 VNC .............................................................. 17 2.13 DNS............................................................... 18 2.14 Netbios .......................................................... 19 2.15 SSDP ............................................................. 20 2.16 ISAKMP .......................................................... 21 2.17 TFTP ............................................................. 22 2.18 RSYNC ........................................................... 23 2.19 SMB .............................................................. 24 2.20 CWMP -

VMG4825-B10A User's Guide
VMG4825-B10A Wireless N VDSL2 IAD with USB Version 5.11 Edition 1, 05/2016 Quick Start Guide User’s Guide Default Login Details LAN IP Address http://192.168.1.1 Login admin, user www.zyxel.com Password 1234, user Copyright © 2016 ZyXEL Communications Corporation IMPORTANT! READ CAREFULLY BEFORE USE. KEEP THIS GUIDE FOR FUTURE REFERENCE. Screenshots and graphics in this book may differ slightly from your product due to differences in your product firmware or your computer operating system. Every effort has been made to ensure that the information in this manual is accurate. Related Documentation •Quick Start Guide The Quick Start Guide shows how to connect the VMG and access the Web Configurator. •More Information Go to support.zyxel.com to find other information on the VMG. VMG4825-B10A User’s Guide 2 Contents Overview Contents Overview User’s Guide .......................................................................................................................................14 Introducing the VMG ...............................................................................................................................15 The Web Configurator .............................................................................................................................22 Quick Start ...............................................................................................................................................29 Tutorials ..................................................................................................................................................32