Summary of UNIX Commands- Version 3.2
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

GNU/Linux AI & Alife HOWTO
GNU/Linux AI & Alife HOWTO GNU/Linux AI & Alife HOWTO Table of Contents GNU/Linux AI & Alife HOWTO......................................................................................................................1 by John Eikenberry..................................................................................................................................1 1. Introduction..........................................................................................................................................1 2. Symbolic Systems (GOFAI)................................................................................................................1 3. Connectionism.....................................................................................................................................1 4. Evolutionary Computing......................................................................................................................1 5. Alife & Complex Systems...................................................................................................................1 6. Agents & Robotics...............................................................................................................................1 7. Statistical & Machine Learning...........................................................................................................2 8. Missing & Dead...................................................................................................................................2 1. Introduction.........................................................................................................................................2 -

Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe
Weblint: Just Another Perl Hack Neil Bowers1 Canon Research Centre Europe Abstract Weblint is a utility for checking the syntax and style of HTML pages. It was inspired by lint [15], which performs a similar function for C and C++ programmers. Weblint does not aspire to be a strict SGML validator, but to provide helpful comments for humans. The importance of quality assurance for web sites is introduced, and one particular area, validation of HTML, is described in more detail. The bulk of the paper is devoted to weblint: what it is, how it is used, and the design and implementation of the current development version. 1. Introduction The conclusion opens with a summary of the information and opinions given in this paper. A Web sites are becoming an increasingly critical part of selection of the lessons learned over the last four years how many companies do business. For many companies is given, followed by plans for the future, and related web sites are their business. It is therefore critical that ideas. owners of web sites perform regular testing and analysis, to ensure quality of service. 2. Web Site Quality Assurance There are many different checks and analyses which The following are some of the questions you should be you can run on a site. For example, how usable is your asking yourself if you have a web presence. I have site when accessed via a modem? An incomplete list of limited the list to those points which are relevant to similar analyses are given at the start of Section 2. -

PANTONE® Colorwebtm 1.0 COLORWEB USER MANUAL
User Manual PANTONE® ColorWebTM 1.0 COLORWEB USER MANUAL Copyright Pantone, Inc., 1996. All rights reserved. PANTONE® Computer Video simulations used in this product may not match PANTONE®-identified solid color standards. Use current PANTONE Color Reference Manuals for accurate color. All trademarks noted herein are either the property of Pantone, Inc. or their respective companies. PANTONE® ColorWeb™, ColorWeb™, PANTONE Internet Color System™, PANTONE® ColorDrive®, PANTONE Hexachrome™† and Hexachrome™ are trademarks of Pantone, Inc. Macintosh, Power Macintosh, System 7.xx, Macintosh Drag and Drop, Apple ColorSync and Apple Script are registered trademarks of Apple® Computer, Inc. Adobe Photoshop™ and PageMill™ are trademarks of Adobe Systems Incorporated. Claris Home Page is a trademark of Claris Corporation. Netscape Navigator™ Gold is a trademark of Netscape Communications Corporation. HoTMetaL™ is a trademark of SoftQuad Inc. All other products are trademarks or registered trademarks of their respective owners. † Six-color Process System Patent Pending - Pantone, Inc.. PANTONE ColorWeb Team: Mark Astmann, Al DiBernardo, Ithran Einhorn, Andrew Hatkoff, Richard Herbert, Rosemary Morretta, Stuart Naftel, Diane O’Brien, Ben Sanders, Linda Schulte, Ira Simon and Annmarie Williams. 1 COLORWEB™ USER MANUAL WELCOME Thank you for purchasing PANTONE® ColorWeb™. ColorWeb™ contains all of the resources nec- essary to ensure accurate, cross-platform, non-dithered and non-substituting colors when used in the creation of Web pages. ColorWeb works with any Web authoring program and makes it easy to choose colors for use within the design of Web pages. By using colors from the PANTONE Internet Color System™ (PICS) color palette, Web authors can be sure their page designs have rich, crisp, solid colors, no matter which computer platform these pages are created on or viewed. -

CS101 Lecture 9
How do you copy/move/rename/remove files? How do you create a directory ? What is redirection and piping? Readings: See CCSO’s Unix pages and 9-2 cp option file1 file2 First Version cp file1 file2 file3 … dirname Second Version This is one version of the cp command. file2 is created and the contents of file1 are copied into file2. If file2 already exits, it This version copies the files file1, file2, file3,… into the directory will be replaced with a new one. dirname. where option is -i Protects you from overwriting an existing file by asking you for a yes or no before it copies a file with an existing name. -r Can be used to copy directories and all their contents into a new directory 9-3 9-4 cs101 jsmith cs101 jsmith pwd data data mp1 pwd mp1 {FILES: mp1_data.m, mp1.m } {FILES: mp1_data.m, mp1.m } Copy the file named mp1_data.m from the cs101/data Copy the file named mp1_data.m from the cs101/data directory into the pwd. directory into the mp1 directory. > cp ~cs101/data/mp1_data.m . > cp ~cs101/data/mp1_data.m mp1 The (.) dot means “here”, that is, your pwd. 9-5 The (.) dot means “here”, that is, your pwd. 9-6 Example: To create a new directory named “temp” and to copy mv option file1 file2 First Version the contents of an existing directory named mp1 into temp, This is one version of the mv command. file1 is renamed file2. where option is -i Protects you from overwriting an existing file by asking you > cp -r mp1 temp for a yes or no before it copies a file with an existing name. -

Formal Aspects of Mobile Code Security
FORMAL ASPECTS OF MOBILE CODE SECURITY RICHARD DREWS DEAN ADISSERTATION PRESENTED TO THE FACULTY OF PRINCETON UNIVERSITY IN CANDIDACY FOR THE DEGREE OF DOCTOR OF PHILOSOPHY RECOMMENDED FOR ACCEPTANCE BY THE DEPARTMENT OF COMPUTER SCIENCE JANUARY 1999 c Copyright by Richard Drews Dean, 1998. All Rights Reserved Abstract We believe that formal methods of all kinds are critical to mobile code security, as one route to gaining the assurance level necessary for running potentially hos- tile code on a routine basis. We begin by examining Java, and understanding the weaknesses in its architecture, on both design and implementation levels. Iden- tifying dynamic linking as a key problem, we produce a formal model of linking, and prove desirable properties about our model. This investigation leads to a deep understanding of the underlying problem. Finally, we turn our attention to crypto- graphic hash functions, and their analysis with binary decision diagrams (BDDs). We show that three commonly used hash functions (MD4, MD5, and SHA-1) do not offer ideal strength against second preimages. The ability of a cryptographic hash function to resist the finding of second preimages is critical for its use in digi- tal signature schemes: a second preimage enables the forgery of digital signatures, which would undermine confidence in digitally signed mobile code. Our results show that modern theorem provers and BDD-based reasoning tools are effective for reasoning about some of the key problems facing mobile code security today. iii Acknowledgments My advisor, Andrew Appel, offered sure guidance through what turned out to be an exceptionally smooth journey through graduate school. -

Lecture 7 Network Management and Debugging
SYSTEM ADMINISTRATION MTAT.08.021 LECTURE 7 NETWORK MANAGEMENT AND DEBUGGING Prepared By: Amnir Hadachi and Artjom Lind University of Tartu, Institute of Computer Science [email protected] / [email protected] 1 LECTURE 7: NETWORK MGT AND DEBUGGING OUTLINE 1.Intro 2.Network Troubleshooting 3.Ping 4.SmokePing 5.Trace route 6.Network statistics 7.Inspection of live interface activity 8.Packet sniffers 9.Network management protocols 10.Network mapper 2 1. INTRO 3 LECTURE 7: NETWORK MGT AND DEBUGGING INTRO QUOTE: Networks has tendency to increase the number of interdependencies among machine; therefore, they tend to magnify problems. • Network management tasks: ✴ Fault detection for networks, gateways, and critical servers ✴ Schemes for notifying an administrator of problems ✴ General network monitoring, to balance load and plan expansion ✴ Documentation and visualization of the network ✴ Administration of network devices from a central site 4 LECTURE 7: NETWORK MGT AND DEBUGGING INTRO Network Size 160 120 80 40 Management Procedures 0 AUTOMATION ILLUSTRATION OF NETWORK GROWTH VS MGT PROCEDURES AUTOMATION 5 LECTURE 7: NETWORK MGT AND DEBUGGING INTRO • Network: • Subnets + Routers / switches Time to consider • Automating mgt tasks: • shell scripting source: http://www.eventhelix.com/RealtimeMantra/Networking/ip_routing.htm#.VvjkA2MQhIY • network mgt station 6 2. NETWORK TROUBLES HOOTING 7 LECTURE 7: NETWORK MGT AND DEBUGGING NETWORK TROUBLESHOOTING • Many tools are available for debugging • Debugging: • Low-level (e.g. TCP/IP layer) • high-level (e.g. DNS, NFS, and HTTP) • This section progress: ping trace route GENERAL ESSENTIAL TROUBLESHOOTING netstat TOOLS STRATEGY nmap tcpdump … 8 LECTURE 7: NETWORK MGT AND DEBUGGING NETWORK TROUBLESHOOTING • Before action, principle to consider: ✴ Make one change at a time ✴ Document the situation as it was before you got involved. -
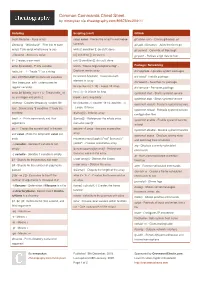
Common Commands Cheat Sheet by Mmorykan Via Cheatography.Com/89673/Cs/20411
Common Commands Cheat Sheet by mmorykan via cheatography.com/89673/cs/20411/ Scripting Scripting (cont) GitHub bash filename - Runs script sleep value - Forces the script to wait value git clone <url > - Clones gitkeeper url Shebang - "# !bi n/b ash " - First line of bash seconds git add <fil ena me> - Adds the file to git script. Tells script what binary to use while [[ condition ]]; do stuff; done git commit - Commits all files to git ./file name - Also runs script if [[ condition ]]; do stuff; fi git push - Pushes all git files to host # - Creates a comment until [[ condition ]]; do stuff; done echo ${varia ble} - Prints variable words=" h ouse dogs telephone dog" - Package / Networking hello_int = 1 - Treats "1 " as a string Declares words array dnf upgrade - Updates system packages Use UPPERC ASE for constant variables for word in ${words} - traverses each dnf install - Installs package element in array Use lowerc ase _wi th_ und ers cores for dnf search - Searches for package for counter in {1..10} - Loops 10 times regular variables dnf remove - Removes package for ((;;)) - Is infinite for loop echo $(( ${hello _int} + 1 )) - Treats hello_int systemctl start - Starts systemd service as an integer and prints 2 break - exits loop body systemctl stop - Stops systemd service mktemp - Creates temporary random file for ((count er=1; counter -le 10; counter ++)) systemctl restart - Restarts systemd service test - Denoted by "[[ condition ]]" tests the - Loops 10 times systemctl reload - Reloads systemd service condition -

Bringing GNU Emacs to Native Code
Bringing GNU Emacs to Native Code Andrea Corallo Luca Nassi Nicola Manca [email protected] [email protected] [email protected] CNR-SPIN Genoa, Italy ABSTRACT such a long-standing project. Although this makes it didactic, some Emacs Lisp (Elisp) is the Lisp dialect used by the Emacs text editor limitations prevent the current implementation of Emacs Lisp to family. GNU Emacs can currently execute Elisp code either inter- be appealing for broader use. In this context, performance issues preted or byte-interpreted after it has been compiled to byte-code. represent the main bottleneck, which can be broken down in three In this work we discuss the implementation of an optimizing com- main sub-problems: piler approach for Elisp targeting native code. The native compiler • lack of true multi-threading support, employs the byte-compiler’s internal representation as input and • garbage collection speed, exploits libgccjit to achieve code generation using the GNU Com- • code execution speed. piler Collection (GCC) infrastructure. Generated executables are From now on we will focus on the last of these issues, which con- stored as binary files and can be loaded and unloaded dynamically. stitutes the topic of this work. Most of the functionality of the compiler is written in Elisp itself, The current implementation traditionally approaches the prob- including several optimization passes, paired with a C back-end lem of code execution speed in two ways: to interface with the GNU Emacs core and libgccjit. Though still a work in progress, our implementation is able to bootstrap a func- • Implementing a large number of performance-sensitive prim- tional Emacs and compile all lexically scoped Elisp files, including itive functions (also known as subr) in C. -

Unix/Linux Command Reference
Unix/Linux Command Reference .com File Commands System Info ls – directory listing date – show the current date and time ls -al – formatted listing with hidden files cal – show this month's calendar cd dir - change directory to dir uptime – show current uptime cd – change to home w – display who is online pwd – show current directory whoami – who you are logged in as mkdir dir – create a directory dir finger user – display information about user rm file – delete file uname -a – show kernel information rm -r dir – delete directory dir cat /proc/cpuinfo – cpu information rm -f file – force remove file cat /proc/meminfo – memory information rm -rf dir – force remove directory dir * man command – show the manual for command cp file1 file2 – copy file1 to file2 df – show disk usage cp -r dir1 dir2 – copy dir1 to dir2; create dir2 if it du – show directory space usage doesn't exist free – show memory and swap usage mv file1 file2 – rename or move file1 to file2 whereis app – show possible locations of app if file2 is an existing directory, moves file1 into which app – show which app will be run by default directory file2 ln -s file link – create symbolic link link to file Compression touch file – create or update file tar cf file.tar files – create a tar named cat > file – places standard input into file file.tar containing files more file – output the contents of file tar xf file.tar – extract the files from file.tar head file – output the first 10 lines of file tar czf file.tar.gz files – create a tar with tail file – output the last 10 lines -
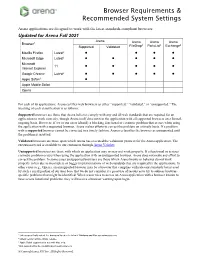
Browser Requirements & Recommended
Browser Requirements & Recommended System Settings Arena applications are designed to work with the latest standards-compliant browsers. Updated for Arena Fall 2021 Arena 1 Arena Arena Arena Browser 4 4 4 Supported Validated FileDrop PartsList Exchange Mozilla Firefox Latest2 l l l l Microsoft Edge Latest2 l l l l l Microsoft 11 l l l l l Internet Explorer Google Chrome Latest2 l l l l l Apple Safari3 l Apple Mobile Safari Opera For each of its applications, Arena certifies web browsers as either “supported,” “validated,” or “unsupported.” The meaning of each classification is as follows: Supported browsers are those that Arena believes comply with any and all web standards that are required for an application to work correctly, though Arena itself does not test the application with all supported browsers on a formal, ongoing basis. However, if we or our users identify a blocking functional or cosmetic problem that occurs when using the application with a supported browser, Arena makes efforts to correct the problem on a timely basis. If a problem with a supported browser cannot be corrected in a timely fashion, Arena reclassifies the browser as unsupported until the problem is resolved. Validated browsers are those upon which Arena has executed the validation protocol for the Arena application. The execution record is available to our customers through Arena Validate. Unsupported browsers are those with which an application may or may not work properly. If a functional or serious cosmetic problem occurs when using the application with an unsupported browser, Arena does not make any effort to correct the problem. -

GNU Emacs Manual
GNU Emacs Manual GNU Emacs Manual Sixteenth Edition, Updated for Emacs Version 22.1. Richard Stallman This is the Sixteenth edition of the GNU Emacs Manual, updated for Emacs version 22.1. Copyright c 1985, 1986, 1987, 1993, 1994, 1995, 1996, 1997, 1998, 1999, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with the Invariant Sections being \The GNU Manifesto," \Distribution" and \GNU GENERAL PUBLIC LICENSE," with the Front-Cover texts being \A GNU Manual," and with the Back-Cover Texts as in (a) below. A copy of the license is included in the section entitled \GNU Free Documentation License." (a) The FSF's Back-Cover Text is: \You have freedom to copy and modify this GNU Manual, like GNU software. Copies published by the Free Software Foundation raise funds for GNU development." Published by the Free Software Foundation 51 Franklin Street, Fifth Floor Boston, MA 02110-1301 USA ISBN 1-882114-86-8 Cover art by Etienne Suvasa. i Short Contents Preface ::::::::::::::::::::::::::::::::::::::::::::::::: 1 Distribution ::::::::::::::::::::::::::::::::::::::::::::: 2 Introduction ::::::::::::::::::::::::::::::::::::::::::::: 5 1 The Organization of the Screen :::::::::::::::::::::::::: 6 2 Characters, Keys and Commands ::::::::::::::::::::::: 11 3 Entering and Exiting Emacs ::::::::::::::::::::::::::: 15 4 Basic Editing -

University of the Philippines Manila College of Arts and Sciences Department of Physical Sciences and Mathematics
UNIVERSITY OF THE PHILIPPINES MANILA COLLEGE OF ARTS AND SCIENCES DEPARTMENT OF PHYSICAL SCIENCES AND MATHEMATICS Health Insurance Corporation Customer Relationship Management Tool (HICorpCRM) A special problem in partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science Submitted by: Paul John N. Macaraeg June 2015 Permission is given for the following people to have access to this SP: Available to the general public Yes Available only after consultation with author/ SP adviser No Available only to those bound by confidentiality agreement No ACCEPTANCE SHEET The Special Problem entitled “Health Insurance Corporation Customer Relationship Management Tool (HICorpCRM)” prepared and submitted by Paul John N. Macaraeg in partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science has been examined and is recommended or acceptance. Ma. Sheila A. Magboo, M.Sc. Adviser EXAMINERS: Approved Disapproved 1. Gregorio B. Baes, Ph.D. 2. Avegail D. Carpio, M.Sc. 3. Perlita E. Gasmen, M.Sc. 4. Richar Bryann L. Chua, M.Sc. 5. Vincent Peter C. Magboo, M.D., M.Sc. 6. Bernie B. Terrado, M.Sc. Accepted and approved as partial fulfillment of the requirements for the degree of Bachelor of Science in Computer Science. Ma. Sheila A. Magboo, M.Sc. Marcelina B. Lirazan, Ph.D. Unit Head Chair Mathematical and Computing Sciences Unit Department of Physical Sciences Department of Physical Sciences and Mathematics and Mathematics Alex C. Gonzaga, Ph.D., Dr.Eng. Dean College of Arts and Sciences iii Abstract The health insurance industry is saturated by big companies competing for market share.