Building Dependable Systems: the Openvms Approach
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Validated Products List, 1995 No. 3: Programming Languages, Database
NISTIR 5693 (Supersedes NISTIR 5629) VALIDATED PRODUCTS LIST Volume 1 1995 No. 3 Programming Languages Database Language SQL Graphics POSIX Computer Security Judy B. Kailey Product Data - IGES Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 July 1995 QC 100 NIST .056 NO. 5693 1995 NISTIR 5693 (Supersedes NISTIR 5629) VALIDATED PRODUCTS LIST Volume 1 1995 No. 3 Programming Languages Database Language SQL Graphics POSIX Computer Security Judy B. Kailey Product Data - IGES Editor U.S. DEPARTMENT OF COMMERCE Technology Administration National Institute of Standards and Technology Computer Systems Laboratory Software Standards Validation Group Gaithersburg, MD 20899 July 1995 (Supersedes April 1995 issue) U.S. DEPARTMENT OF COMMERCE Ronald H. Brown, Secretary TECHNOLOGY ADMINISTRATION Mary L. Good, Under Secretary for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Arati Prabhakar, Director FOREWORD The Validated Products List (VPL) identifies information technology products that have been tested for conformance to Federal Information Processing Standards (FIPS) in accordance with Computer Systems Laboratory (CSL) conformance testing procedures, and have a current validation certificate or registered test report. The VPL also contains information about the organizations, test methods and procedures that support the validation programs for the FIPS identified in this document. The VPL includes computer language processors for programming languages COBOL, Fortran, Ada, Pascal, C, M[UMPS], and database language SQL; computer graphic implementations for GKS, COM, PHIGS, and Raster Graphics; operating system implementations for POSIX; Open Systems Interconnection implementations; and computer security implementations for DES, MAC and Key Management. -

1992 Cern School of Computing
ORGANISATION EUROPEENNE POUR LA RECHERCHE NUCLEAIRE CERN EUROPEAN ORGANIZATION FOR NUCLEAR RESEARCH 1992 CERN SCHOOL OF COMPUTING Scuola Superiore G. Reiss Romoli, L'Aquila, Italy 30 August-12 September 1992 PROCEEDINGS Editor: C. Verkerk GENEVA 1993 © Copyright CERN, Genève, 1993 Propriété littéraire et scientifique réservée Literary and scientific copyrights reserved in pour tous les paya < 11» inonde. Ce document ne all countries of the world. This report, or peut être reproduit ou traduit en tout ou en any part of it. may not be reprinted or trans partie sans l'autorisation écrite du Directeur lated without written permission ol the copy général du CERN, titulaire du droit d'auteur. right holder, the Director-General of CERN. Dans les cas appropriés, et s'il s'agit d'utiliser However, permission will be freely granted for le document à des fins non commerciales, cette appropriate non-commercial use. autorisation sera volontiers accordée. If any patentable invention or registrable Le CERN ne revendique pas la propriété des design is described in the report. CERN makes inventions brevetables et dessins ou modèles no claim to property rights in it but offers i( susceptibles de dépôt qui pourraient être for the free use of research institutions, man décrits dans le présent document ; ceux-ci peu ufacturers and others. CERN, however, may vent être librement utilisés par les instituts de oppose any attempt by a user to claim any recherche, les industriels et autres intéressés. proprietary or patent rights in such inventions Cependant, le CERN se réserve le droit de or designs as may be described in the present s'opposer à toute revendication qu'un usager document. -

I Txso C~T Dc~ 5 SPD / LETTER FC~R
i DIGITAL Digital Equipm~t3t Corporation SOFTW~►,RE Digital Drive SILL OF MATERIALS Westminster, Massachusetts 01473-0471 Option Number Option Title Date Page ~ QA-10 OAA-W55.6 ~rAX FORTF~? V5.6 UPD TK5 0 28-Feb-91 1 of 1 ~TY PICK LOCATION PART NLJL~ER PART DESCRIPTION .~_ -.. 1 *FS* 36-28231-07 TRE~I~ZA~L S~~RCODE LABEL 1 *FS* 99-08545-02 BOOKT~IRAP 1 t UR) AQ-FP 8 6N-BN ~irAX FORTP~AN V5.6 BIN TK5 0 1 ~ DP ~ AV-PF4FA-TK SUP REPLACEMENT LETTER 1 EN-01044-07 SFT'WR PERFOF~!~ANCE REPORT FORM 1 ***** NS ~~~ QA-10 OAA-WZ 5.6 ~irAX FORTF~AN V5.6 UPD DOC 1 *FS* 36-28231-0? THEF~!zA,L P.~ARCODE LABEL 1 *FS* 99-08545-02 BOOKT~IRAP 1 (UR} AE-JF8?L-TE ~irAX FORTP►AN V5.6 SPD 2 5.16.3 6 1 - t~~ AE-LT36H-TE ~irAX FORTP;AN SSA 2 5.16.3 6 -A 1 SDP ) AE -1~tA,5 OA- TK SOFTWARE W TY ADDENDUM 1 tUR~ AV-N672V-TE V'AX FORTP►AN V5.6 PAD FIRS T 1 EN-02512-05 C~3LANGE OF ADDRESS CARD ilk.~ r~~i~li~ilpirfi~~ra~~reis~-~-~~~------~----~~~~ t~ii~~l~+~r~~~-~~~--~--~.r~.~ i Txso c~t Dc~ 5 SPD / LETTER FC~R : AV-PF4FA- TK October, 1990 d 9 Dear Service Customer, Enclosed is a software product update/maintenance release supplied as part of your software maintenance agreement. As part of its planned License Management Zbols program, Digital has initiated replacement of all Service Update PAKs (SUPs) for licensed software product with License Product Authorization Keys (PAKs). -

Openvms DCL Dictionary: N–Z
OpenVMS DCL Dictionary: N–Z Order Number: AA–PV5LG–TK April 2001 This manual provides detailed reference information and examples for Compaq OpenVMS DCL commands and lexical functions. Revision/Update Information: This manual supersedes the OpenVMS DCL Dictionary, Version 7.2. Software Version: OpenVMS Alpha Version 7.3 OpenVMS VAX Version 7.3 Compaq Computer Corporation Houston, Texas © 2001 Compaq Computer Corporation Compaq, VAX, VMS, and the Compaq logo Registered in U.S. Patent and Trademark Office. OpenVMS and Tru64 are trademarks of Compaq Information Technologies Group, L.P in the United States and other countries. Microsoft, MS-DOS, Visual C++, Windows, and Windows NT are trademarks of Microsoft Corporation in the United States and other countries. Intel, Intel Inside, and Pentium are trademarks of Intel Corporation in the United States and other countries. Motif, OSF/1, and UNIX are trademarks of The Open Group in the United States and other countries. All other product names mentioned herein may be trademarks of their respective companies. Confidential computer software. Valid license from Compaq required for possession, use, or copying. Consistent with FAR 12.211 and 12.212, Commercial Computer Software, Computer Software Documentation, and Technical Data for Commercial Items are licensed to the U.S. Government under vendor’s standard commercial license. Compaq shall not be liable for technical or editorial errors or omissions contained herein. The information in this document is provided "as is" without warranty of any kind and is subject to change without notice. The warranties for Compaq products are set forth in the express limited warranty statements accompanying such products. -

DB2SPI B.03.02 User's Guide
HP OpenView Tiering Matrix For HP and Partner use Page 1 of 5 Updated: 18 August 2006 (For OV Performance Agent, OV Operations Agent, SPIs, OVIS, OVAI, GlancePlus and GlancePlus Pak) Usage Notes 1. This matrix is a tool for identifying what tier a system is in. NOT ALL of the listed products are supported on all systems in this matrix. Please read this introduction carefully and also look at the footnotes on each page provided for special cases. 2. Single-user Systems (Unix): For OV Operations Agents, Performance Agents and SPIs a workstation used as a single-user system is classified as a Tier 0 system. 3. Desktop Systems (Windows, Linux, Netware): Professional Desktop License is for use on a single-user Intel-based PC that is running Windows NT Workstation, Windows 2000 Professional, Windows XP Professional, RedHat Linux or Novell NetWare. 4. The tiering below is valid for all systems running AIX, HP-UX, Tru64 UNIX, Digital Unix, Linux, Sun Solaris, MS Windows and Novell NetWare. All other systems are tiered / priced using separate product numbers as follows: o OV Multi-vendor Agent - B7442AA, o OV Multi-vendor Operations Agent - B7443AA, o OV Multi-vendor Performance Agent - B7444AA. 5. Multiple Partitions (Virtual Servers): a. UNIX-based If an OV Agent is being ordered for an UNIX-based system which has multiple partitions / domains (virtual systems) a ‘password request form’ specifying the number of ‘additional’ partitions/domains has to be completed and sent to the password delivery center. There is one license required based upon the tiering of the hosting system and (n-1) free additional Tier 1 licenses for the additional partitions/domains. -

Binary Translation 1 Abstract Binary Translation Is a Technique Used To
Binary Translation 1 Abstract Binary translation is a technique used to change an executable program for one computer architecture and operating system into an executable program for a different computer architecture and operating system. Two binary translators are among the migration tools available for Alpha AXP computers: VEST translates OpenVMS VAX binary images to OpenVMS AXP images; mx translates ULTRIX MIPS images to DEC OSF/1 AXP images. In both cases, translated code usually runs on Alpha AXP computers as fast or faster than the original code runs on the original architecture. In contrast to other migration efforts in the industry, the VAX translator reproduces subtle CISC behavior on a RISC machine, and both open-ended translators provide good performance on dynamically modified programs. Alpha AXP binary translators are important migration tools - hundreds of translated OpenVMS VAX and ULTRIX MIPS images currently run on Alpha AXP systems. When Digital started to design the Alpha AXP architecture in the fall of 1988, the Alpha AXP team was concerned about how to run existing VAX code and soon-to-exist MIPS code on the new Alpha AXP computers.[1,2] To take full advantage of the performance capability of a new computer architecture, an application must be ported by rebuilding, using native compilers. For a single program written in a standard programming language, this is a matter of recompile and run. A complex software application, however, can be built from hundreds of source pieces using dozens of tools. A native port of such an application is possible only when all parts of the build path are running on the new architecture. -

DEC Ada Installation Guide for Openvms Alpha Systems
DEC Ada Installation Guide for OpenVMS Alpha Systems Order Number: AA–PW1VC–TE May 1999 This guide contains instructions for installing DEC Ada Version 3.5 on OpenVMS Alpha systems. It also explains how to read the online release notes before or after installing the product. This guide applies to DEC Ada Version 3.5 and all maintenance updates throughout that version. Revision/Update Information: This is a new guide. Operating System & Version: OpenVMS Alpha Version 6.2 through 7.2 Software Version: DEC Ada Version 3.5 Compaq Computer Corporation Houston, Texas First Printing, January 1993 Revised, May 1999 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software on equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Restricted Rights: Use, duplication, or disclosure by the U.S. Government is subject to restrictions as set forth in subparagraph (c)(1)(ii) of the Rights in Technical Data and Computer Software clause at DFARS 252.227-7013. © Digital Equipment Corporation 1992, 1999. All Rights Reserved. Compaq and the Compaq logo are registered trademarks of Compaq Computer Corporation. Bookreader, DEC, DEC Ada, DEC C, DECdocument, Debugger, DECnet, DECset, DECstation, DECthreads, DIGITAL, DIGITAL Fortran, DIGITAL FUSE, DIGITAL Ladebug, DIGITAL logo, Digital UNIX, OpenVMS, ULTRIX, VAX, VAXcluster, VAX DOCUMENT, VMScluster are trademarks of Digital Equipment Corporation. -

VAX 4000 Model 100 to DEC 3000 Model 400S AXP Upgrade Instr
VAX 4000 Model 100 to DEC 3000 Model 400S AXP Upgrade Instructions MLO-010669 Part Number: EK-VX44S-IN. A01 Options You Can Upgrade Can Cannot Upgrade Upgrade Disks: RZ23L*, RZ24L* RZ57 RZ24* RZ25* RZ26* RZ55* RZ56* RZ58* Drives: RRD42** B400X RWZ01** DSSI Devices RX26* R400X TLZ04 TF85 TLZ06** TK50 TSZ05* TK70 TSZ07* TKZ08 TZ30 TSV05 TZ85* TU81 TZK10 Expansion Boxes: SZ03 SZ12 SZ16 Memory: None *Supported only in external device. **Including tabletop device. Check Components Shipped Your shipment should contain the following two kits. If you are missing any of these components, contact your Digital sales representative. System Kit: Ethernet Loopback Connector System Unit SCSI Documentation Terminator Antistatic Modem Loopback Wrist Strap Connector Printer Port Terminator System Power Cord Network Label Screwdriver Accessory Kit: Upgrade xxxxxxx xxxxxxxxxxx Card xxx Rubber Grommets RX26 Brackets Metal Support Plate TZ30 RFI Return Shield Address Label MLO-010670 Remove the System Unit Cover Follow these steps to remove the system unit cover: 1. Turn off the system by pressing the on/off switch to the off (O) position. 2. Disconnect the cables, connectors, and terminators from the system unit. 3. Loosen the two captive screws on the back of the system unit. B 1 A 0 0 Captive Screws MLO-010744 4. Slide the cover forward and lift it up from the system unit. Set the cover aside. Remove Fixed Disk Drives Note: The DEC 3000 system can hold two fixed disk drives and one removable-media drive. 1. Press and hold the spring clip that locks the disk drive in position. 2. -

Computer Architectures an Overview
Computer Architectures An Overview PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sat, 25 Feb 2012 22:35:32 UTC Contents Articles Microarchitecture 1 x86 7 PowerPC 23 IBM POWER 33 MIPS architecture 39 SPARC 57 ARM architecture 65 DEC Alpha 80 AlphaStation 92 AlphaServer 95 Very long instruction word 103 Instruction-level parallelism 107 Explicitly parallel instruction computing 108 References Article Sources and Contributors 111 Image Sources, Licenses and Contributors 113 Article Licenses License 114 Microarchitecture 1 Microarchitecture In computer engineering, microarchitecture (sometimes abbreviated to µarch or uarch), also called computer organization, is the way a given instruction set architecture (ISA) is implemented on a processor. A given ISA may be implemented with different microarchitectures.[1] Implementations might vary due to different goals of a given design or due to shifts in technology.[2] Computer architecture is the combination of microarchitecture and instruction set design. Relation to instruction set architecture The ISA is roughly the same as the programming model of a processor as seen by an assembly language programmer or compiler writer. The ISA includes the execution model, processor registers, address and data formats among other things. The Intel Core microarchitecture microarchitecture includes the constituent parts of the processor and how these interconnect and interoperate to implement the ISA. The microarchitecture of a machine is usually represented as (more or less detailed) diagrams that describe the interconnections of the various microarchitectural elements of the machine, which may be everything from single gates and registers, to complete arithmetic logic units (ALU)s and even larger elements. -

Console Port
DIGITAL NetRider Network Access Server Management Part Number: AA-PW5VE-TE June 1997 Revision/Update Information: This is a revised document. Software and Version: DECserver Network Access Software, Version 2.2 © Digital Equipment Corporation 1997. All rights reserved. Digital Equipment Corporation makes no representations that the use of its products in the manner described in this document will not infringe on existing or future patent rights, nor do the descriptions contained in this document imply the granting of licenses to make, use, or sell equipment or software in accordance with the description. Possession, use, or copying of this software and media is authorized only pursuant to a valid written license from DIGITAL or an authorized sublicensor. The following are trademarks of Digital Equipment Corporation: DDCMP, DEC, DECmcc, DECnet, DECserver, DECsystem, DECwindows, DIGITAL, DNA, LAT, NetRider, OpenVMS, ThinWire, ULTRIX, VAX, VAXstation, VMS, VMScluster, VT100, VT220,VT320, VT330, and the DIGITAL logo. The following are third-party trademarks: AppleTalk and Macintosh are registered trademarks of Apple Computer, Inc. HP and Hewlett-Packard are registered trademarks of Hewlett Packard Company. IBM is a registered trademark of International Business Machines Corporation. Kerberos is a trademark of the Massachusetts Institute of Technology. Microsoft, MS-DOS, and Windows 95 are registered trademarks, and Windows NT is a trademark of Microsoft Corporation. NetBIOS is a trademark of Micro Computer Systems, Inc. Novell and NetWare are registered trademarks of Novell, Inc. OS/2 is a registered trademark of International Business Machines Corporation. OSF/1 is a registered trademark of Open Software Foundation, Inc. PostScript is a registered trademark of Adobe Systems, Inc. -
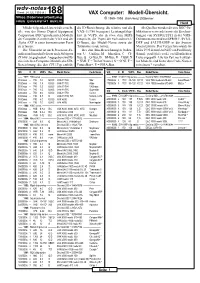
VAX-Computer
wdv-notes Stand: 24.JUL.1993 (4.) 188 VAX Computer: Modell-Übersicht. Wiss.Datenverarbeitung © 1980–1993 Karl-Heinz Dittberner FREIE UNIVERSITÄT BERLIN Hard Mit der folgenden Liste wird versucht, die ID-Bezeichnung, die relative (auf die Als Quellen wurden diverse DEC-Pu- alle von der Firma Digital Equipment VAX-11/780 bezogene) Leistungsfähig- blikationen verwendet sowie die Beschrei- Corporation (DEC) produzierten Modelle keit in VUPS, die in etwa dem MIPS bungen von SYS$GETSYI in der VMS- der Computer-Familien der VAX und der entspricht, die Typen der vorhandenen I/ Dokumentation und von $PRDEF, $VAX- Alpha AXP in einer konzentrierten Form O-Busse, der Modell-Name sowie der DEF und $ALPHADEF in der System zu erfassen. Tarnname (code name). Macro Library. Das Verzeichnis wurde im Die Übersicht ist nach Prozessor-Fa- Bei den Bus-Bezeichnungen bedeu- März 1993 der im UseNET von Paul Hardy milien und innerhalb dieser nach Subtypen ten: U = UniBus, M = MassBus, C = CI- (Email: [email protected]) veröffentlichten (X bzw. S) gegliedert. Angegeben sind für Bus, Q = Q-Bus, B = BI-Bus, D = DSSI, X Liste angepaßt. Alle zur Zeit noch aktuel- die einzelnen Computer-Modelle die SID- = XMI, T = TurboChannel, S = SCSI, F = len Modelle sind hinter dem Code-Namen Bezeichnung, die den CPU-Typ enthält, FutureBus+, E = EISA-Bus. mit einem * versehen. SID X ID VUPS Bus Model Name Code Name SID X ID VUPS Bus Model Name Code Name —— 1977: 700 series ———————————————————————————— —— 1991: NVAX+ chip series ———– Decimal SID = 385875968 ———————— 0100xxxx – 780 1.0 -

DSSI Vmscluster Installation and Troubleshooting Guide
DSSI VMScluster Installation and Troubleshooting Guide Order Number: EK–410AB–MG. D01 Digital Equipment Corporation Maynard, Massachusetts First Printing, October 1994 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation makes no representation that the use of its products in the manner described in the publication will not infringe on existing or future patent rights, nor do the descriptions contained in this publication imply the granting of licenses to make, use, or sell equipment or software in accordance with the description. Possession, use or copying of the sofware described in this publication is authorized only pursuant to a valid written license from Digital or an authorized sublicensor. Copyright © Digital Equipment Corporation, 1994. All Rights reserved. The Reader’s Comments form at the end of this document requests your critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: Alpha AXP, AXP, DEC, DECnet, Digital, MicroVAX, OpenVMS, VAX, VAX DOCUMENT, VAXcluster, VMScluster, the AXP logo, and the DIGITAL logo. OSF/1 is a registered trademark of Open Software Foundation, Inc. All other trademarks and registered trademarks are the property of their respective holders. FCC NOTICE: The equipment described in this manual generates, uses, and may emit radio frequency energy. The equipment has been type tested and found to comply with the limits for a Class A computing device pursuant to Subpart J of Part 15 of FCC Rules, which are designed to provide reasonable protection against such radio frequency interference when operated in a commercial environment.