Administrator Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Copyrighted Material
Index Numerics Address Resolution Protocol (ARP), 1052–1053 admin password, SOHO network, 16-bit Windows applications, 771–776, 985, 1011–1012 900, 902 Administrative Tools window, 1081–1083, 32-bit (x86) architecture, 124, 562, 769 1175–1176 64-bit (x64) architecture, 124, 562, 770–771 administrative tools, Windows, 610 administrator account, 1169–1170 A Administrators group, 1171 ADSL (Asynchronous Digital Subscriber Absolute Software LoJack feature, 206 Line), 1120 AC (alternating current), 40 Advanced Attributes window, NTFS AC adapters, 311–312, 461, 468–469 partitions, 692 Accelerated Graphics Port (AGP), 58 Advanced Computing Environment (ACE) accelerated video cards (graphics initiative, 724 accelerator cards), 388 Advanced Confi guration and Power access points, wireless, 996, 1121 Interface (ACPI) standard, 465 access time, hard drive, 226 Advanced Graphics Port (AGP) card, access tokens, 1146–1147 391–392 Account Operators group, 1172 Advanced Graphics Port (AGP) port, 105 ACE (Advanced Computing Environment) Advanced Host Controller Interface (AHCI), initiative, 724 212–213 ACPI (Advanced Confi guration and Power Advanced Micro Devices (AMD), 141–144 Interface) standard, 465 Advanced Packaging Tool (APT), 572 Action Center, 1191–1192 Advanced Power Management (APM) Active Directory Database, 1145–1146, 1183 standard, 465 active heat sink, 150 Advanced Programmable Interrupt active matrix display, LCD (thin-fi lm Controller (APIC), 374 transistor (TFT) display), 470 Advanced RISC Computing Specifi cation active partition, 267, -

Product Name User Guide
Smart-X Software Solutions Core Configurator User guide _______________________________________________________________ SmartX Software Solutions Core Configurator User Guide Table of content: WELCOME 4 FEATURES AND CAPABILITIES 5 MORE SYSTEM MANAGEMENT TOOLS 6 REQUIREMENTS 8 LICENSING AND INSTALLATION 8 EVALUATION VERSION LIMITATION 8 INSTALLATION 8 INSTALLING CORECONFIG ON WINDOWS 7 / 2008 R2 BETA VERSIONS 9 LICENSING 10 WORKING WITH CORE CONFIGURATOR 11 שגיאה! הסימניה אינה מוגדרת. CORE CONFIGURATOR MAIN SCREEN – 32 BIT HOW IT WORKS 11 CORE CONFIGURATOR MAIN SCREEN – 64 BIT 12 ACTIVATION SCREEN 13 HOW IT WORKS: 13 DISPLAY SETTINGS 14 HOW IT WORKS 14 TIME ZONE 15 HOW IT WORKS 15 REMOTE DESKTOP 16 HOW IT WORKS 16 ACCOUNT MANAGEMENT 17 HOW IT WORKS 17 FIREWALL 18 HOW IT WORKS 18 WINRM 19 HOW IT WORKS 19 NETWORKING 20 HOW IT WORKS 21 COMPUTER NAME 22 HOW IT WORKS 22 FEATURES 23 HOW IT WORKS 23 BACKUP PERFORMANCE 24 DCPROMO 25 HOW IT WORKS 26 AUTOMATIC UPDATES 27 HOW IT WORKS 29 REGIONAL LANGUAGES 30 HOW IT WORKS 30 REGISTRY EDITOR 31 2 SmartX Software Solutions Core Configurator User Guide HOW IT WORKS 31 TASK MANAGER 32 HOW IT WORKS 32 SERVICE 33 HOW IT WORKS 33 SYSTEM INFO 34 SHOW COMMANDS 35 3 SmartX Software Solutions Core Configurator User Guide Chapter 1 Welcome Welcome to Smart-X. Thank you for choosing Core Configurator™, one of the top tools developed by Smart-X Software Solutions expert team in an effort to optimize your everyday work. Core Configurator helps you manage your system efficiently, effortlessly and productively. This chapter describes the features and capabilities of Core Configurator, and lists additional tools in the same field that can help optimize your work environment. -

Windows Tool Reference
AppendixChapter A1 Windows Tool Reference Windows Management Tools This appendix lists sets of Windows management, maintenance, configuration, and monitor- ing tools that you may not be familiar with. Some are not automatically installed by Windows Setup but instead are hidden away in obscure folders on your Windows Setup DVD or CD- ROM. Others must be downloaded or purchased from Microsoft. They can be a great help in using, updating, and managing Windows. We’ll discuss the following tool kits: ■ Standard Tools—Our pick of handy programs installed by Windows Setup that we think are unappreciated and not well-enough known. ■ Support Tools—A set of useful command-line and GUI programs that can be installed from your Windows Setup DVD or CD-ROM. ■ Value-Added Tools—Several more sets of utilities hidden away on the Windows Setup CD-ROM. ■ Windows Ultimate Extras and PowerToys for XP—Accessories that can be downloaded for free from microsoft.com. The PowerToys include TweakUI, a program that lets you make adjustments to more Windows settings than you knew existed. ■ Resource Kits—A set of books published by Microsoft for some versions of Windows that includes a CD-ROM containing hundreds of utility programs. What you may not have known is that in some cases you can download the Resource Kit program toolkits with- out purchasing the books. ■ Subsystem for UNIX-Based Applications (SUA)—A package of network services and command-line tools that provide a nearly complete UNIX environment. It can be installed only on Windows Vista Ultimate and Enterprise, and Windows Server 2003. -

Copyrighted Material
Index rootkits, 629–631 Numerics Security settings, 625–627 0day exploits/worms, 602–603, 677 troubleshooting in, 206–207 3D Text screen saver, 240 activating Windows 7 3d Traceroute, 458 overview, 60 4:3 aspect ratio, 780 process, 60–63 16:9 aspect ratio, 780–781 Windows Activation Technologies, 32-bit version, 43–44 63–64 64-bit version, 43–44 active desktop, 35–36 802.11b protocol, 755 ActiveX, security issues, 499 802.11g protocol, 755 Activities icon, 589 802.11n protocol, 755 adapter, network, 737–738, 757–758 Adblock Plus add-on, 524 Add a List of All Burned Files setting, 335 A Add to Calendar menu item, 552 Add Pictures and Video to the DVD AAC (Advanced Audio Coding) fi les, window, 419 177, 351 Add Search Providers page, 467 Accelerators, 497–498 address bar access points, wireless (WAPs) Internet Explorer, 473 defi ned, 729, 753 Windows Media Player, 312 overview, 757–758 Adjust Color icon, 394 accounts, user administrator account, 118–119 adding, 124–125 Adobe Flash, 505 logging on, 116–117 ADSL (asymmetric digital subscriber overview, 115–116 line), 451 password reset disk, 130 Advanced Audio Coding (AAC) fi les, settings, changing, 126–130 177, 351 switching, 130–131 Advanced Boot options, 136–138 types of Advanced Research Project Agency administrator, 118–119 (ARPA), 444 Guest, 125–126 COPYRIGHTEDAdvanced MATERIAL Search overview, 118 Google, 537–539 selecting appropriate, 119–121 Windows 7, 282–284 standard, 118 adware, 16 User Account Control, 121–124 Aero Glass interface, 33–34 Acquire Licenses setting, 309 Aero Peek, -

Windows Performance Troubleshooting and Analysis Daniel Pearson David Solomon Expert Seminars Daniel Pearson
Windows Performance Troubleshooting and Analysis Daniel Pearson David Solomon Expert Seminars Daniel Pearson • Started working with Windows NT 3.51 • Three years at Digital Equipment Corporation • Supporting Intel and Alpha systems running Windows NT • Seven years at Microsoft • Senior Escalation Lead in Windows base team • Worked in the Mobile Internet sustained engineering team • Instructor for David Solomon, co-author of the Windows Internals book series Agenda • Components of performance analysis • Understanding the tools for troubleshooting and analyzing performance issues • Troubleshooting CPU and memory issues using various Windows tools * Portions of this session are based on material developed by Mark Russinovich and David Solomon Components of Performance Analysis • Event Tracing for Windows • Core component of the operating system • Kernel mode data structures • Used to store information about the system and system objects that can be read by various tools • e.g. dt nt!_KTHREAD KernelTime • CPU performance monitoring events • Refer to the Intel 64 and IA-32 Architectures Software Developer‟s Manual • http://developer.intel.com/products/processor/manuals Event Tracing for Windows • Built in to the system • High performance, low overhead and scalable • 2.5% CPU usage for a sustained rate of 10,000 events/sec on a 2 GHz CPU1 • Operations throughout the system that are of interest to performance are fully instrumented • e.g. process and thread activity, registry I/O, disk I/O 1. Milirud, Michael. 2008. Windows Performance Analysis: -

Monitor and Maintain a Multi-User Networked Operating System 114053
Monitor and maintain a multi-user networked operating system 114053 PURPOSE OF THE UNIT STANDARD This unit standard is intended To provide proficient knowledge of the areas covered For those working in, or entering the workplace in the area of Data Communications & Networking People credited with this unit standard are able to: Monitor the performance of a multi-user networked operating system Resolve problems with a multi-user networked operating system Maintain a multi-user networked operating system. The performance of all elements is to a standard that allows for further learning in this area. LEARNING ASSUMED TO BE IN PLACE AND RECOGNITION OF PRIOR LEARNING The credit value of this unit is based on a person having prior knowledge and skills to: Install and configure a multi-user networked operating system. Module 4 – Operating system support skills Author: LEARNER MANUAL Rel Date: 27/01/2018 Rev Date: 01/06/2023 Doc Ref: 48573 LM Mod 4 v-1 PAGE 55 INDEX Competence Requirements Page Unit Standard 114053 alignment index Here you will find the different outcomes explained which you need to be 57 proved competent in, in order to complete the Unit Standard 114053. Unit Standard 114053 59 Monitor the performance of a multi-user networked operating system 62 Resolve problems with a multi-user networked operating system 68 Maintain a multi-user networked operating system 84 Self-assessment Once you have completed all the questions after being facilitated, you need to check the progress you have made. If you feel that you are competent in the areas mentioned, you may tick the blocks, if however you feel that you 94 require additional knowledge, you need to indicate so in the block below. -

Dan's Motorcycle Windows Commands
1 Complete List of Run Commands in Windows XP, Vista, 7, 8 & 8.1 ¶ People can get stuck if they are attacked with viruses or in any way can’t access different Applications in Windows. Sometimes it gets difficult to find the commands to start the applications directly. Knowing the Run Command for a program in different Windows versions can be very useful. if you’d like to start a program from a script file or if you only have access to a command line interface this can be helpful. For example, If you have Microsoft Word installed (Any version of Microsoft Office®) rather then searching or clicking the start icon, locating the Microsoft Office folder and then clicking the Microsoft Word. You can use the Windows Run Box instead to access the application directly. Just Click Start and Click Run or press "Window Key + R" and type "Winword" and press enter, Microsoft Word will open immediately. Here is a, hopefully, Complete list of RUN Commands in Windows XP, Vista, 7, 8 and 8.1 for your quick and easy access. Description of Applications Run Command 32-bit ODBC driver under 64-bit platform = C:\windows\sysWOW64\ odbcad32.exe 64 bit ODBC driver under 64-bit platform = C:\windows\system32\ odbcad32.exe Accessibility Controls access.cpl Accessibility Options control access.cpl Accessibility Wizard accwiz Copyright © 1999-2016 dansmc.com. All rights reserved. Adapter Troubleshooter (Vista/Win7) AdapterTroubleshooter 2 Add Features to Windows 8 Win8 windowsanytimeupgradeui Add Hardware Wizard Win8 hdwwiz Add New Hardware Wizard hdwwiz.cpl Add/Remove -
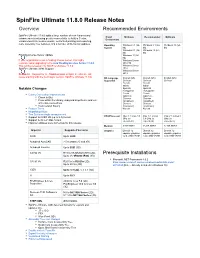
Spinfire Ultimate 11.8.0 Release Notes Overview Recommended Environments
SpinFire Ultimate 11.8.0 Release Notes Overview Recommended Environments SpinFire Ultimate 11.8.0 adds a large number of new features and Client Minimum Recommended Optimum enhancements including greater connectivity to Actify's Centro, Environment enhancements to measurements, vectorized printing and exporting, more assembly tree features, and a number of file format updates. Operating Windows 8.1 (64- Windows 8.1 (64- Windows 10 (64- System bit) bit) bit) Windows 8.1 (32- Windows 10 (64- bit) bit) Floating License Server Update Windows 10 (64- bit) If your organization uses a floating license server, it is highly Windows Server recommended upgrading to the new Floating License Server 11.8.0. 2012 R2 This will be necessary for SpinFire Ultimate 11.9.0. Windows Server SpinFire Ultimate 32-bit Support 2016 Windows Server Reminder - Support for the 32-bit version of SpinFire Ultimate will 2019 cease starting with the next major version, SpinFire Ultimate 11.9.0, OS Language English (US) English (US) English (US) Supported German German German French French Italian Italian Notable Changes Spanish Spanish Portuguese Portuguese Czech Czech Centro Connection Improvements Japanese Japanese Check In/Out Chinese Chinese From within the Library, drag and drop files in and out (simplified) (simplified) of Centro connections Chinese Chinese View version history (traditional) (traditional) Feature Trees Korean Korean Magnifying Glass Two Surfaces Angle measurement CPU/Processor Intel i3 4 Core 3.8 Intel i5 4 Cores Intel i7 8 Cores 4 Support for IGES -
Computer Performance
Computer Performance macOS macOS is Apple’s operating system for all Mac devices. For more information about macOS visit the macOS Apple Page. About This Mac This dialog shows you basic information about the manufacture date and hardware of your Mac. Click the Apple icon at the top left of the screen on the menu bar. Click About This Mac. The dialog window with basic system information will pop up. Click the System Report button for more detailed information for the advanced user. Activity Monitor Similar to Task Manager for PC, Activity Monitor displays every program running on your Mac. You can manage these running programs and identify how they are affecting your Mac’s performance. For more information visit Activity Monitor Support. Uninstall Unnecessary Applications One simple way to clear disk space and keep your computer running smoothly is to uninstall applications you don’t need or aren’t using. NOTE: Make sure you know what the application function is before you delete it, some applications are key to keeping your computer functioning properly. Find the list of applications: Open Finder → Applications (left side panel) How to Uninstall Applications on Mac Windows Windows is Microsoft’s operating system for PCs. For more information about Windows visit the Microsoft Windows Page. System Information Windows also has a basic system information dialog, similar to About This Mac (OS Version, Processor, Memory, 32/64bit info) Right click the This PC Icon on your Desktop and Click Properties. If it isn't there, search "This PC" in the Search Box on your Taskbar. -

Windows Command Guide 2010
bcdalai's Free Tech. Support Blog: [http://bcdalai.blogspot.com] Windows Command Guide 2010 Version 3.4 (May 2010 updates) No great discovery was ever made without a bold guess. –Isaac Newton Experience is the name everyone gives to their mistakes. –Oscar Wilde Persistence and positive thinking to make things happen. Welcome to the “Windows Command Guide”. In this guide you will find all types of Windows commands. This guide includes every possible command; those are available on a Windows platform. There are many long and unusual commands, those you may not use commonly – but, these commands available in Windows platform whether you know it or not. If you have more information, then please share with me. For more information visit the website. About this Article: As every Windows user knows what a command is, so there is no need for describing it. This guide contains 440+ Run commands and 580+ additional Windows commands. This guide contains approx. 1000+ Windows commands in various categories. This is very useful for everyone using – desktop, laptop and server. The objective of this guide is to know more about Windows commands, internals features and to speed up the administrative tasks. See the version number to check the latest updates and new release. Document History: (updated: v3.4) Time Changes 2010 Version 3.xx: 75+ GUID, shell commands, latest updates and revision. 2009 Version 2.xx: major updates: 300+ Run commands; 95+ Rundll32 commands; 120+ Environment Variables; 150+ Command-line tools; 75+ Control Panel Applets Canonical names on Vista SP2, 2008 SP2, Windows 7 and Office 2010. -

Memory System Resource Partitioning and Monitoring (MPAM), for Armv8-A
Arm® Architecture Reference Manual Supplement Memory System Resource Partitioning and Monitoring (MPAM), for Armv8-A Copyright © 2018-2020 Arm Limited or its affiliates. All rights reserved. ARM DDI 0598B.a (ID022020) Arm Architecture Reference Manual Supplement Memory System Resource Partitioning and Monitoring (MPAM), for Armv8-A Copyright © 2018-2020 Arm Limited or its affiliates. All rights reserved. Release Information The following releases of this document have been made. Release history Date Issue Confidentiality Change 30 October 2018 A.a Non-Confidential EAC release 05 July 2019 A.b Non-Confidential Updated EAC release 21 February 2020 B.a Non-confidential Updated EAC release incorporationg MPAMv0.1 and MPAMv1.1 architectures Proprietary Notice This document is protected by copyright and other related rights and the practice or implementation of the information contained in this document may be protected by one or more patents or pending patent applications. No part of this document may be reproduced in any form by any means without the express prior written permission of Arm. No license, express or implied, by estoppel or otherwise to any intellectual property rights is granted by this document unless specifically stated. Your access to the information in this document is conditional upon your acceptance that you will not use or permit others to use the information for the purposes of determining whether implementations infringe any third party patents. THIS DOCUMENT IS PROVIDED “AS IS”. Arm PROVIDES NO REPRESENTATIONS AND NO WARRANTIES, EXPRESS, IMPLIED OR STATUTORY, INCLUDING, WITHOUT LIMITATION, THE IMPLIED WARRANTIES OF MERCHANTABILITY, SATISFACTORY QUALITY, NON-INFRINGEMENT OR FITNESS FOR A PARTICULAR PURPOSE WITH RESPECT TO THE DOCUMENT. -

Windows 2012 Server Network Security Save 30% on Syngress Books and Ebooks
Windows 2012 Server Network Security Save 30% on Syngress books and eBooks n Save 30% on all Syngress books and eBooks at the Elsevier Store when you use promo code CW3013. n Free shipping on all orders. No minimum purchase. n Offer valid only on Syngress books sold by the Elsevier store until 31 December 2014. Click here to order a copy of: Windows Server 2012 Server Network Security How it works: 1. Choose a Syngress title. 2. Add the title to your shopping cart. 3. Click on “Enter Discount Code” in your shopping cart. 4. Enter code CW3013 to obtain your discount and click apply. Windows 2012 Server Network Security Securing Your Windows Network Systems and Infrastructure Derrick Rountree Richard Hicks, Technical Editor AMSTERDAM • BOSTON • HEIDELBERG • LONDON NEW YORK • OXFORD • PARIS • SAN DIEGO SAN FRANCISCO • SINGAPORE • SYDNEY • TOKYO Syngress is an Imprint of Elsevier Acquiring Editor: Chris Katsaropoulos Editorial Project Manager: Heather Scherer Project Manager: Priya Kumaraguruparan Designer: Mark Rogers Syngress is an imprint of Elsevier 225 Wyman Street, Waltham, MA 02451, USA Copyright © 2013 Elsevier Inc. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, electronic or mechanical, including photocopying, recording, or any information storage and retrieval system, without permission in writing from the publisher. Details on how to seek permission, further information about the Publisher’s permissions policies and our arrange- ments with organizations, such as the Copyright Clearance Center and the Copyright Licens- ing Agency, can be found at our website: www.elsevier.com/permissions.