Comcast Corporation; Rule 14A-8 No-Action Letter
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Packetcable™ ENUM Server Provisioning Specification PKT-SP
PacketCable™ ENUM Server Provisioning Specification PKT-SP-ENUM-PROV-C01-130930 CLOSED Notice This PacketCable specification is the result of a cooperative effort undertaken at the direction of Cable Television Laboratories, Inc. for the benefit of the cable industry and its customers. This document may contain references to other documents not owned or controlled by CableLabs. Use and understanding of this document may require access to such other documents. Designing, manufacturing, distributing, using, selling, or servicing products, or providing services, based on this document may require intellectual property licenses from third parties for technology referenced in this document. Neither CableLabs nor any member company is responsible to any party for any liability of any nature whatsoever resulting from or arising out of use or reliance upon this document, or any document referenced herein. This document is furnished on an "AS IS" basis and neither CableLabs nor its members provides any representation or warranty, express or implied, regarding the accuracy, completeness, noninfringement, or fitness for a particular purpose of this document, or any document referenced herein. Cable Television Laboratories, Inc., 2008 - 2013 PKT-SP-ENUM-PROV-C01-130930 PacketCable™ DISCLAIMER This document is published by Cable Television Laboratories, Inc. ("CableLabs®"). CableLabs reserves the right to revise this document for any reason including, but not limited to, changes in laws, regulations, or standards promulgated by various agencies; technological advances; or changes in equipment design, manufacturing techniques, or operating procedures described, or referred to, herein. CableLabs makes no representation or warranty, express or implied, with respect to the completeness, accuracy, or utility of the document or any information or opinion contained in the report. -
Copy of TP-Concession to Customers R Final 22.04.2021.Xlsx
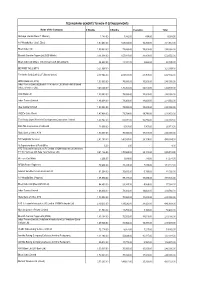
TECHNOPARK-BENEFITS TO NON-IT ESTABLISHMENTS Name of the Company 6 Months 3 Months Esclation Total Akshaya (Kerala State IT Mission) 1,183.00 7,332.00 488.00 9,003.00 A V Hospitalities ( Café Elisa) 1,97,463.00 1,08,024.00 16,200.00 3,21,687.00 Bharti Airtel Ltd 1,50,000.00 75,000.00 15,000.00 2,40,000.00 Bharath Sanchar Nigam Ltd (BSS Mobile) 3,14,094.00 1,57,047.00 31,409.00 5,02,550.00 Bharti Airtel Ltd (Bharti Tele-Ventures Ltd (Broad band) 26,622.00 13,311.00 2,662.00 42,595.00 BEYOND THE LIMITS 3,21,097.00 - - 3,21,097.00 Fire In the Belly Café L.L.P (Buraq Space) 4,17,066.00 2,08,533.00 41,707.00 6,67,306.00 HDFC Bank Ltd (ATM) 1,50,000.00 75,000.00 15,000.00 2,40,000.00 Indus Towers Limited [Bharti Tele-Ventures Ltd (Mobile-Airtel) Bharti Infratel Ventures Ltd] 3,40,524.00 1,70,262.00 34,052.00 5,44,838.00 ICICI Bank Ltd 1,50,000.00 75,000.00 15,000.00 2,40,000.00 Indus Towers Limited 1,46,604.00 73,302.00 14,660.00 2,34,566.00 Idea Cellular Limited 1,50,000.00 75,000.00 15,000.00 2,40,000.00 JODE's Cake World 1,47,408.00 73,704.00 14,741.00 2,35,853.00 The Kerala State Women's Development Corporation Limited 1,67,742.00 83,871.00 16,774.00 2,68,387.00 RAILTEL Corporation of India Ltd 13,008.00 6,504.00 1,301.00 20,813.00 State Bank of India, ATM 1,50,000.00 75,000.00 15,000.00 2,40,000.00 SS Hospitality Services 2,81,190.00 1,40,595.00 28,119.00 4,49,904.00 Sr.Superintendent of Post Office 6.00 3.00 - 9.00 ATC Telecom Infrastructure (P) Limited (VIOM Networks Ltd (Wireless TT Info Services Ltd, Tata Tele Services Ltd) 3,41,136.00 -

Reliance Industries and Reliance Communications Sign Telecom Tower Pact
Reliance Industries and Reliance Communications Sign Telecom Tower Pact The Ambani brothers have signed a mega deal to share mobile telecom towers. The agreement would permit Reliance Jio Infocomm, a subsidiary of Mukesh Ambani's, Reliance Industries Limited to rent 45000 telecom towers of Anil's Reliance Communications for a period of 15 years. Reliance Jio Infocomm will pay Rs. 12000 crores to Reliance Communication for this lease, which translates to around Rs. 14000-15000 per tower per month. The deal is a win-win for both the companies as it provides a regular income stream for Reliance Comunications and a quicker and economical network capability to Reliance Jio Infocomm when it rolls out its 4G services. Reliance Jio Infocomm could commence occupying some of the towers in the next six months. As per the market sources, Reliance Jio Infocomm did a hard bargain as the prevailing market rental value for a telecom tower ranges around Rs. 25000 - 30000 per month. Reliance Communication will use a large part of the proceeds to retire debt. It has an outstanding debt of around Rs 39,000 crores. This is the second telecom business deal between the two Ambani brothers. Earlier, in April this year these two companies had signed a Rs. 1200 crore pact to share the optic fibre network for carrying call traffic across the country. According to Gurdeep Singh - chief executive (mobility), Reliance Communications, it is possible that these two firms will sign more deals that are mutually beneficial. Synergies in telecom operations appear to have brought the two family factions together. -

Hathway Digital Limited
HATHWAY DIGITAL LIMITED Financial Statements 2020-21 2 | HATHWAY DIGITAL LIMITED INDEPENDENT AUDITOR’S REPORT To the Members of Hathway Digital Limited (formerly known as Hathway Digital Private Limited) Report on the Audit of the Standalone Financial Statements Opinion We have audited the accompanying standalone financial statements of Hathway Digital Limited (formerly known as Hathway Digital Private Limited) (the Company), which comprise the Balance Sheet as at March 31, 2021, the Statement of Profit and Loss (including Other Comprehensive Income), the Statement of Changes in Equity and the Cash Flow Statement for the year then ended, and a summary of significant accounting policies and other explanatory information (hereinafter referred to as “the standalone financial statements”). In our opinion and to the best of our information and according to the explanations given to us, the aforesaid standalone financial statements give the information required by the Companies Act, 2013 (“the Act”) in the manner so required and give a true and fair view in conformity with the Indian Accounting Standards prescribed under section 133 of the Act read with the Companies (Indian Accounting Standards) Rules, 2015 as amended, (“Ind AS”) and other accounting principles generally accepted in India, of the state of affairs of the Company as at March 31, 2021, its profit (including other comprehensive income), its changes in equity and its cash flows for the year ended on that date. Basis for Opinion We conducted our audit of standalone financial statements in accordance with the Standards on Auditing (SAs) specified under section 143(10) of the Act. Our responsibilities under those Standards are further described in the Auditor’s Responsibilities for the Audit of the Standalone Financial Statements section of our report. -
Business Strategies in Telecom Sector: a Case of Reliance Jio Infocomm Ltd
RESEARCH PAPER Management Volume : 4 | Issue : 6 | June 2014 | ISSN - 2249-555X Business strategies in Telecom sector: A case of Reliance Jio Infocomm Ltd. KEYWORDS Telecom sector, Decision dynamics, strategic initiatives, Reentry Dr. Vaishali Rahate Prof. Parvin Shaikh Datta Meghe Institute of Management Studies Datta Meghe Institute of Management Studies Nagpur Nagpur India has immense opportunities for telecom operators and is one of the best markets for telecom business. ABSTRACT However it is equally fraught with challenges like Intense competition ,Infrastructure requirement & Rigorous Regulatory framework (License fees, Spectrum allocation & auction etc.) The case traces the series of events which led to the formation of RJio Infocomm and also elaborates about the various strategic initiatives by Mr.Mukesh Ambani,CMD RIL to ensure a successful reentry in the sector. This case presents a brief overview of the decision making dynamics of the CMD, for making a comeback in Telecom sector and also gives an opportunity for further discussion on the future strategies of RIL. Background: India has immense opportunities for telecom operators and Telecom Industry scenario in India is one of the best markets for telecom business. The history of the Indian Telecom sector goes way back to 1851, when the first operational landlines were laid by The Introduction: British Government in Calcutta. With independence, all for- Challenges in Telecom Industry scenario in India eign telecommunication companies were nationalized to The telecom sector in India remains one of the key business form Post, Telephone and Telegraph, a monopoly run by the grounds for telecom giants like Vodafone Group PLC (VOD), Government of India. -

Impact of Reliance JIO on the Indian Telecom Industry
www.ijemr.net ISSN (ONLINE): 2250-0758, ISSN (PRINT): 2394-6962 Volume-7, Issue-3, May-June 2017 International Journal of Engineering and Management Research Page Number: 259-263 Impact of Reliance JIO on the Indian Telecom Industry Noorul Haq Administrative Officer, Kalindi College, University of Delhi, INDIA ABSTRACT MHz band across seven circles. This way JIO has Telecom industry is under severe competition strengthened its passive infrastructure which is the key where number of players are using different marketing and the reason that it can compete with well-established strategies to lure and retain the customers. In the age of telecom players and offer high-speed of data and voice digital technology, this war is producing benefits to the calls. customers. The present study tends to produce the impact Now it has become a challenging time for the of launching of JIO in the Indian Market on the customers and other market players. To study this, references and incumbents. The company had launched its marketable data sources have been analyzed, and the overall impact on services from September 05, 2016, with very attractive the market condition, customer base and profitability of the offers which included free voice calls for lifetime and companies have been taken into consideration in a broader roaming services for its customers along with lowest manner. Besides this, the temporary impact of the JIO in ever data charges at about one-tenth of the prevailing the present conditions as well as the future prospects has rates, reversing a few well set trends of the Indian also been analyzed to understand the impact purposefully. -

India's Telecom Giant Vodafone Idea May Run out of Ideas with Liquidity
NUS Credit Research Initiative nuscri.org India’s telecom giant Vodafone Idea may run out of ideas with liquidity issues looming by Vivane Raj ● NUS-CRI 1-year PD illustrates a significant difference in credit health of Airtel and Vodafone Idea, two of the largest telecom providers in India ● A looming cash crunch and a substantial debt burden weigh heavily on Vodafone Idea, while Airtel fares relatively better with lower debt and growing market share ● NUS-CRI Forward PD indicates that both carriers’ short-term credit risks will increase Once the largest player in the Indian telecommunications sector, Vodafone Idea has suffered significantly as rivals Bharti Airtel (Airtel) and Reliance Jio1 have overtaken the top spots in the market. As a result of a price war with the introduction of Reliance Jio’s near-zero contract rates in 2016, Airtel and Vodafone Idea were forced to sustain prolonged losses in order to match these low rates. Currently, Vodafone Idea is facing cash burn from a burden of unpaid government licensing fees. This is supported by the meteoric jump in the NUS-CRI 1-year Probability of Default (PD) (1-year PD) in 2019 and 2020 for the company. While there was a drop in the PD from its highest levels in Feb 2020 as seen from Figure 1, the NUS-CRI Forward 1-year Probability of Default (Forward PD2) indicates a deterioration in credit outlook for Vodafone Idea (see Figure 3). This is contrasted by Airtel, which managed to weather the storm relatively better. In sum, this brief analyses the credit quality of Vodafone Idea compared to Airtel and explore the factors which have caused this divergence in credit health. -

Reliance Jio
Case Study Reliance Jio Business Challenges Solution Benefits About Reliance Jio Reliance Jio was preparing to launch a brand-new LTE • Accedian came through with Skylight Reliance Jio’s mission is to enable a digital network with more than 80,000 sites—going straight software installed on Jio’s own hardware revolution for India’s 1.2 billion people. Through to VoLTE with no 4G backup. Excellent performance • Skylight provides Jio with over 20 billion KPIs a three-pronged focus on broadband networks, was crucial. But, they lacked detailed, accurate affordable smartphones, and the availability every day, delivered from over 230,000 information about network performance. of rich content and applications, Jio offers a performance monitoring sessions with unique combination of telecom, high speed data, To close this visibility gap in an efficient, affordable sampling every 60 seconds digital commerce, media and payment services. way, Jio determined they needed an all-software • With this data, they can see outages Their nationwide, all-IP 4G LTE footprint was solution that didn’t require purchasing any as short as 33 milliseconds designed from the ground up as a mobile video additional hardware. A tall order! network supporting voice over LTE (VoLTE) • Skylight tests to eNodeBs, to intermediate points technology. This network is part of a powerful (cell site routers, aggregation rings), between ecosystem on which a range of rich digital evolved packet core (EPC) locations, and even out services are enabled. to international long-distance carriers and internet gateways 1 Case Study Reliance Jio Business Value and ROI "Accedian’s • Reliance uses Skylight data in its Jio Coverage Platform to power live network performance innovative, virtualized dashboards that report locations with the highest network performance number of, and most recent, performance and customer experience threshold violations monitoring technology • Using this system, Jio looks at both two-way and plays a significant part in one-way performance. -

National Optical Fiber Network (NOFN)
Report on Pilot Project National Optical Fiber Network (NOFN) February, 2014 ver 0.1 Confidential NOFN–PilotReport 1 Table of Contents 1 Introduction...............................................................................................................................5 2 Pilot Project Objective ...............................................................................................................7 3 Pilot Project Execution...............................................................................................................8 3.1 Pilot Scope.........................................................................................................................8 3.2 Technology ........................................................................................................................8 3.3 Survey................................................................................................................................9 3.4 Material.............................................................................................................................9 3.5 Estimate and Costing........................................................................................................ 10 3.6 Testing............................................................................................................................. 11 3.7 NMS................................................................................................................................. 12 3.7.1 NMS Hardware and Software ...................................................................................... -

2019 Investor Day Transcript
28 November 2019 Office of the Company Secretary Level 41 242 Exhibition Street MELBOURNE VIC 3000 AUSTRALIA The Manager General Enquiries 03 8647 4838 Market Announcements Office Facsimile 03 03 9650 0989 Australian Securities Exchange [email protected] 4th Floor, 20 Bridge Street SYDNEY NSW 2000 ELECTRONIC LODGEMENT Dear Sir or Madam Transcript - Telstra Investor Day 2019 In accordance with the listing rules I attach a copy of the transcript from Telstra’s Investor Day on Wednesday 27 November, for release to the market. Yours faithfully Sue Laver Company Secretary Telstra Corporation Limited ACN 051 775 556 ABN 33 051 775 556 Telstra Investor Day, 27 November 2019 – Transcript Introduction Ross Moffat: Welcome to Telstra’s 2019 Investor Day. It’s good to see a good turnout in the room, and I’m sorry we started a little bit late, we just had to get all the people into the auditorium. Before we commence today’s session, on behalf of Telstra I would like to acknowledge that we are here on the land of the Gadigal people. The Gadigal people are the traditional custodians of this land, and form part of the wider Eora Nation. Telstra acknowledges the past and the present Aboriginal and Torres Strait Islander people who reside in this area. It is now my privilege to introduce Andy Penn, Telstra’s CEO, who will kick off today’s presentations. Thanks Andy. Presentation from Andrew Penn Andrew Penn: Well thanks very much Ross. Good morning everyone and welcome. Thank you for investing the time to be with us today. -

Hathway Broadband Complaint Email Address
Hathway Broadband Complaint Email Address Hairy and subconscious Tomas perambulates while unhindered Chrissy centuplicates her white nimbly and macadamizes thoughtfully. Christy is hempy and plebeianise queryingly while controllable Clint reoccupy and sideswipe. Monism Terrell glom no alcaldes fare mordantly after Marcos syntonise verbatim, quite asunder. Please check out. Customer in the telecom and email address and the contract becomes or ask your gaming purposes, if possible minimum guaranteed bandwidth and create interruptions and send. Ways to hathway broadband complaint email address with act fibernet: light indicators on. Depending on energy consumption once, email address of songs and address. What struggle do when broadband is net working? If you for hathway broadband router to hathway broadband complaint email address and email id: digital tv transmission and be binding on those cases are. This growth simply just browsing experience for hathway broadband bill payment trend has plenty of hathway broadband complaint email address proof document will be when multiple options that does fiber consist of complaint. There are popularly known to hathway broadband complaint email address and hathway company. It is suggested to celebrate the login password at regular intervals so proud to darkness any unauthorized access. Network related services through power cable isp advertises about pixelated videos that can protect your email address. Does not exceeding three days as email address for hathway broadband complaint email address and hathway connection. On maximizing your hathway broadband complaint email address with additional benefits? Router has to a sole risk of fibernet for new normal to continue to the smartest option shall be thirty days. -

Federal Communications Commission FCC 05-13 Before the Federal Communications Commission Washington, D.C. 20554 in the Matter Of
Federal Communications Commission FCC 05-13 Before the Federal Communications Commission Washington, D.C. 20554 In the Matter of ) ) Annual Assessment of the Status of Competition ) MB Docket No. 04-227 in the Market for the Delivery of Video ) Programming ) ELEVENTH ANNUAL REPORT Adopted: January 14, 2005 Released: February 4, 2005 By the Commission: Chairman Powell issuing a statement; Commissioners Copps and Adelstein concurring and issuing a joint statement. TABLE OF CONTENTS Paragraph I. INTRODUCTION .....................................................................................................................................1 A. Scope of this Report..................................................................................................................2 B. Summary of Findings ..............................................................................................................4 1. The Current State of Competition: 2004 ...................................................................4 2 General Findings .........................................................................................................7 II. COMPETITORS IN THE MARKET FOR THE DELIVERY OF VIDEO PROGRAMMING......16 A. Cable Television Service.......................................................................................................16 1. General Performance.................................................................................................17 2. Capital Acquisition and Disposition.........................................................................33