Antivirus – Internet Security Software
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton Antivirus™ 2009 Feature Comparison Chart
Norton 360™ Version 3.0, Norton Internet Security™ 2009, and Norton AntiVirus™ 2009 Feature Comparison Chart Feature Norton 360 Norton Internet Norton Explanation Version 3.0 Security 2009 AntiVirus 2009 Core Protection Antivirus ✔ ✔ ✔ Detects and removes viruses, Internet worms, and Trojan horses Antispyware ✔ ✔ ✔ Prevents spyware from infecting the PC Email and instant messaging protection ✔ ✔ ✔ Monitors email and instant messaging so users can exchange files without exchanging threats Antispam ✔ ✔ Automatically filters out annoying and fraudulent or phishing email from the user’s email inbox Advanced Protection Botnet detection ✔ ✔ ✔ Detects and prevents others from taking control of the PC, accessing private information, or using the computer to host an attack Rootkit detection ✔ ✔ ✔ Finds and removes threats that are hidden deep in the operating system Norton™ Insight ✔ ✔ ✔ Includes innovative, intelligence-driven technology for faster, fewer, shorter scans Norton™ Pulse Updates ✔ ✔ ✔ Delivers rapid pulse updates every 5 to 15 minutes for protection against new threats Smart, two-way firewall ✔ ✔ Makes intelligent incoming and outgoing security decisions without interrupting users to ask them each time Enhanced browser protection ✔ ✔ ✔ Secures against Web-based attacks that use browser vulnerabilities to infect PCs with malware Real-time behavioral protection ✔ ✔ ✔ Provides enhanced, real-time protection (SONAR™) Wireless network security protection ✔ ✔ Checks the status of wireless network security and provides expert advice on managing -

Norton™ Utilities Premium: User Manual
Norton™ Utilities Premium User Manual Norton Utilities Premium User Guide The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright © 2018 Symantec Corporation. All rights reserved. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. "Commercial Computer Software and Commercial Computer Software Documentation," as applicable, and any successor regulations, whether delivered by Symantec as on premises or hosted services. Any use, modification, reproduction release, performance, display or disclosure of the Licensed Software and Documentation by the U.S. Government shall be solely in accordance with the terms of this Agreement. -
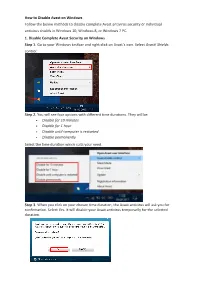
How to Disable to Antivirus
How to Disable Avast on Windows Follow the below methods to disable complete Avast antivirus security or individual antivirus shields in Windows 10, Windows 8, or Windows 7 PC. 1. Disable Complete Avast Security on Windows Step 1. Go to your Windows taskbar and right click on Avast’s icon. Select Avast! Shields control. Step 2. You will see four options with different time durations. They will be: • Disable for 10 minutes • Disable for 1 hour • Disable until computer is restarted • Disable permanently Select the time duration which suits your need. Step 3. When you click on your chosen time duration, the Avast antivirus will ask you for confirmation. Select Yes. It will disable your Avast antivirus temporarily for the selected duration. @CK How to disable or turn off AVG antivirus. 1. For AVG antivirus software: 1. Right-click the AVG icon in the system tray next to the clock. 2. Click "Temporarily disable AVG protection". 3. Choose how long you want the protection to be disabled and whether to disable the firewall as well, and then click "OK". 2. You can also disable AVG from the "Advanced settings": 1. Open the AVG Program. @CK 2. On the "Options" menu, click "Advanced settings". 3. Select "Temporarily disable AVG protection" in the menu on the left side. 4. Click the "Temporarily disable AVG protection" button. 5. Choose how long you want the protection to be disabled and whether to disable the Firewall as well, and then click "OK". @CK HOW TO DEACTIVATE / ACTIVATE AVIRA PROTECTION 1. Open the Avira Control Center 2. -

Hostscan 4.8.01064 Antimalware and Firewall Support Charts
HostScan 4.8.01064 Antimalware and Firewall Support Charts 10/1/19 © 2019 Cisco and/or its affiliates. All rights reserved. This document is Cisco public. Page 1 of 76 Contents HostScan Version 4.8.01064 Antimalware and Firewall Support Charts ............................................................................... 3 Antimalware and Firewall Attributes Supported by HostScan .................................................................................................. 3 OPSWAT Version Information ................................................................................................................................................. 5 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.890.0 for Windows .................................................. 5 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.890.0 for Windows ........................................................ 44 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.824.0 for macos .................................................... 65 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.824.0 for macOS ........................................................... 71 Cisco AnyConnect HostScan Antimalware Compliance Module v4.3.730.0 for Linux ...................................................... 73 Cisco AnyConnect HostScan Firewall Compliance Module v4.3.730.0 for Linux .............................................................. 76 ©201 9 Cisco and/or its affiliates. All rights reserved. This document is Cisco Public. -

Ques 1) How to Book a Domain ? Follow These Steps for Booking
Ques 1) How to Book a Domain ? Follow these steps for booking your Domain Name: Step 1 In the Domain search box on the home page enter the domain name you want, select an extension for your Domain name (e.g. .com, .net, org, .tv etc.) and start your search by clicking on the Search button. Step 2 The results page will next show you whether the Domain is available or not. If not available then you will have to resume your search again. If your Domain name is available, you may proceed to register by selecting the checkbox against the domain name you want and clicking on Continue. Step 3 Proceed to complete the Domain registration form. Note: INSTALINKS.NET does not need any pre-registration, and you will directly proceeded to a Domain registration form. Registration is absolutely free of cost. You only have to register once on the site. After completing and submitting the Domain registration form, you will get an order code and will receive an email from Instalinks containing your all information pertaining to the domain that you have booked. Your domain will be activated within 48 hrs of receiving your payment. Note: This email does NOT mean that your domain has been registered, it merely confirms your order. You have to send the Cheque/Draft for the amount pertaining to the domain you have booked to INSTALINKS for the registration of the domain. From the day you have applied for Domain booking, Instalinks will keep it for a maximum period of 21 days, during which you will receive reminders. -

A Glance Into the Eye Pyramid Technical Article V2
A glance into the Eye Pyramid RĂZVAN OLTEANU Security Reasercher We keep you safe and we keep it simple. 01 Introduction On January 11, 2017 Italian news agency AGI, published a court order regarding cyber-attacks against high ranking Italian government members and Italian institutions. The attacks were conducted by two Italian brothers to get financial information that would help them gain an advantage when trading on financial markets. Overview The campaign was carried out over several years starting in 2008 and continuing into 2010, 2011, 2012 and 2014. The mechanism the brothers used to distribute their malware was simple; targeted spear-phishing emails aimed at victims who had already been selected. The emails con- tained a malware attachment, which once opened harvested information from the victims’ computers. This information consisted of pictures, documents, archives, presenta- tions, email contacts, email bodies, usernames, passwords, keystrokes, web pages content and databases. Technical details The malware was written in VisualBasic.net and was obfuscated twice using common obfuscators: Dotfuscator and Skater .NET which can be easily reversed. The malware stored its sensitive data – license keys, URLs and paths – by encrypting with the Triple DES algorithm using the MD5 of a provided password as key and SHA256 of the pass- word as initialization vector. A glance into the Eye Pyramid 01 02 Figure 1 Security applications To remain unnoticed, it tried to disable any security application installed on the victim’s computer. Targeted -

FS-TST) Is a Software Package That Supports the Testing of Disk Imaging Tools
NISTIR 7103-B Forensic Software Testing Support Tools Test Summary Report Serban Gavrila VDG, Inc. Elizabeth Fong Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 NIST National Institute of Standards and Technology Technology Administration U.S. Department of Commerce NISTIR 7103-B Forensic Software Testing Support Tools Test Summary Report Serban Gavrila VDG, Inc. Elizabeth Fong Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899 April 2004 U.S.DEPARTMENT OF COMMERCE Donald L. Evans, Secretary TECHNOLOGY ADMINISTRATION Phillip J. Bond, Under Secretary of Commerce for Technology NATIONAL INSTITUTE OF STANDARDS AND TECHNOLOGY Ardent L. Bement, Jr., Director Forensic Software Testing Support Tools Test Summary Report Serban Gavrila* Elizabeth Fong ** ABSTRACT The Computer Forensics Tool Testing (CFTT) project at the National Institute of Standards and Technology (NIST), an agency of the United States Department of Commerce, provides a measure of confidence in the software tools used in computer forensic investigations. CFTT focuses on a class of tools called disk-imaging tools that copy or “image” hard disk drives. Forensic Software Testing Support Tools (FS-TST) is a software package that supports the testing of disk imaging tools. FS-TST includes 15 tools that perform hard disk initialization, faulty disk simulation, hard disk comparisons, extraction of information from a hard disk, and copying of disks or disk partitions. This NIST Interagency/Internal Report consists of two parts. Part A, covers the planning, design and specification of testing the tools included in the FS-TST package. Part B, which is this document, covers the test summary report. -

Aluria Security Center Avira Antivir Personaledition Classic 7
Aluria Security Center Avira AntiVir PersonalEdition Classic 7 - 8 Avira AntiVir Personal Free Antivirus ArcaVir Antivir/Internet Security 09.03.3201.9 x64 Ashampoo FireWall Ashampoo FireWall PRO 1.14 ALWIL Software Avast 4.0 Grisoft AVG 7.x Grisoft AVG 6.x Grisoft AVG 8.x Grisoft AVG 8.x x64 Avira Premium Security Suite 2006 Avira WebProtector 2.02 Avira AntiVir Personal - Free Antivirus 8.02 Avira AntiVir PersonalEdition Premium 7.06 AntiVir Windows Workstation 7.06.00.507 Kaspersky AntiViral Toolkit Pro BitDefender Free Edition BitDefender Internet Security BullGuard BullGuard AntiVirus BullGuard AntiVirus x64 CA eTrust AntiVirus 7 CA eTrust AntiVirus 7.1.0192 eTrust AntiVirus 7.1.194 CA eTrust AntiVirus 7.1 CA eTrust Suite Personal 2008 CA Licensing 1.57.1 CA Personal Firewall 9.1.0.26 CA Personal Firewall 2008 CA eTrust InoculateIT 6.0 ClamWin Antivirus ClamWin Antivirus x64 Comodo AntiSpam 2.6 Comodo AntiSpam 2.6 x64 COMODO AntiVirus 1.1 Comodo BOClean 4.25 COMODO Firewall Pro 1.0 - 3.x Comodo Internet Security 3.8.64739.471 Comodo Internet Security 3.8.64739.471 x64 Comodo Safe Surf 1.0.0.7 Comodo Safe Surf 1.0.0.7 x64 DrVirus 3.0 DrWeb for Windows 4.30 DrWeb Antivirus for Windows 4.30 Dr.Web AntiVirus 5 Dr.Web AntiVirus 5.0.0 EarthLink Protection Center PeoplePC Internet Security 1.5 PeoplePC Internet Security Pack / EarthLink Protection Center ESET NOD32 file on-access scanner ESET Smart Security 3.0 eTrust EZ Firewall 6.1.7.0 eTrust Personal Firewall 5.5.114 CA eTrust PestPatrol Anti-Spyware Corporate Edition CA eTrust PestPatrol -

Norton Antivirus Product Manual
NortonTM AntiVirus Product Manual Care for our Environment; ‘It's the right thing to do.’ Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. This manual is made from recycled materials. Norton AntiVirus™ Product Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 21.4 Copyright © 2014 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, LiveUpdate, Norton 360, and Norton are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Portions of this product Copyright 1996-2011 Glyph & Cog, LLC. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. -

Features of Norton Mobile Security
Norton Mobile Security User Guide DOWNLOAD AND INSTALL NORTON MOBILE SECURITY .................................................................. 1 ACTIVATE NORTON MOBILE SECURITY............................................................................................ 4 FEATURES OF NORTON MOBILE SECURITY ...................................................................................... 5 KEY FEATURES FOR IPHONES OR IPADS .......................................................................................... 7 SYSTEM REQUIREMENTS FOR NORTON MOBILE SECURITY ............................................................. 7 Download and install Norton Mobile Security You can directly download and install Norton Mobile Security on your mobile devices, or you can send an email with download instructions and access it on your mobile device. Select the device you are installing from: I am on a computEr and want to sEnd instructions to install Norton MobilE SEcurity to my devicE 1. Sign In to Norton. 2. If you are not signed in to Norton already, you are prompted to sign in. Type in your email address and password for Norton, and click Sign In. If you do not have a Norton account, click Create account, and complete the sign-up process. 3. In the Norton Setup window, move your mouse over Download Norton, and then click Send a Download Link. 4. Type an email address you can access on your device, and click the send icon . An email is sent to the email address with instructions to install the Norton product. Click DonE. 1 5. On the device where you want to install Norton, find and open the email that you received from "The Norton Team", and tap Download Now. The download link opens the Norton Setup page in your browser. 6. In the Norton Setup window, tap Download Now or Install. 7. You are redirected to the Norton Security and Antivirus page on the Google Play Store or App Store. -

Product Releases Dec 02
Historical Product Releases Dec-02 Symantec ManHunt 2.2 Symantec ManTrap 3.0 Symantec Host Intrusion Detection 4.0 Symantec NetRecon 3.6 Symantec Event Manager for Antivirus 1.0 Symantec Event Manager for Client Security 1.0 Symantec Event Collector for NET ePO Symantec Event Relay Tivoli Symantec Incident Manager 1.0 Symantec AntiVirus Corporate Edition 8.0 EMC Symantec AntiVirus Scan Engine 4.0 Symantec AntiVirus 4.0 for ISA Symantec AntiVirus 4.0 for NetApp Filer Symantec AntiVirus for NetApp NetCache Symantec AntiVirus Filtering for Domino W2NT v 3.1 Norton Internet Security Professional 2003 Sep-02 Enterprise Security Manager for Databases 3.0 Enterprise Security Manager for Firewall 2.0 Enterprise Security Manager for HIPAA 1.0 Symantec AntiVirus for SMTP Gateways 3.0 Symantec AntiVirus Gateway Solution 3.0 Symantec AntiVirus Enterprise Edition 8.5 Symantec Client Security Norton AntiVirus 2003 Norton AntiVirus Professional 2003 Norton Ghost 2003 Norton Internet Security 2003 Norton Personal Firewall 2003 Norton SystemWorks 2003 Norton SystemWorks Professional 2003 Jun-02 Symantec Web Security 2.5 Syamantec Gateway Security (models 5100, 5200, 5300) VelociRaptor 1.5 (models 1100, 1200, 1300) Net Prowler 3.5.1 Symantec AntiVirus Gateway Solution Symantec AntiVirus Scan Engine 3.0 Symantec AntiVirus for Inktomi Traffic Edge 3.0 Symantec AntiVirus for Network Appliances filer/NetCache 3.0 Norton AntiVirus for Lotus Notes/Domino on Linux Mar-02 Symantec Gateway Security RK4 ESM - Best Practice Policies Firewall 1.0 ESM - Best Practice -

2005 Annual Report
SYMANTEC 2005 ANNUAL REPORT BE FEARLESS LEAD THREE YEAR SUMMARY Fiscal Year Ended (in millions, except per share amounts) 2005 2004 2003 Reconciliation of Non-GAAP to GAAP Results*: Revenues $ 2,583 $ 1,870 $ 1,407 Non-GAAP Gross Margin $ 2,180 $ 1,584 $ 1,186 Cost of revenues: amortization of acquired product rights $ (49) $ (41) $ (29) GAAP Gross Margin $ 2,131 $ 1,543 $ 1,157 Non-GAAP Operating Expenses $ 1,292 $ 1,007 $ 796 Amortization of other intangibles from acquisitions $ 5 $ 3 $ 3 Amortization of deferred stock-based compensation $ 5 – – Acquired in-process research and development $ 3 $ 4 $ 5 Restructuring $ 3 $ 1 $ 11 Patent settlement – $ 14 – Integration costs $ 3 – – GAAP Operating Expenses $ 1,311 $ 1,029 $ 815 Non-GAAP Net Income $ 634 $ 411 $ 280 Cost of revenues $ (49) $ (41) $ (29) Operating expenses $ (20) $ (21) $ (19) Income tax benefit $ 25 $ 22 $ 16 Tax charge on cash repatriation $ (54) – – GAAP Net Income $ 536 $ 371 $ 248 GAAP Net Income per Share – Diluted $ 0.74 $ 0.54 $ 0.38 Non-GAAP Net Income per Share – Diluted $ 0.87 $ 0.59 $ 0.43 Other Information: Cash Flow from Operating Activities $ 1,207 $ 903 $ 599 Total Assets $ 5,614 $ 4,456 $ 3,266 Stockholders’ Equity $ 3,705 $ 2,426 $ 1,764 Total Employees 6,395 5,300 4,344 *In addition to reporting financial results in accordance with generally accepted accounting principles, or GAAP, Symantec reports non-GAAP financial results. Non-GAAP net income per share exclude amortization of acquisition-related intangibles, amortization of deferred stock-based compensation, in-process research and development, and certain other identified charges, such as restructuring, patent settlement, and integration planning expenses associated with the VERITAS merger, as well as the tax ef- fect of these items, and the one-time tax effect associated with the company’s cash repatriation under the American Jobs Creation Act.