ARM Optimizing C/C++ Compiler V18.1.0.LTS
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Compiling Sandboxes: Formally Verified Software Fault Isolation
Compiling Sandboxes: Formally Verified Software Fault Isolation Frédéric Besson1[0000−0001−6815−0652], Sandrine Blazy1[0000−0002−0189−0223], Alexandre Dang1, Thomas Jensen1, and Pierre Wilke2[0000−0001−9681−644X] 1 Inria, Univ Rennes, CNRS, IRISA 2 CentraleSupélec, Inria, Univ Rennes, CNRS, IRISA Abstract. Software Fault Isolation (SFI) is a security-enhancing pro- gram transformation for instrumenting an untrusted binary module so that it runs inside a dedicated isolated address space, called a sandbox. To ensure that the untrusted module cannot escape its sandbox, existing approaches such as Google’s Native Client rely on a binary verifier to check that all memory accesses are within the sandbox. Instead of rely- ing on a posteriori verification, we design, implement and prove correct a program instrumentation phase as part of the formally verified com- piler CompCert that enforces a sandboxing security property a priori. This eliminates the need for a binary verifier and, instead, leverages the soundness proof of the compiler to prove the security of the sandbox- ing transformation. The technical contributions are a novel sandboxing transformation that has a well-defined C semantics and which supports arbitrary function pointers, and a formally verified C compiler that im- plements SFI. Experiments show that our formally verified technique is a competitive way of implementing SFI. 1 Introduction Isolating programs with various levels of trustworthiness is a fundamental se- curity concern, be it on a cloud computing platform running untrusted code provided by customers, or in a web browser running untrusted code coming from different origins. In these contexts, it is of the utmost importance to pro- vide adequate isolation mechanisms so that a faulty or malicious computation cannot compromise the host or neighbouring computations. -

Language Subsetting in an Industrial Context: a Comparison of MISRA C 1998 and MISRA C 2004
Language subsetting in an industrial context: a comparison of MISRA C 1998 and MISRA C 2004 Les Hatton CISM, University of Kingston∗ November 20, 2005 Abstract The MISRA C standard [7] first appeared in 1998 with the objective of providing a set of guidelines to restrict features in the ISO C language of known undefined or otherwise dangerous behaviour. The standard was assembled by representatives of a number of companies in the automobile sector in response to the rapidly growing use of C in electronic embedded systems in automobiles. The standard attempts to build on the earlier work of [6], [3] and others. Due to various perceived deficiencies, notably considerable ambiguity in the rule definitions, a revision was planned and eventually appeared in 2004. This paper measures how well the two stan- dards compare on the same population of software and also determines how well the 2004 version achieved its stated goals. Given its increasing influence, the results raise important concerns. Keywords: safer subsets, MISRA C, embedded control systems 1 Overview Pragmatic safer subsetting of languages to remove dependence on poorly defined features is finally becoming a mainstream activity with the recent recommen- dation to form a high-integrity study group under the auspices of the ISO, [8] with the intention of producing sets of rules to restrict features with undefined or otherwise dangerous behaviour in programming languages in common use. It frequently comes as a surprise to developers that significant parts of a pro- gramming language can fall into this category. In practice, all standardised programming languages contain problematic features for a variety of reasons which include the inability of the standardising committee to agree on the be- haviour of a particular feature, the use of unintentionally ambiguous language in the standards document itself, omitting to say anything at all and so on. -

Using the GNU Compiler Collection (GCC)
Using the GNU Compiler Collection (GCC) Using the GNU Compiler Collection by Richard M. Stallman and the GCC Developer Community Last updated 23 May 2004 for GCC 3.4.6 For GCC Version 3.4.6 Published by: GNU Press Website: www.gnupress.org a division of the General: [email protected] Free Software Foundation Orders: [email protected] 59 Temple Place Suite 330 Tel 617-542-5942 Boston, MA 02111-1307 USA Fax 617-542-2652 Last printed October 2003 for GCC 3.3.1. Printed copies are available for $45 each. Copyright c 1988, 1989, 1992, 1993, 1994, 1995, 1996, 1997, 1998, 1999, 2000, 2001, 2002, 2003, 2004 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with the Invariant Sections being \GNU General Public License" and \Funding Free Software", the Front-Cover texts being (a) (see below), and with the Back-Cover Texts being (b) (see below). A copy of the license is included in the section entitled \GNU Free Documentation License". (a) The FSF's Front-Cover Text is: A GNU Manual (b) The FSF's Back-Cover Text is: You have freedom to copy and modify this GNU Manual, like GNU software. Copies published by the Free Software Foundation raise funds for GNU development. i Short Contents Introduction ...................................... 1 1 Programming Languages Supported by GCC ............ 3 2 Language Standards Supported by GCC ............... 5 3 GCC Command Options ......................... -

Bringing GNU Emacs to Native Code
Bringing GNU Emacs to Native Code Andrea Corallo Luca Nassi Nicola Manca [email protected] [email protected] [email protected] CNR-SPIN Genoa, Italy ABSTRACT such a long-standing project. Although this makes it didactic, some Emacs Lisp (Elisp) is the Lisp dialect used by the Emacs text editor limitations prevent the current implementation of Emacs Lisp to family. GNU Emacs can currently execute Elisp code either inter- be appealing for broader use. In this context, performance issues preted or byte-interpreted after it has been compiled to byte-code. represent the main bottleneck, which can be broken down in three In this work we discuss the implementation of an optimizing com- main sub-problems: piler approach for Elisp targeting native code. The native compiler • lack of true multi-threading support, employs the byte-compiler’s internal representation as input and • garbage collection speed, exploits libgccjit to achieve code generation using the GNU Com- • code execution speed. piler Collection (GCC) infrastructure. Generated executables are From now on we will focus on the last of these issues, which con- stored as binary files and can be loaded and unloaded dynamically. stitutes the topic of this work. Most of the functionality of the compiler is written in Elisp itself, The current implementation traditionally approaches the prob- including several optimization passes, paired with a C back-end lem of code execution speed in two ways: to interface with the GNU Emacs core and libgccjit. Though still a work in progress, our implementation is able to bootstrap a func- • Implementing a large number of performance-sensitive prim- tional Emacs and compile all lexically scoped Elisp files, including itive functions (also known as subr) in C. -

Hop Client-Side Compilation
Chapter 1 Hop Client-Side Compilation Florian Loitsch1, Manuel Serrano1 Abstract: Hop is a new language for programming interactive Web applications. It aims to replace HTML, JavaScript, and server-side scripting languages (such as PHP, JSP) with a unique language that is used for client-side interactions and server-side computations. A Hop execution platform is made of two compilers: one that compiles the code executed by the server, and one that compiles the code executed by the client. This paper presents the latter. In order to ensure compatibility of Hop graphical user interfaces with popular plain Web browsers, the client-side Hop compiler has to generate regular HTML and JavaScript code. The generated code runs roughly at the same speed as hand- written code. Since the Hop language is built on top of the Scheme program- ming language, compiling Hop to JavaScript is nearly equivalent to compiling Scheme to JavaScript. SCM2JS, the compiler we have designed, supports the whole Scheme core language. In particular, it features proper tail recursion. How- ever complete proper tail recursion may slow down the generated code. Despite an optimization which eliminates up to 40% of instrumentation for tail call in- tensive benchmarks, worst case programs were more than two times slower. As a result Hop only uses a weaker form of tail-call optimization which simplifies recursive tail-calls to while-loops. The techniques presented in this paper can be applied to most strict functional languages such as ML and Lisp. SCM2JS can be downloaded at http://www-sop.inria.fr/mimosa/person- nel/Florian.Loitsch/scheme2js/. -

MISRA-C Subset of the C Language for Critical Systems SAFETY-CRITICAL SYSTEMS
MISRA-C Subset of the C language for critical systems SAFETY-CRITICAL SYSTEMS System is safety-critical if people might die due to software bugs Examples Automobile stability / traction control Medical automation Many military applications You develop safety-critical software differently from non-critical software MISRA-C MISRA – Motor Industry Software Reliability Association Their bright idea: Can’t avoid C But can force developers to avoid features of C that are known to be problematic Some language flaws Some legitimate features that happen to be bad for embedded software Most of MISRA-C is just good common sense for any C programmer TERMINOLOGY Execution error: Something illegal done by a program Out-of-bounds array reference Divide by zero Uninitialized variable usage Trapped execution error: Immediately results in exception or program termination Untrapped execution error: Program keeps running But may fail in an unexpected way later on E.g., due to corrupted RAM In C, operations with undefined behavior are not trapped SAFETY A safe language does not allow untrapped execution errors A statically safe language catches all execution errors at compile time Useful languages can’t be completely statically safe Java is dynamically safe C and C++ are very unsafe MISRA C is not safe either However, adherence to MISRA-C can largely be statically checked This eliminates or reduces the likelihood of some kinds of untrapped execution errors MISRA-C RULE 1.2 No reliance shall be placed on undefined or unspecified behavior. Lots of things in C have undefined behavior Divide by zero Out-of-bounds memory access Signed integer overflow Lots of things in C have implementation-defined and unspecified behavior printf (“a”) + printf (“b”); Both of these hard to detect at compile time, in general Implementation-defined behavior is fine in MISRA-C Why? MISRA-C RULE 5.2 Identifiers in an inner scope shall not use the same name as an identifier in an outer scope, and therefore hide that identifier. -

Crosscore Embedded Studio 2.2.0 C/C++ Compiler Manual for SHARC
CrossCore Embedded Studio 2.2.0 C/C++ Compiler Manual for SHARC Processors Revision 1.5, February 2016 Part Number 82-100117-01 Analog Devices, Inc. One Technology Way Norwood, MA 02062-9106 Copyright Information ©2016 Analog Devices, Inc., ALL RIGHTS RESERVED. This document may not be reproduced in any form without prior, express written consent from Analog Devices, Inc. Printed in the USA. Disclaimer Analog Devices, Inc. reserves the right to change this product without prior notice. Information furnished by Ana- log Devices is believed to be accurate and reliable. However, no responsibility is assumed by Analog Devices for its use; nor for any infringement of patents or other rights of third parties which may result from its use. No license is granted by implication or otherwise under the patent rights of Analog Devices, Inc. Trademark and Service Mark Notice The Analog Devices logo, Blackfin, CrossCore, EngineerZone, EZ-Board, EZ-KIT, EZ-KIT Lite, EZ-Extender, SHARC, and VisualDSP++ are registered trademarks of Analog Devices, Inc. Blackfin+, SHARC+, and EZ-KIT Mini are trademarks of Analog Devices, Inc. All other brand and product names are trademarks or service marks of their respective owners. CrossCore Embedded Studio 2.2.0 i Contents Preface Purpose of This Manual................................................................................................................................. 1±1 Intended Audience........................................................................................................................................ -

MISRA-C:2004 Guidelines for the Use of the C Language in Critical Systems
MISRA-C:2004 Guidelines for the use of the C language in critical systems October 2004 Licensed to: Tyler Doering. 10 Sep 2008. Copy 1 of 1 First published October 2004 by MIRA Limited Watling Street Nuneaton Warwickshire CV10 0TU UK www.misra-c.com Edition 2 reprinted July 2008 incorporating Technical Corrigendum 1 © MIRA Limited, 2004, 2008. “MISRA”, “MISRA C” and the triangle logo are registered trademarks of MIRA Limited, held on behalf of the MISRA Consortium. All rights reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical or photocopying, recording or otherwise without the prior written permission of the Publisher. ISBN 978-0-9524156-2-6 paperback ISBN 978-0-9524156-4-0 PDF Printed by Hobbs the Printers Ltd British Library Cataloguing in Publication Data. A catalogue record for this book is available from the British Library This copy of MISRA-C:2004 - Guidelines for the use of the C language in critical systems is issued to Tyler Doering. The file must not be altered in any way. No permission is given for distribution of this file. This includes but is not exclusively limited to making the copy available to others by email, placing it on a server for access by intra- or inter-net, or by printing and distributing hardcopies. Any such use constitutes an infringement of copyright. MISRA gives no guarantees about the accuracy of the information contained in this PDF version of the Guidelines. The published paper document should be taken as authoritative. -

Evaluation of Open Source Operating Systems for Safety-Critical Applications Master’S Thesis in Embedded Electronic System Design
Evaluation of open source operating systems for safety-critical applications Master’s thesis in Embedded Electronic System Design Petter Sainio Berntsson Department of Computer Science and Engineering CHALMERS UNIVERSITY OF TECHNOLOGY UNIVERSITY OF GOTHENBURG Gothenburg, Sweden 2017 MASTER’S THESIS 2017 Evaluation of open source operating systems for Safety-critical applications Petter Sainio Berntsson Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg Gothenburg, Sweden 2017 Evaluation of open source operating systems for safety-critical applications Petter Sainio Berntsson © Petter Sainio Berntsson, 2017 Examiner: Per Larsson-Edefors Chalmers University of Technology Department of Computer Science and Engineering Academic supervisor: Jan Jonsson Chalmers University of Technology Department of Computer Science and Engineering Industrial supervisors: Lars Strandén RISE Research Institutes of Sweden Dependable Systems Fredrik Warg RISE Research Institutes of Sweden Dependable Systems Master’s Thesis 2017 Department of Computer Science and Engineering Chalmers University of Technology University of Gothenburg SE-412 96 Gothenburg Telephone +46(0) 31 772 1000 Abstract Today many embedded applications will have to handle multitasking with real-time time constraints and the solution for handling multitasking is to use a real-time operating system for scheduling and managing the real-time tasks. There are many different open source real-time operating systems available and the use of open source software for safety-critical applications is considered highly interesting by industries such as medical, aerospace and automotive as it enables a shorter time to market and lower development costs. If one would like to use open source software in a safety-critical context one would have to provide evidence that the software being used fulfills the requirement put forth by the industry specific standard for functional safety, such as the ISO 26262 standard for the automotive industry. -
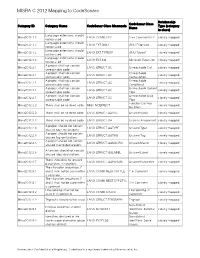
MISRA C 2012 Mapping to Codesonar®
MISRA C 2012 Mapping to CodeSonar® Relationship CodeSonar Class Category ID Category Name CodeSonar Class Mnemonic Type (category Name to class) Language extensions should Misra2012:1.2 LANG.COMM.CPP C++ Comment in C closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.GNU GNU Extension closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.TYPEOF GNU Typeof closely mapped not be used Language extensions should Misra2012:1.2 LANG.EXT.MS Microsoft Extension closely mapped not be used A project shall not contain Misra2012:2.1 LANG.STRUCT.UC Unreachable Call closely mapped unreachable code A project shall not contain Unreachable Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Computation A project shall not contain Unreachable Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Conditional A project shall not contain Unreachable Control Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Flow A project shall not contain Unreachable Data Misra2012:2.1 LANG.STRUCT.UC closely mapped unreachable code Flow Function Call Has Misra2012:2.2 There shall be no dead code MISC.NOEFFECT closely mapped No Effect Misra2012:2.2 There shall be no dead code LANG.STRUCT.UUVAL Unused Value closely mapped Misra2012:2.2 There shall be no dead code LANG.STRUCT.UA Useless Assignment closely mapped A project should not contain Misra2012:2.3 LANG.STRUCT.UUTYPE Unused Type closely mapped unused type declarations A project should not contain Misra2012:2.4 LANG.STRUCT.UUTAG Unused Tag closely -

C-STAT® Static Analysis Guide
C-STAT® Static Analysis Guide CSTAT-14 COPYRIGHT NOTICE © 2015–2021 IAR Systems AB and Synopsys, Inc. No part of this document may be reproduced without the prior written consent of IAR Systems AB. The software described in this document is furnished under a license and may only be used or copied in accordance with the terms of such a license. This publication incorporates portions of the Technical Report, “SEI CERT C Coding Standard Rules for Developing Safe, Reliable, and Secure Systems 2016 Edition,” by CERT. © 2016 Carnegie Mellon University, with special permission from its Software Engineering Institute. DISCLAIMERS The information in this document is subject to change without notice and does not represent a commitment on any part of IAR Systems. While the information contained herein is assumed to be accurate, IAR Systems assumes no responsibility for any errors or omissions. In no event shall IAR Systems, its employees, its contractors, or the authors of this document be liable for special, direct, indirect, or consequential damage, losses, costs, charges, claims, demands, claim for lost profits, fees, or expenses of any nature or kind. Any material of Carnegie Mellon University and/or its software engineering institute contained herein is furnished on an “as-is” basis. Carnegie Mellon University makes no warranties of any kind, either expressed or implied, as to any matter including, but not limited to, warranty of fitness for purpose or merchantability, exclusivity, or results obtained from use of the material. Carnegie Mellon University does not make any warranty of any kind with respect to freedom from patent, trademark, or copyright infringement. -

Practical Control-Flow Integrity
Practical Control-Flow Integrity by Ben Niu Presented to the Graduate and Research Committee of Lehigh University in Candidacy for the Degree of Doctor of Philosophy in Computer Science Lehigh University January, 2016 Copyright © 2015 Ben Niu. All rights reserved. ii Approved and recommended for acceptance as a dissertation in partial fulfillment of the re- quirements for the degree of Doctor of Philosophy. Ben Niu Practical Control-Flow Integrity Date Gang Tan, Dissertation Director Accepted Date Committee Members Gang Tan (Chair) Mooi-Choo Chuah Michael Spear Stephen McCamant iii ACKNOWLEDGEMENTS I am very grateful to my great advisor Prof. Gang Tan. I had no idea how to do research when I came to Lehigh, and he taught me what to think of, how to think, how to present my thoughts, and how to write them down. His door was always open for discussion, he replied emails during weekends, and he provided detailed guidance on any technical problem. I was constantly surprised at his breadth of knowledge and depth of understanding, and I enjoyed working with him. I also thank my thesis committee members, Prof. Mooi-Choo Chuah, Prof. Michael Spear, and Prof. Stephen McCamant for their courses, research works and insightful comments on my research. Michael’s parallel programming course introduced me lock-free algorithms and his operating system course consolidated my system programming skills. Stephen’s research on SFI provided me a foundation in my research, without which I would be still looking for decent solutions. I appreciate my colleagues at MSRC during my internship at Microsoft, especially Matt & Ken, Suha, Vishal, Swamy, Joe, Axel and Marcus.