Honeynet and Snort IDS Data Collection Analysis Server Configur
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Campus Networking Best Practices Session 5: Wireless
Campus Networking Best Practices Session 5: Wireless LAN Hervey Allen Dale Smith NSRC & University of Oregon University of Oregon & NSRC [email protected] [email protected] Wireless LAN • Provide wireless network across your campus that has the following characteristics: – Authentication – only allow your users – Roaming – allow users to start up in one section of your network, then move to another location – Runs on your campus network Firewall/ Border Traffic Shaper Router Wireless REN switch Authentication Core Gateway Router Core Servers Network Access Control (NAC) Enterprise Identity Management • Processes and Documentation of users. – Now you must deal with this. – What to use as the back-end user store? • LDAP • Active Directory • Kerberos • Other? – Will this play nice with future use? • email, student/staff information, resource access, ... Identity Management Cont. • An example of such a project can be seen here: – http://ccadmin.uoregon.edu/idm/ • This is a retrofit on to an already retrofitted system. • Learn from others and try to avoid this situation if possible. A Wireless Captive Portal The Wireless Captive Portal • Previous example was very simple. • A Captive Portal is your chance to: – Explain your Acceptable Use Policies – Decide if you must authenticate, or – Allow users on your network and monitor for problems instead (alternate solution). – Anything else? Branding? What's Happening? • remember our initial network diagrams...? • Do you think our hotel built their own solution? • Probably not... Commercial Solutions • Aruba http://www.arubanetworks.com/ • Bradford Networks – http://www.bradfordnetworks.com/ • Cisco NAC Appliance (Clean Access) – http://www.cisco.com/en/US/products/ps6128/ • Cisco Wireless LAN Controllers – http://www.cisco.com/en/US/products/hw/wireless/ • Enterasys http://www.enterasys.com/ • Vernier http://www.verniernetworks.com Open Source Solutions • CoovaChilli (morphed from Chillispot) – http://coova.org/wiki/index.php/CoovaChilli – Uses RADIUS for access and accounting. -

Introduzione Al Mondo Freebsd
Introduzione al mondo FreeBSD Corso avanzato Netstudent Netstudent http://netstudent.polito.it E.Richiardone [email protected] maggio 2009 CC-by http://creativecommons.org/licenses/by/2.5/it/ The FreeBSD project - 1 ·EÁ un progetto software open in parte finanziato ·Lo scopo eÁ mantenere e sviluppare il sistema operativo FreeBSD ·Nasce su CDROM come FreeBSD 1.0 nel 1993 ·Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 ·Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free ·Dalla release 5.0 (2003) assume la struttura che ha oggi ·Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... ·La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 ·Erede di 4.4BSD (eÁ la stessa gente...) ·Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato ·Documentazione ufficiale ben curata ·Licenza molto permissiva, spesso attrae aziende per progetti commerciali: ·saltuariamente esterni collaborano con implementazioni ex-novo (i.e. Intel, GEOM, atheros, NDISwrapper, ZFS) ·a volte no (i.e. Windows NT) ·Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: ·Un sistema base ·Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali ·Sorgenti completi in /usr/src (~500MB) ·EÁ giaÁ abbastanza completo (i.e. ipfw, ppp, bind, ...) ·Un sistema di gestione per software aggiuntivo ·Ports e packages ·Documentazione, canali di assistenza, strumenti di sviluppo ·i.e. Handbook, -

Wireless Authentication
Wireless Authentication Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Overview Define authentication Strengths and weaknesses of captive portals How captive portals work What is Authentication? Verifying the claim that an entity is allowed to act on behalf of a given known identity More simply: • Is this person/device who they say they are? • Can they prove it • for example, with password, signature? • In our case, the entity is the software, acting on behalf of the user controlling the computer. Why Is Auth So Complicated? I am on a computer. Am I its owner? • Device is not the same as person. I am a network administrator • Should I have access to the finance system? I am connecting to the network from home • Should I have access to all my work resources? I am a printer • Should I be able to scp files to the network? Authentication Core Concepts These are all different concepts: • Confidentiality • Access Control • Authorization • Authentication Confidentiality Ensure that only those who should have access to information can indeed do so (usually encryption) Access Control Access control is the mechanisms by which rights & restrictions are controlled & enforced Authorization Authorization defines what an entity (a user, a device) is authorized (allowed), to access • Which networks (ACLs/filters) • Which systems, which files ? (FS ACLs, permissions) • When can they do that (time policies) ? • Can they run an application or access a service ? Authentication We want to know: WHO, WHERE(*), WHEN • Which entity? • What AP did they associate with? • When did they log on ? • What IP number did they have? PSK (Pre-Shared Key) cannot tell us this. -

Discontinued Browsers List
Discontinued Browsers List Look back into history at the fallen windows of yesteryear. Welcome to the dead pool. We include both officially discontinued, as well as those that have not updated. If you are interested in browsers that still work, try our big browser list. All links open in new windows. 1. Abaco (discontinued) http://lab-fgb.com/abaco 2. Acoo (last updated 2009) http://www.acoobrowser.com 3. Amaya (discontinued 2013) https://www.w3.org/Amaya 4. AOL Explorer (discontinued 2006) https://www.aol.com 5. AMosaic (discontinued in 2006) No website 6. Arachne (last updated 2013) http://www.glennmcc.org 7. Arena (discontinued in 1998) https://www.w3.org/Arena 8. Ariadna (discontinued in 1998) http://www.ariadna.ru 9. Arora (discontinued in 2011) https://github.com/Arora/arora 10. AWeb (last updated 2001) http://www.amitrix.com/aweb.html 11. Baidu (discontinued 2019) https://liulanqi.baidu.com 12. Beamrise (last updated 2014) http://www.sien.com 13. Beonex Communicator (discontinued in 2004) https://www.beonex.com 14. BlackHawk (last updated 2015) http://www.netgate.sk/blackhawk 15. Bolt (discontinued 2011) No website 16. Browse3d (last updated 2005) http://www.browse3d.com 17. Browzar (last updated 2013) http://www.browzar.com 18. Camino (discontinued in 2013) http://caminobrowser.org 19. Classilla (last updated 2014) https://www.floodgap.com/software/classilla 20. CometBird (discontinued 2015) http://www.cometbird.com 21. Conkeror (last updated 2016) http://conkeror.org 22. Crazy Browser (last updated 2013) No website 23. Deepnet Explorer (discontinued in 2006) http://www.deepnetexplorer.com 24. Enigma (last updated 2012) No website 25. -

2013 State of Media
UNDERSTANDING GROWTH TARGETING THE NEW MOBILE AUDIOAND FRAGMENTATION 26 CONSUMER82 STATE OF MEDIA 2013 ANALYTICS DEATH OF BIG DATA, RISE OF SMART DATA 68 ESPN: End of an Empire? 34 02 VIDEO EVERYWHERE FACT, FICTION & FUTURE Letter from the President For me, working in the discussions that will continue this industry has to drive growth and progress. always been an exciting adventure. Offline and online are cohabitating It still is to this now more than ever to earn day. Nevertheless, viewers’ time, so let’s examine the continuous shakeup of content and provider advancements models. Today technologies like in the media Dish Network’s Hopper and landscape Aereo (page 6) are stirring the can make pot, but tomorrow, who knows? our jobs and the task of tracking I also happen to be a tablet addict, trends a challenging endeavor. so it’s been enjoyable to see my These rapid changes are what favorite magazines adapting to the encouraged us to write our very ever-increasing push for crossover first STATE OF MEDIA (SOM) content (page 22). This process has four years ago, and I am proud to already made for some truly creative say our mission to keep business uses of the medium and I can’t wait partners, clients, new friends and to see what’s next. Again, it all ourselves informed has successfully reminds me that we should dispel continued to this day. Now, just the premonitions and instead look like the industry in which we work, at the opportunities a more unified KSM is evolving our publication media ecosystem will produce. -

M0n0wall and PPTP Preface
M0n0wall and PPTP December 8, 2003 Version 1.0 Francisco Artes [email protected] Preface: ............................................................................................................................... 1 Audience: ............................................................................................................................ 1 Assumptions:....................................................................................................................... 2 Subnetting and VLAN routing:........................................................................................... 2 Setup of m0n0wall software: .............................................................................................. 3 PPTP User Setup:................................................................................................................5 PPTP Firewall Rules:.......................................................................................................... 6 Example of filtered PPTP Rules: .................................................................................... 9 Setting up a PPTP Client on Windows XP™:................................................................... 11 Testing our PPTP Connection in Windows ™: ............................................................ 14 Some things I have found not to work over the PPTP Connection: ................................. 17 Preface: This document is intended to outline several different PPTP VPN type setups, it includes a how-to on setting up a -
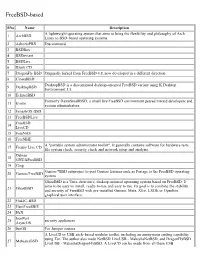
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

Before the Web There Was Gopher
Before the Web There Was Gopher Philip L. Frana Charles Babbage Institute The World Wide Web, universally well known today, was preceded by an efficient software tool that was fondly named Gopher. The Internet Gopher, much like the Web, enabled users to obtain information quickly and easily. Why, then, did it disappear but the Web did not? Gopher faded into obscurity for two main reasons: hypertext and commerce. Before the Web there was Gopher, a nearly anymore, despite the efforts of a handful of defunct Internet application protocol and asso- individuals to revitalize the protocol. Why did ciated client and server software.1 In the early Gopher fail? Many Gopher aficionados have a 1990s, Gopher burrowed a crucial path ready answer: pretty pictures. For them, the through a perceived bottleneck on the Web won and Gopher lost because the Web Information Superhighway. Internet Gopher could display vibrant images of, for example, passed away as a technological and social phe- hand-woven Turkish rugs, animated glyphs of nomenon quickly: Its inventors released mice stuffing email into virtual mailboxes, and Gopher in 1991. Within three years, the World blinking advertising banners. Clearly, the Wide Web had bypassed it. Most people who “Gopher faithful”—as they are often called— surf the Web today have no idea what Gopher are right about the importance of pictures. is, but in the 1990s it helped usher in a new age People get serious when money is at stake, and of user-friendly access to a rapidly growing uni- in the early 1990s lots of people came to accept verse of online information. -

How to Accelerate Your Internet
How To Accelerate Your Internet A practical guide to Bandwidth Management and Optimisation using Open Source Software How To Accelerate Your Internet For more information about this project, visit us online at http://bwmo.net/ Editor: Flickenger R. Associate Editors: Belcher M., Canessa E., Zennaro M. Publishers: INASP/ICTP © 2006, BMO Book Sprint Team First edition: October 2006 ISBN: 0-9778093-1-5 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibil- ity for errors or omissions. No liability is assumed for incidental or consequen- tial damages in connection with or arising out of the use of the information con- tained herein. This work is released under the Creative Commons Attribution-ShareAlike 2.5 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/2.5/ Contents Preface ix About This Book xi Introduction 1 Bandwidth, throughput, latency, and speed.............................................................................. 2 Not enough to go around........................................................................................................ -

Why Websites Can Change Without Warning
Why Websites Can Change Without Warning WHY WOULD MY WEBSITE LOOK DIFFERENT WITHOUT NOTICE? HISTORY: Your website is a series of files & databases. Websites used to be “static” because there were only a few ways to view them. Now we have a complex system, and telling your webmaster what device, operating system and browser is crucial, here’s why: TERMINOLOGY: You have a desktop or mobile “device”. Desktop computers and mobile devices have “operating systems” which are software. To see your website, you’ll pull up a “browser” which is also software, to surf the Internet. Your website is a series of files that needs to be 100% compatible with all devices, operating systems and browsers. Your website is built on WordPress and gets a weekly check up (sometimes more often) to see if any changes have occured. Your site could also be attacked with bad files, links, spam, comments and other annoying internet pests! Or other components will suddenly need updating which is nothing out of the ordinary. WHAT DOES IT LOOK LIKE IF SOMETHING HAS CHANGED? Any update to the following can make your website look differently: There are 85 operating systems (OS) that can update (without warning). And any of the most popular roughly 7 browsers also update regularly which can affect your site visually and other ways. (Lists below) Now, with an OS or browser update, your site’s 18 website components likely will need updating too. Once website updates are implemented, there are currently about 21 mobile devices, and 141 desktop devices that need to be viewed for compatibility. -

Introduzione Al Mondo Freebsd Corso Avanzato
Introduzione al mondo FreeBSD corso Avanzato •Struttura •Installazione •Configurazione •I ports •Gestione •Netstudent http://netstudent.polito.it •E.Richiardone [email protected] •Novembre 2012 •CC-by http://creativecommons.org/licenses/by/3.0/it/ The FreeBSD project - 1 • E` un progetto software open • Lo scopo e` mantenere e sviluppare il sistema operativo FreeBSD • Nasce su CDROM come FreeBSD 1.0 nel 1993 • Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 • Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free • Dalla release 4.0 (2000) assume la struttura che ha oggi • Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... • La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 • Erede di 4.4BSD (e` la stessa gente...) • Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato • Documentazione ufficiale ben curata • Licenza molto permissiva, spesso attrae aziende per progetti commerciali: • saltuariamente progetti collaborano con implementazioni ex-novo (i.e. Intel, GEOM, NDISwrapper, ZFS, GNU/Linux emulation) • Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: • Un sistema base • Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali • Sorgenti completi in /usr/src (~500MB) • E` gia` completo (i.e. ipfw, ppp, bind, ...) • Un sistema di gestione per software aggiuntivo • Ports e packages • Documentazione, canali di assistenza, strumenti -

Pare-Feu : Architecture Et Déploiement V1.0
Pare-feu : architecture et déploiement V1.0 Pare-feu : Architecture et déploiement V 1.0 Stéphane DUFOUR (Architecte système et sécurité) - 1 - Pare-feu : architecture et déploiement V1.0 Table des matières PARE-FEU : ARCHITECTURE ET DEPLOIEMENT ..............................................................................................................................0 TABLE DES MATIERES...................................................................................................................................................................2 INTRODUCTION ...........................................................................................................................................................................4 CONCEPTS DE BASE......................................................................................................................................................................5 RAPPEL SECURITE .................................................................................................................................................................................5 Les fondamentaux ......................................................................................................................................................................5 Les menaces ................................................................................................................................................................................6 Best practice .............................................................................................................................................................................16