Guiding Development of Contribution and Community Strategies in Open Source Software Requirements Engineering Linåker, Johan
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Wandisco Fusion® Microsoft Azure Data Box
WANDISCO FUSION® MICROSOFT AZURE DATA BOX Use WANdisco Fusion with Data Box for bulk transfer of changing data WANdisco Fusion is the only solution that enables Microsoft customers to use the bulk transfer capabilities of the Azure Data Box to transfer static and changing Guaranteed data consistency information from Big Data applications to Azure Cloud with guaranteed data consistency. Users can continue to Take advantage of the storage on Azure Data Box for write to their local cluster while the Azure Data Box is in bulk data transfer while continuing to write to a local transit so when the Azure Data Box is subsequently being cluster and replicate those changes while the Azure uploaded, any changes are replicated to the Azure Cloud Data Box is uploaded to the Azure Cloud. with guaranteed consistency. Easy and intuitive step-by-step operation • Applications write to Azure Data Box using the same API that they use to interact with the Azure Cloud. No downtime and • WANdisco Fusion for Azure Data Box requires no change to applications which can continue to use the no business disruption API as they would normally. Write data to a local HDFS-compatible endpoint • Replication is continuous and recovers from on-premises and replicate to a storage location in intermittent network or system failures automatically. Microsoft Azure with no modification or disruption to applications on-premises. AZURE 2 STORAGE Cost saving MICROSOFT 1 3 AZURE DATA BOX Avoid the high network costs common to large scale data transfers and benefit from a range of FUSION applications available in Azure Cloud. -

Participating Organisations | June 2021 Aon Rewards Solutions Proprietary and Confidential
Aon Rewards Solutions Proprietary and Confidential Participating organisations | June 2021 Aon Rewards Solutions Proprietary and Confidential Participating organisations 1. .au Domain Administration 44. Alexion Pharmaceuticals Limited Australasia Pty Ltd 2. [24]7.ai 45. Alfa Financial Software 3. 10X Genomics* Limited 4. 4 Pines Brewing Company 46. Alibaba Group Inc 5. 8X8 47. Alida* 6. A.F. Gason Pty Ltd* 48. Align Technology Inc. 7. A10 Networks 49. Alkane Resources Limited 8. Abacus DX 50. Allianz Australia Ltd 9. AbbVie Pty Ltd 51. Allscripts 10. Ability Options Ltd 52. Alteryx 11. Abiomed* 53. Altium Ltd 12. AC3 54. Amazon.com 55. AMEC Foster Wheeler 13. ACCELA* Australia Pty Ltd 14. Accenture Australia Ltd 56. Amgen Australia Pty Ltd 15. AccorHotels 57. AMP Services Limited 16. Acer Computer Australia Pty Ltd* 58. AMSC 17. Achieve Australia Limited* 59. Analog Devices 18. Achmea Australia 60. Anaplan 19. ACI Worldwide 61. Ancestry.com 62. Anglo American Metallurgical 20. Acquia Coal Pty Ltd 21. Actian Corporation 63. AngloGold Ashanti Australia 22. Activision Blizzard Limited* 23. Adaman Resources 64. ANZ Banking Group Ltd 24. Adcolony 65. Aon Corporation Australia 25. A-dec Australia 66. APA Group 26. ADG Engineers* 67. Apollo Endosurgery Inc. 27. Adherium Limited 68. APPEN LTD 28. Administrative Services 69. Appian* 29. Adobe Systems Inc 70. Apple and Pear Australia Ltd* 30. ADP 71. Apple Pty Ltd 31. Adtran 72. Apptio 32. Advanced Micro Devices 73. APRA AMCOS 33. Advanced Sterlization 74. Aptean Products* 75. Aptos* 34. AECOM* 76. Apttus 35. AEMO 77. Aquila Resources 36. Aeris Resources Limited 78. Arcadis 37. -

Wandisco Plc Annual Report and Accounts 2020.Pdf
WANdisco plc Annual Report and Accounts 2020 WANdisco is the LiveData company WANdisco solutions enable enterprises to create an environment where data is always available, accurate and protected, creating a strong backbone for their IT infrastructure and a bedrock for running consistent, accurate machine learning applications. With zero downtime and zero data loss, WANdisco’s products keep geographically dispersed data at any scale consistent between on-premises and cloud environments allowing businesses to operate seamlessly in a hybrid or multi-cloud environment. WANdisco has over a hundred customers and significant go-to-market partnerships with Microsoft Azure, Amazon Web Services, Google Cloud, Oracle, and others, as well as OEM relationships with IBM and Alibaba. Learn more about our solutions from page 4 Reasons to invest in WANdisco Contents Overview Innovative technology Significant opportunity 02 Our year in review Our technology is based on a Our addressable market is expanding 04 WANdisco at a glance patented, high-performance coordination engine Strategic report $1bn– 06 Chairman and Chief Executive’s report 08 Our markets $9.0m $1.5bn 12 Our business model development spend total addressable market 14 Our partnerships and technology Learn more about our innovative Learn more about our significant 16 Our strategy technology from page 12 opportunity from page 9 20 Key performance indicators 22 Risks 26 Financial review 28 Sustainability Corporate governance 32 Board of Directors 34 Executive Team 36 Vice Chairman’s introduction -

Tortoisesvn Mac Os X Download
Tortoisesvn Mac Os X Download Tortoisesvn Mac Os X Download 1 / 4 2 / 4 Centos Linux ¶CentOS project (client and server) CollabNet (supported and certified by CollabNet; requires registration) WANdisco (supported and certified by WANdisco; requires registration)Debian Linux ¶Svn MacDebian Project (maintained by Debian Project; client and server; svnserve is part of the subversion package, mod_dav_svn is in the separate libapache2-mod- svn package (formerly libapache2-svn)) WANdisco (supported and certified by WANdisco; requires registration)Fedora Linux ¶FreeBSD ¶Tortoisesvn Download Windows 10HP-UX ¶.. 4 x svn/1 5 x svn from SVN This is the currently supported build preference on OS X and is also subject to a different licence to the rest of the wiki.. Note that binary packages usually come out about a week after the corresponding source release. 1. tortoisesvn 2. tortoisesvn tutorial 3. tortoisesvn command line As such, the listing here is limited to those packages which may be reasonably considered binary distributions of Apache Subversion alone. tortoisesvn tortoisesvn, tortoisesvn download, tortoisesvn tutorial, tortoisesvn mac, tortoisesvn create branch, tortoisesvn command line, tortoisesvn repository, tortoisesvn repository browser, tortoisesvn commit, tortoisesvn portable, tortoisesvn undo commit, tortoisesvn create repository Picmonkey Free Download For Mac Several vendors offer such things, but we concern ourselves primarily with Subversion itself.. Please don't post to the mailing lists asking when a binary package for a given -
![Wandisco Plc Wandisco Finals: [Epub Ahead of Print]](https://docslib.b-cdn.net/cover/4326/wandisco-plc-wandisco-finals-epub-ahead-of-print-2144326.webp)
Wandisco Plc Wandisco Finals: [Epub Ahead of Print]
WANdisco plc WAND – LSE; WAND.L March 7, 2018 European Software & IT Services BUY COMPANY UPDATE WANdisco Finals: [epub ahead of print] Price (6 March 2018) 755p Summary Changes Previous Current Rating - BUY WANdisco brings some California sparkle to a dank London morning with its FY2017A Target Price 1,067p 1,081p results. WANdisco pre-announced (16 January) that it had exceeded our bookings forecasts, today we see revenue, Adj EBITDA and cash all crush expectations. The start- Key data turn was ‘Fusion’ with bookings +121% YoY to US$15.7m, (iii) Average Contract Value Bloomberg/Reuters codes: WAND LN / WAND.L continues to increase, with several US$1m+ contracts and, (iii) cash overheads were Market cap (£m) 251 contained at US$24.5m, from US$23.4m Y/Y. As we factor in cash burn down to US$5.3m, FTSE ALL SHARE 3,946 US$8.3m Y/Y this is a blue riband performance, and the third beat & raise from CFO 1mth perf (%) 6.0 Erik Miller. As we bake these results into our forecasts we raise 2018E revenue from US 3mths perf (%) 28.0 $21.9m to US$24.46m and Adj EBITDA from US$1.0m to US$1.28m – savour that profit. 12mths perf (%) 48.0 Whilst it is easy to get carried away with the numbers, in truth we are more impressed 12mth high-low (p) 890 - 362 by CEO Mr Richards: (i) ability to drive a deep transformation while ensuring the integrity Free float (%) 75 of the deep technical skill base (R&D spend US$6.3m, US$5.9m Y/Y). -

Wandisco Fusion® Amazon S3
WANDISCO FUSION® AMAZON S3 Seamless cloud migration and hybrid cloud WANdisco Fusion is the only solution that seamlessly moves transactional data to Amazon S3 as it changes in on-premise local and NFS S3 mounted file systems, Hadoop clusters and other cloud environments. WANdisco Fusion’s patented Active Transactional Data Replication™ captures every change and supports hybrid cloud FUSION use cases for on-demand burst-out processing, data archiving and offsite disaster recovery (DR) with no downtime and no data loss. FUSION FUSION No migration downtime S3 and on-premise environments operate in parallel during migration, allowing data, applications and users to move in phases HADOOP without disrupting normal operations. LOCAL AND NFS MOUNTED Guaranteed data consistency FILE SYSTEMS Amazon S3, on-premise storage and other cloud environments stay continuously in sync with LAN-speed read/write access Automatic recovery to the same data at every location. Recovery is automatic after planned or unplanned network or hardware outages in both on-premise and S3 environments. Easy and intuitive Simple setup in both on-premise and S3 environments using AWS Marketplace Cloud Formation Templates gets the software up and running in minutes. Its intuitive admin console for monitoring, scheduling and audit further simplifies the process. Copyright © 2016 WANdisco, Inc. All rights reserved. About WANdisco WANdisco (LSE: WAND) is the world leader in Active Transactional Data Replication™. Its patented technology provides continuous consistent access to changing data anytime and anywhere with no downtime and no disruption. WANdisco’s patented technology serves crucial high availability (HA) requirements, including FREE 14 DAY TRIAL cloud migration, Hadoop Big Data and Application Experience the benefits of Fusion’s Lifecycle Management (ALM), including Subversion, Amazon S3 Migrator before you buy Git and Gerrit. -

Wandisco Fusion® Subversion Multisite Plus
FUSION WANDISCO FUSION® SUBVERSION MULTISITE PLUS Reliability and productivity WANdisco Subversion Multisite Plus (MSP), using our game-changing patented technology, is a hardened service for replicating Subversion repositories around the world to enable fast, low latency, read and write access by a global development community. Guaranteed data consistency Repository byte-for-byte consistency is maintained by applying low-level Subversion transactions in the same order at all repository replicas. Automatic recovery Sites that are offline during transactions are automatically recovered when they return to service. No administrator No Subversion client modifications necessary intervention is required. MSP enables your developers to continue to use their favorite Subversion clients without change. Efficient Configurable redundancy versioning of both text and binary images fully supported. Only build and pay for what you need. Apache and “svnserve” support Cost savings and ROI Server-side MSP supports Subversion access via either Studies show MSP delivers triple digit ROI and millions in Apache or “svnserve” (or both). No proxies required: every cost savings during the first year of use*. site is writable! Integrated with Enterprise Security LDAP and Kerberos Authorities suported. Powerful “selective replication” You easily select where each repository is replicated for maximum control of your environment. Network efficient No WAN traffic for repository read operations. Repository update data is compressed before sharing via the WAN. Immediate -

Wandisco Fusion® Google Cloud
FUSION WANDISCO FUSION® GOOGLE CLOUD Seamless cloud migration and hybrid cloud WANdisco Fusion is the only solution that seamlessly moves active data to Google Cloud as it changes in on- premises local and NFS mounted file systems, Hadoop GOOGLE CLOUD clusters and other cloud environments. Our game- changing, patented technology captures every change and supports hybrid cloud use cases for on-demand burst-out processing, data archiving and offsite disaster recovery with no downtime and no data loss. No migration downtime FUSION Google Cloud and on-premises environments operate in parallel during migration, allowing data, applications and users to move in phases without disrupting normal operations. FUSION FUSION Guaranteed data consistency Google Cloud, on-premises storage and other cloud environments stay continuously in sync with LAN-speed read/write access to the same data at every location. HADOOP Automatic recovery LOCAL AND Recovery is automatic after planned or unplanned NFS MOUNTED FILE SYSTEMS network or hardware outages in both on-premises and Google Cloud environments. Easy and intuitive Simple setup in both on-premises and cloud environments using the Google Cloud Platform Templates gets the software up and running in minutes. Its intuitive admin console for monitoring, scheduling and audit further simplifies the process. Copyright © 2019 WANdisco, Inc. All rights reserved. Supported environments Hadoop Cloud • Amazon EMR • Amazon • Cloudera CDH • Alibaba Cloud • Google Cloud • Google Cloud™ Dataproc • Microsoft Azure® • Hortonworks -

The World Leader in Active Data Replication
WANDISCO PLC ANNUAL REPORT AND ACCOUNTS 2016 The World Leader in Active Data Replication WANDISCO PLC ANNUAL REPORT AND ACCOUNTS 2016 In this report OVERVIEW 02 Financial and operational highlights 03 Our year in review 04 At a glance STRATEGIC REPORT 06 Interim Chairman and Chief Executive’s report 08 Our markets 10 Our strategy 11 Key performance indicators 12 Our business model 13 Our products in action 15 Our partners 16 Risks 19 Financial review 21 Our people GOVERNANCE 22 Board of Directors 24 Chairman’s introduction to governance 25 Corporate governance report 28 Audit Committee report 29 Nomination Committee report 30 Remuneration Committee and remuneration report 32 Directors’ report 34 Statement of Directors’ responsibilities FINANCIAL STATEMENTS 35 Independent auditor’s report 36 Consolidated statement of profit and loss and other comprehensive income 37 Consolidated balance sheet 38 Consolidated statement of changes in equity 39 Consolidated statement of cash flows 40 Notes to the consolidated financial statements 61 Five year record 62 Notice of Annual General Meeting 65 Secretary, advisers and share capital information TO STAY UP TO DATE WITH ALL THE LATEST NEWS VISIT WWW.WANDISCO.COM Patented technology created by the best and the brightest WANdisco is the world leader in Active Data Replication™. Our patented technology enables the replication of continuously changing data to the cloud and on-premises data centres with guaranteed consistency, no downtime and no business disruption. It also allows distributed development teams to collaborate as if they were all working at one location as software development projects are tracked in real time. -

Wandisco Fusion® for Cloud Migration
WANDISCO FUSION® FOR CLOUD MIGRATION Migrate active data to the cloud Always accurate Imagine being able to move continuously changing data anywhere, anytime and always. We imagined the same On-premises and cloud environments stay and made it happen. With WANdisco Fusion you can continuously in sync with automated recovery after migrate large volumes of continuously changing data to an outage. the cloud in real-time with guaranteed consistency, no downtime and no business disruption. Increase productivity, profitability and security with our game-changing, patented active replication technology. Benefits of our patented technology Always available • Move large volumes of continuously changing Cloud and on-premises environments operate in data between any WANdisco Fusion supported parallel during migration allowing data, applications on-premises and cloud environment with no and users to move in phases with no disruption to data loss and no downtime. normal operations. • Use the cloud as an extension of your on-premises data centers with guaranteed data consistency in both locations. • Ingest and replicate streaming data from multiple sources and locations simultaneously with guaranteed consistency. Lower cost structure • Keep sensitive data where it belongs to remain compliant with data security and privacy Leverage economies of scale offered by the cloud protection regulations. through a range of analytics applications that would be impossible to deploy in-house. • Simple set up and our intuitive admin console has you up and running in minutes. Cloud computing has been one of the most exciting and disruptive forces in the tech market in the past decade. FORRESTER RESEARCH 2016 Copyright © 2018 WANdisco, Inc. -

Wandisco Plc FY Update... 'Hit 'Em with the Fusion, Nah'
WANdisco plc WAND – LSE; WAND.L January 16, 2018 European Software & IT Services BUY COMPANY UPDATE FY update... ‘Hit 'em with the fusion, nah’ Price (15 January 2018) 830p Summary Changes Previous Current Rating - BUY WANdisco smashes our 2017 forecast with bookings, +45% YoY to US$22.5m – besting Target Price 1,062p 1,067p our US$20.8m estimate. The start-turn was ‘Fusion’ where bookings are +121% YoY to US$15.7m - we had expected US$12.6m. Also, CFO Erik Miller continues to delight on Key data cash, US$27.4m, ahead of estimates. Whilst WANdisco did not disclose to revenue or Bloomberg/Reuters codes: WAND LN / WAND.L EBITDA detail we elected to make small upgrades as we ‘bake-in’ the bookings beat. Market cap (£m) 276 Net/net we raise 2017E revenue from US$16.8m to US$18.6m and Adj EBITDA from - FTSE ALL SHARE 4,264 US$2.4m to -US$1.79m. Whilst it is easy to get carried away with the numbers beat in 1mth perf (%) 45.6 truth we are more impressed by the CEO Mr Richards commentary that “. there has 3mths perf (%) (3.8) been a transformation at WANdisco which started when we launched our core WANdisco 12mths perf (%) 270.5 Fusion product ‘. With this we are reminded that Mr Richards has, by evolving Fusion as 12mth high-low (p) 890 - 246 a general data replication platform (i.e. this is no longer the Hadoop-play) he has created Free float (%) 75 shareholder value 'in the moment' and for the long term as Fusion maps onto a changing market. -
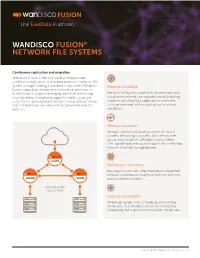
Wandisco Fusion® Network File Systems
FUSION WANDISCO FUSION® NETWORK FILE SYSTEMS Continuous replication and migration WANdisco Fusion is the only solution that provides continuous replication of changing data from Network File System storage, making it available in any other WANdisco Always available Fusion supported storage environment on-premises or in the cloud. Our game-changing, patented technology Network File Systems and other on-premises and captures every change and supports hybrid cloud use cloud environments can operate in parallel during cases for on-demand burst-out processing, data archiving migration allowing data, applications and users and offsite disaster recovery with no downtime and no to move in phases with no disruption to normal data loss. operations. Always accurate Storage systems can share access to the same content, remaining consistent with one another across every location. WANdisco Fusion offers LAN-speed read/write access optimized for NetApp network attached storage devices. FUSION Automatic recovery Recovery is automatic after planned or unplanned network or hardware outages in both on-premises FUSION FUSION and cloud environments. NFS MOUNTED FILE SYSTEMS Easy and intuitive Simple set up gets the software up and running in minutes. Our intuitive console for monitoring, scheduling and audit further simplifies the process. Copyright © 2019 WANdisco, Inc. All rights reserved. Supported environments Hadoop Cloud • Amazon EMR • Amazon • Cloudera CDH • Alibaba Cloud • Google Cloud • Google Cloud™ Dataproc • Microsoft Azure® • Hortonworks (HDP)