* "What Tech Skills Are Hot for 2006
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Strider Web Security
Adversarial Web Crawling with Strider Monkeys Yi-Min Wang Director, Cyber-Intelligence Lab Internet Services Research Center (ISRC) Microsoft Research Search Engine Basics • Crawler – Crawling policy • Page classification & indexing • Static ranking • Query processing • Document-query matching & dynamic ranking – Diversity • Goals of web crawling – Retrieve web page content seen by browser users – Classify and index the content for search ranking • What is a monkey? – Automation program that mimics human user behavior Stateless Static Crawling • Assumptions – Input to the web server: the URL • Stateless client – Output from the web server: page content in HTML • Static crawler ignores scripts Stateful Static Crawling • We all know that Cookies affect web server response • HTTP User-Agent field affects response too – Some servers may refuse low-value crawlers – Some spammers use crawler-browser cloaking • Give crawlers a page that maximizes ranking (=traffic) • Give users a page that maximizes profit Dynamic Crawling • Simple crawler-browser cloaking can be achieved by returning HTML with scripts – Crawlers only parse static HTML text that maximizes ranking/traffic – Users’ browsers additionally execute the dynamic scripts that maximize profit • Usually redirect to a third-party domain to server ads • Need browser-based dynamic crawlers to index the true content Search Spam Example: Google search “coach handbag” Spam Doorway URL = http://coach-handbag-top.blogspot.com http://coach-handbag-top.blogspot.com/ script execution led to redirection -

Summary of U.S. Foreign Intelligence Surveillance Law, Practice, Remedies, and Oversight
___________________________ SUMMARY OF U.S. FOREIGN INTELLIGENCE SURVEILLANCE LAW, PRACTICE, REMEDIES, AND OVERSIGHT ASHLEY GORSKI AMERICAN CIVIL LIBERTIES UNION FOUNDATION AUGUST 30, 2018 _________________________________ TABLE OF CONTENTS QUALIFICATIONS AS AN EXPERT ............................................................................................. iii INTRODUCTION ......................................................................................................................... 1 I. U.S. Surveillance Law and Practice ................................................................................... 2 A. Legal Framework ......................................................................................................... 3 1. Presidential Power to Conduct Foreign Intelligence Surveillance ....................... 3 2. The Expansion of U.S. Government Surveillance .................................................. 4 B. The Foreign Intelligence Surveillance Act of 1978 ..................................................... 5 1. Traditional FISA: Individual Orders ..................................................................... 6 2. Bulk Searches Under Traditional FISA ................................................................. 7 C. Section 702 of the Foreign Intelligence Surveillance Act ........................................... 8 D. How The U.S. Government Uses Section 702 in Practice ......................................... 12 1. Data Collection: PRISM and Upstream Surveillance ........................................ -

Limitless Surveillance at the Fda: Pro- Tecting the Rights of Federal Whistle- Blowers
LIMITLESS SURVEILLANCE AT THE FDA: PRO- TECTING THE RIGHTS OF FEDERAL WHISTLE- BLOWERS HEARING BEFORE THE COMMITTEE ON OVERSIGHT AND GOVERNMENT REFORM HOUSE OF REPRESENTATIVES ONE HUNDRED THIRTEENTH CONGRESS SECOND SESSION FEBRUARY 26, 2014 Serial No. 113–88 Printed for the use of the Committee on Oversight and Government Reform ( Available via the World Wide Web: http://www.fdsys.gov http://www.house.gov/reform U.S. GOVERNMENT PRINTING OFFICE 87–176 PDF WASHINGTON : 2014 For sale by the Superintendent of Documents, U.S. Government Printing Office Internet: bookstore.gpo.gov Phone: toll free (866) 512–1800; DC area (202) 512–1800 Fax: (202) 512–2104 Mail: Stop IDCC, Washington, DC 20402–0001 VerDate Aug 31 2005 11:40 Mar 31, 2014 Jkt 000000 PO 00000 Frm 00001 Fmt 5011 Sfmt 5011 C:\DOCS\87176.TXT APRIL COMMITTEE ON OVERSIGHT AND GOVERNMENT REFORM DARRELL E. ISSA, California, Chairman JOHN L. MICA, Florida ELIJAH E. CUMMINGS, Maryland, Ranking MICHAEL R. TURNER, Ohio Minority Member JOHN J. DUNCAN, JR., Tennessee CAROLYN B. MALONEY, New York PATRICK T. MCHENRY, North Carolina ELEANOR HOLMES NORTON, District of JIM JORDAN, Ohio Columbia JASON CHAFFETZ, Utah JOHN F. TIERNEY, Massachusetts TIM WALBERG, Michigan WM. LACY CLAY, Missouri JAMES LANKFORD, Oklahoma STEPHEN F. LYNCH, Massachusetts JUSTIN AMASH, Michigan JIM COOPER, Tennessee PAUL A. GOSAR, Arizona GERALD E. CONNOLLY, Virginia PATRICK MEEHAN, Pennsylvania JACKIE SPEIER, California SCOTT DESJARLAIS, Tennessee MATTHEW A. CARTWRIGHT, Pennsylvania TREY GOWDY, South Carolina TAMMY DUCKWORTH, Illinois BLAKE FARENTHOLD, Texas ROBIN L. KELLY, Illinois DOC HASTINGS, Washington DANNY K. DAVIS, Illinois CYNTHIA M. LUMMIS, Wyoming PETER WELCH, Vermont ROB WOODALL, Georgia TONY CARDENAS, California THOMAS MASSIE, Kentucky STEVEN A. -

Congressional Correspondence
People Record 7006012 for The Honorable Peter T. King Help # ID Opened � WF Code Assigned To Template Due Date Priority Status 1 885995 11/3/2010 ESLIAISON4 (b)(6) ESEC Workflow 11/10/2010 9 CLOSED FEMA Draft Due to ESEC: 11/10/2010 ESEC Case Number (ESEC Use Only): 10-9970 To: Secretary Document Date: 10/25/2010 *Received Date: 11/03/2010 *Attachment: Yes Significant Correspondence (ESEC Use Only): Yes *Summary of Document: Write in support of the application submitted by the (b)(4) for $7,710,089 under the Staffing for Adequate Fire and Emergency Response grant program. *Category: Congressional *Type: Congressional - Substantive Issue *Action to be Taken: Assistant Secretary OLA Signature Status: Action: *Lead Component: FEMA *Signed By (ESEC Use Only): Component Reply Direct and cc: *Date Response Signed: 11/02/2010 Action Completed: 11/04/2010 *Complete on Time: Yes Attachments: 10-9970rcuri 10.25.10.pdf Roles: The Honorable Michael Arcuri(Primary, Sender), The Honorable Timothy H. Bishop(Sender) 2 884816 10/22/2010 ESLIAISON4 (b)(6) ESEC Workflow 11/5/2010 9 OPEN FEMA Reply Direct Final Due Date: 11/05/2010 ESEC Case Number (ESEC Use Only): 10-9776 To: Secretary Mode: Fax Document Date: 10/20/2010 *Received Date: 10/22/2010 *Attachment: Yes Significant Correspondence (ESEC Use Only): No *Summary of Document: Requests an Urban Area Security Initiative designation for seven southern San Joaquin Valley Counties. *Category: Congressional *Type: Congressional - Substantive Issue *Action to be Taken: Component Reply Direct and Cc: Status: -

GLOBAL CENSORSHIP Shifting Modes, Persisting Paradigms
ACCESS TO KNOWLEDGE RESEARCH GLOBAL CENSORSHIP Shifting Modes, Persisting Paradigms edited by Pranesh Prakash Nagla Rizk Carlos Affonso Souza GLOBAL CENSORSHIP Shifting Modes, Persisting Paradigms edited by Pranesh Pra ash Nag!a Ri" Car!os Affonso So$"a ACCESS %O KNO'LE(GE RESEARCH SERIES COPYRIGHT PAGE © 2015 Information Society Project, Yale Law School; Access to Knowle !e for "e#elo$ment %entre, American Uni#ersity, %airo; an Instituto de Technolo!ia & Socie a e do Rio+ (his wor, is $'-lishe s'-ject to a %reati#e %ommons Attri-'tion./on%ommercial 0%%.1Y./%2 3+0 In. ternational P'-lic Licence+ %o$yri!ht in each cha$ter of this -oo, -elon!s to its res$ecti#e a'thor0s2+ Yo' are enco'ra!e to re$ro 'ce, share, an a a$t this wor,, in whole or in part, incl' in! in the form of creat . in! translations, as lon! as yo' attri-'te the wor, an the a$$ro$riate a'thor0s2, or, if for the whole -oo,, the e itors+ Te4t of the licence is a#aila-le at <https677creati#ecommons+or!7licenses7-y.nc73+07le!alco e8+ 9or $ermission to $'-lish commercial #ersions of s'ch cha$ter on a stan .alone -asis, $lease contact the a'thor, or the Information Society Project at Yale Law School for assistance in contactin! the a'thor+ 9ront co#er ima!e6 :"oc'ments sei;e from the U+S+ <m-assy in (ehran=, a $'-lic omain wor, create by em$loyees of the Central Intelli!ence A!ency / em-assy of the &nite States of America in Tehran, de$ict. -

Escape from Monkey Island: ? Evading High-Interaction Honeyclients
Escape from Monkey Island: ? Evading High-Interaction Honeyclients Alexandros Kapravelos1, Marco Cova2, Christopher Kruegel1, Giovanni Vigna1 1 UC Santa Barbara {kapravel,chris,vigna}@cs.ucsb.edu 2 University of Birmingham, UK {m.cova}@cs.bham.ac.uk Abstract. High-interaction honeyclients are the tools of choice to detect mali- cious web pages that launch drive-by-download attacks. Unfortunately, the ap- proach used by these tools, which, in most cases, is to identify the side-effects of a successful attack rather than the attack itself, leaves open the possibility for malicious pages to perform evasion techniques that allow one to execute an at- tack without detection or to behave in a benign way when being analyzed. In this paper, we examine the security model that high-interaction honeyclients use and evaluate their weaknesses in practice. We introduce and discuss a number of possible attacks, and we test them against several popular, well-known high- interaction honeyclients. Our attacks evade the detection of these tools, while successfully attacking regular visitors of malicious web pages. 1 Introduction In a drive-by-download attack, a user is lured into visiting a malicious web page, which contains code that exploits vulnerabilities in the user’s browser and/or its environment. If successful, the exploits can execute arbitrary code on the victim’s machine [33]. This ability is typically used to automatically download and run malware programs on the compromised machine, which, as a consequence, often becomes part of a botnet [31]. Drive-by-download attacks are one of the most pervasive threats on the web, and past measurements have found millions of malicious web pages [3, 32]. -
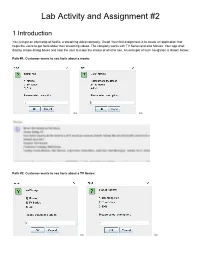
Lab Activity and Assignment #2
Lab Activity and Assignment #2 1 Introduction You just got an internship at Netfliz, a streaming video company. Great! Your first assignment is to create an application that helps the users to get facts about their streaming videos. The company works with TV Series and also Movies. Your app shall display simple dialog boxes and help the user to make the choice of what to see. An example of such navigation is shown below: Path #1: Customer wants to see facts about a movie: >> >> Path #2: Customer wants to see facts about a TV Series: >> >> >> >> Your app shall read the facts about a Movie or a TV Show from text files (in some other course you will learn how to retrieve this information from a database). They are provided at the end of this document. As part of your lab, you should be creating all the classes up to Section 3 (inclusive). As part of your lab you should be creating the main Netfliz App and making sure that your code does as shown in the figures above. The Assignment is due on March 8th. By doing this activity, you should be practicing the concept and application of the following Java OOP concepts Class Fields Class Methods Getter methods Setter methods encapsulation Lists String class Split methods Reading text Files Scanner class toString method Override superclass methods Scanner Class JOptionPane Super-class sub-class Inheritance polymorphism Class Object Class Private methods Public methods FOR loops WHILE Loops Aggregation Constructors Extending Super StringBuilder Variables IF statements User Input And much more.. -

Patrol Guide § 212-72
EXHIBIT K AOR307 An Investigation of NYPD’s Compliance with Rules Governing Investigations of Political Activity New York City Department of Investigation Office of the Inspector General for the NYPD (OIG-NYPD) Mark G. Peters Commissioner Philip K. Eure Inspector General for the NYPD August 23, 2016 AOR308 AN INVESTIGATION OF NYPD’S COMPLIANCE WITH RULES GOVERNING AUGUST 2016 INVESTIGATIONS OF POLITICAL ACTIVITY Table of Contents Overview ............................................................................................................................... 1 Executive Summary ............................................................................................................... 3 Introduction ........................................................................................................................ 11 I. NYPD Investigations of Political Activity: Handschu and Patrol Guide § 212-72 ....... 11 II. OIG-NYPD Investigation .............................................................................................. 12 Methodology and Access ..................................................................................................... 13 I. Treatment of Sensitive Information ............................................................................ 13 II. Compliance Criteria ..................................................................................................... 13 III. Scope and Sampling .................................................................................................... 14 -

Tracking and Mitigation of Malicious Remote Control Networks
Tracking and Mitigation of Malicious Remote Control Networks Inauguraldissertation zur Erlangung des akademischen Grades eines Doktors der Naturwissenschaften der Universität Mannheim vorgelegt von Thorsten Holz aus Trier Mannheim, 2009 Dekan: Prof. Dr. Felix Christoph Freiling, Universität Mannheim Referent: Prof. Dr. Felix Christoph Freiling, Universität Mannheim Korreferent: Prof. Dr. Christopher Krügel, University of California, Santa Barbara Tag der mündlichen Prüfung: 30. April 2009 Abstract Attacks against end-users are one of the negative side effects of today’s networks. The goal of the attacker is to compromise the victim’s machine and obtain control over it. This machine is then used to carry out denial-of-service attacks, to send out spam mails, or for other nefarious purposes. From an attacker’s point of view, this kind of attack is even more efficient if she manages to compromise a large number of machines in parallel. In order to control all these machines, she establishes a malicious remote control network, i.e., a mechanism that enables an attacker the control over a large number of compromised machines for illicit activities. The most common type of these networks observed so far are so called botnets. Since these networks are one of the main factors behind current abuses on the Internet, we need to find novel approaches to stop them in an automated and efficient way. In this thesis we focus on this open problem and propose a general root cause methodology to stop malicious remote control networks. The basic idea of our method consists of three steps. In the first step, we use honeypots to collect information. -

Hakin9 Extra Followers, We [email protected] Are Giving You the Latest Fruit of Our Labour
Szukaj nas takze na www.ashampoo.com Pwn Plug. The Industry’s First Commercial Air Freshener? Pentesting Drop Box. Printer PSU? ...nope FEATURES: % Covert tunneling % SSH access over 3G/GSM cell networks % NAC/802.1x bypass % and more! Discover the glory of Universal Plug & Pwn @ pwnieexpress.com t) @pwnieexpress e) [email protected] p) 802.227.2PWN pwnplug - Dave-ad3-203x293mm.indd 1 1/5/12 3:32 PM To hack or not to hack Managing: Michał Wiśniewski – that is [email protected] the question Senior Consultant/Publisher: Paweł Marciniak Editor in Chief: Grzegorz Tabaka ear Hakin9 Extra Followers, we [email protected] are giving you the latest fruit of our labour. Honeypots are our le- Art Director: itmotiv this month. Especially for Marcin Ziółkowski Dyou, our dear followers, we have selected the choicest articles within the topic of Ho- DTP: neypots/Honeynets. I sincerely hope that we Marcin Ziółkowski sufficiently expanded on the topic to satisfy www.gdstudio.pl your needs and we quenched your appetite for Hakin9 knowledge. I am also very happy Production Director: that we managed to have an exclusive inte- Andrzej Kuca rview with Dr. Fred Cohen – the „father” of [email protected] computer viruses and that, once again, our respected authors helped us with their con- Marketing Director: tributions. This month: Jeremiah Brott will, Grzegorz Tabaka in great detail, tell you about different ty- [email protected] pes of honeypots and their use. Roberto Saia is going to present you „Proactive Network Proofreadres: Defence Through Simulated Networks”. Hari Bob Folden, I. -

An Anthropological Study of Smes in Manchester
“BLOCKS TO CONVERGENCE” IN THE NEW MEDIA INDUSTRIES: AN ANTHROPOLOGICAL STUDY OF SMALL AND MEDIUM SIZED ENTERPRISES IN MANCHESTER A thesis submitted to the University of Manchester for the degree of Doctor of Philosophy in the Faculty of Social Sciences and Law 2003 HANNAH KNOX DEPARTMENT OF SOCIAL ANTHROPOLOGY 1 TABLE OF CONTENTS Table of Figures 3 Abstract 4 Declaration 6 Copyright 6 The Author 7 Acknowledgements 7 Abbreviations 8 1: Introduction......................................................................................................9 Why Anthropology? 14 Chapter Outline 40 2: The Study of Cities - Making Manchester...................................................45 Views of the City 46 From Landscape to Space 50 Competitive Spaces 59 Historical Stories 65 Creative Places 74 Conclusion 81 3: New Media Workplaces ................................................................................84 Anthropology and Organisations 85 Gaining Access 91 Work and Identity 111 4: Realising Our Potential - Paradigms of Newness and Change................117 Introducing Convergence 119 Conversations on Convergence 122 Gaming 124 Interactive TV 131 Commerce and Convergence 135 Blocks to Convergence 148 The “Newness” of New Media 157 Conclusion 161 5: The Discourse of Skills in the Practice of the Economic ..........................168 Wider Discourses on Skill 174 Skills – a Means to an End 182 6: The Network as Cultural Form ..................................................................205 Network Theories 208 Networks in New Media -

The Electrical Transformation of the Public Sphere: Home Video, the Family, and the Limits of Privacy in the Digital Age
THE ELECTRICAL TRANSFORMATION OF THE PUBLIC SPHERE: HOME VIDEO, THE FAMILY, AND THE LIMITS OF PRIVACY IN THE DIGITAL AGE By Adam Capitanio A DISSERTATION Submitted to Michigan State University in partial fulfillment of the requirements for the degree of DOCTOR OF PHILOSOPHY American Studies 2012 ABSTRACT THE ELECTRICAL TRANSFORMATION OF THE PUBLIC SPHERE: HOME VIDEO, THE FAMILY, AND THE LIMITS OF PRIVACY IN THE DIGITAL AGE By Adam Capitanio One of the constituent features of the digital age has been the redrawing of the line between private and public. Millions of social media users willingly discuss intimate behavior and post private photographs and videos on the internet. Meanwhile, state and corporate bodies routinely violate individual privacy in the name of security and sophisticated marketing techniques. While these occurrences represent something new and different, they are unsurprising given the history of home and amateur media. In this dissertation, I argue that contemporary shifts in the nature of the public/private divide have historical roots in the aesthetics and style found in home movies and videos. In other words, long before Facebook and YouTube enabled users to publicly document their private lives, home movies and videos generated patterns of representation that were already shifting the unstable constitution of the “private” and the “public” spheres. Using critical theory and archival research, I demonstrate how home moviemakers represented their families and experiences in communal and liminal spaces, expanding the meaning of “home.” When video become the predominant medium for domestic usage, home mode artifacts became imbricated with television, granting them a form of phantasmagoric publicity that found fulfillment in the digital era.