Study on Android Operating System and Its Versions M
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Netsuite for Mobile
NetSuite for Mobile September 9, 2020 2020.2 Copyright © 2005, 2020, Oracle and/or its affiliates. All rights reserved. This software and related documentation are provided under a license agreement containing restrictions on use and disclosure and are protected by intellectual property laws. Except as expressly permitted in your license agreement or allowed by law, you may not use, copy, reproduce, translate, broadcast, modify, license, transmit, distribute, exhibit, perform, publish, or display any part, in any form, or by any means. Reverse engineering, disassembly, or decompilation of this software, unless required by law for interoperability, is prohibited. The information contained herein is subject to change without notice and is not warranted to be error- free. If you find any errors, please report them to us in writing. If this is software or related documentation that is delivered to the U.S. Government or anyone licensing it on behalf of the U.S. Government, then the following notice is applicable: U.S. GOVERNMENT END USERS: Oracle programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, delivered to U.S. Government end users are "commercial computer software" pursuant to the applicable Federal Acquisition Regulation and agency-specific supplemental regulations. As such, use, duplication, disclosure, modification, and adaptation of the programs, including any operating system, integrated software, any programs installed on the hardware, and/or documentation, shall be subject to license terms and license restrictions applicable to the programs. No other rights are granted to the U.S. Government. This software or hardware is developed for general use in a variety of information management applications. -
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -

A Survey on Architectures of Mobile Operating Systems: Challenges and Issues
International Journal of Research Studies in Computer Science and Engineering (IJRSCSE) Volume 2, Issue 3, March 2015, PP 73-76 ISSN 2349-4840 (Print) & ISSN 2349-4859 (Online) www.arcjournals.org A Survey on Architectures of Mobile Operating Systems: Challenges and Issues Prof. Y. K. Sundara Krishna1 HOD, Dept. of Computer Science, Krishna University Mr. G K Mohan Devarakonda2 Research Scholar, Krishna University Abstract: In the early years of mobile evolution, Discontinued Platforms Current mobile devices are enabled only with voice services Platforms that allow the users to communicate with each other. Symbian OS Android But now a days, the mobile technology undergone Palm OS IOS various changes to a great extent so that the devices Maemo OS Windows Phone allows the users not only to communicate but also to Meego OS Firefox OS attain a variety of services such as video calls, faster Black Berry OS browsing services,2d and 3d games, Camera, 2.1 Symbian OS: This Operating system was Banking Services, GPS services, File sharing developed by NOKIA. services, Tracking Services, M-Commerce and so many. The changes in mobile technology may be due Architecture: to Operating System or Hardware or Network or Memory. This paper presents a survey on evolutions SYMBIAN OS GUI Library in mobile developments especially on mobile operating system Architectures, challenges and Issues in various mobile operating Systems. Application Engines JAVA VM 1. INTRODUCTION Servers (Operating System Services) A Mobile operating system is a System Software that is specifically designed to run on handheld devices Symbian OS Base (File Server, Kernel) such as Mobile Phones, PDA’s. -

Read PDF Linux-Distribusjoner: Ubuntu, Fedora
[PDF] Linux-distribusjoner: Ubuntu, Fedora, Slackware, Mandriva Linux, Splashtop, Kubuntu, Debian, Mark Shuttleworth, Linux Mint, Gobuntu Linux-distribusjoner: Ubuntu, Fedora, Slackware, Mandriva Linux, Splashtop, Kubuntu, Debian, Mark Shuttleworth, Linux Mint, Gobuntu Book Review Absolutely one of the best pdf We have ever read. I really could comprehended every little thing using this written e book. I am easily could get a satisfaction of reading a written publication. (Dr. Od ie Ham ill) LINUX-DISTRIBUSJONER: UBUNTU, FEDORA , SLA CKWA RE, MA NDRIVA LINUX, SPLA SHTOP, KUBUNTU, DEBIA N, MA RK SHUTTLEW ORTH, LINUX MINT, GOBUNTU - To read Linux - distribusjoner: Ubuntu, Fedora, Slackware, Mandriva Linux , Splashtop, Kubuntu, Debian, Mark Shuttleworth, Linux Mint, Gobuntu PDF, you should follow the hyperlink beneath and save the ebook or gain access to other information which are highly relevant to Linux-distribusjoner: Ubuntu, Fedora, Slackware, Mandriva Linux, Splashtop, Kubuntu, Debian, Mark Shuttleworth, Linux Mint, Gobuntu book. » Download Linux -distribusjoner: Ubuntu, Fedora, Slackware, Mandriva Linux , Splashtop, Kubuntu, Debian, Mark Shuttleworth, Linux Mint, Gobuntu PDF « Our solutions was launched using a want to serve as a total on the internet electronic digital catalogue which offers usage of multitude of PDF document collection. You may find many different types of e-book along with other literatures from the paperwork database. Particular popular issues that distributed on our catalog are famous books, answer key, exam test questions and answer, guide example, practice guideline, quiz trial, customer manual, user guide, service instruction, maintenance manual, and so forth. All e-book all privileges remain together with the writers, and downloads come as is. -

The Linux Kernel Module Programming Guide
The Linux Kernel Module Programming Guide Peter Jay Salzman Michael Burian Ori Pomerantz Copyright © 2001 Peter Jay Salzman 2007−05−18 ver 2.6.4 The Linux Kernel Module Programming Guide is a free book; you may reproduce and/or modify it under the terms of the Open Software License, version 1.1. You can obtain a copy of this license at http://opensource.org/licenses/osl.php. This book is distributed in the hope it will be useful, but without any warranty, without even the implied warranty of merchantability or fitness for a particular purpose. The author encourages wide distribution of this book for personal or commercial use, provided the above copyright notice remains intact and the method adheres to the provisions of the Open Software License. In summary, you may copy and distribute this book free of charge or for a profit. No explicit permission is required from the author for reproduction of this book in any medium, physical or electronic. Derivative works and translations of this document must be placed under the Open Software License, and the original copyright notice must remain intact. If you have contributed new material to this book, you must make the material and source code available for your revisions. Please make revisions and updates available directly to the document maintainer, Peter Jay Salzman <[email protected]>. This will allow for the merging of updates and provide consistent revisions to the Linux community. If you publish or distribute this book commercially, donations, royalties, and/or printed copies are greatly appreciated by the author and the Linux Documentation Project (LDP). -

Google Glass App Development
Google Glass App development Krishna Vattipalli Vice President @ Imaginnovate WELCOME to WEARABLE TECHNOLOGY Google Glass What does Google Glass do? • Connected to Internet • Via WiFi, Bluetooth tethering • Communicate with Smartphone • Bluetooth • Camera • Photos, Video • Location information • GPS History... • Google Glass was developed by Google X • Public testing began in April 2012 • Publicly first released in June 2012 during Google IO • Developer versions released in 2013 • Glassware app store July 2013 • Anyone can purchase developer versions from Google Play store (US only) - 2014 Technical Specifications • Google Glass software version XE21.3 • Android 4.4.4 • 5 MP camera, 720p Video recording • WiFi 802.11 b/g • Bluetooth • 16GB storage • 2GB RAM • 3 axis Gyroscope, Accelerometer, Magnetometer • Ambient light sensing and proximity sensor • Bone conduction audio transducer Google Glass Live • Navigation • Timeline • Settings • Email • Messaging • Sharing • Google Now • Camera Timeline • Past activities • Present activity • Future activities Design Guidelines • Do not distract user • Keep it relevant • Area constraint • Limited layouts • Battery • Device heats up quickly • Navigation constraints Design – Cards (Layout) Design – Colors, Fonts • Pre-defined colors • Uses Black and White most of the time • Roboto Thin – Primary font (above 26px) • Roboto Light – Secondary (26px or less) • Text is dynamically resized, depending on content • Keep text simple, relevant and clean Development - Patterns • Notifications (Static Cards) -

Android (Operating System) 1 Android (Operating System)
Android (operating system) 1 Android (operating system) Android Home screen displayed by Samsung Nexus S with Google running Android 2.3 "Gingerbread" Company / developer Google Inc., Open Handset Alliance [1] Programmed in C (core), C++ (some third-party libraries), Java (UI) Working state Current [2] Source model Free and open source software (3.0 is currently in closed development) Initial release 21 October 2008 Latest stable release Tablets: [3] 3.0.1 (Honeycomb) Phones: [3] 2.3.3 (Gingerbread) / 24 February 2011 [4] Supported platforms ARM, MIPS, Power, x86 Kernel type Monolithic, modified Linux kernel Default user interface Graphical [5] License Apache 2.0, Linux kernel patches are under GPL v2 Official website [www.android.com www.android.com] Android is a software stack for mobile devices that includes an operating system, middleware and key applications.[6] [7] Google Inc. purchased the initial developer of the software, Android Inc., in 2005.[8] Android's mobile operating system is based on a modified version of the Linux kernel. Google and other members of the Open Handset Alliance collaborated on Android's development and release.[9] [10] The Android Open Source Project (AOSP) is tasked with the maintenance and further development of Android.[11] The Android operating system is the world's best-selling Smartphone platform.[12] [13] Android has a large community of developers writing applications ("apps") that extend the functionality of the devices. There are currently over 150,000 apps available for Android.[14] [15] Android Market is the online app store run by Google, though apps can also be downloaded from third-party sites. -

Energy Efficient Wifi Tethering on a Smartphone
Energy Efficient Wifi Tethering on a Smartphone Kyoung-Hak Jung†, Yuepeng Qi†, Chansu Yu†‡, and Young-Joo Suh† †Department of Computer Science and Engineering & Division of IT Convergence Engineering Pohang Univ. of Science and Tech., Pohang, 790-784, Republic of Korea Email: {yeopki81, yuepengqi, yjsuh}@postech.ac.kr ‡Department of Electrical and Computer Engineering Cleveland State University, Cleveland, Ohio 44115 Email: [email protected] Abstract—While numerous efforts have been made to save energy of “client” devices but it has not been addressed for access points (APs) as they are assumed to be supported by AC power. This paper proposes E-MAP, which is an energy saving algorithm for a tethering smartphone that plays a role of mobile AP (MAP) temporarily. It saves MAP’s energy by introducing the sleep cycle as in power save mode (PSM) in 802.11 but successfully keeps clients from transmitting while it sleeps. One (a) Nexus One with traffic (b) iPhone 4 with traffic important design goal of E-MAP is backward compatibility, i.e., it requires no modification on the client side and supports PSM and adaptive PSM (A-PSM) as well as normal constant awake mode (CAM) clients. Experiments show that E-MAP reduces the energy consumption of a Wifi tethering smartphone by up to 54% with a little impact on packet delay under various traffic patterns derived from real-life traces. (c) Nexus One without traffic (d) iPhone 4 without traffic Fig. 1: Power consumption measurements using Monsoon Power I. INTRODUCTION Monitor [11]. (Each figure compares power consumption of a smart- While the coverage of cellular networks is much larger phone when it is used as a 3G client, a Wifi client, and a MAP with than that of Wifi networks in the US (99% vs. -

Android Operating System
Software Engineering ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, 2012, pp.-10-13. Available online at http://www.bioinfo.in/contents.php?id=76 ANDROID OPERATING SYSTEM NIMODIA C. AND DESHMUKH H.R. Babasaheb Naik College of Engineering, Pusad, MS, India. *Corresponding Author: Email- [email protected], [email protected] Received: February 21, 2012; Accepted: March 15, 2012 Abstract- Android is a software stack for mobile devices that includes an operating system, middleware and key applications. Android, an open source mobile device platform based on the Linux operating system. It has application Framework,enhanced graphics, integrated web browser, relational database, media support, LibWebCore web browser, wide variety of connectivity and much more applications. Android relies on Linux version 2.6 for core system services such as security, memory management, process management, network stack, and driver model. Architecture of Android consist of Applications. Linux kernel, libraries, application framework, Android Runtime. All applications are written using the Java programming language. Android mobile phone platform is going to be more secure than Apple’s iPhone or any other device in the long run. Keywords- 3G, Dalvik Virtual Machine, EGPRS, LiMo, Open Handset Alliance, SQLite, WCDMA/HSUPA Citation: Nimodia C. and Deshmukh H.R. (2012) Android Operating System. Software Engineering, ISSN: 2229-4007 & ISSN: 2229-4015, Volume 3, Issue 1, pp.-10-13. Copyright: Copyright©2012 Nimodia C. and Deshmukh H.R. This is an open-access article distributed under the terms of the Creative Commons Attribution License, which permits unrestricted use, distribution, and reproduction in any medium, provided the original author and source are credited. -

A Survey on Potential Privacy Leaks of GPS Information in Android Applications
UNLV Theses, Dissertations, Professional Papers, and Capstones May 2015 A Survey on Potential Privacy Leaks of GPS Information in Android Applications Srinivas Kalyan Yellanki University of Nevada, Las Vegas Follow this and additional works at: https://digitalscholarship.unlv.edu/thesesdissertations Part of the Library and Information Science Commons Repository Citation Yellanki, Srinivas Kalyan, "A Survey on Potential Privacy Leaks of GPS Information in Android Applications" (2015). UNLV Theses, Dissertations, Professional Papers, and Capstones. 2449. http://dx.doi.org/10.34917/7646102 This Thesis is protected by copyright and/or related rights. It has been brought to you by Digital Scholarship@UNLV with permission from the rights-holder(s). You are free to use this Thesis in any way that is permitted by the copyright and related rights legislation that applies to your use. For other uses you need to obtain permission from the rights-holder(s) directly, unless additional rights are indicated by a Creative Commons license in the record and/ or on the work itself. This Thesis has been accepted for inclusion in UNLV Theses, Dissertations, Professional Papers, and Capstones by an authorized administrator of Digital Scholarship@UNLV. For more information, please contact [email protected]. A SURVEY ON POTENTIAL PRIVACY LEAKS OF GPS INFORMATION IN ANDROID APPLICATIONS By Srinivas Kalyan Yellanki Bachelor of Technology, Information Technology Jawaharlal Nehru Technological University, India 2013 A thesis submitted in partial fulfillment -

History and Evolution of the Android OS
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Springer - Publisher Connector CHAPTER 1 History and Evolution of the Android OS I’m going to destroy Android, because it’s a stolen product. I’m willing to go thermonuclear war on this. —Steve Jobs, Apple Inc. Android, Inc. started with a clear mission by its creators. According to Andy Rubin, one of Android’s founders, Android Inc. was to develop “smarter mobile devices that are more aware of its owner’s location and preferences.” Rubin further stated, “If people are smart, that information starts getting aggregated into consumer products.” The year was 2003 and the location was Palo Alto, California. This was the year Android was born. While Android, Inc. started operations secretly, today the entire world knows about Android. It is no secret that Android is an operating system (OS) for modern day smartphones, tablets, and soon-to-be laptops, but what exactly does that mean? What did Android used to look like? How has it gotten where it is today? All of these questions and more will be answered in this brief chapter. Origins Android first appeared on the technology radar in 2005 when Google, the multibillion- dollar technology company, purchased Android, Inc. At the time, not much was known about Android and what Google intended on doing with it. Information was sparse until 2007, when Google announced the world’s first truly open platform for mobile devices. The First Distribution of Android On November 5, 2007, a press release from the Open Handset Alliance set the stage for the future of the Android platform. -
Ibeta-Device-Invento
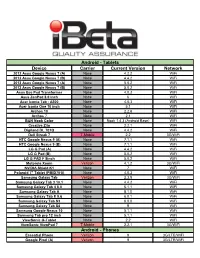
Android - Tablets Device Carrier Current Version Network 2012 Asus Google Nexus 7 (A) None 4.2.2 WiFi 2012 Asus Google Nexus 7 (B) None 4.4.2 WiFi 2013 Asus Google Nexus 7 (A) None 5.0.2 WiFi 2013 Asus Google Nexus 7 (B) None 5.0.2 WiFi Asus Eee Pad Transformer None 4.0.3 WiFi Asus ZenPad 8.0 inch None 6 WiFi Acer Iconia Tab - A500 None 4.0.3 WiFi Acer Iconia One 10 inch None 5.1 WiFi Archos 10 None 2.2.6 WiFi Archos 7 None 2.1 WiFi B&N Nook Color None Nook 1.4.3 (Android Base) WiFi Creative Ziio None 2.2.1 WiFi Digiland DL 701Q None 4.4.2 WiFi Dell Streak 7 T-Mobile 2.2 3G/WiFi HTC Google Nexus 9 (A) None 7.1.1 WiFi HTC Google Nexus 9 (B) None 7.1.1 WiFi LG G Pad (A) None 4.4.2 WiFi LG G Pad (B) None 5.0.2 WiFi LG G PAD F 8inch None 5.0.2 WiFi Motorola Xoom Verizon 4.1.2 3G/WiFi NVIDIA Shield K1 None 7 WiFi Polaroid 7" Tablet (PMID701i) None 4.0.3 WiFi Samsung Galaxy Tab Verizon 2.3.5 3G/WiFi Samsung Galaxy Tab 3 10.1 None 4.4.2 WiFi Samsung Galaxy Tab 4 8.0 None 5.1.1 WiFi Samsung Galaxy Tab A None 8.1.0 WiFi Samsung Galaxy Tab E 9.6 None 6.0.1 WiFi Samsung Galaxy Tab S3 None 8.0.0 WiFi Samsung Galaxy Tab S4 None 9 WiFi Samsung Google Nexus 10 None 5.1.1 WiFi Samsung Tab pro 12 inch None 5.1.1 WiFi ViewSonic G-Tablet None 2.2 WiFi ViewSonic ViewPad 7 T-Mobile 2.2.1 3G/WiFi Android - Phones Essential Phone Verizon 9 3G/LTE/WiFi Google Pixel (A) Verizon 9 3G/LTE/WiFi Android - Phones (continued) Google Pixel (B) Verizon 8.1 3G/LTE/WiFi Google Pixel (C) Factory Unlocked 9 3G/LTE/WiFi Google Pixel 2 Verizon 8.1 3G/LTE/WiFi Google Pixel