Extended Memory Specification (XMS), Ver 3.0
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Kontron / ICS Advent SB586P(V) Manual (Pdf)
Full-service, independent repair center -~ ARTISAN® with experienced engineers and technicians on staff. TECHNOLOGY GROUP ~I We buy your excess, underutilized, and idle equipment along with credit for buybacks and trade-ins. Custom engineering Your definitive source so your equipment works exactly as you specify. for quality pre-owned • Critical and expedited services • Leasing / Rentals/ Demos equipment. • In stock/ Ready-to-ship • !TAR-certified secure asset solutions Expert team I Trust guarantee I 100% satisfaction Artisan Technology Group (217) 352-9330 | [email protected] | artisantg.com All trademarks, brand names, and brands appearing herein are the property o f their respective owners. Find the Kontron / ICS Advent SB586PV at our website: Click HERE Model SB586P(V) Product Manual MANUAL NUMBER : 00431-027-3C Page - ii FOREWORD This product manual provides information to install, operate and or program the referenced product(s) manufactured or distributed by ICS Advent. The following pages contain information regarding the war- ranty and repair policies. Technical assistance is available at: 800-480-0044. Manual Errors, Omissions and Bugs: A "Bug Sheet" is included as the last page of this manual. Please use the "Bug Sheet" if you experience any problems with the manual that requires correction. The information in this document is provided for reference only. ICS Advent does not assume any liability arising from the application or use of the information or products described herein. This document may contain or reference information and products protected by copyrights or patents and does not convey any license under the patent rights of ICS Advent, nor the rights of others. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

SOS Internals
Understanding a Simple Operating System SOS is a Simple Operating System designed for the 32-bit x86 architecture. Its purpose is to understand basic concepts of operating system design. These notes are meant to help you recall the class discussions. Chapter 1 : Starting Up SOS 3 Registers in the IA-32 x86 Architecture BIOS (Basic Input/Ouput System) Routines Real Mode Addressing Organization of SOS on Disk and Memory Master Boot Record SOS Startup A20 Line 32-bit Protected Mode Addressing Privilege Level Global Descriptor Table (GDT) More on Privilege Levels The GDT Setup Enabling Protected Mode Calling main() Chapter 2 : SOS Initializations 10 In main() Disk Initialization Display Initialization Setting Up Interrupt Handlers Interrupt Descriptor Table (IDT) A Default Interrupt Handler Load IDT The Programmable Interrupt Controller (PIC) The Keyboard Interrupt Handler Starting the Console Putting It All Together Chapter 3: SOS1 – Single-tasking SOS 16 Running User Programs GDT Entries Default Exception Handler User Programs Executable Format System Calls Creating User Programs The run Command Understanding a Simple Operating System The DUMB Memory Manager Program Address Space Process Control Block Switching to a User Program Kernel-Mode Stack Chapter 4 : SOS2 – Multi-tasking SOS 24 Running Multiple User Programs NAÏVE Memory Manager Programmable Interval Timer (PIT) Process States Timer Interrupt Handler Sleep System Call The run Command Process Queue The Scheduler The Complete Picture ps Command Chapter 5 : SOS3 – Paging in SOS 31 -

The Bootstrap the Where Are Wenow?
Dedicated Operating System March2011 Prof. Dr.Antônio AugustoFröhlich http://www.lisha.ufsc.br/Guto Getting ready for the OS for the ready Getting [email protected] LISHA/UFSC The Boot: The March 2011 (http://www.lisha.ufsc.br) 1 Dedicated Operating System March2011 ● ● ● BIOSgot the system ready for BIOSbrought the system on ● Lots of “jmp” so far, no calls, why? ● First instruction fetched ● initializedBIOS a complex architecture Where the stack?Where is 0x7c00 BIST, POST, hooks The Bootstrap Where are we now? we are Where (http://www.lisha.ufsc.br) =>Today class 2 EPOS Bootstrap: m src/boot/pc_boot.S e t ; CONSTANTS s ;============================================================ y ; PHYSICAL MEMORY MAP S ; 0x0000 0000 -+-----------------------+ BOOT_IDT ; | IDT (4 K) | g ; 0x0000 1000 -+-----------------------+ BOOT_GDT ; | GDT (4 K) | n i ; 0x0000 2000 -+-----------------------+ t ; : : a ; | BOOT STACK (23 K) | r ; 0x0000 7c00 -+-----------------------+ BOOTSTRAP_STACK e ; | BOOT CODE (512 b) | BOOTSTRAP_CODE p ; 0x0000 7e00 -+-----------------------+ ; | RESERVED (512 b) | O ; 0x0000 8000 -+-----------------------+ DISK_IMAGE ; | DISK IMAGE (608 K) | d ; : : e ; | | t ; 0x000a 0000 -+-----------------------+ a ; | UNUSED (384K) | c ; : : i ; | | d ; 0x000f f000 -+-----------------------+ e D March 2011 (http://www.lisha.ufsc.br) 3 EPOS Bootstrap: Notes m e t s Code to be ran at real mode (16 bits) y S Interrupts (IDT) ● g At real mode, always at 0x0000 n ● i At protected mode, anywhere (IDTR) t a Segmentation (GDT) r ● e Always -

Computing :: Operatingsystems :: DOS Beyond 640K 2Nd
DOS® Beyond 640K 2nd Edition DOS® Beyond 640K 2nd Edition James S. Forney Windcrest®/McGraw-Hill SECOND EDITION FIRST PRINTING © 1992 by James S. Forney. First Edition © 1989 by James S. Forney. Published by Windcrest Books, an imprint of TAB Books. TAB Books is a division of McGraw-Hill, Inc. The name "Windcrest" is a registered trademark of TAB Books. Printed in the United States of America. All rights reserved. The publisher takes no responsibility for the use of any of the materials or methods described in this book, nor for the products thereof. Library of Congress Cataloging-in-Publication Data Forney, James. DOS beyond 640K / by James S. Forney. - 2nd ed. p. cm. Rev. ed. of: MS-DOS beyond 640K. Includes index. ISBN 0-8306-9717-9 ISBN 0-8306-3744-3 (pbk.) 1. Operating systems (Computers) 2. MS-DOS (Computer file) 3. PC -DOS (Computer file) 4. Random access memory. I. Forney, James. MS-DOS beyond 640K. II. Title. QA76.76.063F644 1991 0058.4'3--dc20 91-24629 CIP TAB Books offers software for sale. For information and a catalog, please contact TAB Software Department, Blue Ridge Summit, PA 17294-0850. Acquisitions Editor: Stephen Moore Production: Katherine G. Brown Book Design: Jaclyn J. Boone Cover: Sandra Blair Design, Harrisburg, PA WTl To Sheila Contents Preface Xlll Acknowledgments xv Introduction xvii Chapter 1. The unexpanded system 1 Physical limits of the system 2 The physical machine 5 Life beyond 640K 7 The operating system 10 Evolution: a two-way street 12 What else is in there? 13 Out of hiding 13 Chapter 2. -

Protected Mode - Wikipedia
2/12/2019 Protected mode - Wikipedia Protected mode In computing, protected mode, also called protected virtual address mode,[1] is an operational mode of x86- compatible central processing units (CPUs). It allows system software to use features such as virtual memory, paging and safe multi-tasking designed to increase an operating system's control over application software.[2][3] When a processor that supports x86 protected mode is powered on, it begins executing instructions in real mode, in order to maintain backward compatibility with earlier x86 processors.[4] Protected mode may only be entered after the system software sets up one descriptor table and enables the Protection Enable (PE) bit in the control register 0 (CR0).[5] Protected mode was first added to the x86 architecture in 1982,[6] with the release of Intel's 80286 (286) processor, and later extended with the release of the 80386 (386) in 1985.[7] Due to the enhancements added by protected mode, it has become widely adopted and has become the foundation for all subsequent enhancements to the x86 architecture,[8] although many of those enhancements, such as added instructions and new registers, also brought benefits to the real mode. Contents History The 286 The 386 386 additions to protected mode Entering and exiting protected mode Features Privilege levels Real mode application compatibility Virtual 8086 mode Segment addressing Protected mode 286 386 Structure of segment descriptor entry Paging Multitasking Operating systems See also References External links History https://en.wikipedia.org/wiki/Protected_mode -

IMS D7305A IBM 386 PC Occam 2 Toolset Delivery Manual
·. ,i .. W .. ~.~.. mrumos®[] IMS D7305A IBM 386 PC occam 2 Toolset delivery manual INMOS"'Y£'-is a member of the SGS-THOMSON Microelectronics Group © INMOS Limited 1993. This document may not be copied, in whole or in part, without prior written consent of INMOS. •,DIITI11OS·, IMS, and occam are trademarks of INMOS Limited. ~~em is a registered trademark of the SGS-THOMSON Microelectronics Group. INMOS Limited is a member of the SGS-THOMSON Microelectronics Group. WATCOM is a trademark of WATCOM Systems Inc. INMOS document number: 72 TDS 389 01 IContents 1 Introduction . 1 1.1 Layout of this manual . 1 1.2 Prerequisites for running the toolset . 1 1.3 Compatibility with previous releases . 1 2 Installing the release . 3 2.1 Installation . 3 2.2 Hosted and non-hosted tools . 4 2.3 Setting up the toolset for use . 5 2.3.1 Setting the FILES variable . 5 2.3.2 Setting the correct PATH . 5 2.3.3 Configuring the DOS extender . 5 2.3.4 Setting up the iserver . 6 Selecting the required iserver . 6 Special notes for users of the PC-NFS iserver . 7 Notes common to both versions of the iserver . 7 Note for users of the IMS B008 motherboard . 8 2.3.5 Use of the iserver by transputer tool driver programs 8 2.3.6 Setting the board memory size . 9 2.3.7 Setting root memory size for idebug . 9 2.3.8 Setting a file system search path . 9 2.3.9 Setting the device driver and terminal definition file 10 2.3.10 Environment space . -

Microsoft Windows Resource
Chapter 13 Troubleshooting Windows 3.1 This chapter provides information about troubleshooting Microsoft Windows for both general users and experts. If you have trouble installing Windows, or if Windows doesn’t run as well as you expected, this chapter will help you find out why and show you how to isolate and solve common problems. Related Information • Windows User’s Guide: Chapter 15, “Maintaining Windows with Setup” See also Chapter 4, “Troubleshooting,” in the Getting Started booklet • Windows Resource Kit: “The Troubleshooting Flowcharts for Windows 3.1” in “Welcome” Contents of this chapter About Troubleshooting.....................................................................................396 Getting Started with Troubleshooting........................................................396 Creating a “Clean Boot” for Troubleshooting ...........................................398 Troubleshooting Setup......................................................................................399 Troubleshooting TSR s During Setup .........................................................400 Troubleshooting MS-DOS Mode Setup......................................................401 Troubleshooting Windows Mode Setup ....................................................402 Troubleshooting Windows Configuration ........................................................403 Troubleshooting the Desktop Configuration .............................................403 Troubleshooting TSR Compatibility Problems ..........................................404 -

Memory Management
University of Mississippi eGrove American Institute of Certified Public Guides, Handbooks and Manuals Accountants (AICPA) Historical Collection 1993 Memory management American Institute of Certified Public Accountants. Information echnologyT Division Follow this and additional works at: https://egrove.olemiss.edu/aicpa_guides Part of the Accounting Commons, and the Taxation Commons Recommended Citation American Institute of Certified Public Accountants. Information echnologyT Division, "Memory management" (1993). Guides, Handbooks and Manuals. 486. https://egrove.olemiss.edu/aicpa_guides/486 This Book is brought to you for free and open access by the American Institute of Certified Public Accountants (AICPA) Historical Collection at eGrove. It has been accepted for inclusion in Guides, Handbooks and Manuals by an authorized administrator of eGrove. For more information, please contact [email protected]. INFORMATION TECHNOLOGY DIVISION BULLETIN AICPA American Institute of Certified Public Accountants TECHNOLOGY Notice to Readers This technology bulletin is the first in a series of bulletins that provide accountants with information about a particular technology. These bulletins are issued by the AICPA Information Technology Division for the benefit of Information Technology Section Members. This bulletin does not establish standards or preferred practice; it represents the opinion of the author and does not necessarily reflect the policies of the AICPA or the Information Technology Division. The Information Technology Division expresses its appreciation to the author of this technology bulletin, Liz O’Dell. She is employed by Crowe, Chizek and Company in South Bend, Indiana, as a manager of firmwide microcomputer operations, supporting both hardware and software applications. Liz is an Indiana University graduate with an associate’s degree in computer information systems and a bachelor’s degree in business management. -

Hardware & Booting
PC Hardware & Booting Chester Rebeiro IIT Madras Outline • Memory and Device Addresses • PC Organization • x86 Evolution • Powering up • Booting xv6 • Multiprocessor booting 2 CPUs Processor i386 3 Everything has an address 0x3c0:0x3cf 0x60:0x6f Processor i386 0x1f0:0x1f7 0x0 : 0x200000 0x60:0x6f 4 Address Types • Memory Addresses • IO Addresses • Memory Mapped IO Addresses 5 Address Types : (Memory Addresses) • Range : 0 to (RAM size or 232-1) • Where main memory is mapped – Used to store data for code, heap, stack, OS, etc. • Accessed by load/store instructions Memory Map 6 Low and Extended Memory (Legacy Issues) • Why study it? – Backward compatibility • 8088 has 20 address lines; can address 220 bytes (1MB) • Memory Ranges – 0 to 640KB used by IBM PC MSDOS • Other DOS versions have a different memory limit – 640 KB to 1MB used by video buffers, expansion ROMS, BIOS ROMs – 1 MB onwards called extended memory • Modern processors have more usable memory – OSes like Linux and x86 simply ignore the first 1MB and load kernel in extended memory 7 Address Types : (IO Ports) • Range : 0 to 216-1 • Used to access devices • Uses a different bus compared to RAM memory access – Completely isolated from memory • Accessed by in/out instructions inb $0x64, %al outb %al, $0x64 ref : http://bochs.sourceforge.net/techspec/PORTS.LST 8 Memory Mapped I/O • Why? – More space • Devices and RAM share the same address space • Instructions used to access RAM can also be used to access devices. – Eg load/store Memory Map 9 Who decides the address ranges? • Standards / Legacy – Such as the IBM PC standard – Fixed for all PCs. -
Microsoft Windows for MS
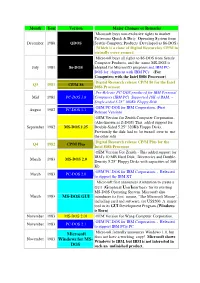
Month Year Version Major Changes or Remarks Microsoft buys non-exclusive rights to market Pattersons Quick & Dirty Operating System from December 1980 QDOS Seattle Computer Products (Developed as 86-DOS) (Which is a clone of Digital Researches C P/M in virtually every respect) Microsoft buys all rights to 86-DOS from Seattle Computer Products, and the name MS-DOS is July 1981 86-DOS adopted for Microsoft's purposes and IBM PC- DOS for shipment with IBM PCs (For Computers with the Intel 8086 Processor) Digital Research release CP/M 86 for the Intel Q3 1981 CP/M 86 8086 Processer Pre-Release PC-DOS produced for IBM Personal Mid 1981 PC-DOS 1.0 Computers (IBM PC) Supported 16K of RAM, ~ Single-sided 5.25" 160Kb Floppy Disk OEM PC-DOS for IBM Corporation. (First August 1982 PC-DOS 1.1 Release Version) OEM Version for Zenith Computer Corporation.. (Also known as Z-DOS) This added support for September 1982 MS-DOS 1.25 Double-Sided 5.25" 320Kb Floppy Disks. Previously the disk had to be turned over to use the other side Digital Research release CP/M Plus for the Q4 1982 CP/M Plus Intel 8086 Processer OEM Version For Zenith - This added support for IBM's 10 MB Hard Disk, Directories and Double- March 1983 MS-DOS 2.0 Density 5.25" Floppy Disks with capacities of 360 Kb OEM PC-DOS for IBM Corporation. - Released March 1983 PC-DOS 2.0 to support the IBM XT Microsoft first announces it intention to create a GUI (Graphical User Interface) for its existing MS-DOS Operating System. -

C++ Memory Management
C++ Memory Management Len Dorfman Marc J. Neuberger Winderest /McGraw-Hill New York San Francisco Washington, D.C. Auckland Bogota Caracas Lisbon London Madrid Mexico City Milan Montreal New Delhi San Juan Singapore Sydney Tokyo Toronto Contents What you need to use this book Introduction 1 Memory management overview Using expanded memory for dynamic memory allocation Using extended memory for dynamic memory allocation Using the hard disk for dynamic memory allocation 7 Summary 7 2 Understanding memory control blocks Preparatory memory management routines 11 Writing a memory chain display utility program 12 Summary 23 3 EMS 3.0 and 3.2 About the EMS programmer's interface 25 EMS 3.0 demonstration programs 26 The EMS 3.0 and 3.2 interface 46 C++ interface functions 64 Initialize EMS 64 Get the EMM status 64 Get the page frame address 66 Get the number of free EMS pages 67 Allocate EMS handle and pages 68 Map an expanded memory page 70 Free a handle and the associated EMS pages 71 Get the EMS version number 72 Save the contents of page map registers 74 Restore the contents of page map registers 75 Get the number of active EMM handles 76 Get number of pages for handle 77 Get number of pages for all handles 79 EMS 3.2 functions 81 Save page map to a buffer 81 Restore page map from a buffer 82 Swap page maps 83 Get the size of a map register save area 85 Summary 87 4 EMS 4.0 EMS 4.0 enhancements 89 EMS 4.0 demonstration programs 90 C++interface functions 115 Save a partial page map 115 Restore a partial page map 117 Get the size of partial