The Medium Access Control Sublayer
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ethernet Switches and Crossover Cables
Ethernet Switch A switch is something that is used to turn various electronic devices on or off. However, in computernetworking, a switch is used to connect multiple computers with each other. Since it is an external device it becomes part of the hardware peripherals used in the operation of a computer system. This connection is done within an existing Local Area network (LAN) only and is identical to an Ethernet hub in terms of appearance, but with more intelligence. These switches not only receive data packets, but also have the ability to inspect them before passing them on to the next computer. That is, they can figure out the source, the contents of the data, and identify the destination as well. As a result of this uniqueness, it sends the data to the relevant connected system only, thereby using less bandwidth at high performance rates. The first Ethernet network switch was pioneered by Kalpana (computer networking equipmentmanufacturing company in Silicon Valley established by an entrepreneur of Indian origin, Vinod Bharadwaj) in 1990. Switches operate at Layer 2 of the OSI Model; the Data-Link Layer. This is in contrast to routers, which operate at Layer 3 of the OSI Model, the Network Layer. A switch stores the MAC Address of each and every device which is connected to it. The switch will then evaluate every frame that passes through it. The switch will examine the destination MAC Address in each frame. Based upon the destination MAC Address, the switch will then decide which port to copy the frame to. If the switch does not recognize the MAC Address, it will not know which port to copy the frame to. -

Medium Access Control Layer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay (historical) ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus (historical) ● Network Infrastructure ● Token Ring (historical) ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● Protocols used to determine who gets next access to the channel Data Link Layer ● Medium Access Control (MAC) sublayer Physical Layer Univ.-Prof. Dr.-Ing. Jochen H. Schiller ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Range ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access .. -

Ts 138 321 V15.3.0 (2018-09)
ETSI TS 138 321 V15.3.0 (2018-09) TECHNICAL SPECIFICATION 5G; NR; Medium Access Control (MAC) protocol specification (3GPP TS 38.321 version 15.3.0 Release 15) 3GPP TS 38.321 version 15.3.0 Release 15 1 ETSI TS 138 321 V15.3.0 (2018-09) Reference RTS/TSGR-0238321vf30 Keywords 5G ETSI 650 Route des Lucioles F-06921 Sophia Antipolis Cedex - FRANCE Tel.: +33 4 92 94 42 00 Fax: +33 4 93 65 47 16 Siret N° 348 623 562 00017 - NAF 742 C Association à but non lucratif enregistrée à la Sous-Préfecture de Grasse (06) N° 7803/88 Important notice The present document can be downloaded from: http://www.etsi.org/standards-search The present document may be made available in electronic versions and/or in print. The content of any electronic and/or print versions of the present document shall not be modified without the prior written authorization of ETSI. In case of any existing or perceived difference in contents between such versions and/or in print, the only prevailing document is the print of the Portable Document Format (PDF) version kept on a specific network drive within ETSI Secretariat. Users of the present document should be aware that the document may be subject to revision or change of status. Information on the current status of this and other ETSI documents is available at https://portal.etsi.org/TB/ETSIDeliverableStatus.aspx If you find errors in the present document, please send your comment to one of the following services: https://portal.etsi.org/People/CommiteeSupportStaff.aspx Copyright Notification No part may be reproduced or utilized in any form or by any means, electronic or mechanical, including photocopying and microfilm except as authorized by written permission of ETSI. -

10/100 Physical Layer Ethernet Switch,16-Port
10/100 PHYSICAL LAYER ETHERNET SWITCH,16-PORT Make 10/100 Physical Layer Ethernet connections without rewiring or rerouting cables. Key Features emotely configure, redistribute, Ethernet hub or network switch You can also instantly and Ideal for point-to-point R and monitor Ethernet devices using a crossover cable. Each effortlessly recall up to 16 Ethernet connections. in 10/100 Ethernet LAN connected device can be placed frequently-used patching environments. The 10/100 up to 328 ft. (100 m) away from the configurations (stored in the Auto-adapts port Physical Layer Ethernet Switch, switch. switch’s non-volatile memory) via speed to either 10 or 16-Port provides point-to-point The switch installs between the LAN or RS-232 serial port. 100 Mbps. connectivity without rewiring or your patch panels and network The control software works rerouting cables. And it switch. Since it operates at the with Windows® 95/98/2000/XP and Switch between up to automatically adapts to port Physical Layer, the switch can Windows NT®. The PC connected 16 devices, each speeds of 10 or 100 Mbps. shut down the physical connec- to the serial port can be located located up to 328 ft. Attach 10BASE-T Ethernet or tion to specific workstations, up to 50 ft. (15.2 m) from the (100 m) away from the 100BASE-TX Fast Ethernet departments, or buildings. You switch, while the workstation switch. devices via the 16 RJ-45 can do this remotely via the connected to the LAN port can be connectors on the switch’s front control software and a PC located up to 328 ft. -

Ethernet Technology 1 Ethernet Technology 2
• History - Xerox : LAN for open office automation (1970s) 3Mbps on 75 Ohm Coax, coverage 1km area - DEC, Intel, and Xerox Co-proposed “Ethernet v1.0” (9/1980) - D.I.X. Ö Ethernet ver 2.0 (11/1982): 50Ohm Coax, 2.8 km • ANSI/IEEE 802.3 (ISO 8802.3) - Reformulated Ethernet v2 in 1985 - Drop cable, connector technology, times and fields are redefined - It’s used with Ethernet interchangeably, but less meaningful than Ethernet (?retain the original name) - Supplementary documents (regarding to various medium) + Upgrades are published after Feb.1989 Î IEEE 802.3x Ethernet Technology 1 Ethernet Technology 2 NotationNotation ofof EthernetEthernet TechnologyTechnology # B X / # Bit rate in Mbps: Distance in 100m: -1 -10 -100 - 2, -5, -36, -1000 -10000 or Medium: Simplified to: Signaling method: - Baseband 10/100Æ T?/TX or F/FX invented by: Bob Metcalfe and David Boggs in 1970 1GE & 10GE - Broadband 1GEÆ (C/S/L)X or T 10GEÆ(S/L/E)(X/R/W) ൩೭ኬǻ Ethernet Technology 3 Ethernet Technology More on Ethernet Family 4 Bus Topology -- 10Base2/5/36 Explanation of the Abbreviations • Connecting nodes via (tap to) coaxial cable • Transmission and receiving over the same media (line) • Basic configuration (Ex: A 10Base5 segment = a coax) : TRL ~ Transceiver’s cable Length DBN ~ Distance Between Nodes ӕືႝᢑࢤȐനߏ 500 ϦЁȑ MSL node NPS ~ Nodes Per Segment DBT Terminator Multiple of 2.5m Coaxial Cable tap Extension ? MES MSL ~ Maximum Segment Length ԏวᏔ Ȑനߏ 50 ϦЁȑ TRL ԏวᏔႝᢑ Transceiver Terminator ಖᆄᏔ MES ~ Maximum Extendable Segments ࢤനӭௗ 100 ঁȑ NPSȐ • Important parameters: TRL, DBT, NPS, MSL, and MND. -

Modern Ethernet
Color profile: Generic CMYK printer profile Composite Default screen All-In-One / Network+ Certification All-in-One Exam Guide / Meyers / 225345-2 / Chapter 6 CHAPTER Modern Ethernet 6 The Network+ Certification exam expects you to know how to • 1.2 Specify the main features of 802.2 (Logical Link Control) [and] 802.3 (Ethernet): speed, access method, topology, media • 1.3 Specify the characteristics (for example: speed, length, topology, and cable type) of the following cable standards: 10BaseT and 10BaseFL; 100BaseTX and 100BaseFX; 1000BaseTX, 1000BaseCX, 1000BaseSX, and 1000BaseLX; 10GBaseSR, 10GBaseLR, and 10GBaseER • 1.4 Recognize the following media connectors and describe their uses: RJ-11, RJ-45, F-type, ST,SC, IEEE 1394, LC, MTRJ • 1.6 Identify the purposes, features, and functions of the following network components: hubs, switches • 2.3 Identify the OSI layers at which the following network components operate: hubs, switches To achieve these goals, you must be able to • Define the characteristics, cabling, and connectors used in 10BaseT and 10BaseFL • Explain how to connect multiple Ethernet segments • Define the characteristics, cabling, and connectors used with 100Base and Gigabit Ethernet Historical/Conceptual The first generation of Ethernet network technologies enjoyed substantial adoption in the networking world, but their bus topology continued to be their Achilles’ heel—a sin- gle break anywhere on the bus completely shut down an entire network. In the mid- 1980s, IBM unveiled a competing network technology called Token Ring. You’ll get the complete discussion of Token Ring in the next chapter, but it’s enough for now to say that Token Ring used a physical star topology. -

Ethernet Networks: Design, Implementation, Operation, Management
Ethernet Networks: Design, Implementation, Operation, Management. Gilbert Held Copyright 2003 John Wiley & Sons, Ltd. ISBN: 0-470-84476-0 ethernet networks Fourth Edition Books by Gilbert Held, published by Wiley Quality of Service in a Cisco Networking Environment 0 470 84425 6 (April 2002) Bulletproofing TCP/IP-Based Windows NT/2000 Networks 0 471 49507 7 (April 2001) Understanding Data Communications: From Fundamentals to Networking, Third Edition 0 471 62745 3 (October 2000) High Speed Digital Transmission Networking: Covering T/E-Carrier Multiplexing, SONET and SDH, Second Edition 0 471 98358 6 (April 1999) Data Communications Networking Devices: Operation, Utilization and LAN and WAN Internetworking, Fourth Edition 0 471 97515 X (November 1998) Dictionary of Communications Technology: Terms, Definitions and Abbreviations, Third Edition 0 471 97517 6 (May 1998) Internetworking LANs and WANs: Concepts, Techniques and Methods, Second Edition 0 471 97514 1 (May 1998) LAN Management with SNMP and RMON 0 471 14736 2 (September 1996) ethernet networks Fourth Edition ♦ Design ♦ Implementation ♦ Operation ♦ Management GILBERT HELD 4-Degree Consulting, Macon, Georgia, USA Copyright 2003 John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex PO19 8SQ, England Telephone (+44) 1243 779777 Email (for orders and customer service enquiries): [email protected] Visit our Home Page on www.wileyeurope.com or www.wiley.com All Rights Reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except under the terms of the Copyright, Designs and Patents Act 1988 or under the terms of a licence issued by the Copyright Licensing Agency Ltd, 90 Tottenham Court Road, London W1T 4LP, UK, without the permission in writing of the Publisher. -

Chapter 6: Medium Access Control Layer
Chapter 6: Medium Access Control Layer Chapter 6: Roadmap " Overview! " Wireless MAC protocols! " Carrier Sense Multiple Access! " Multiple Access with Collision Avoidance (MACA) and MACAW! " MACA By Invitation! " IEEE 802.11! " IEEE 802.15.4 and ZigBee! " Characteristics of MAC Protocols in Sensor Networks! " Energy Efficiency! " Scalability! " Adaptability! " Low Latency and Predictability! " Reliability! " Contention-Free MAC Protocols! " Contention-Based MAC Protocols! " Hybrid MAC Protocols! Fundamentals of Wireless Sensor Networks: Theory and Practice Waltenegus Dargie and Christian Poellabauer © 2010 John Wiley & Sons Ltd. 2! Medium Access Control " In most networks, multiple nodes share a communication medium for transmitting their data packets! " The medium access control (MAC) protocol is primarily responsible for regulating access to the shared medium! " The choice of MAC protocol has a direct bearing on the reliability and efficiency of network transmissions! " due to errors and interferences in wireless communications and to other challenges! " Energy efficiency also affects the design of the MAC protocol! " trade energy efficiency for increased latency or a reduction in throughput or fairness! Fundamentals of Wireless Sensor Networks: Theory and Practice Waltenegus Dargie and Christian Poellabauer © 2010 John Wiley & Sons Ltd. 3! 1! Overview " Responsibilities of MAC layer include:! " decide when a node accesses a shared medium! " resolve any potential conflicts between competing nodes! " correct communication errors occurring at the physical layer! " perform other activities such as framing, addressing, and flow control! " Second layer of the OSI reference model (data link layer) or the IEEE 802 reference model (which divides data link layer into logical link control and medium access control layer)! Fundamentals of Wireless Sensor Networks: Theory and Practice Waltenegus Dargie and Christian Poellabauer © 2010 John Wiley & Sons Ltd. -

Ethernet Explained
Technical Note TN_157 Ethernet Explained Version 1.0 Issue Date: 2015-03-23 The FTDI FT900 32 bit MCU series, provides for high data rate, computationally intensive data transfers. One of the interfaces used for this high speed communication is Ethernet. This application note discusses some of the key features of an Ethernet link and how the FT900 assists in establishing the link. Use of FTDI devices in life support and/or safety applications is entirely at the user’s risk, and the user agrees to defend, indemnify and hold FTDI harmless from any and all damages, claims, suits or expense resulting from such use. Future Technology Devices International Limited (FTDI) Unit 1, 2 Seaward Place, Glasgow G41 1HH, United Kingdom Tel.: +44 (0) 141 429 2777 Fax: + 44 (0) 141 429 2758 Web Site: http://ftdichip.com Copyright © 2015 Future Technology Devices International Limited Technical Note TN_157 Ethernet Explained Version 1.0 Document Reference No.: FT_001105 Clearance No.: FTDI# 442 Table of Contents 1 Introduction .................................................................................................................................... 3 1.1 Scope ....................................................................................................................................... 3 2 What is Ethernet? ........................................................................................................................... 4 2.1 Speeds .................................................................................................................................... -

Fast Ethernet Hub Instruction Leaflet 5 Port Hub RS Stock No
Issued March 1998 10772 Fast Ethernet Hub Instruction Leaflet 5 port hub RS stock no. 288-5825 Table of contents Page 1.0 Introduction______________________________________________2 1.1 Inspecting the package and product __________________________________2 1.2 Product description ________________________________________________2 1.2.1 Ports 1-5: 100Mbps shared ports ________________________________3 1.2.2 Port 6: 10Mbps or 100Mbps switched port________________________3 1.3 Features and Benefits ________________________________________________3 1.4 Applications________________________________________________________4 2.0 Installation ______________________________________________6 2.1 Locating the hub __________________________________________________6 2.2 Ethernet media connections __________________________________________6 2.3 Collision domain diameter __________________________________________6 2.4 Connections to auto-negotiation 10/100 NICs____________________________9 2.5 Powering the Hub __________________________________________________9 3.0 Operation ______________________________________________9 3.1 Functionality ______________________________________________________9 3.1.1 Filtering and forwarding________________________________________9 3.1.2 Address learning (address table maintenance) __________________10 3.1.3 Throughput increase__________________________________________10 3.1.4 Software transparency ________________________________________11 3.2 LED’s ____________________________________________________________11 3.3 100Mb -
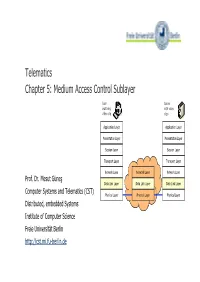
Medium Access Control Sublayer
Telematics Chapter 5: Medium Access Control Sublayer User Server watching with video Beispielbildvideo clip clips Application Layer Application Layer Presentation Layer Presentation Layer Session Layer Session Layer Transport Layer Transport Layer Network Layer Network Layer Network Layer Prof. Dr. Mesut Güneş Data Link Layer Data Link Layer Data Link Layer Computer Systems and Telematics (CST) Physical Layer Physical Layer Physical Layer Distributed, embedded Systems Institute of Computer Science Freie Universität Berlin http://cst.mi.fu-berlin.de Contents ● Design Issues ● Metropolitan Area Networks ● Network Topologies (()MAN) ● The Channel Allocation Problem ● Wide Area Networks (WAN) ● Multiple Access Protocols ● Frame Relay ● Ethernet ● ATM ● IEEE 802.2 – Logical Link Control ● SDH ● Token Bus ● Network Infrastructure ● Token Ring ● Virtual LANs ● Fiber Distributed Data Interface ● Structured Cabling Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.2 Design Issues Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.3 Design Issues ● Two kinds of connections in networks ● Point-to-point connections OSI Reference Model ● Broadcast (Multi-access channel, Application Layer Random access channel) Presentation Layer ● In a network with broadcast Session Layer connections ● Who gets the channel? Transport Layer Network Layer ● PtProtoco ls use dtdtd to determ ine w ho gets next access to the channel Data Link Layer ● Medium Access Control (()MAC) sublay er Phy sical Laye r Prof. Dr. Mesut Güneş ▪ cst.mi.fu-berlin.de ▪ Telematics ▪ Chapter 5: Medium Access Control Sublayer 5.4 Network Types for the Local Rang e ● LLC layer: uniform interface and same frame format to upper layers ● MAC layer: defines medium access - LLC IEEE 802.2 Logical Link Control .. -

515 a Access Control List , 184–187, 200, 289, 294, 404 Control Matrix
Index A B Access Bandwidth , 8, 10, 11, 13, 27, 40, 85, 133, 278, control list , 184–187, 200, 289, 294, 404 281, 327, 388, 392, 393, 398, 403, 415, control matrix , 185–186 457, 467, 474 mandatory , 189, 190, 197, 352 Base-T , 37 role-based , 185–188, 477 Base-X , 37 rule-based , 185, 188–189 Bastion , 248, 251, 262–264, 268 Activism , 115, 491, 497 Biometrics , 43, 53, 192–193, 204, 208, Advocacy , 339, 497 209, 305 Alert noti fi er , 279–280 Blue box , 112, 113 Amplitude , 8, 391 Bluetooth , 40, 400–402, 408, 419, 432, 433, Annualized loss , 159–160 438, 440–442 Anomaly , 272, 275–277, 279, 291 Bridge , 3, 13, 24, 25, 28–31, 33, 35, 141, 248, ARPANET , 68, 113 259, 293, 396 Asynchronous token , 211 Buffer over fl ow , 63, 67, 78, 110 Asynchronous transfer mode (ATM) , 23, 25, 38–40, 379, 395 Auditing , 56, 145–147, 165–167, 183, 204, C 261, 290, 352, 384 Carrier sense multiple access (CSMA) , Authentication 36, 401 anonymous , 209, 217, 220 CASPR. See Commonly Accepted Security DES , 216 Practices and Regulations (CASPR) dial-in , 215–217 CERT. See Computer Emergency Response header , 374, 375 Team (CERT) Kerberos , 214–215, 366–369 Certi fi cate authority , 213, 234, 236, 237, 239, null , 216, 405 241, 364, 366, 506, 509 policy , 218–219 Certi fi cation protocols , 214, 216, 218, 317, 366, process , 152, 164–165 382–384, 425 security , 145, 146, 164–165 remote , 209, 215–218, 383–384 Chain of custody , 302, 306, 313 Unix , 216 Challenge-response , 204, 210–212, 216, 363 Authenticator , 203, 204, 206, 207, 209, Cipher 211, 215, 216 feedback , 225 Authority registration , 240, 241 specs , 370, 371 Authorization Cladding , 12 coarse grain , 200 Coaxial cable , 11, 150, 394 fi ne grain , 200 Code Red , 68, 78, 98, 114, 329, 331, 332 granularity , 198, 199 Common criteria (CC) , 349–350 Availability , 6, 10, 85, 93, 95, 98, 109, 121, 122, Commonly Accepted Security Practices 164, 165, 201, 292, 298, 353, 392, 393, and Regulations (CASPR) , 56 422, 424, 448, 460, 467, 474–486, 504 Communicating element , 236, 237 J.M.