Surround SCM Installation Guide V2017.1
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Useful Tools for Game Making
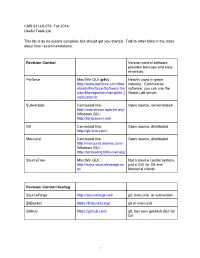
CMS.611J/6.073 Fall 2014 Useful Tools List This list is by no means complete, but should get you started. Talk to other folks in the class about their recommendations. Revision Control Version control software, provides backups and easy reversion. Perforce Mac/Win GUI (p4v): Heavily used in game http://www.perforce.com/dow industry. Commercial nloads/Perforce-Software-Ver software; you can use the sion-Management/complete_l Game Lab server. ist/Customer Subversion Command line: Open source, server-based http://subversion.apache.org/ Windows GUI: http://tortoisesvn.net/ Git Command line: Open source, distributed http://git-scm.com/ Mercurial Command line: Open source, distributed http://mercurial.selenic.com/ Windows GUI: http://tortoisehg.bitbucket.org/ SourceTree Mac/Win GUI: Not a source control system, http://www.sourcetreeapp.co just a GUI for Git and m/ Mercurial clients Revision Control Hosting SourceForge http://sourceforge.net/ git, mercurial, or subversion BitBucket https://bitbucket.org/ git or mercurial GitHub https://github.com/ git, has own (painful) GUI for Git 1 Image Editing MSPaint Windows, pre-installed Surprisingly useful quick pixel art editor (esp for prototypes) Paint.NET Windows, About as easy as MSPaint, but http://www.getpaint.net/download much more powerful .html Photoshop Mac, Windows New Media Center, 26-139 GIMP Many platforms, Easier than photoshop, at http://www.gimp.org/downloads/ least. Sound GarageBand Mac New Media Center, 26-139 Audacity Many platforms, Free, open source. http://audacity.sourceforge.ne -

Seapine ALM Reporting Platform Database Reference Guide V2016.1
Seapine ALM Data Warehouse Database Reference Guide Version 2016.1 Contents Key entities ................................................................................................................................................................... 1 Repository ................................................................................................................................................................. 1 License Server .......................................................................................................................................................... 1 QA Wizard Pro .......................................................................................................................................................... 1 Surround SCM ........................................................................................................................................................... 1 TestTrack ................................................................................................................................................................... 2 Data dictionary ............................................................................................................................................................. 5 Table: LS_AUTHENTICATION_METHOD ................................................................................................................ 5 Table: LS_EMAIL ..................................................................................................................................................... -

Jenkins Job Builder Documentation Release 3.10.0
Jenkins Job Builder Documentation Release 3.10.0 Jenkins Job Builder Maintainers Aug 23, 2021 Contents 1 README 1 1.1 Developers................................................1 1.2 Writing a patch..............................................2 1.3 Unit Tests.................................................2 1.4 Installing without setup.py........................................2 2 Contents 5 2.1 Quick Start Guide............................................5 2.1.1 Use Case 1: Test a job definition................................5 2.1.2 Use Case 2: Updating Jenkins Jobs...............................5 2.1.3 Use Case 3: Working with JSON job definitions........................6 2.1.4 Use Case 4: Deleting a job...................................6 2.1.5 Use Case 5: Providing plugins info...............................6 2.2 Installation................................................6 2.2.1 Documentation.........................................7 2.2.2 Unit Tests............................................7 2.2.3 Test Coverage..........................................7 2.3 Configuration File............................................7 2.3.1 job_builder section.......................................8 2.3.2 jenkins section.........................................9 2.3.3 hipchat section.........................................9 2.3.4 stash section...........................................9 2.3.5 __future__ section.......................................9 2.4 Running.................................................9 2.4.1 Test Mode........................................... -

Visual Build Help
Visual Build Professional User's Manual Copyright © 1999-2021 Kinook Software, Inc. Contents I Table of Contents Part I Introduction 1 1 Overview ................................................................................................................................... 1 2 Why Visual................................................................................................................................... Build? 1 3 New Features................................................................................................................................... 2 Version 4 .......................................................................................................................................................... 2 Version 5 .......................................................................................................................................................... 3 Version 6 .......................................................................................................................................................... 4 Version 7 .......................................................................................................................................................... 7 Version 8 .......................................................................................................................................................... 9 Version 9 ......................................................................................................................................................... -

DVCS Or a New Way to Use Version Control Systems for Freebsd
Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions DVCS or a new way to use Version Control Systems for FreeBSD Ollivier ROBERT <[email protected]> BSDCan 2006 Ottawa, Canada May, 12-13th, 2006 Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions Agenda 1 Brief history of VCS 2 FreeBSD context & gures 3 Is Arch/baz suited for FreeBSD? 4 Mercurial to the rescue 5 New processes & policies needed 6 Conclusions Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions The ancestors: SCCS, RCS File-oriented Use a subdirectory to store deltas and metadata Use lock-based architecture Support shared developments through NFS (fragile) SCCS is proprietary (System V), RCS is Open Source a SCCS clone exists: CSSC You can have a central repository with symlinks (RCS) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS, the de facto VCS for the free world Initially written as shell wrappers over RCS then rewritten in C Centralised server Easy UI Use sandboxes to avoid locking Simple 3-way merges Can be replicated through CVSup or even rsync Extensive documentation (papers, websites, books) Free software and used everywhere (SourceForge for example) Ollivier ROBERT <[email protected]> DVCS or a new way to use Version Control Systems for FreeBSD Brief history of VCS FreeBSD context & gures Is Arch/baz suited for FreeBSD? Mercurial to the rescue New processes & policies needed Conclusions CVS annoyances and aws BUT.. -

Helix Authentication Service Administrator Guide 2021.1 May 2021 Copyright © 2020-2021 Perforce Software, Inc
Helix Authentication Service Administrator Guide 2021.1 May 2021 Copyright © 2020-2021 Perforce Software, Inc.. All rights reserved. All software and documentation of Perforce Software, Inc. is available from www.perforce.com. You can download and use Perforce programs, but you can not sell or redistribute them. You can download, print, copy, edit, and redistribute the documentation, but you can not sell it, or sell any documentation derived from it. You can not modify or attempt to reverse engineer the programs. This product is subject to U.S. export control laws and regulations including, but not limited to, the U.S. Export Administration Regulations, the International Traffic in Arms Regulation requirements, and all applicable end-use, end-user and destination restrictions. Licensee shall not permit, directly or indirectly, use of any Perforce technology in or by any U.S. embargoed country or otherwise in violation of any U.S. export control laws and regulations. Perforce programs and documents are available from our Web site as is. No warranty or support is provided. Warranties and support, along with higher capacity servers, are sold by Perforce. Perforce assumes no responsibility or liability for any errors or inaccuracies that might appear in this book. By downloading and using our programs and documents you agree to these terms. Perforce and Inter-File Branching are trademarks of Perforce. All other brands or product names are trademarks or registered trademarks of their respective companies or organizations. Contents How to use -

Staying out of the Swamp
Staying out of the server swamp Richard Baum Perforce Software October, 2001 Contents Introduction How do I tell if I'm in the swamp? Is your system CPU bound? Is your system memory bound? Is your system I/O bound? How can Perforce cause server swamp? Network Attached Storage Confusing and complex client mappings Background processes The Perforce error log Gigantic operations Conclusion Introduction Perforce runs extremely well when it is given the right resources. A Perforce server does not generally require much CPU. Memory and disk requirements correspond to the amount of data you wish to store. Conditions can sometimes conspire to change a well-performing server into a poorly-performing one. This talk will cover some of the things to watch out for to keep your Perforce server happy and healthy. The object of this talk is to familiarize you with what to look for so you can determine where the problem lies, and what to do so you can remedy the problem. In general, performance that a user will see is limited by the I/O bandwidth of the server and the speed of its connection with a client machine. A server that appears to not be responding in its typically speedy fashion may, in fact, be swamped with data and requests for data. How do I tell if I'm in the swamp? If you suspect that your Perforce server is swamped, the first things to do are to check whether it is, in fact, running, and to examine the machine that hosts the server for any obvious signs of a problem. -

Analiza in Prenova Sistema Upravljanja Z Dokumentacijo V Podjetju
UNIVERZA V LJUBLJANI FAKULTETA ZA RA ČUNALNIŠTVO IN INFORMATIKO Aleksander Pahor ANALIZA IN PRENOVA SISTEMA UPRAVLJANJA Z DOKUMENTACIJO V PODJETJU Diplomsko delo na visokošolskem strokovnem študiju Mentor: dr. Mojca Ciglari č Ljubljana, 2009 I Z J A V A O A V T O R S T V U diplomskega dela Spodaj podpisani/-a ____________________________________, z vpisno številko ____________________________________, sem avtor/-ica diplomskega dela z naslovom: _________________________________________________________________________ _________________________________________________________________________ S svojim podpisom zagotavljam, da: • sem diplomsko delo izdelal/-a samostojno pod mentorstvom (naziv, ime in priimek) ___________________________________________________________________ in somentorstvom (naziv, ime in priimek) ___________________________________________________________________ • so elektronska oblika diplomskega dela, naslov (slov., angl.), povzetek (slov., angl.) ter klju čne besede (slov., angl.) identi čni s tiskano obliko diplomskega dela • soglašam z javno objavo elektronske oblike diplomskega dela v zbirki »Dela FRI«. V Ljubljani, dne ______________ Podpis avtorja/-ice:______________________ Zahvala V prvi vrsti se zahvaljujem svoji mentorici dr. Mojci Ciglari č za potrpljenje, ki ga je izkazala z menoj. Predvsem cenim to, da je bila pripravljena z nekaterimi izdelki po čakati, kar je bilo pogojeno z mojim delom, ki velikokrat ne dopuš ča, da bi se svojim ostalim obveznostim posvetil toliko, kolikor bi si zaslužile. Zahvaljujem se vsem v podjetju Hermes Softlab d.d., ki so mi vedno stali ob strani in mi pomagali odrasti strokovno, poslovno in osebno. Davorju Hvali, ki me je vzel v službo in vsem mojim nadrejenim: Alešu Pestotniku, Primožu Svetku, Mihi Urbaniji in Alešu Koširju, ki so mi zaupali vedno bolj odgovorne naloge, ki so mi omogo čile videti svet in delati na mnogih projektih in podjetjih. -

Coverity Static Analysis
Coverity Static Analysis Quickly find and fix Overview critical security and Coverity® gives you the speed, ease of use, accuracy, industry standards compliance, and quality issues as you scalability that you need to develop high-quality, secure applications. Coverity identifies code critical software quality defects and security vulnerabilities in code as it’s written, early in the development process when it’s least costly and easiest to fix. Precise actionable remediation advice and context-specific eLearning help your developers understand how to fix their prioritized issues quickly, without having to become security experts. Coverity Benefits seamlessly integrates automated security testing into your CI/CD pipelines and supports your existing development tools and workflows. Choose where and how to do your • Get improved visibility into development: on-premises or in the cloud with the Polaris Software Integrity Platform™ security risk. Cross-product (SaaS), a highly scalable, cloud-based application security platform. Coverity supports 22 reporting provides a holistic, more languages and over 70 frameworks and templates. complete view of a project’s risk using best-in-class AppSec tools. Coverity includes Rapid Scan, a fast, lightweight static analysis engine optimized • Deployment flexibility. You for cloud-native applications and Infrastructure-as-Code (IaC). Rapid Scan runs decide which set of projects to do automatically, without additional configuration, with every Coverity scan and can also AppSec testing for: on-premises be run as part of full CI builds with conventional scan completion times. Rapid Scan can or in the cloud. also be deployed as a standalone scan engine in Code Sight™ or via the command line • Shift security testing left. -

Opinnäytetyö Ohjeet
Lappeenrannan–Lahden teknillinen yliopisto LUT School of Engineering Science Tietotekniikan koulutusohjelma Kandidaatintyö Mikko Mustonen PARHAITEN OPETUSKÄYTTÖÖN SOVELTUVAN VERSIONHALLINTAJÄRJESTELMÄN LÖYTÄMINEN Työn tarkastaja: Tutkijaopettaja Uolevi Nikula Työn ohjaaja: Tutkijaopettaja Uolevi Nikula TIIVISTELMÄ LUT-yliopisto School of Engineering Science Tietotekniikan koulutusohjelma Mikko Mustonen Parhaiten opetuskäyttöön soveltuvan versionhallintajärjestelmän löytäminen Kandidaatintyö 2019 31 sivua, 8 kuvaa, 2 taulukkoa Työn tarkastajat: Tutkijaopettaja Uolevi Nikula Hakusanat: versionhallinta, versionhallintajärjestelmä, Git, GitLab, SVN, Subversion, oppimateriaali Keywords: version control, version control system, Git, GitLab, SVN, Subversion, learning material LUT-yliopistossa on tietotekniikan opetuksessa käytetty Apache Subversionia versionhallintaan. Subversionin käyttö kuitenkin johtaa ylimääräisiin ylläpitotoimiin LUTin tietohallinnolle. Lisäksi Subversionin julkaisun jälkeen on tullut uusia versionhallintajärjestelmiä ja tässä työssä tutkitaankin, olisiko Subversion syytä vaihtaa johonkin toiseen versionhallintajärjestelmään opetuskäytössä. Työn tavoitteena on löytää opetuskäyttöön parhaiten soveltuva versionhallintajärjestelmä ja tuottaa sille opetusmateriaalia. Työssä havaittiin, että Git on suosituin versionhallintajärjestelmä ja se on myös suhteellisen helppo käyttää. Lisäksi GitLab on tutkimuksen mukaan Suomen yliopistoissa käytetyin ja ominaisuuksiltaan ja hinnaltaan sopivin Gitin web-käyttöliittymä. Näille tehtiin -

Teamcity 7.1 Documentation.Pdf
1. TeamCity Documentation . 4 1.1 What's New in TeamCity 7.1 . 5 1.2 What's New in TeamCity 7.0 . 14 1.3 Getting Started . 26 1.4 Concepts . 30 1.4.1 Agent Home Directory . 31 1.4.2 Agent Requirements . 32 1.4.3 Agent Work Directory . 32 1.4.4 Authentication Scheme . 33 1.4.5 Build Agent . 33 1.4.6 Build Artifact . 34 1.4.7 Build Chain . 35 1.4.8 Build Checkout Directory . 36 1.4.9 Build Configuration . 37 1.4.10 Build Configuration Template . 38 1.4.11 Build Grid . 39 1.4.12 Build History . 40 1.4.13 Build Log . 40 1.4.14 Build Number . 40 1.4.15 Build Queue . 40 1.4.16 Build Runner . 41 1.4.17 Build State . 41 1.4.18 Build Tag . 42 1.4.19 Build Working Directory . 43 1.4.20 Change . 43 1.4.21 Change State . 43 1.4.22 Clean Checkout . 44 1.4.23 Clean-Up . 45 1.4.24 Code Coverage . 46 1.4.25 Code Duplicates . 47 1.4.26 Code Inspection . 47 1.4.27 Continuous Integration . 47 1.4.28 Dependent Build . 47 1.4.29 Difference Viewer . 49 1.4.30 Guest User . 50 1.4.31 History Build . 51 1.4.32 Notifier . 51 1.4.33 Personal Build . 52 1.4.34 Pinned Build . 52 1.4.35 Pre-Tested (Delayed) Commit . 52 1.4.36 Project . 53 1.4.37 Remote Run . .. -

Main Brochure2.Indd
Automate your Build Process . Powerful and fl exible user interface . Automate version control, compilers, install builders, deployment, testing, notifi cations, and lots more... Dynamic build process using fl ow control, iterators, loops, and exceptions . Full debugger built in - breakpoints, variable watches, live logging . Script events for every action to customise your build process Hierarchical Logging Error Handling FinalBuilder ActionStudio . The log is presented in the same . Easily detect and handle errors during . Allows development of native FinalBuilder hierarchy as your build process your build process actions . Optionally view live log output . Exception handling actions . Includes property page designer and as the build runs include: TRY, CATCH, FINALLY code editor with syntax highlighting . Builds logs are automatically . Control the fl ow of your build process . Develop actions in VBScript, JScript, COM, archived and recover from errors or any .Net language such as C#, VB.Net or Delphi for .Net . Export the log as XML, HTML, or . Unhandled errors trigger the OnFailure Text action list . Included in all editions of FinalBuilder VSoft Technologies Pty Ltd http://www.fi nalbuilder.com ABN: 82 078 466 092 P.O. Box 126, Erindale Centre, ACT 2903, Australia salesinfo@fi nalbuilder.com Phone: +61 2 6282 7488, Fax +61 2 6282 7588 news://news.fi nalbuilder.com FinalBuilder Integrates with your version control system . Microsoft TeamSystem Use a GUI instead of XML fi les . Microsoft Visual SourceSafe . Perforce Although FinalBuilder uses an XML based fi le format, you . IBM Rational ClearCase don’t need to understand it or even look at it. The FinalBuilder . QSC Team Coherence GUI allows you to quickly and easily create a build process .