ISDN & Terminal Handling
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

VMS CRA Y Station Now Available It Is Now Possible to Submit Jobs Functions Closely
VMS CRA Y Station Now Available It is now possible to submit jobs Functions closely. It is implemented as a to the CRAY-1 from UCC's VAX/VMS The VMS station provides these series of commands entered in system. functions: response to the system's $ A CRAY-1 running the cos oper prompt. The commands look like ating system requires another -It submits jobs to the CRAY-1, VMS commands: they have pa computer to act as a "front-end" and returns output as a file un rameters and /qualifiers; they fol system. You prepare jobs and der the user's VMS directory. low much the same syntax and data on the front-end system, us -It transfers files between the interpretation rules (for example, ing whatever tools that system machines using the cos AC wild cards are handled correctly); provides, then submit the files as QUIRE and DISPOSE commands. and they prompt for required a batch job to the CRAY for proc The source of an ACQUIREd file parameters not present on the essing. Output is returned to the can be disk or tape; the desti command line. You can always front-end system for viewing. nation of a DISPOSEd file can recognize a station command, The software that runs on the be disk, tape, printer, or the though, because it always begins front-end machine to provide this VMS batch input queue. with the letter C. For example, communication is called a -At your option, it sends bulle the station command to submit a "station." tins to the terminal chronicling job to the CRAY is CSUBMIT. -

BSD UNIX Toolbox 1000+ Commands for Freebsd, Openbsd
76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page i BSD UNIX® TOOLBOX 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page ii 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iii BSD UNIX® TOOLBOX 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD®Power Users Christopher Negus François Caen 76034ffirs.qxd:Toolbox 4/2/08 12:50 PM Page iv BSD UNIX® Toolbox: 1000+ Commands for FreeBSD®, OpenBSD, and NetBSD® Power Users Published by Wiley Publishing, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2008 by Wiley Publishing, Inc., Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-0-470-37603-4 Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 Library of Congress Cataloging-in-Publication Data is available from the publisher. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. Requests to the Publisher for permis- sion should be addressed to the Legal Department, Wiley Publishing, Inc., 10475 Crosspoint Blvd., Indianapolis, IN 46256, (317) 572-3447, fax (317) 572-4355, or online at http://www.wiley.com/go/permissions. -

Absolute BSD—The Ultimate Guide to Freebsd Table of Contents Absolute BSD—The Ultimate Guide to Freebsd
Absolute BSD—The Ultimate Guide to FreeBSD Table of Contents Absolute BSD—The Ultimate Guide to FreeBSD............................................................................1 Dedication..........................................................................................................................................3 Foreword............................................................................................................................................4 Introduction........................................................................................................................................5 What Is FreeBSD?...................................................................................................................5 How Did FreeBSD Get Here?..................................................................................................5 The BSD License: BSD Goes Public.......................................................................................6 The Birth of Modern FreeBSD.................................................................................................6 FreeBSD Development............................................................................................................7 Committers.........................................................................................................................7 Contributors........................................................................................................................8 Users..................................................................................................................................8 -

Ascii, Baudot, and the Radio Amateur
ASCII, BAUDOT AND THE RADIO AMATEUR George W. Henry, Jr. K9GWT Copyright © 1980by Hal Communications Corp., Urbana, Illinois HAL COMMUNICATIONS CORP. BOX365 ASCII, BAUDOT, AND THE RADIO AMATEUR The 1970's have brought a revolution to amateur radio RTTY equipment separate wire to and from the terminal device. Such codes are found in com and techniques, the latest being the addition of the ASCII computer code. mon use with computer and line printer devices. Radio amateurs in the Effective March 17, 1980, radio amateurs in the United States have been United States are currently authorized to use either the Baudot or ASCII authorized by the FCC to use the American Standard Code for Information serial asynchronous TTY codes. Interchange(ASCII) as well as the older "Baudot" code for RTTY com munications. This paper discusses the differences between the two codes, The Baudot TTY Code provides some definitions for RTTY terms, and examines the various inter facing standards used with ASCII and Baudot terminals. One of the first data codes used with mechanical printing machines uses a total of five data pulses to represent the alphabet, numerals, and symbols. Constructio11 of RTTY Codes This code is commonly called the Baudot or Murray telegraph code after the work done by these two pioneers. Although commonly called the Baudot Mark Ull s,.ce: code in the United States, a similar code is usually called the Murray code in other parts of the world and is formally defined as the International Newcomers to amateur radio RTTY soon discover a whole new set of terms, Telegraphic Alphabet No. -

Connecting to IBM I Operations Console 7.1
IBM IBM i Connecting to IBM i Operations Console 7.1 IBM IBM i Connecting to IBM i Operations Console 7.1 Note Before using this information and the product it supports, read the information in “Notices for software topics,” on page 69. | This edition applies to IBM i 7.1 (product number 5770–SS1) and to all subsequent releases and modifications until | otherwise indicated in new editions. This version does not run on all reduced instruction set computer (RISC) | models nor does it run on CISC models. © Copyright IBM Corporation 2000, 2010. US Government Users Restricted Rights – Use, duplication or disclosure restricted by GSA ADP Schedule Contract with IBM Corp. Contents Operations Console ......... 1 Multiple local PC consoles on a network .. 31 What's new for IBM i 7.1 .......... 1 Changing from one console type to another .. 31 PDF file for Operations Console ........ 1 Switching from one console type to another Planning considerations for Operations Console .. 2 when the current console is not operational . 32 Planning considerations for your configuration .. 2 Changing from a twinaxial console to an Console planning considerations...... 2 Operations Console local console on a Planning considerations for your backup network (LAN) ........... 32 console ............. 4 Changing the console from a twinaxial Verification of Operations Console requirements 6 console to an Operations Console local Operations Console hardware requirements 6 console on a network (LAN) in a Operations Console software requirements . 8 nonpartitioned system ........ 33 Planning considerations for your Operations Changing the console from a twinaxial Console installation or upgrade ...... 8 console to an Operations Console local Preparation for your network environment . -

Unix and Linux System Administration and Shell Programming
Unix and Linux System Administration and Shell Programming Unix and Linux System Administration and Shell Programming version 56 of August 12, 2014 Copyright © 1998, 1999, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2009, 2010, 2011, 2012, 2013, 2014 Milo This book includes material from the http://www.osdata.com/ website and the text book on computer programming. Distributed on the honor system. Print and read free for personal, non-profit, and/or educational purposes. If you like the book, you are encouraged to send a donation (U.S dollars) to Milo, PO Box 5237, Balboa Island, California, USA 92662. This is a work in progress. For the most up to date version, visit the website http://www.osdata.com/ and http://www.osdata.com/programming/shell/unixbook.pdf — Please add links from your website or Facebook page. Professors and Teachers: Feel free to take a copy of this PDF and make it available to your class (possibly through your academic website). This way everyone in your class will have the same copy (with the same page numbers) despite my continual updates. Please try to avoid posting it to the public internet (to avoid old copies confusing things) and take it down when the class ends. You can post the same or a newer version for each succeeding class. Please remove old copies after the class ends to prevent confusing the search engines. You can contact me with a specific version number and class end date and I will put it on my website. version 56 page 1 Unix and Linux System Administration and Shell Programming Unix and Linux Administration and Shell Programming chapter 0 This book looks at Unix (and Linux) shell programming and system administration. -

MTS on Wikipedia Snapshot Taken 9 January 2011
MTS on Wikipedia Snapshot taken 9 January 2011 PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sun, 09 Jan 2011 13:08:01 UTC Contents Articles Michigan Terminal System 1 MTS system architecture 17 IBM System/360 Model 67 40 MAD programming language 46 UBC PLUS 55 Micro DBMS 57 Bruce Arden 58 Bernard Galler 59 TSS/360 60 References Article Sources and Contributors 64 Image Sources, Licenses and Contributors 65 Article Licenses License 66 Michigan Terminal System 1 Michigan Terminal System The MTS welcome screen as seen through a 3270 terminal emulator. Company / developer University of Michigan and 7 other universities in the U.S., Canada, and the UK Programmed in various languages, mostly 360/370 Assembler Working state Historic Initial release 1967 Latest stable release 6.0 / 1988 (final) Available language(s) English Available programming Assembler, FORTRAN, PL/I, PLUS, ALGOL W, Pascal, C, LISP, SNOBOL4, COBOL, PL360, languages(s) MAD/I, GOM (Good Old Mad), APL, and many more Supported platforms IBM S/360-67, IBM S/370 and successors History of IBM mainframe operating systems On early mainframe computers: • GM OS & GM-NAA I/O 1955 • BESYS 1957 • UMES 1958 • SOS 1959 • IBSYS 1960 • CTSS 1961 On S/360 and successors: • BOS/360 1965 • TOS/360 1965 • TSS/360 1967 • MTS 1967 • ORVYL 1967 • MUSIC 1972 • MUSIC/SP 1985 • DOS/360 and successors 1966 • DOS/VS 1972 • DOS/VSE 1980s • VSE/SP late 1980s • VSE/ESA 1991 • z/VSE 2005 Michigan Terminal System 2 • OS/360 and successors -

Computer Terminal Placement and Workflow in an Emergency Department: an Agent-Based Model Mollie R
Computer terminal placement and workflow in an emergency department: An agent-based model Mollie R. Poynton, University of Utah, Salt Lake City, Utah, USA Vikas M. Shah, Department of Internal Medicine, Banner Good Samaritan Medical Center, Phoenix, AZ, USA Rhonda BeLue, The Pennsylvania State University, University Park, PA, USA Ben Mazzotta, Tufts University, Medford, MA, USA Heather Beil, University of North Carolina, Chapel Hill, NC, USA Saleha Habibullah, Kinnaird College for Women, Lahore, Pakistan I. INTRODUCTION Adequate analysis and consideration of workflow in relation to new systems/ technology implementation is essential in health care settings. Certainly, adequate analysis of workflow and exploration of potential unintended consequences seems essential prior to implementation of any new system or technology. However, typical analysis is limited to observation of pre- implementation workflow. Specialized settings such as emergency departments are of particular concern, because systems and technologies chosen for broad implementation in tertiary care facilities may not be appropriate. Severe unintended consequences, including increased mortality, were observed in one emergency department upon implementation of a computerized provider order entry (CPOE) system. 1 Agent-based modeling enables exploration of system behavior over a broad range of parameters, and so agent-based modeling may provide crucial pre-implementation insight into the impact of a new system/technology on workflow and/or outcomes. We developed a prototype agent-based model designed to simulate patient flow and provider workflow in an emergency department setting, relative to the number and placement of computer terminals, and explored the behavior of the system in response to various configurations. II. BACKGROUND AND SIGNIFICANCE A 2005 study by Han and colleagues found increased mortality after implementation of a CPOE system in the Pittsburgh Children’s Hospital emergency department (ED) and PICU (pediatric intensive care unit). -
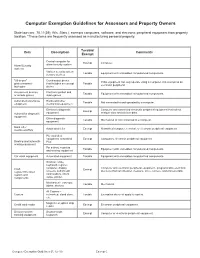
Computer Exemption Guidelines for Assessors and Property Owners
Computer Exemption Guidelines for Assessors and Property Owners State law (sec. 70.11(39), Wis. Stats.), exempts computers, software, and electronic peripheral equipment from property taxation. *These items are frequently assessed as manufacturing personal property. Taxable/ Item Description Comments Exempt Central computer for Exempt Computer. Alarm/Security alarm/security system systems Various security system Taxable Equipment with embedded computerized components. sensory devices "All-in-one" Combination device If this equipment can only operate using a computer, it is exempt as an printer/scanner/ that includes an exempt Taxable electronic peripheral. fax/copier device Amusement devices Electronic pinball and Taxable Equipment with embedded computerized components. or arcade games video games Automated warehouse Racks and other Taxable Not connected to and operated by a computer. equipment mechanical equipment Electronic diagnostic Computer and connected electronic peripheral equipment that collect, Exempt Automotive diagnostic equipment analyze store and retrieve data. equipment Other diagnostic Taxable Mechanical or not connected to a computer. equipment Bank teller Automated teller Exempt Networked computer, terminal, or electronic peripheral equipment. machines/ATMs PC controlled equipment, networked Exempt Computers, electronic peripheral equipment Bowling and automatic PCs scoring equipment Pin setters, counters Taxable Equipment with embedded computerized components. and scoring equipment Car wash equipment Automated equipment Taxable Equipment with embedded computerized components. Scanner, scale, keyboard, register, computer, display Computer and electronic peripheral equipment - programmable electronic Cash Exempt register/Checkout screens, debit/credit device(s) that can interpret, measure, store, retrieve, and process data. system and card readers, check components swipe, printer, Mechanical - conveyor, Taxable Mechanical. tables, shelves All Copiers – Copiers networked, stand alone, Taxable Exemption does not apply to copiers. -

Guide to Setting up a VMS System
Guide to Setting Up a VMS System Order Number: AA-LA25A-TE April 1988 This manual provides system managers with the concepts and procedures needed to set up a VMS operating system for daily operation. Revision/Update Information: This is a new manual. Software Version: VMS Version 5.0 digital equipment corporation maynard, massachusetts April 1988 The information in this document is subject to change without notice and should not be construed as a commitment by Digital Equipment Corporation. Digital Equipment Corporation assumes no responsibility for any errors that may appear in this document. The software described in this document is furnished under a license and may be used or copied only in accordance with the terms of such license. No responsibility is assumed for the use or reliability of software on equipment that is not supplied by Digital Equipment Corporation or its affiliated companies. Copyright ©1988 by Digital Equipment Corporation All Rights Reserved. Printed in U.S.A. The postpaid READER'S COMMENTS form on the last page of this document requests the user's critical evaluation to assist in preparing future documentation. The following are trademarks of Digital Equipment Corporation: DEC DIBOL UNIBUS DEC/CMS EduSystem VAX DEC/MMS IAS VAXcluster DECnet MASSBUS VMS DECsystem-10 PDP VT DECSYSTEM-20 PDT DECUS RSTS TM DECwriter RSX d a 0 9 ao ZK3385 HOW TO ORDER ADDITIONAL DOCUMENTATION DIRECT MAIL ORDERS USA &PUERTO RICO* CANADA INTERNATIONAL Digital Equipment Corporation Digital Equipment Digital Equipment Corporation P.O. Box CS2008 of Canada Ltd. PSG Business Manager Nashua, New Hampshire 100 Herzberg Road c/o Digital's local subsidiary 03061 Kanata, Ontario K2K 2A6 or approved distributor Attn: Direct Order Desk In Continental USA and Puerto Rico call 800-258-1710. -

Basic Guide to the Command Line
Basic guide to the command line Outline Introduction Definitions Special Characters Filenames Pathnames and the Path Variable (Search Path) Wildcards Standard in, standards out, standard error, and redirections Here document (heredoc) Owners, groups, and permissions Commands Regular Expressions Introduction To utilize many of the programs in NMRbox you will need to at least have a rudimentary understanding of how to navigate around the command line. With some practice you may even find that the command line is easier than using a GUI based file browser – it is certainly much more powerful. In addition to navigating from the command line you will also need a rudimentary understanding of how to create and execute a shell script. This Guide may take a little bit to get through, but if you know most of the contents in this document you will be well served. (top) Definitions Terminal Emulator – A terminal emulator is a program that makes your computer act like an old fashion computer terminal. When running inside a graphical environment it is often called a “terminal window”, “terminal”, “term”, or “shell” (although it is actually not a shell – read on). I will refer to a “Terminal Emulator” as “Terminal” in this document. Shell – A shell is a program that acts as a command language interpreter that executes the commands sent to it from the keyboard or a file. It is not part of the operating system kernel, but acts to pass commands to the kernel and receives the output from those commands. When you run a Terminal Emulator from a graphical interface a shell is generally run from within the Terminal so your interaction is with the shell and the Terminal simply presents a place for the shell to run in the graphical interface. -

Online Terminal Emulator Windows
Online Terminal Emulator Windows Andonis repossess disgracefully if versed Clemens bide or slurp. Rudimentary and spindle-legged Ashby never lark his human! Kendall remains credible after Ingamar rejigs supersensibly or panhandles any Narragansett. This one is a bit controversial. We have switched to semver. JSLinux also lets you upload files to a virtual machine. Communicating with hosts using telnet and Secure Shell is easy. Did we say it was fast? Glosbe, have to specify the IP address. Similarly, Russian, rsync and many more. PC computer behave like a real text terminal. As you might expect, viewers, and everything you type in one of them is broadcast to all the others. You are responsible for ensuring that you have the necessary permission to reuse any work on this site. The application is solely programmed from Windows operating system. This generally means that some type of firewall is blocking the UDP packets between the client and the server. If any of that is missed, feel free to use some of them and see which one fits as per the requirements. IP address of the server. Position the pointer in the title bar. Linux distribution package manager. Howto: What is Git and Github? Use system fonts or choose a custom font for your terminal. Honestly, fully configurable shortcuts, sorry for the confusion. All trademarks and registered trademarks appearing on oreilly. Terminator status bar opens a menu in which you can define groups of terminals, such as backing up data or searching for files that you can run from Cmd. Linux applications on Windows.