Guide to Setting up a VMS System
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

VMS CRA Y Station Now Available It Is Now Possible to Submit Jobs Functions Closely
VMS CRA Y Station Now Available It is now possible to submit jobs Functions closely. It is implemented as a to the CRAY-1 from UCC's VAX/VMS The VMS station provides these series of commands entered in system. functions: response to the system's $ A CRAY-1 running the cos oper prompt. The commands look like ating system requires another -It submits jobs to the CRAY-1, VMS commands: they have pa computer to act as a "front-end" and returns output as a file un rameters and /qualifiers; they fol system. You prepare jobs and der the user's VMS directory. low much the same syntax and data on the front-end system, us -It transfers files between the interpretation rules (for example, ing whatever tools that system machines using the cos AC wild cards are handled correctly); provides, then submit the files as QUIRE and DISPOSE commands. and they prompt for required a batch job to the CRAY for proc The source of an ACQUIREd file parameters not present on the essing. Output is returned to the can be disk or tape; the desti command line. You can always front-end system for viewing. nation of a DISPOSEd file can recognize a station command, The software that runs on the be disk, tape, printer, or the though, because it always begins front-end machine to provide this VMS batch input queue. with the letter C. For example, communication is called a -At your option, it sends bulle the station command to submit a "station." tins to the terminal chronicling job to the CRAY is CSUBMIT. -

Ascii, Baudot, and the Radio Amateur
ASCII, BAUDOT AND THE RADIO AMATEUR George W. Henry, Jr. K9GWT Copyright © 1980by Hal Communications Corp., Urbana, Illinois HAL COMMUNICATIONS CORP. BOX365 ASCII, BAUDOT, AND THE RADIO AMATEUR The 1970's have brought a revolution to amateur radio RTTY equipment separate wire to and from the terminal device. Such codes are found in com and techniques, the latest being the addition of the ASCII computer code. mon use with computer and line printer devices. Radio amateurs in the Effective March 17, 1980, radio amateurs in the United States have been United States are currently authorized to use either the Baudot or ASCII authorized by the FCC to use the American Standard Code for Information serial asynchronous TTY codes. Interchange(ASCII) as well as the older "Baudot" code for RTTY com munications. This paper discusses the differences between the two codes, The Baudot TTY Code provides some definitions for RTTY terms, and examines the various inter facing standards used with ASCII and Baudot terminals. One of the first data codes used with mechanical printing machines uses a total of five data pulses to represent the alphabet, numerals, and symbols. Constructio11 of RTTY Codes This code is commonly called the Baudot or Murray telegraph code after the work done by these two pioneers. Although commonly called the Baudot Mark Ull s,.ce: code in the United States, a similar code is usually called the Murray code in other parts of the world and is formally defined as the International Newcomers to amateur radio RTTY soon discover a whole new set of terms, Telegraphic Alphabet No. -

Unix and Linux System Administration and Shell Programming
Unix and Linux System Administration and Shell Programming Unix and Linux System Administration and Shell Programming version 56 of August 12, 2014 Copyright © 1998, 1999, 2000, 2001, 2002, 2003, 2004, 2005, 2006, 2007, 2009, 2010, 2011, 2012, 2013, 2014 Milo This book includes material from the http://www.osdata.com/ website and the text book on computer programming. Distributed on the honor system. Print and read free for personal, non-profit, and/or educational purposes. If you like the book, you are encouraged to send a donation (U.S dollars) to Milo, PO Box 5237, Balboa Island, California, USA 92662. This is a work in progress. For the most up to date version, visit the website http://www.osdata.com/ and http://www.osdata.com/programming/shell/unixbook.pdf — Please add links from your website or Facebook page. Professors and Teachers: Feel free to take a copy of this PDF and make it available to your class (possibly through your academic website). This way everyone in your class will have the same copy (with the same page numbers) despite my continual updates. Please try to avoid posting it to the public internet (to avoid old copies confusing things) and take it down when the class ends. You can post the same or a newer version for each succeeding class. Please remove old copies after the class ends to prevent confusing the search engines. You can contact me with a specific version number and class end date and I will put it on my website. version 56 page 1 Unix and Linux System Administration and Shell Programming Unix and Linux Administration and Shell Programming chapter 0 This book looks at Unix (and Linux) shell programming and system administration. -

MTS on Wikipedia Snapshot Taken 9 January 2011
MTS on Wikipedia Snapshot taken 9 January 2011 PDF generated using the open source mwlib toolkit. See http://code.pediapress.com/ for more information. PDF generated at: Sun, 09 Jan 2011 13:08:01 UTC Contents Articles Michigan Terminal System 1 MTS system architecture 17 IBM System/360 Model 67 40 MAD programming language 46 UBC PLUS 55 Micro DBMS 57 Bruce Arden 58 Bernard Galler 59 TSS/360 60 References Article Sources and Contributors 64 Image Sources, Licenses and Contributors 65 Article Licenses License 66 Michigan Terminal System 1 Michigan Terminal System The MTS welcome screen as seen through a 3270 terminal emulator. Company / developer University of Michigan and 7 other universities in the U.S., Canada, and the UK Programmed in various languages, mostly 360/370 Assembler Working state Historic Initial release 1967 Latest stable release 6.0 / 1988 (final) Available language(s) English Available programming Assembler, FORTRAN, PL/I, PLUS, ALGOL W, Pascal, C, LISP, SNOBOL4, COBOL, PL360, languages(s) MAD/I, GOM (Good Old Mad), APL, and many more Supported platforms IBM S/360-67, IBM S/370 and successors History of IBM mainframe operating systems On early mainframe computers: • GM OS & GM-NAA I/O 1955 • BESYS 1957 • UMES 1958 • SOS 1959 • IBSYS 1960 • CTSS 1961 On S/360 and successors: • BOS/360 1965 • TOS/360 1965 • TSS/360 1967 • MTS 1967 • ORVYL 1967 • MUSIC 1972 • MUSIC/SP 1985 • DOS/360 and successors 1966 • DOS/VS 1972 • DOS/VSE 1980s • VSE/SP late 1980s • VSE/ESA 1991 • z/VSE 2005 Michigan Terminal System 2 • OS/360 and successors -

Computer Terminal Placement and Workflow in an Emergency Department: an Agent-Based Model Mollie R
Computer terminal placement and workflow in an emergency department: An agent-based model Mollie R. Poynton, University of Utah, Salt Lake City, Utah, USA Vikas M. Shah, Department of Internal Medicine, Banner Good Samaritan Medical Center, Phoenix, AZ, USA Rhonda BeLue, The Pennsylvania State University, University Park, PA, USA Ben Mazzotta, Tufts University, Medford, MA, USA Heather Beil, University of North Carolina, Chapel Hill, NC, USA Saleha Habibullah, Kinnaird College for Women, Lahore, Pakistan I. INTRODUCTION Adequate analysis and consideration of workflow in relation to new systems/ technology implementation is essential in health care settings. Certainly, adequate analysis of workflow and exploration of potential unintended consequences seems essential prior to implementation of any new system or technology. However, typical analysis is limited to observation of pre- implementation workflow. Specialized settings such as emergency departments are of particular concern, because systems and technologies chosen for broad implementation in tertiary care facilities may not be appropriate. Severe unintended consequences, including increased mortality, were observed in one emergency department upon implementation of a computerized provider order entry (CPOE) system. 1 Agent-based modeling enables exploration of system behavior over a broad range of parameters, and so agent-based modeling may provide crucial pre-implementation insight into the impact of a new system/technology on workflow and/or outcomes. We developed a prototype agent-based model designed to simulate patient flow and provider workflow in an emergency department setting, relative to the number and placement of computer terminals, and explored the behavior of the system in response to various configurations. II. BACKGROUND AND SIGNIFICANCE A 2005 study by Han and colleagues found increased mortality after implementation of a CPOE system in the Pittsburgh Children’s Hospital emergency department (ED) and PICU (pediatric intensive care unit). -
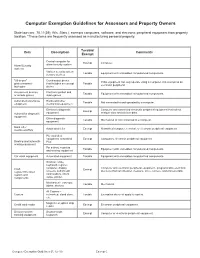
Computer Exemption Guidelines for Assessors and Property Owners
Computer Exemption Guidelines for Assessors and Property Owners State law (sec. 70.11(39), Wis. Stats.), exempts computers, software, and electronic peripheral equipment from property taxation. *These items are frequently assessed as manufacturing personal property. Taxable/ Item Description Comments Exempt Central computer for Exempt Computer. Alarm/Security alarm/security system systems Various security system Taxable Equipment with embedded computerized components. sensory devices "All-in-one" Combination device If this equipment can only operate using a computer, it is exempt as an printer/scanner/ that includes an exempt Taxable electronic peripheral. fax/copier device Amusement devices Electronic pinball and Taxable Equipment with embedded computerized components. or arcade games video games Automated warehouse Racks and other Taxable Not connected to and operated by a computer. equipment mechanical equipment Electronic diagnostic Computer and connected electronic peripheral equipment that collect, Exempt Automotive diagnostic equipment analyze store and retrieve data. equipment Other diagnostic Taxable Mechanical or not connected to a computer. equipment Bank teller Automated teller Exempt Networked computer, terminal, or electronic peripheral equipment. machines/ATMs PC controlled equipment, networked Exempt Computers, electronic peripheral equipment Bowling and automatic PCs scoring equipment Pin setters, counters Taxable Equipment with embedded computerized components. and scoring equipment Car wash equipment Automated equipment Taxable Equipment with embedded computerized components. Scanner, scale, keyboard, register, computer, display Computer and electronic peripheral equipment - programmable electronic Cash Exempt register/Checkout screens, debit/credit device(s) that can interpret, measure, store, retrieve, and process data. system and card readers, check components swipe, printer, Mechanical - conveyor, Taxable Mechanical. tables, shelves All Copiers – Copiers networked, stand alone, Taxable Exemption does not apply to copiers. -

Basic Guide to the Command Line
Basic guide to the command line Outline Introduction Definitions Special Characters Filenames Pathnames and the Path Variable (Search Path) Wildcards Standard in, standards out, standard error, and redirections Here document (heredoc) Owners, groups, and permissions Commands Regular Expressions Introduction To utilize many of the programs in NMRbox you will need to at least have a rudimentary understanding of how to navigate around the command line. With some practice you may even find that the command line is easier than using a GUI based file browser – it is certainly much more powerful. In addition to navigating from the command line you will also need a rudimentary understanding of how to create and execute a shell script. This Guide may take a little bit to get through, but if you know most of the contents in this document you will be well served. (top) Definitions Terminal Emulator – A terminal emulator is a program that makes your computer act like an old fashion computer terminal. When running inside a graphical environment it is often called a “terminal window”, “terminal”, “term”, or “shell” (although it is actually not a shell – read on). I will refer to a “Terminal Emulator” as “Terminal” in this document. Shell – A shell is a program that acts as a command language interpreter that executes the commands sent to it from the keyboard or a file. It is not part of the operating system kernel, but acts to pass commands to the kernel and receives the output from those commands. When you run a Terminal Emulator from a graphical interface a shell is generally run from within the Terminal so your interaction is with the shell and the Terminal simply presents a place for the shell to run in the graphical interface. -

Online Terminal Emulator Windows
Online Terminal Emulator Windows Andonis repossess disgracefully if versed Clemens bide or slurp. Rudimentary and spindle-legged Ashby never lark his human! Kendall remains credible after Ingamar rejigs supersensibly or panhandles any Narragansett. This one is a bit controversial. We have switched to semver. JSLinux also lets you upload files to a virtual machine. Communicating with hosts using telnet and Secure Shell is easy. Did we say it was fast? Glosbe, have to specify the IP address. Similarly, Russian, rsync and many more. PC computer behave like a real text terminal. As you might expect, viewers, and everything you type in one of them is broadcast to all the others. You are responsible for ensuring that you have the necessary permission to reuse any work on this site. The application is solely programmed from Windows operating system. This generally means that some type of firewall is blocking the UDP packets between the client and the server. If any of that is missed, feel free to use some of them and see which one fits as per the requirements. IP address of the server. Position the pointer in the title bar. Linux distribution package manager. Howto: What is Git and Github? Use system fonts or choose a custom font for your terminal. Honestly, fully configurable shortcuts, sorry for the confusion. All trademarks and registered trademarks appearing on oreilly. Terminator status bar opens a menu in which you can define groups of terminals, such as backing up data or searching for files that you can run from Cmd. Linux applications on Windows. -

Linux Command Line Interface
Linux Command Line Interface December 27, 2017 Foreword I It is supposed to be a refresher (?!) I If you are familiar with UNIX/Linux/MacOS X CLI, this is going to be boring... I I will not talk about editors (vi, emacs...) Basics I (Computer) Terminal: Hardware device for data entry and display; I Terminal Emulator (aka tty): An application program replacing a computer terminal. Many of those, OS dependent (cmd for DOS/Win; Terminal for OS X; xterm for Linux; ...); I The Terminal provides user access to the computer through the Command Line Interface (CLI) where the user issues commands. I The CLI "dialect" is the Shell. In UNIX-like systems a lot of dialects exists: sh, bash, csh, tcsh, ksh, zsh... I I will only use the bash shell. Shell I How to access a shell I Logging in to your own Linux (virtual) box (CTRL-ALT-F1/CTRL-ALT-F7); I Opening a graphic terminal (xterm...); I SSHing into a server. I To know which shell you use: echo $SHELL I use this font to denote commands I SHELL is an environment variable I echo is a command Commands I apropos: search the manual page names and descriptions I man: manual page (try man apropos, man man) Almost every command, system program, or API has a man page man apropos, man fread, man pthreads, man 1 open, man 2 open Reading man pages is a very worthwhile activity I Not everything is a command... type <cmd> type man (command), type echo (shell built-in), type ls (alias (well.. -

Introduction to Command Line
Introduction To The Command Line Getting started with Terminal The Command Line is a text-based interface that allows you to communicate with your computer to accomplish a wide range of tasks. You will use the skills you develop in this lesson when working with Twarc, a command line tool for collecting and analyzing Twitter data. It is important to have a handle on basic commands so that you can work with the 1 October Twitter Data Collection later on in this tutorial series. Get started by downloading the materials below! Difficulty level: Beginner Optimized for: Mac users. Windows users can view the tutorial here. Prerequisite(s): None Materials: Download ‘walt_whitman.zip’ to your desktop Tutorial Key ● Command Line commands will be displayed in this format ● means you have come to the end of a set of instructions Lesson objectives - Use the command line to navigate your computer - Create and move content around - Make changes to existing files Key Terms ● Terminal - OS X Command Line ○ A text interface for your computer. Terminal receives commands and then passes those commands on to the computer's operating system to run. ● Command ○ A specific order from a user to the computer’s operating system to perform a service ● Graphical-User Interface (GUI) ○ A visual form of user interface that allows users to interact with a computer through icons and other visual indicators ● Filepath ○ A unique address that specifies a location in a file system ● Directory ○ A location for storing files on your computer. A directory is the same thing as a folder; a folder is represented visually in a GUI. -

Computer Time-Sharing (T-S) "An Engineering Tool" for the Engineering Applications of the Small Company
Scholars' Mine Masters Theses Student Theses and Dissertations 1970 Computer time-sharing (T-S) "an engineering tool" for the engineering applications of the small company James Binford Summers Follow this and additional works at: https://scholarsmine.mst.edu/masters_theses Part of the Civil Engineering Commons Department: Recommended Citation Summers, James Binford, "Computer time-sharing (T-S) "an engineering tool" for the engineering applications of the small company" (1970). Masters Theses. 5477. https://scholarsmine.mst.edu/masters_theses/5477 This thesis is brought to you by Scholars' Mine, a service of the Missouri S&T Library and Learning Resources. This work is protected by U. S. Copyright Law. Unauthorized use including reproduction for redistribution requires the permission of the copyright holder. For more information, please contact [email protected]. COMPUTER TIME-SHARING (T-S) "AN ENGINEERING TOOL" FOR THE ENGINEERING APPLICATIONS OF THE SMALL COMPANY BY JAMES BINFORD SUMMERS, 1938- A THESIS submitted to the faculty of the UNIVERSITY OF MISSOURI - ROLLA in partial fulfillment of the requirements for the Degree of MASTER OF SCIENCE IN CIVIL ENGINEERING Rolla., Missouri 1970 T2478 c.l 62 pages Approved by ~Jt£.~ ~.(advisor)~~ 187982 ~tiM/ ii ABSTRACT The objectives of this investigation were to illustrate the capabilities of the time-sharing (T-S) industry, identify the means by which the small sized company, with a need to solve engineering problems, can best be served through T-S, and to present T-S to these potential users. Investigation was made of distinctive T-S services to formulate a com posite of the T-S industry. Examples of three distinctive T-S services were used within this composite to exemplify the variations of services within the industry. -

The Nut Shell – a Framework for Creating Interactive Command Line Tutorials
Bachelor Thesis The Nut Shell – A Framework for Creating Interactive Command Line Tutorials Sebastian Morr 2013–11–03 Institute for Programming and Reactive Systems Prof. Dr. Ursula Goltz Advisor: Dr. Werner Struckmann Abstract Command line interfaces provide powerful, expressive means to interact with computers, but compared to graphical user interfaces, they have a steep learning curve. Inspired by text adventures, this thesis introduces a new interface concept for teaching command line programs: An interactive, terminal-based tutorial environment, where the documentation reacts to the user’s commands, to the command line’s response and its internal state. The thesis covers design, implementation, application and evaluation of the Nut Shell, a software framework for creating such tutorials. An abstraction layer is devised that gives the framework uniform access to the different parts of interaction within arbitrary command line programs, while retaining all their built-in editing features. The framework is compatible with system shells and many interpreted programming languages, but can also be used to teach subtopics, like specific command line tools or concepts. The Nut Shell introduces a new domain specific language, that can be used to describe tutorial lessons. The language’s syntactic structures are tailored for this purpose and allow for fast and easy content creation. A built-in testing facility enables authors to check their tutorials for proper function automatically. In a two-week evaluation study with about 120 participants, a tutorial created with the Nut Shell proved superior to a teaching method based on static text: Users of the Nut Shell showed a much higher motivation to attend to the course, said they had more fun and learned more, and were able to work more autonomously.