Digital Forensics
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

An Advance Visual Model for Animating Behavior of Cryptographic Protocols
An Advance Visual Model for Animating Behavior of Cryptographic Protocols Mabroka Ali Mayouf Maeref1*, Fatma Alghali2, Khadija Abied2 1 Sebha University, Faculty of Science, Department of Computer Science, P. O. Box 18758 Sebha, Libya, Libyan. 2 Sebha University of Libya, Sebha, Libya. * Corresponding author. Tel.: 00218-925132935; email: [email protected] Manuscript submitted February 13, 2015; accepted July 5, 2015. doi: 10.17706/jcp.10.5.336-346 Abstract: Visual form description benefits from the ability of visualization to provide precise and clear description of object behavior especially if the visual form is extracted from the real world. It provides clear definition of object and the behavior of that object. Although the current descriptions of cryptographic protocol components and operations use a different visual representation, the cryptographic protocols behaviors are not actually reflected. This characteristic is required and included within our proposed visual model. The model uses visual form and scenario-based approach for describing cryptographic protocol behavior and thus increasing the ability to describe more complicated protocol in a simple and easy way. Key words: Animation, cryptographic protocols, interactive tool, visualization. 1. Introduction Cryptographic protocols (CPs) mostly combine both theory and practice [1], [2]. These cause protocol complexity describing and understanding. Therefore, separating the mathematical part from the protocol behavior should provide feeling of how the protocol works, thus increasing the ability to describe and to gain confidence in reflecting more complicated information about CPs, as well as to generate interest to know about other more complex protocol concepts. Several researchers realized the use of visual model and animation techniques to reflect the explanation of the learning objectives and their benefits [3]-[11]. -

Revention of Coldboot Attack on Linux Systems Measures to Prevent Coldboot Attack
Special Issue - 2017 International Journal of Engineering Research & Technology (IJERT) ISSN: 2278-0181 ICIATE - 2017 Conference Proceedings Prevention of Coldboot Attack on Linux Systems Measures to Prevent Coldboot Attack Siddhesh Patil Ekta Patel Nutan Dhange Information Technology, Atharva Information Technology, Atharva Assistant Professor College of Engineering College of Engineering Information Technology, Atharva Mumbai University Mumbai University College of Engineering Mumbai, India Mumbai, India Mumbai University Mumbai, India Abstract— Contrary to the popular belief, DDR type RAM boot attack techniques. We implement measures to ensure that data modules retain stored memory even after power is cut off. stays secure on system shutdown. Data security is critical for most Provided physical access to the cryptosystem, a hacker or a of the business and even home computer users. RAM is used to store forensic specialist can retrieve information stored in the RAM non-persistent information into it. When an application is in use, by installing it on another system and booting from a USB drive user-specific or application-specific data may be stored in RAM. to take a RAM dump. With adequate disassembly and analytic This data can be sensitive information like client information, tools, this information stored in the RAM dump can be payment details, personal files, bank account details, etc. All this deciphered. Hackers thrive on such special-case attack information, if fallen into wrong hands, can be potentially techniques to gain access to systems with sensitive information. dangerous. The goal of most unethical hackers / attackers is to An unencrypted RAM module will contain the decryption key disrupt the services and to steal information. -

CIS 4360 Secure Computer Systems Attacks Against Boot And
CIS 4360 Secure Computer Systems Attacks against Boot and RAM Professor Qiang Zeng Spring 2017 Previous Class • BIOS-MBR: Generation I system boot – What BIOS and MBR are? – How does it boot the system? // Jumping to MBR – How does multi-boot work? // Chain-loading • The limitations of BIOS and MBR – Disk, memory, file system, multi-booting, security, … • UEFI-GPT: Generation II system boot – What UEFI and GPT are? – How does it boot the system? // UEFI boot manager – How does multi-boot work? // separate dirs in ESP CIS 4360 – Secure Computer Systems 2 Limitations of BIOS-MBR • MBR is very limited – Support ~2TB disk only – 4 primary partitions at most (so four OSes at most) – A MBR can store only one boot loader • BIOS is very restrictive – 16-bit processor mode; 1MB memory space (little spare space to accommodate a file system driver) – Blindly executes whatever code on MBR CIS 4360 – Secure Computer Systems 3 UEFI vs. BIOS • Disk partitioning schemes – GPT (GUID Partition Table): part of UEFI spec.; to replace MBR – MBR supports disk size 232 x 512B = 2TB, while UEFI supports much larger disks (264 x 512B = 8,000,000,000 TB) – MBR supports 4 partitions, while GPT supports 128 • Memory space – BIOS: 20-bit addressing; UEFI: 32-bit or 64-bit • Pre-OS environment – BIOS only provides raw disk access, while UEFI supports the FAT file system (so you can use file names to read files) • Booting – BIOS supports boot through boot sectors (MBR and VBR) – UEFI provides a boot partition of hundreds of megabytes (and boot manager and secure boot) CIS 4360 – Secure Computer Systems 4 Previous Class How does dual-boo-ng of Linux and Windows work in UEFI-GPT? Each vendor has a separate directory storing its own boot loader code and configuraon files in the ESP (EFI System Par--on). -

Low-Cost Mitigation Against Cold Boot Attacks for an Authentication Token
Low-cost Mitigation against Cold Boot Attacks for an Authentication Token Ian Goldberg?1, Graeme Jenkinson2, and Frank Stajano2 1 University of Waterloo (Canada) 2 University of Cambridge (United Kingdom) Abstract. Hardware tokens for user authentication need a secure and usable mechanism to lock them when not in use. The Pico academic project proposes an authentication token unlocked by the proximity of simpler wearable devices that provide shares of the token’s master key. This method, however, is vulnera- ble to a cold boot attack: an adversary who captures a running Pico could extract the master key from its RAM and steal all of the user’s credentials. We present a cryptographic countermeasure—bivariate secret sharing—that protects all the credentials except the one in use at that time, even if the token is captured while it is on. Remarkably, our key storage costs for the wearables that supply the cryp- tographic shares are very modest (256 bits) and remain constant even if the token holds thousands of credentials. Although bivariate secret sharing has been used before in slightly different ways, our scheme is leaner and more efficient and achieves a new property—cold boot protection. We validated the efficacy of our design by implementing it on a commercial Bluetooth Low Energy development board and measuring its latency and energy consumption. For reasonable choices of latency and security parameters, a standard CR2032 button-cell battery can power our prototype for 5–7 months, and we demonstrate a simple enhancement that could make the same battery last for over 9 months. -

A Matter of Security, Privacy and Trust
A matter of security, privacy and trust: A study of the principles and values of encryption in New Zealand Michael Dizon Ryan Ko Wayne Rumbles Patricia Gonzalez Philip McHugh Anthony Meehan Acknowledgements This study was funded by grants from the New Zealand Law Foundation and the University of Waikato. We would like to express our gratitude to our project collaborators and members of the Advisory Board – Prof Bert-Jaap Koops (Tilburg University), Prof Lyria Bennett Moses (UNSW Sydney), Prof Alana Maurushat (Western Sydney University), and Associate Professor Alex Sims (University of Auckland) – for their support as well as feedback on specific parts of this report. We would also like to thank Patricia Gonzalez, Joseph Graddy, Philip McHugh, Anthony Meehan, Jean Murray and Peter Upson for their valuable research assistance and other contributions to this study. Michael Dizon, Ryan Ko and Wayne Rumbles Principal investigators December 2019 Executive summary Cybersecurity is crucial for ensuring the safety and well-being of the general public, businesses, government, and the country as a whole. New Zealand has a reasonably comprehensive and well-grounded legal regime and strategy for dealing with cybersecurity matters. However, there is one area that deserves further attention and discussion – encryption. Encryption is at the heart of and underpins many of the technologies and technical processes used for computer and network security, but current laws and policies do not expressly cover this significant technology. The principal objective of this study is to identify the principles and values of encryption in New Zealand with a view to informing future developments of encryption- related laws and policies. -

Security Analysis of the Signal Protocol Student: Bc
ASSIGNMENT OF MASTER’S THESIS Title: Security Analysis of the Signal Protocol Student: Bc. Jan Rubín Supervisor: Ing. Josef Kokeš Study Programme: Informatics Study Branch: Computer Security Department: Department of Computer Systems Validity: Until the end of summer semester 2018/19 Instructions 1) Research the current instant messaging protocols, describe their properties, with a particular focus on security. 2) Describe the Signal protocol in detail, its usage, structure, and functionality. 3) Select parts of the protocol with a potential for security vulnerabilities. 4) Analyze these parts, particularly the adherence of their code to their documentation. 5) Discuss your findings. Formulate recommendations for the users. References Will be provided by the supervisor. prof. Ing. Róbert Lórencz, CSc. doc. RNDr. Ing. Marcel Jiřina, Ph.D. Head of Department Dean Prague January 27, 2018 Czech Technical University in Prague Faculty of Information Technology Department of Computer Systems Master’s thesis Security Analysis of the Signal Protocol Bc. Jan Rub´ın Supervisor: Ing. Josef Kokeˇs 1st May 2018 Acknowledgements First and foremost, I would like to express my sincere gratitude to my thesis supervisor, Ing. Josef Kokeˇs,for his guidance, engagement, extensive know- ledge, and willingness to meet at our countless consultations. I would also like to thank my brother, Tom´aˇsRub´ın,for proofreading my thesis. I cannot express enough gratitude towards my parents, Lenka and Jaroslav Rub´ınovi, who supported me both morally and financially through my whole studies. Last but not least, this thesis would not be possible without Anna who re- lentlessly supported me when I needed it most. Declaration I hereby declare that the presented thesis is my own work and that I have cited all sources of information in accordance with the Guideline for adhering to ethical principles when elaborating an academic final thesis. -

Analysis and Implementation of the Messaging Layer Security Protocol
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by AMS Tesi di Laurea Alma Mater Studiorum · Universita` di Bologna CAMPUS DI CESENA Dipartimento di Informatica - Scienza e Ingegneria Corso di Laurea Magistrale in Ingegneria e Scienze Informatiche Analysis and Implementation of the Messaging Layer Security Protocol Tesi in Sicurezza delle Reti Relatore: Presentata da: Gabriele D'Angelo Nicola Giancecchi Anno Accademico 2018/2019 Parole chiave Network Security Messaging MLS Protocol Ratchet Trees \Oh me, oh vita! Domande come queste mi perseguitano. Infiniti cortei d'infedeli, citt`agremite di stolti, che v'`edi nuovo in tutto questo, oh me, oh vita! Risposta: Che tu sei qui, che la vita esiste e l’identit`a. Che il potente spettacolo continua, e che tu puoi contribuire con un verso." - Walt Whitman Alla mia famiglia. Introduzione L'utilizzo di servizi di messaggistica su smartphone `eincrementato in maniera considerevole negli ultimi anni, complice la sempre maggiore disponi- bilit`adi dispositivi mobile e l'evoluzione delle tecnologie di comunicazione via Internet, fattori che hanno di fatto soppiantato l'uso dei classici SMS. Tale incremento ha riguardato anche l'utilizzo in ambito business, un contesto dove `epi`ufrequente lo scambio di informazioni confidenziali e quindi la necessit`adi proteggere la comunicazione tra due o pi`upersone. Ci`onon solo per un punto di vista di sicurezza, ma anche di privacy personale. I maggiori player mondiali hanno risposto implementando misure di sicurezza all'interno dei propri servizi, quali ad esempio la crittografia end-to-end e regole sempre pi`ustringenti sul trattamento dei dati personali. -

Is Bob Sending Mixed Signals?
Is Bob Sending Mixed Signals? Michael Schliep Ian Kariniemi Nicholas Hopper University of Minnesota University of Minnesota University of Minnesota [email protected] [email protected] [email protected] ABSTRACT Demand for end-to-end secure messaging has been growing rapidly and companies have responded by releasing applications that imple- ment end-to-end secure messaging protocols. Signal and protocols based on Signal dominate the secure messaging applications. In this work we analyze conversational security properties provided by the Signal Android application against a variety of real world ad- versaries. We identify vulnerabilities that allow the Signal server to learn the contents of attachments, undetectably re-order and drop messages, and add and drop participants from group conversations. We then perform proof-of-concept attacks against the application to demonstrate the practicality of these vulnerabilities, and suggest mitigations that can detect our attacks. The main conclusion of our work is that we need to consider more than confidentiality and integrity of messages when designing future protocols. We also stress that protocols must protect against compromised servers and at a minimum implement a trust but verify model. 1 INTRODUCTION (a) Alice’s view of the conversa-(b) Bob’s view of the conversa- Recently many software developers and companies have been inte- tion. tion. grating end-to-end encrypted messaging protocols into their chat applications. Some applications implement a proprietary protocol, Figure 1: Speaker inconsistency in a conversation. such as Apple iMessage [1]; others, such as Cryptocat [7], imple- ment XMPP OMEMO [17]; but most implement the Signal protocol or a protocol based on Signal, including Open Whisper Systems’ caching. -

Signal E2E-Crypto Why Can’T I Hold All These Ratchets
Signal E2E-Crypto Why Can’t I Hold All These Ratchets oxzi 23.03.2021 In the next 30 minutes there will be I a rough introduction in end-to-end encrypted instant messaging, I an overview of how Signal handles those E2E encryption, I and finally a demo based on a WeeChat plugin. Historical Background I Signal has not reinvented the wheel - and this is a good thing! I Goes back to Off-the-Record Communication (OTR)1. OTR Features I Perfect forward secrecy I Deniable authentication 1Borisov, Goldberg, and Brewer. “Off-the-record communication, or, why not to use PGP”, 2004 Influence and Evolution I OTR influenced the Signal Protocol, Double Ratchet. I Double Ratchet influence OMEMO; supports many-to-many communication. I Also influenced Olm, E2E encryption of the Matrix protocol. I OTR itself was influenced by this, version four was introduced in 2018. Double Ratchet The Double Ratchet algorithm is used by two parties to exchange encrypted messages based on a shared secret key. The Double Ratchet algorithm2 is essential in Signal’s E2E crypto. But first, some basics. 2Perrin, and Marlinspike. “The Double Ratchet Algorithm”, 2016 Cryptographic Ratchet A ratchet is a cryptographic function that only moves forward. In other words, one cannot easily reverse its output. Triple Ratchet, I guess.3 3By Salvatore Capalbi, https://www.flickr.com/photos/sheldonpax/411551322/, CC BY-SA 2.5 Symmetric-Key Ratchet Symmetric-Key Ratchet In everyday life, Keyed-Hash Message Authentication Code (HMAC) or HMAC-based KDFs (HKDF) are used. func ratchet(ckIn[]byte)(ckOut, mk[]byte){ kdf := hmac.New(sha256.New, ckIn) kdf.Write(c) // publicly known constant c out := kdf.Sum(nil) return out[:32], out[32:] } ck0 :=[]byte{0x23, 0x42, ...} // some initial shared secret ck1, mk1 := ratchet(ck0) ck2, mk2 := ratchet(ck1) Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Diffie-Hellman Key Exchange Originally, DH uses primitive residue classes modulo n. -
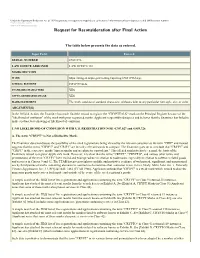
Request for Reconsideration After Final Action
Under the Paperwork Reduction Act of 1995 no persons are required to respond to a collection of information unless it displays a valid OMB control number. PTO Form 1960 (Rev 10/2011) OMB No. 0651-0050 (Exp 09/20/2020) Request for Reconsideration after Final Action The table below presents the data as entered. Input Field Entered SERIAL NUMBER 87031396 LAW OFFICE ASSIGNED LAW OFFICE 116 MARK SECTION MARK https://tmng-al.uspto.gov/resting2/api/img/87031396/large LITERAL ELEMENT CRYPTTALK STANDARD CHARACTERS YES USPTO-GENERATED IMAGE YES MARK STATEMENT The mark consists of standard characters, without claim to any particular font style, size or color. ARGUMENT(S) In the Official Action, the Examiner has made final the refusal to register the "CRYPTTALK" mark on the Principal Register because of the "likelihood of confusion" of the mark with prior registered marks. Applicant respectfully disagrees and believes that the Examiner has failed to make a prima facie showing of likelihood of confusion. I. NO LIKELIHOOD OF CONFUSION WITH U.S. REGISTRATION NOS. 4,707,027 and 4,859,726 A. The term "CRYPT" is Not a Distinctive Mark. The Examiner does not discuss the possibility of the cited registrations being viewed by the relevant consumer as the term "CRIP" and instead suggests that the terms "CRYPT" and "CRIPT" are the only relevant words to compare. The Examiner goes on to conclude that "CRYPT" and "CRIPT" in the respective marks "appear similar and are phonetic equivalents." This alleged similarity has been made the basis of the Examiners refusal to register Applicant's mark. -

Cryptography and Public Key Infrastructure on the Internet
Cryptography and Public Key Infrastructure on the Internet Klaus Schmeh Gesellsschaft für IT-Sicherheit AG Bochum, Germany Cryptography and Public Key Infrastructure on the Internet Cryptography and Public Key Infrastructure on the Internet Klaus Schmeh Gesellsschaft für IT-Sicherheit AG Bochum, Germany Copyright © 2001 by dpunkt.verlag GmbH, Heidelberg, Germany. Title of the German original: Kryptografie und Publik-Key-Infrastrukturen im Internet. ISBN: 3 932588 90 8 English translation Copyright 2003 by John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex PO19 8SQ, England. All rights reserved National 01243 779777 International (+44) 1243 779777 e-mail (for orders and customer service enquiries): [email protected] Visit our Home Page on http://www.wileyeurope.com or http://www.wiley.com All Rights Reserved. No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except under the terms of the Copyright, Designs and Patents Act 1988 or under the terms of a licence issued by the Copyright Licensing Agency Ltd, 90 Tottenham Court Road, London W1T 4LP, UK, without the permission in writing of the Publisher, with the exception of any material supplied specifically for the purpose of being entered and executed on a computer system, for exclusive use by the purchaser of the publication. Requests to the Publisher should be addressed to the Permissions Department, John Wiley & Sons Ltd, The Atrium, Southern Gate, Chichester, West Sussex PO19 8SQ, England, or emailed to [email protected], or faxed to (+44) 1243 770571. -
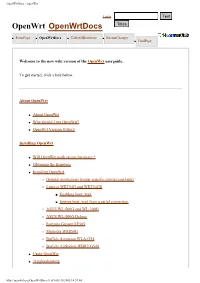
Openwrtdocs - Openwrt
OpenWrtDocs - OpenWrt Login OpenWrt OpenWrtDocs ● FrontPage ● OpenWrtDocs ● TableOfHardware ● RecentChanges ● FindPage Welcome to the new wiki version of the OpenWrt userguide. To get started, click a link below. About OpenWrt ● About OpenWrt ● Why should I run OpenWrt? ● OpenWrt Version History Installing OpenWrt ● Will OpenWrt work on my hardware ? ● Obtaining the firmware ● Installing OpenWrt ❍ General instructions (router specific instructions later) ❍ Linksys WRT54G and WRT54GS ■ Enabling boot_wait ■ Setting boot_wait from a serial connection ❍ ASUS WL-500G and WL-300G ❍ ASUS WL-500G Deluxe ❍ Siemens Gigaset SE505 ❍ Motorola WR850G ❍ Buffalo Airstation WLA-G54 ❍ Buffalo AirStation WBR2-G54S ● Using OpenWrt ● Troubleshooting http://openwrt.org/OpenWrtDocs (1 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt Using OpenWrt ● Using OpenWrt for the first time ● Firstboot / jffs2 ● Editing Files ● ipkg ● Configuration OpenWrt Configuration ● NVRAM ● Network configuration ❍ Sample network configurations ❍ The ethernet switch ■ Normal Behavior ■ Using Robocfg ● Wireless configuration ❍ Basic settings ❍ WEP encryption ❍ WPA encryption ❍ Wireless Distribution System (WDS) / Repeater / Bridge ❍ OpenWrt as client / wireless bridge ● Software configuration ❍ System ■ dnsmasq ■ nas ■ wl ■ TimeZone and NTP ■ Crontab ■ PPPoE Internet Connection ■ Access to syslog ❍ Applications ■ httpd ■ socks-Proxy http://openwrt.org/OpenWrtDocs (2 of 6)18.10.2005 14:57:04 OpenWrtDocs - OpenWrt ■ uPnP ■ CUPS - Printing system with spooling ● Hardware ❍ LED OpenWrt