Ermal Luçi E-Mail: [email protected]
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Campus Networking Best Practices Session 5: Wireless
Campus Networking Best Practices Session 5: Wireless LAN Hervey Allen Dale Smith NSRC & University of Oregon University of Oregon & NSRC [email protected] [email protected] Wireless LAN • Provide wireless network across your campus that has the following characteristics: – Authentication – only allow your users – Roaming – allow users to start up in one section of your network, then move to another location – Runs on your campus network Firewall/ Border Traffic Shaper Router Wireless REN switch Authentication Core Gateway Router Core Servers Network Access Control (NAC) Enterprise Identity Management • Processes and Documentation of users. – Now you must deal with this. – What to use as the back-end user store? • LDAP • Active Directory • Kerberos • Other? – Will this play nice with future use? • email, student/staff information, resource access, ... Identity Management Cont. • An example of such a project can be seen here: – http://ccadmin.uoregon.edu/idm/ • This is a retrofit on to an already retrofitted system. • Learn from others and try to avoid this situation if possible. A Wireless Captive Portal The Wireless Captive Portal • Previous example was very simple. • A Captive Portal is your chance to: – Explain your Acceptable Use Policies – Decide if you must authenticate, or – Allow users on your network and monitor for problems instead (alternate solution). – Anything else? Branding? What's Happening? • remember our initial network diagrams...? • Do you think our hotel built their own solution? • Probably not... Commercial Solutions • Aruba http://www.arubanetworks.com/ • Bradford Networks – http://www.bradfordnetworks.com/ • Cisco NAC Appliance (Clean Access) – http://www.cisco.com/en/US/products/ps6128/ • Cisco Wireless LAN Controllers – http://www.cisco.com/en/US/products/hw/wireless/ • Enterasys http://www.enterasys.com/ • Vernier http://www.verniernetworks.com Open Source Solutions • CoovaChilli (morphed from Chillispot) – http://coova.org/wiki/index.php/CoovaChilli – Uses RADIUS for access and accounting. -

Introduzione Al Mondo Freebsd
Introduzione al mondo FreeBSD Corso avanzato Netstudent Netstudent http://netstudent.polito.it E.Richiardone [email protected] maggio 2009 CC-by http://creativecommons.org/licenses/by/2.5/it/ The FreeBSD project - 1 ·EÁ un progetto software open in parte finanziato ·Lo scopo eÁ mantenere e sviluppare il sistema operativo FreeBSD ·Nasce su CDROM come FreeBSD 1.0 nel 1993 ·Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 ·Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free ·Dalla release 5.0 (2003) assume la struttura che ha oggi ·Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... ·La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 ·Erede di 4.4BSD (eÁ la stessa gente...) ·Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato ·Documentazione ufficiale ben curata ·Licenza molto permissiva, spesso attrae aziende per progetti commerciali: ·saltuariamente esterni collaborano con implementazioni ex-novo (i.e. Intel, GEOM, atheros, NDISwrapper, ZFS) ·a volte no (i.e. Windows NT) ·Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: ·Un sistema base ·Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali ·Sorgenti completi in /usr/src (~500MB) ·EÁ giaÁ abbastanza completo (i.e. ipfw, ppp, bind, ...) ·Un sistema di gestione per software aggiuntivo ·Ports e packages ·Documentazione, canali di assistenza, strumenti di sviluppo ·i.e. Handbook, -

The Pfsense Book Release
The pfSense Book Release The pfSense Team May 10, 2017 CONTENTS 1 Preface 1 1.1 Acknowledgements...........................................1 1.2 Feedback.................................................3 1.3 Typographic Conventions........................................3 1.4 Authors..................................................4 2 Foreword 7 3 Introduction 9 3.1 What does pfSense stand for/mean?...................................9 3.2 Why FreeBSD?..............................................9 3.3 Common Deployments.......................................... 10 3.4 Interface Naming Terminology..................................... 11 3.5 Finding Information and Getting Help.................................. 12 3.6 Project Inception............................................. 13 4 Networking Concepts 15 4.1 Understanding Public and Private IP Addresses............................. 15 4.2 IP Subnetting Concepts......................................... 16 4.3 IP Address, Subnet and Gateway Configuration............................. 16 4.4 Understanding CIDR Subnet Mask Notation.............................. 17 4.5 CIDR Summarization.......................................... 18 4.6 Broadcast Domains............................................ 19 4.7 IPv6.................................................... 19 4.8 Brief introduction to OSI Model Layers................................. 32 5 Hardware 33 5.1 Minimum Hardware Requirements................................... 33 5.2 Hardware Selection........................................... 33 -

PC-BSD 9 Turns a New Page
CONTENTS Dear Readers, Here is the November issue. We are happy that we didn’t make you wait for it as long as for October one. Thanks to contributors and supporters we are back and ready to give you some usefull piece of knowledge. We hope you will Editor in Chief: Patrycja Przybyłowicz enjoy it as much as we did by creating the magazine. [email protected] The opening text will tell you What’s New in BSD world. It’s a review of PC-BSD 9 by Mark VonFange. Good reading, Contributing: especially for PC-BSD users. Next in section Get Started you Mark VonFange, Toby Richards, Kris Moore, Lars R. Noldan, will �nd a great piece for novice – A Beginner’s Guide To PF Rob Somerville, Erwin Kooi, Paul McMath, Bill Harris, Jeroen van Nieuwenhuizen by Toby Richards. In Developers Corner Kris Moore will teach you how to set up and maintain your own repository on a Proofreaders: FreeBSD system. It’s a must read for eager learners. Tristan Karstens, Barry Grumbine, Zander Hill, The How To section in this issue is for those who enjoy Christopher J. Umina experimenting. Speed Daemons by Lars R Noldan is a very good and practical text. By reading it you can learn Special Thanks: how to build a highly available web application server Denise Ebery with advanced networking mechanisms in FreeBSD. The Art Director: following article is the �nal one of our GIS series. The author Ireneusz Pogroszewski will explain how to successfully manage and commission a DTP: complex GIS project. -

Wireless Authentication
Wireless Authentication Network Startup Resource Center www.nsrc.org These materials are licensed under the Creative Commons Attribution-NonCommercial 4.0 International license (http://creativecommons.org/licenses/by-nc/4.0/) Overview Define authentication Strengths and weaknesses of captive portals How captive portals work What is Authentication? Verifying the claim that an entity is allowed to act on behalf of a given known identity More simply: • Is this person/device who they say they are? • Can they prove it • for example, with password, signature? • In our case, the entity is the software, acting on behalf of the user controlling the computer. Why Is Auth So Complicated? I am on a computer. Am I its owner? • Device is not the same as person. I am a network administrator • Should I have access to the finance system? I am connecting to the network from home • Should I have access to all my work resources? I am a printer • Should I be able to scp files to the network? Authentication Core Concepts These are all different concepts: • Confidentiality • Access Control • Authorization • Authentication Confidentiality Ensure that only those who should have access to information can indeed do so (usually encryption) Access Control Access control is the mechanisms by which rights & restrictions are controlled & enforced Authorization Authorization defines what an entity (a user, a device) is authorized (allowed), to access • Which networks (ACLs/filters) • Which systems, which files ? (FS ACLs, permissions) • When can they do that (time policies) ? • Can they run an application or access a service ? Authentication We want to know: WHO, WHERE(*), WHEN • Which entity? • What AP did they associate with? • When did they log on ? • What IP number did they have? PSK (Pre-Shared Key) cannot tell us this. -

MNHO-068 DATASHEET Intel® J1900 4 LAN 1 COM Wifi 4G Firewall Router Mini Server
MNHO-068 DATASHEET Intel® J1900 4 LAN 1 COM WiFi 4G Firewall Router Mini Server https://www.pondesk.com/product/MNHO-068 Features ● Small Security Gateway, Firewall Router, Mini Server ● Intel® Celeron® J1900 Quad Core Processor ● 4 Threads, 2M Cache, up to 2.42 GHz ● Four Intel 82574L Gigabit Ethernet ● Support Network wake-up/PXE ● RJ45-DB9 COM (Cisco Standard) ● Support WiFi, 3G/4G WWAN Networks (optional) ● Watchdog (L256, 0~255 seconds) ● Support up to 8GB DDR3L Memory ● Support Dual Storage (mSATA SSD & 2.5" SATA SSD/HDD) ● VGA Display, USB 2.0 ● Intel® HD Graphics ● Energy Efficient 10W (idle) Low Power Consumption ● Ready for IoT - Simply Connected Using 3G/4G LTE via Mini PCIe ● Support Windows/Linux/Unix/MikroTik/Firewalls etc. ● Can be configured as a Firewall, LAN/WAN Router, VPN, DNS Server, DHCP Server ● Perfect for Security Gateway, Server, VPN and Firewall such as pfSense, Untangle, ● Sophos, Smoothwall, ClearOS, m0n0wall etc. Specifications Dimensions Processor Advanced Technologies Intel® Celeron® Processor J1900 Intel® Virtualization Technology (VT-x) 4 Core, 4 Threads Intel® 64 2M Cache, up to 2.42 GHz Enhanced Intel SpeedStep® Technology Memory Onboard I/O Support up to 8GB 1 x JVGA1 (2*12pin) W DDR3L SODIMM 1.35V Low Voltage 1 x SYS FAN (1*3pin) Single Sided non-ECC Memory 1 x CPU FAN (1*4pin) One Memory Slot 1 x ATX_4P +12V 1 x COM (2*5pin) Storage 1 x SATA2.0 Support 1 x mSATA SSD 1 x JLAN_LED (2*8pin) L H Support 1 x 2.5" SATA SSD/HDD 1 x Full height mini PCIe (For WiFi & 3G module) LAN 1 x mSATA (For SSD) 197mm -

Kratka Povijest Unixa Od Unicsa Do Freebsda I Linuxa
Kratka povijest UNIXa Od UNICSa do FreeBSDa i Linuxa 1 Autor: Hrvoje Horvat Naslov: Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa Licenca i prava korištenja: Svi imaju pravo koristiti, mijenjati, kopirati i štampati (printati) knjigu, prema pravilima GNU GPL licence. Mjesto i godina izdavanja: Osijek, 2017 ISBN: 978-953-59438-0-8 (PDF-online) URL publikacije (PDF): https://www.opensource-osijek.org/knjige/Kratka povijest UNIXa - Od UNICSa do FreeBSDa i Linuxa.pdf ISBN: 978-953- 59438-1- 5 (HTML-online) DokuWiki URL (HTML): https://www.opensource-osijek.org/dokuwiki/wiki:knjige:kratka-povijest- unixa Verzija publikacije : 1.0 Nakalada : Vlastita naklada Uz pravo svakoga na vlastito štampanje (printanje), prema pravilima GNU GPL licence. Ova knjiga je napisana unutar inicijative Open Source Osijek: https://www.opensource-osijek.org Inicijativa Open Source Osijek je član udruge Osijek Software City: http://softwarecity.hr/ UNIX je registrirano i zaštićeno ime od strane tvrtke X/Open (Open Group). FreeBSD i FreeBSD logo su registrirani i zaštićeni od strane FreeBSD Foundation. Imena i logo : Apple, Mac, Macintosh, iOS i Mac OS su registrirani i zaštićeni od strane tvrtke Apple Computer. Ime i logo IBM i AIX su registrirani i zaštićeni od strane tvrtke International Business Machines Corporation. IEEE, POSIX i 802 registrirani i zaštićeni od strane instituta Institute of Electrical and Electronics Engineers. Ime Linux je registrirano i zaštićeno od strane Linusa Torvaldsa u Sjedinjenim Američkim Državama. Ime i logo : Sun, Sun Microsystems, SunOS, Solaris i Java su registrirani i zaštićeni od strane tvrtke Sun Microsystems, sada u vlasništvu tvrtke Oracle. Ime i logo Oracle su u vlasništvu tvrtke Oracle. -

M0n0wall and PPTP Preface
M0n0wall and PPTP December 8, 2003 Version 1.0 Francisco Artes [email protected] Preface: ............................................................................................................................... 1 Audience: ............................................................................................................................ 1 Assumptions:....................................................................................................................... 2 Subnetting and VLAN routing:........................................................................................... 2 Setup of m0n0wall software: .............................................................................................. 3 PPTP User Setup:................................................................................................................5 PPTP Firewall Rules:.......................................................................................................... 6 Example of filtered PPTP Rules: .................................................................................... 9 Setting up a PPTP Client on Windows XP™:................................................................... 11 Testing our PPTP Connection in Windows ™: ............................................................ 14 Some things I have found not to work over the PPTP Connection: ................................. 17 Preface: This document is intended to outline several different PPTP VPN type setups, it includes a how-to on setting up a -
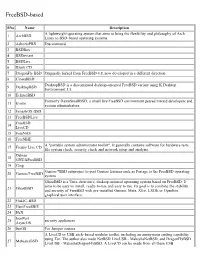
List of BSD Operating Systems
FreeBSD-based SNo Name Description A lightweight operating system that aims to bring the flexibility and philosophy of Arch 1 ArchBSD Linux to BSD-based operating systems. 2 AskoziaPBX Discontinued 3 BSDBox 4 BSDeviant 5 BSDLive 6 Bzerk CD 7 DragonFly BSD Originally forked from FreeBSD 4.8, now developed in a different direction 8 ClosedBSD DesktopBSD is a discontinued desktop-oriented FreeBSD variant using K Desktop 9 DesktopBSD Environment 3.5. 10 EclipseBSD Formerly DamnSmallBSD; a small live FreeBSD environment geared toward developers and 11 Evoke system administrators. 12 FenestrOS BSD 13 FreeBSDLive FreeBSD 14 LiveCD 15 FreeNAS 16 FreeSBIE A "portable system administrator toolkit". It generally contains software for hardware tests, 17 Frenzy Live CD file system check, security check and network setup and analysis. Debian 18 GNU/kFreeBSD 19 Ging Gentoo/*BSD subproject to port Gentoo features such as Portage to the FreeBSD operating 20 Gentoo/FreeBSD system GhostBSD is a Unix-derivative, desktop-oriented operating system based on FreeBSD. It aims to be easy to install, ready-to-use and easy to use. Its goal is to combine the stability 21 GhostBSD and security of FreeBSD with pre-installed Gnome, Mate, Xfce, LXDE or Openbox graphical user interface. 22 GuLIC-BSD 23 HamFreeSBIE 24 HeX IronPort 25 security appliances AsyncOS 26 JunOS For Juniper routers A LiveCD or USB stick-based modular toolkit, including an anonymous surfing capability using Tor. The author also made NetBSD LiveUSB - MaheshaNetBSD, and DragonFlyBSD 27 MaheshaBSD LiveUSB - MaheshaDragonFlyBSD. A LiveCD can be made from all these USB distributions by running the /makeiso script in the root directory. -

How to Accelerate Your Internet
How To Accelerate Your Internet A practical guide to Bandwidth Management and Optimisation using Open Source Software How To Accelerate Your Internet For more information about this project, visit us online at http://bwmo.net/ Editor: Flickenger R. Associate Editors: Belcher M., Canessa E., Zennaro M. Publishers: INASP/ICTP © 2006, BMO Book Sprint Team First edition: October 2006 ISBN: 0-9778093-1-5 Many designations used by manufacturers and vendors to distinguish their products are claimed as trademarks. Where those designations appear in this book, and the authors were aware of a trademark claim, the designations have been printed in all caps or initial caps. All other trademarks are property of their respective owners. The authors and publisher have taken due care in preparation of this book, but make no expressed or implied warranty of any kind and assume no responsibil- ity for errors or omissions. No liability is assumed for incidental or consequen- tial damages in connection with or arising out of the use of the information con- tained herein. This work is released under the Creative Commons Attribution-ShareAlike 2.5 license. For more details regarding your rights to use and redistribute this work, see http://creativecommons.org/licenses/by-sa/2.5/ Contents Preface ix About This Book xi Introduction 1 Bandwidth, throughput, latency, and speed.............................................................................. 2 Not enough to go around........................................................................................................ -

Introduzione Al Mondo Freebsd Corso Avanzato
Introduzione al mondo FreeBSD corso Avanzato •Struttura •Installazione •Configurazione •I ports •Gestione •Netstudent http://netstudent.polito.it •E.Richiardone [email protected] •Novembre 2012 •CC-by http://creativecommons.org/licenses/by/3.0/it/ The FreeBSD project - 1 • E` un progetto software open • Lo scopo e` mantenere e sviluppare il sistema operativo FreeBSD • Nasce su CDROM come FreeBSD 1.0 nel 1993 • Deriva da un patchkit per 386BSD, eredita codice da UNIX versione Berkeley 1977 • Per problemi legali subisce un rallentamento, release 2.0 nel 1995 con codice royalty-free • Dalla release 4.0 (2000) assume la struttura che ha oggi • Disponibile per x86 32 e 64bit, ia64, MIPS, ppc, sparc... • La mascotte (Beastie) nasce nel 1984 The FreeBSD project - 2 • Erede di 4.4BSD (e` la stessa gente...) • Sistema stabile; sviluppo uniforme; codice molto chiaro, ordinato e ben commentato • Documentazione ufficiale ben curata • Licenza molto permissiva, spesso attrae aziende per progetti commerciali: • saltuariamente progetti collaborano con implementazioni ex-novo (i.e. Intel, GEOM, NDISwrapper, ZFS, GNU/Linux emulation) • Semplificazione di molte caratteristiche tradizionali UNIX Di cosa si tratta Il progetto FreeBSD include: • Un sistema base • Bootloader, kernel, moduli, librerie di base, comandi e utility di base, servizi tradizionali • Sorgenti completi in /usr/src (~500MB) • E` gia` completo (i.e. ipfw, ppp, bind, ...) • Un sistema di gestione per software aggiuntivo • Ports e packages • Documentazione, canali di assistenza, strumenti -

Pare-Feu : Architecture Et Déploiement V1.0
Pare-feu : architecture et déploiement V1.0 Pare-feu : Architecture et déploiement V 1.0 Stéphane DUFOUR (Architecte système et sécurité) - 1 - Pare-feu : architecture et déploiement V1.0 Table des matières PARE-FEU : ARCHITECTURE ET DEPLOIEMENT ..............................................................................................................................0 TABLE DES MATIERES...................................................................................................................................................................2 INTRODUCTION ...........................................................................................................................................................................4 CONCEPTS DE BASE......................................................................................................................................................................5 RAPPEL SECURITE .................................................................................................................................................................................5 Les fondamentaux ......................................................................................................................................................................5 Les menaces ................................................................................................................................................................................6 Best practice .............................................................................................................................................................................16