On the Impact of Touch ID on Iphone Passcodes
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

5Tips for Securing Your Mobile Device for Telehealth
Tips for Securing your Mobile Device 5for Telehealth The Health Insurance Portability and Accountability Act (HIPAA) requires that providers protect your information and not share it without your permission. Telehealth providers are required by law to secure medical information that can be shared electronically by encrypting messages and adding other safeguards into the software they use. However, patients’ devices on the receiving end of care often do not always have these safeguards while some medical devices have been shown to be vulnerable to hackers. It is therefore the responsibility of the patient to secure personal devices. 01 Use a PIN or Passcode to secure device Securing your mobile device is important for ensuring that others do not have access to your confidential information and applications. To protect your iPad, iPhone, Android phone you need to set a passcode. It is a 4- to 6-digit PIN used to grant access to the device, like the code you use for an ATM bank card or a debit card. Securing your Apple (iPhone and iPad) and Android devices In addition to allowing you to secure your phone with a passcode, Newer Apple and Android devices also use biometrics called Touch ID and Face ID on Apple, and Face recognition, Irises, and Fingerprints on some Android devices. These tools use your Face, eyes, and fingerprints as unique identifiers to help secure your devices. Face ID and Face recognition use your facial features in order to unlock your device. Touch ID, which is no longer being used on newer versions of iPhone and iPad, and Fingerprints on Android is a fingerprinting tool. -

Legal-Process Guidelines for Law Enforcement
Legal Process Guidelines Government & Law Enforcement within the United States These guidelines are provided for use by government and law enforcement agencies within the United States when seeking information from Apple Inc. (“Apple”) about customers of Apple’s devices, products and services. Apple will update these Guidelines as necessary. All other requests for information regarding Apple customers, including customer questions about information disclosure, should be directed to https://www.apple.com/privacy/contact/. These Guidelines do not apply to requests made by government and law enforcement agencies outside the United States to Apple’s relevant local entities. For government and law enforcement information requests, Apple complies with the laws pertaining to global entities that control our data and we provide details as legally required. For all requests from government and law enforcement agencies within the United States for content, with the exception of emergency circumstances (defined in the Electronic Communications Privacy Act 1986, as amended), Apple will only provide content in response to a search issued upon a showing of probable cause, or customer consent. All requests from government and law enforcement agencies outside of the United States for content, with the exception of emergency circumstances (defined below in Emergency Requests), must comply with applicable laws, including the United States Electronic Communications Privacy Act (ECPA). A request under a Mutual Legal Assistance Treaty or the Clarifying Lawful Overseas Use of Data Act (“CLOUD Act”) is in compliance with ECPA. Apple will provide customer content, as it exists in the customer’s account, only in response to such legally valid process. -

BY USING YOUR Iphone, Ipad OR Ipod TOUCH (“Ios DEVICE”), YOU ARE AGREEING to BE BOUND by the FOLLOWING TERMS
ENGLISH IMPORTANT: BY USING YOUR iPHONE, iPAD OR iPOD TOUCH (“iOS DEVICE”), YOU ARE AGREEING TO BE BOUND BY THE FOLLOWING TERMS: A. APPLE iOS SOFTWARE LICENSE AGREEMENT B. APPLE PAY SUPPLEMENTAL TERMS C. NOTICES FROM APPLE APPLE INC. iOS SOFTWARE LICENSE AGREEMENT Single Use License PLEASE READ THIS SOFTWARE LICENSE AGREEMENT (“LICENSE”) CAREFULLY BEFORE USING YOUR iOS DEVICE OR DOWNLOADING THE SOFTWARE UPDATE ACCOMPANYING THIS LICENSE. BY USING YOUR iOS DEVICE OR DOWNLOADING A SOFTWARE UPDATE, AS APPLICABLE, YOU ARE AGREEING TO BE BOUND BY THE TERMS OF THIS LICENSE. IF YOU DO NOT AGREE TO THE TERMS OF THIS LICENSE, DO NOT USE THE iOS DEVICE OR DOWNLOAD THE SOFTWARE UPDATE. IF YOU HAVE RECENTLY PURCHASED AN iOS DEVICE AND YOU DO NOT AGREE TO THE TERMS OF THE LICENSE, YOU MAY RETURN THE iOS DEVICE WITHIN THE RETURN PERIOD TO THE APPLE STORE OR AUTHORIZED DISTRIBUTOR WHERE YOU OBTAINED IT FOR A REFUND, SUBJECT TO APPLE’S RETURN POLICY FOUND AT http://www.apple.com/legal/sales_policies/. 1. General. (a) The software (including Boot ROM code, embedded software and third party software), documentation, interfaces, content, fonts and any data that came with your iOS Device (“Original iOS Software”), as may be updated or replaced by feature enhancements, software updates or system restore software provided by Apple (“iOS Software Updates”), whether in read only memory, on any other media or in any other form (the Original iOS Software and iOS Software Updates are collectively referred to as the “iOS Software”) are licensed, not sold, to you by Apple Inc. -

First Pryority Bank Apple Pay®
First Pryority Bank Apple Pay® An Easier Way to Pay Don’t search for your wallet, use your smartphone to pay! Apple Pay® is a type of mobile payment system that allows users to complete transactions using their compatible Apple device. Apple Pay® for your First Pryority Bank Visa® Debit Card is easy, private, and secure. Once you’ve added your First Pryority Bank Visa® Debit Card to Apple Pay®, you can pay securely with your Touch ID or passcode at hundreds of thousands of stores and participating apps. Disclosure *Apple, the Apple Logo, iPhone, and iPad are trademarks of Apple Inc., registered in the U.S. and other countries. Apple Pay and Touch ID are trademarks of Apple Inc. Frequently Asked Questions How does it work? When you add your First Pryority Bank Visa® Debit Card in your eligible iPhone®, iPad®, Apple Watch®, or Mac®, a unique digital account number is assigned, encrypted, and securely stored, instead of using your actual card number. When you make a purchase, your actual card number is not shared by Apple with merchants or transmitted with a payment. In addition, when paying with Apple Pay®, the cashier never sees your name, card number or three-digit security code, so it is very private. To pay, just hold your iPhone near a participating merchant’s contactless reader. A vibration and beep let you know your payment has been accepted. You can also use Apple Pay on your phone, iPad Air, iPad Mini, and Apple Watch with shopping apps. Look for a contactless reader bearing these icons: What Apple devices are compatible with Apple -

Iphone - Ipad - Watch - TV Ipod - Airpods -Homepod App and Itunes January 2020
iDevices SIG iPhone - iPad - Watch - TV iPod - AirPods -HomePod App and iTunes January 2020 Happy New Year 1 Modern Life 2 Modern Life 3 Modern Life 4 A Message from our Sponsor Welcome to the iDevices SIG. We appreciate your interest in our program today. As information, participation in SIG activities requires you to be a member of the Computer Club. If you are not a CC member, you are welcome to attend today’s presentation as a guest, but you must join the club if you wish to come again. You can join online via the Sun City website ticketing program or in person at the Members Services office in the Social Center. And now back to our regularly scheduled program… 5 iDevice SIG Meeting Notes Posted on the Computer Club’s web page. Click to view or download meeting notes 6 Do you want to receive SIG emails? • Log on to Sun City website • Select ‘My Memberships’ • Put a check mark by the SIGs you want 7 Click here for the main Support Page Click here for the Support Site Map iPhone https://support.apple.com/iphone iPad https://support.apple.com/ipad Watch https://support.apple.com/watch Apple ID https://support.apple.com/apple-id iTunes https://support.apple.com/itunes Apple TV https://support.apple.com/apple-tv Apple Music https://support.apple.com/music iPod https://support.apple.com/ipod AirPods https://support.apple.com/airpods Apple Pay https://support.apple.com/apple-pay iCloud https://support.apple.com/icloud Apps https://support.apple.com/apps Manuals https://support.apple.com/en_US/manuals And don’t forget the Books app for -
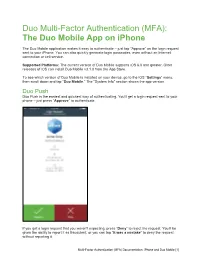
(MFA): the Duo Mobile App on Iphone
Duo Multi-Factor Authentication (MFA): The Duo Mobile App on iPhone The Duo Mobile application makes it easy to authenticate – just tap “Approve” on the login request sent to your iPhone. You can also quickly generate login passcodes, even without an Internet connection or cell service. Supported Platforms: The current version of Duo Mobile supports iOS 6.0 and greater. Older releases of iOS can install Duo Mobile v3.1.0 from the App Store. To see which version of Duo Mobile is installed on your device, go to the iOS “Settings” menu, then scroll down and tap “Duo Mobile.” The "System Info" section shows the app version. Duo Push Duo Push is the easiest and quickest way of authenticating. You'll get a login request sent to your phone – just press “Approve” to authenticate. If you get a login request that you weren't expecting, press “Deny” to reject the request. You’ll be given the ability to report it as fraudulent, or you can tap “It was a mistake” to deny the request without reporting it. Multi-Factor Authentication (MFA) Documentation: iPhone and Duo Mobile [1] Touch ID Duo Mobile for iOS also supports Touch ID for Duo Push-based logins; an additional layer of security to verify your users’ identities. If you're using a Touch ID capable iOS device, you'll see a Touch ID prompt each time you authenticate via Duo Mobile (if required by your administrator). If you're not able to scan your fingerprint using the TouchID sensor you can also approve the Duo authentication request using the device's passcode (the same one you use on the iOS lock screen). -

Touch ID™ Frequently Asked Questions What Is Touch ID? Touch
Touch ID™ Frequently Asked Questions What is Touch ID? Touch ID is the biometric fingerprint authentication technology available with Apple devices such as iPhone 5s, iPhone 6 and 6S, iPad Air 2, iPad mini 3, or newer. Why use Touch ID? Touch ID is meant as a quick and convenient way to access your account. It's a seamless way to use your fingerprint as your credentials. How do I Enable or Disable Touch ID? To manually Enable or Disable Touch ID, go to the application Settings and click on Touch ID. On the Touch ID Settings screen, swipe the Touch ID button. A confirmation prompt will display. How secure is Touch ID? Every fingertip is unique, so it is rare that even a small section of two separate fingerprints are alike to register for Touch ID. If my phone has multiple fingerprints registered, will they be able to access my account? Yes, all saved fingerprints on your device will have access to your account. How do I keep my phone further protected? We recommend you add a passcode or security lock to your phone to further secure access when the device is not in use. In addition, keep your phone software up to date, including your Service 1st application. If the device doesn't recognize my fingerprint, can I still view my account? Yes, you will always have the option to log in using your account number/User ID and password. When the Touch ID prompt comes up click Cancel and enter your account credentials to log in. Can an account be Enabled for Touch ID on multiple devices? Yes, an account may be setup on multiple devices. -

With the Release of the Ipad 8Th Generation and the Ipad Air 4Th Generation, Apple Has Made Available Ipads That Support the Apple Pencil and Are Reasonably Priced
With the release of the iPad 8th Generation and the iPad Air 4th Generation, Apple has made available iPads that support the Apple Pencil AND are reasonably priced. We continue to believe the combination of an iPad and an Apple Pencil provides a very powerful learning tool. ● For this reason, the School is requiring each student in Middle School to use an iPad which is compatible with the Apple Pencil. ● Students are not required to own an Apple Pencil as the School will make class sets of Pencils available for teachers to check out for specific classroom activities. If you are contemplating the purchase of a new iPad for your student, The Technology Team offers the following general minimum recommendations in order of our suggested preference: 1. iPad Pro 11” (2nd Generation) with 256GB of iPad storage and the Apple Pencil (2nd generation) ● The iPad Pro 11” and the Apple Pencil (2nd generation) are amazing tools for the classroom. ● The 256GB of storage is sufficient for school data (apps, videos, and projects) as well as personal data. ● The iPad Pro 11” has superior display qualities and a faster processor. ● The iPad Pro 11” is compatible with the Magic Keyboard and the Smart Keyboard Folio. ● The iPad Pro 11” supports Face ID. 2. iPad Air (4th generation) and the Apple Pencil (2nd generation) ● The iPad Air is a mid-range-priced iPad. ● The iPad Air supports the Apple Pencil (2nd generation). ● The 64GB of storage should be sufficient for school data (apps, videos, and projects). If you anticipate a lot of personal data, you may want to upgrade the storage to 256GB. -

Turning on Encryption for an Iphone, Ipad Or Ipod Touch
Turning on encryption for an iPhone, iPad or iPod Touch Enabling encryption on Apple’s iPhone, iPad or iPod Toucg devices is simple. Hopefully you’ll find it’s already all been set as part of the initial set up and configuration process when you got the phone or tablet but you can check, and turn it on if it’s not already activated, by following the steps below. The moment you set a passcode or enable Touch ID on the device running iOS 8 and above, the full device encryption is turned on automatically without you having to do anything. If you’ve not set an unlock code you can do so by. Step 1: Launch the Settings app on your iPhone, iPad or iPod touch. Step 2: Select Touch ID & Passcode from the list of available options. Step 3: Now simply tap Turn Passcode On and enter in a passcode of your choice. A longer alphanumeric passcode is recommended but a six-digit PIN code will do as well. Avoid four-digit PINs as your passcode. (You can change this from Passcode Options in Set Passcode screen). Additionally, you can also opt to utilise Touch ID for authentication if your device comes eQuipped with Apple’s Touch ID sensor. Step 4: To confirm if encryption is enabled or not, head to Settings -> Touch ID & Passcode and then scroll to the bottom of the screen. Here you should see “Data protection is enabled” That’s it. Your iOS device should now be fully encrypted. To remote wipe Before you can locate and wipe your devices, you need to set up iCloud and turn on Find My iPhone (or Find My iPad) on each of your iOS devices. -

Session 6: Making Things Easier with Apple Features
Apple Mobile Device Training Session 6: Making Things Easier with Apple Features Breakdown of Sessions Mondays (10:00am – 12:00pm) Thursdays (3:30pm – 5:30pm) • Session 1: Welcome to your iPhone or iPad • Session 2: Apple ID & Backups • Session 3: Apps & Settings • Session 4: Settings (Continued) • Session 5: Settings (Continued) • Session 6: Making Things Easier with Apple Features • Session 7: Communicating on your Device • Session 8: The Camera & Photos App • Session 9: Mail App & your Email Address • Session 10: Searching the Internet with the Safari App • Session 11: Productivity Apps • Session 12: Productivity Apps (Continued) • Session 13: How to Troubleshoot & Reset your Device if needed • Session 14: Other Useful Apps & Websites 2 Download Class Materials Go to https://sfcommunityliving.org/learn- skills/computer-training/, look through our Tech Help Desk class schedules for all online classes hosted by Community Living Campaign. • Here you can also download printable copies of the class materials used for today’s lesson & all other planned lessons on CLC’s Tech schedule. 3 Today’s Goals • What is Siri? • Adjusting Siri Settings • What is Dictation? • Using Dictation • What are Passcode, Touch ID & Face ID? • Adjusting Passcode & ID Settings 4 What is Siri? • Siri is the voice assistant built by Apple. • Siri helps you simplify navigating through your Apple device by simply listening to your voice and then performing the task you ask it to do. (For instance, you can ask Siri to set an alarm or a reminder for you at a specific time of a specific day.) • All devices have a button for the user to press & hold in order to activate Siri and then give the verbal command. -
Ios-Security-Guide.Pdf
iOS Security iOS 9.3 or later May 2016 Contents Page 4 Introduction Page 5 System Security Secure boot chain S y s t e m S o f t w a r e A uthorization S e c u r e E n c l a v e T o u c h I D Page 10 Encryption and Data Protection Hardware security features File Data Protection Passcodes Data Protection classes Keychain Data Protection Access to Safari saved passwords Keybags Security Certifications and programs Page 18 App Security App code signing Runtime process security Extensions App Groups Data Protection in apps Accessories HomeKit HealthKit Secure Notes Apple Watch Page 28 Network Security TLS VPN Wi-Fi Bluetooth Single Sign-on AirDrop security Page 32 Apple Pay Apple Pay components How Apple Pay uses the Secure Element How Apple Pay uses the NFC controller Credit and debit card provisioning Payment authorization Transaction-specific dynamic security code Contactless payments with Apple Pay Paying with Apple Pay within apps Rewards cards Suspending, removing, and erasing cards iOS Security—White Paper | May 2016 2 Page 39 Internet Services A p p l e I D i M e s s a g e F a c e T i m e i C l o u d i C l o u d K e y c h a i n S i r i C o n t i n u i t y Spotlight Suggestions Page 52 Device Controls Passcode protection i O S p a i r i n g m o d e l Configuration enforcement Mobile device management (MDM) Shared iPad Apple School Manager D e v i c e E n r o l l m e n t Apple Configurator 2 Supervision Restrictions R e m o t e W ipe Lost Mode Activation Lock Page 59 Privacy Controls Location Services Access to personal data P r i v a c y p o l i c y Page 60 Conclusion A commitment to security Page 61 Glossary Page 63 Document Revision History iOS Security—White Paper | May 2016 3 Introduction Apple designed the iOS platform with security at its core. -

Apple Pay® Frequently Asked Questions
Apple Pay® Frequently Asked Questions 1. What is Apple Pay? Apple Pay is a contactless payment feature accessed through your iPhone® or Apple Watch® that allows merchants to receive payments. You can also use your iPad Air 2® or iPad Mini 3® to pay within certain applications. 2. How does Apple Pay work? Apply Pay creates an electronic version of your credit and debit cards, assigning device account numbers, for added security. You can use Apple Pay at participating merchants who accept Apple Pay. 3. Is Apple Pay secure? Yes. When you use Apple Pay, your Central Bank card number is not stored on your phone or given to the merchant. A unique digital code is created specifically for your device. You still enjoy all the benefits of your Central Bank debit card, which protects you from unauthorized purchases. 4. Is there a cost associated with Apple Pay? There is no cost to use Apple Pay; however, wireless carrier data fees may apply. Central Bank debit card Terms & Conditions and your Debit Card Deposit Account Agreement will apply for all purchases. 5. What do I need to use Apple Pay? • iPhone – These are the models compatible with Apple Pay o iPhone models with Face ID TM, iPhone models with Touch ID TM, except for iPhone 5s • iPad-These are the models compatible with Apple Pay o iPad Pro, iPad, iPad Air, iPad Mini with Touch ID TM or Face ID TM • Apple Watch-These are the models compatible with Apple Pay o Apple Watch (1st generation), Apple Watch Series 1 and 2 and later • iOS 8.1 or later • Face ID TM, Touch ID TM or passcode on your device ® • iCloud account Apple Pay is NOT available on other devices such as Android or Windows.