Tetration Reference
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Five Fundamental Operations of Mathematics: Addition, Subtraction
The five fundamental operations of mathematics: addition, subtraction, multiplication, division, and modular forms Kenneth A. Ribet UC Berkeley Trinity University March 31, 2008 Kenneth A. Ribet Five fundamental operations This talk is about counting, and it’s about solving equations. Counting is a very familiar activity in mathematics. Many universities teach sophomore-level courses on discrete mathematics that turn out to be mostly about counting. For example, we ask our students to find the number of different ways of constituting a bag of a dozen lollipops if there are 5 different flavors. (The answer is 1820, I think.) Kenneth A. Ribet Five fundamental operations Solving equations is even more of a flagship activity for mathematicians. At a mathematics conference at Sundance, Robert Redford told a group of my colleagues “I hope you solve all your equations”! The kind of equations that I like to solve are Diophantine equations. Diophantus of Alexandria (third century AD) was Robert Redford’s kind of mathematician. This “father of algebra” focused on the solution to algebraic equations, especially in contexts where the solutions are constrained to be whole numbers or fractions. Kenneth A. Ribet Five fundamental operations Here’s a typical example. Consider the equation y 2 = x3 + 1. In an algebra or high school class, we might graph this equation in the plane; there’s little challenge. But what if we ask for solutions in integers (i.e., whole numbers)? It is relatively easy to discover the solutions (0; ±1), (−1; 0) and (2; ±3), and Diophantus might have asked if there are any more. -

Large but Finite
Department of Mathematics MathClub@WMU Michigan Epsilon Chapter of Pi Mu Epsilon Large but Finite Drake Olejniczak Department of Mathematics, WMU What is the biggest number you can imagine? Did you think of a million? a billion? a septillion? Perhaps you remembered back to the time you heard the term googol or its show-off of an older brother googolplex. Or maybe you thought of infinity. No. Surely, `infinity' is cheating. Large, finite numbers, truly monstrous numbers, arise in several areas of mathematics as well as in astronomy and computer science. For instance, Euclid defined perfect numbers as positive integers that are equal to the sum of their proper divisors. He is also credited with the discovery of the first four perfect numbers: 6, 28, 496, 8128. It may be surprising to hear that the ninth perfect number already has 37 digits, or that the thirteenth perfect number vastly exceeds the number of particles in the observable universe. However, the sequence of perfect numbers pales in comparison to some other sequences in terms of growth rate. In this talk, we will explore examples of large numbers such as Graham's number, Rayo's number, and the limits of the universe. As well, we will encounter some fast-growing sequences and functions such as the TREE sequence, the busy beaver function, and the Ackermann function. Through this, we will uncover a structure on which to compare these concepts and, hopefully, gain a sense of what it means for a number to be truly large. 4 p.m. Friday October 12 6625 Everett Tower, WMU Main Campus All are welcome! http://www.wmich.edu/mathclub/ Questions? Contact Patrick Bennett ([email protected]) . -

The Infinity Theorem Is Presented Stating That There Is at Least One Multivalued Series That Diverge to Infinity and Converge to Infinite Finite Values
Open Journal of Mathematics and Physics | Volume 2, Article 75, 2020 | ISSN: 2674-5747 https://doi.org/10.31219/osf.io/9zm6b | published: 4 Feb 2020 | https://ojmp.wordpress.com CX [microresearch] Diamond Open Access The infinity theorem Open Mathematics Collaboration∗† March 19, 2020 Abstract The infinity theorem is presented stating that there is at least one multivalued series that diverge to infinity and converge to infinite finite values. keywords: multivalued series, infinity theorem, infinite Introduction 1. 1, 2, 3, ..., ∞ 2. N =x{ N 1, 2,∞3,}... ∞ > ∈ = { } The infinity theorem 3. Theorem: There exists at least one divergent series that diverge to infinity and converge to infinite finite values. ∗All authors with their affiliations appear at the end of this paper. †Corresponding author: [email protected] | Join the Open Mathematics Collaboration 1 Proof 1 4. S 1 1 1 1 1 1 ... 2 [1] = − + − + − + = (a) 5. Sn 1 1 1 ... 1 has n terms. 6. S = lim+n + S+n + 7. A+ft=er app→ly∞ing the limit in (6), we have S 1 1 1 ... + 8. From (4) and (7), S S 2 = 0 + 2 + 0 + 2 ... 1 + 9. S 2 2 1 1 1 .+.. = + + + + + + 1 10. Fro+m (=7) (and+ (9+), S+ )2 2S . + +1 11. Using (6) in (10), limn+ =Sn 2 2 limn Sn. 1 →∞ →∞ 12. limn Sn 2 + = →∞ 1 13. From (6) a=nd (12), S 2. + 1 14. From (7) and (13), S = 1 1 1 ... 2. + = + + + = (b) 15. S 1 1 1 1 1 ... + 1 16. S =0 +1 +1 +1 +1 +1 1 .. -

The Modal Logic of Potential Infinity, with an Application to Free Choice
The Modal Logic of Potential Infinity, With an Application to Free Choice Sequences Dissertation Presented in Partial Fulfillment of the Requirements for the Degree Doctor of Philosophy in the Graduate School of The Ohio State University By Ethan Brauer, B.A. ∼6 6 Graduate Program in Philosophy The Ohio State University 2020 Dissertation Committee: Professor Stewart Shapiro, Co-adviser Professor Neil Tennant, Co-adviser Professor Chris Miller Professor Chris Pincock c Ethan Brauer, 2020 Abstract This dissertation is a study of potential infinity in mathematics and its contrast with actual infinity. Roughly, an actual infinity is a completed infinite totality. By contrast, a collection is potentially infinite when it is possible to expand it beyond any finite limit, despite not being a completed, actual infinite totality. The concept of potential infinity thus involves a notion of possibility. On this basis, recent progress has been made in giving an account of potential infinity using the resources of modal logic. Part I of this dissertation studies what the right modal logic is for reasoning about potential infinity. I begin Part I by rehearsing an argument|which is due to Linnebo and which I partially endorse|that the right modal logic is S4.2. Under this assumption, Linnebo has shown that a natural translation of non-modal first-order logic into modal first- order logic is sound and faithful. I argue that for the philosophical purposes at stake, the modal logic in question should be free and extend Linnebo's result to this setting. I then identify a limitation to the argument for S4.2 being the right modal logic for potential infinity. -

Cantor on Infinity in Nature, Number, and the Divine Mind
Cantor on Infinity in Nature, Number, and the Divine Mind Anne Newstead Abstract. The mathematician Georg Cantor strongly believed in the existence of actually infinite numbers and sets. Cantor’s “actualism” went against the Aristote- lian tradition in metaphysics and mathematics. Under the pressures to defend his theory, his metaphysics changed from Spinozistic monism to Leibnizian volunta- rist dualism. The factor motivating this change was two-fold: the desire to avoid antinomies associated with the notion of a universal collection and the desire to avoid the heresy of necessitarian pantheism. We document the changes in Can- tor’s thought with reference to his main philosophical-mathematical treatise, the Grundlagen (1883) as well as with reference to his article, “Über die verschiedenen Standpunkte in bezug auf das aktuelle Unendliche” (“Concerning Various Perspec- tives on the Actual Infinite”) (1885). I. he Philosophical Reception of Cantor’s Ideas. Georg Cantor’s dis- covery of transfinite numbers was revolutionary. Bertrand Russell Tdescribed it thus: The mathematical theory of infinity may almost be said to begin with Cantor. The infinitesimal Calculus, though it cannot wholly dispense with infinity, has as few dealings with it as possible, and contrives to hide it away before facing the world Cantor has abandoned this cowardly policy, and has brought the skeleton out of its cupboard. He has been emboldened on this course by denying that it is a skeleton. Indeed, like many other skeletons, it was wholly dependent on its cupboard, and vanished in the light of day.1 1Bertrand Russell, The Principles of Mathematics (London: Routledge, 1992 [1903]), 304. -

Grade 7/8 Math Circles the Scale of Numbers Introduction
Faculty of Mathematics Centre for Education in Waterloo, Ontario N2L 3G1 Mathematics and Computing Grade 7/8 Math Circles November 21/22/23, 2017 The Scale of Numbers Introduction Last week we quickly took a look at scientific notation, which is one way we can write down really big numbers. We can also use scientific notation to write very small numbers. 1 × 103 = 1; 000 1 × 102 = 100 1 × 101 = 10 1 × 100 = 1 1 × 10−1 = 0:1 1 × 10−2 = 0:01 1 × 10−3 = 0:001 As you can see above, every time the value of the exponent decreases, the number gets smaller by a factor of 10. This pattern continues even into negative exponent values! Another way of picturing negative exponents is as a division by a positive exponent. 1 10−6 = = 0:000001 106 In this lesson we will be looking at some famous, interesting, or important small numbers, and begin slowly working our way up to the biggest numbers ever used in mathematics! Obviously we can come up with any arbitrary number that is either extremely small or extremely large, but the purpose of this lesson is to only look at numbers with some kind of mathematical or scientific significance. 1 Extremely Small Numbers 1. Zero • Zero or `0' is the number that represents nothingness. It is the number with the smallest magnitude. • Zero only began being used as a number around the year 500. Before this, ancient mathematicians struggled with the concept of `nothing' being `something'. 2. Planck's Constant This is the smallest number that we will be looking at today other than zero. -

Subtraction Strategy
Subtraction Strategies Bley, N.S., & Thornton, C.A. (1989). Teaching mathematics to the learning disabled. Austin, TX: PRO-ED. These math strategies focus on subtraction. They were developed to assist students who are experiencing difficulty remembering subtraction facts, particularly those facts with teen minuends. They are beneficial to students who put heavy reliance on counting. Students can benefit from of the following strategies only if they have ability: to recognize when two or three numbers have been said; to count on (from any number, 4 to 9); to count back (from any number, 4 to 12). Students have to make themselves master related addition facts before using subtraction strategies. These strategies are not research based. Basic Sequence Count back 27 Count Backs: (10, 9, 8, 7, 6, 5, 4, 3, 2) - 1 (11, 10, 9, 8, 7, 6, 5, 4, 3) - 2 (12, 11, 10, 9, 8, 7, 6, 5,4) – 3 Example: 12-3 Students start with a train of 12 cubes • break off 3 cubes, then • count back one by one The teacher gets students to point where they touch • look at the greater number (12 in 12-3) • count back mentally • use the cube train to check Language emphasis: See –1 (take away 1), -2, -3? Start big and count back. Add to check After students can use a strategy accurately and efficiently to solve a group of unknown subtraction facts, they are provided with “add to check activities.” Add to check activities are additional activities to check for mastery. Example: Break a stick • Making "A" train of cubes • Breaking off "B" • Writing or telling the subtraction sentence A – B = C • Adding to check Putting the parts back together • A - B = C because B + C = A • Repeating Show with objects Introduce subtraction zero facts Students can use objects to illustrate number sentences involving zero 19 Zeros: n – 0 = n n – n =0 (n = any number, 0 to 9) Use a picture to help Familiar pictures from addition that can be used to help students with subtraction doubles 6 New Doubles: 8 - 4 10 - 5 12 - 6 14 - 7 16 - 8 18-9 Example 12 eggs, remove 6: 6 are left. -
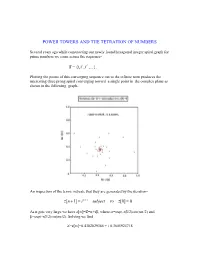
Power Towers and the Tetration of Numbers
POWER TOWERS AND THE TETRATION OF NUMBERS Several years ago while constructing our newly found hexagonal integer spiral graph for prime numbers we came across the sequence- i S {i,i i ,i i ,...}, Plotting the points of this converging sequence out to the infinite term produces the interesting three prong spiral converging toward a single point in the complex plane as shown in the following graph- An inspection of the terms indicate that they are generated by the iteration- z[n 1] i z[n] subject to z[0] 0 As n gets very large we have z[]=Z=+i, where =exp(-/2)cos(/2) and =exp(-/2)sin(/2). Solving we find – Z=z[]=0.4382829366 + i 0.3605924718 It is the purpose of the present article to generalize the above result to any complex number z=a+ib by looking at the general iterative form- z[n+1]=(a+ib)z[n] subject to z[0]=1 Here N=a+ib with a and b being real numbers which are not necessarily integers. Such an iteration represents essentially a tetration of the number N. That is, its value up through the nth iteration, produces the power tower- Z Z n Z Z Z with n-1 zs in the exponents Thus- 22 4 2 22 216 65536 Note that the evaluation of the powers is from the top down and so is not equivalent to the bottom up operation 44=256. Also it is clear that the sequence {1 2,2 2,3 2,4 2,...}diverges very rapidly unlike the earlier case {1i,2 i,3i,4i,...} which clearly converges. -

A Child Thinking About Infinity
A Child Thinking About Infinity David Tall Mathematics Education Research Centre University of Warwick COVENTRY CV4 7AL Young children’s thinking about infinity can be fascinating stories of extrapolation and imagination. To capture the development of an individual’s thinking requires being in the right place at the right time. When my youngest son Nic (then aged seven) spoke to me for the first time about infinity, I was fortunate to be able to tape-record the conversation for later reflection on what was happening. It proved to be a fascinating document in which he first treated infinity as a very large number and used his intuitions to think about various arithmetic operations on infinity. He also happened to know about “minus numbers” from earlier experiences with temperatures in centigrade. It was thus possible to ask him not only about arithmetic with infinity, but also about “minus infinity”. The responses were thought-provoking and amazing in their coherent relationships to his other knowledge. My research in studying infinite concepts in older students showed me that their ideas were influenced by their prior experiences. Almost always the notion of “limit” in some dynamic sense was met before the notion of one to one correspondences between infinite sets. Thus notions of “variable size” had become part of their intuition that clashed with the notion of infinite cardinals. For instance, Tall (1980) reported a student who considered that the limit of n2/n! was zero because the top is a “smaller infinity” than the bottom. It suddenly occurred to me that perhaps I could introduce Nic to the concept of cardinal infinity to see what this did to his intuitions. -
WRITING and READING NUMBERS in ENGLISH 1. Number in English 2
WRITING AND READING NUMBERS IN ENGLISH 1. Number in English 2. Large Numbers 3. Decimals 4. Fractions 5. Power / Exponents 6. Dates 7. Important Numerical expressions 1. NUMBERS IN ENGLISH Cardinal numbers (one, two, three, etc.) are adjectives referring to quantity, and the ordinal numbers (first, second, third, etc.) refer to distribution. Number Cardinal Ordinal In numbers 1 one First 1st 2 two second 2nd 3 three third 3rd 4 four fourth 4th 5 five fifth 5th 6 six sixth 6th 7 seven seventh 7th 8 eight eighth 8th 9 nine ninth 9th 10 ten tenth 10th 11 eleven eleventh 11th 12 twelve twelfth 12th 13 thirteen thirteenth 13th 14 fourteen fourteenth 14th 15 fifteen fifteenth 15th 16 sixteen sixteenth 16th 17 seventeen seventeenth 17th 18 eighteen eighteenth 18th 19 nineteen nineteenth 19th 20 twenty twentieth 20th 21 twenty-one twenty-first 21st 22 twenty-two twenty-second 22nd 23 twenty-three twenty-third 23rd 1 24 twenty-four twenty-fourth 24th 25 twenty-five twenty-fifth 25th 26 twenty-six twenty-sixth 26th 27 twenty-seven twenty-seventh 27th 28 twenty-eight twenty-eighth 28th 29 twenty-nine twenty-ninth 29th 30 thirty thirtieth 30th st 31 thirty-one thirty-first 31 40 forty fortieth 40th 50 fifty fiftieth 50th 60 sixty sixtieth 60th th 70 seventy seventieth 70 th 80 eighty eightieth 80 90 ninety ninetieth 90th 100 one hundred hundredth 100th 500 five hundred five hundredth 500th 1,000 One/ a thousandth 1000th thousand one thousand one thousand five 1500th 1,500 five hundred, hundredth or fifteen hundred 100,000 one hundred hundred thousandth 100,000th thousand 1,000,000 one million millionth 1,000,000 ◊◊ Click on the links below to practice your numbers: http://www.manythings.org/wbg/numbers-jw.html https://www.englisch-hilfen.de/en/exercises/numbers/index.php 2 We don't normally write numbers with words, but it's possible to do this. -

Simple Statements, Large Numbers
University of Nebraska - Lincoln DigitalCommons@University of Nebraska - Lincoln MAT Exam Expository Papers Math in the Middle Institute Partnership 7-2007 Simple Statements, Large Numbers Shana Streeks University of Nebraska-Lincoln Follow this and additional works at: https://digitalcommons.unl.edu/mathmidexppap Part of the Science and Mathematics Education Commons Streeks, Shana, "Simple Statements, Large Numbers" (2007). MAT Exam Expository Papers. 41. https://digitalcommons.unl.edu/mathmidexppap/41 This Article is brought to you for free and open access by the Math in the Middle Institute Partnership at DigitalCommons@University of Nebraska - Lincoln. It has been accepted for inclusion in MAT Exam Expository Papers by an authorized administrator of DigitalCommons@University of Nebraska - Lincoln. Master of Arts in Teaching (MAT) Masters Exam Shana Streeks In partial fulfillment of the requirements for the Master of Arts in Teaching with a Specialization in the Teaching of Middle Level Mathematics in the Department of Mathematics. Gordon Woodward, Advisor July 2007 Simple Statements, Large Numbers Shana Streeks July 2007 Page 1 Streeks Simple Statements, Large Numbers Large numbers are numbers that are significantly larger than those ordinarily used in everyday life, as defined by Wikipedia (2007). Large numbers typically refer to large positive integers, or more generally, large positive real numbers, but may also be used in other contexts. Very large numbers often occur in fields such as mathematics, cosmology, and cryptography. Sometimes people refer to numbers as being “astronomically large”. However, it is easy to mathematically define numbers that are much larger than those even in astronomy. We are familiar with the large magnitudes, such as million or billion. -

Attributes of Infinity
International Journal of Applied Physics and Mathematics Attributes of Infinity Kiamran Radjabli* Utilicast, La Jolla, California, USA. * Corresponding author. Email: [email protected] Manuscript submitted May 15, 2016; accepted October 14, 2016. doi: 10.17706/ijapm.2017.7.1.42-48 Abstract: The concept of infinity is analyzed with an objective to establish different infinity levels. It is proposed to distinguish layers of infinity using the diverging functions and series, which transform finite numbers to infinite domain. Hyper-operations of iterated exponentiation establish major orders of infinity. It is proposed to characterize the infinity by three attributes: order, class, and analytic value. In the first order of infinity, the infinity class is assessed based on the “analytic convergence” of the Riemann zeta function. Arithmetic operations in infinity are introduced and the results of the operations are associated with the infinity attributes. Key words: Infinity, class, order, surreal numbers, divergence, zeta function, hyperpower function, tetration, pentation. 1. Introduction Traditionally, the abstract concept of infinity has been used to generically designate any extremely large result that cannot be measured or determined. However, modern mathematics attempts to introduce new concepts to address the properties of infinite numbers and operations with infinities. The system of hyperreal numbers [1], [2] is one of the approaches to define infinite and infinitesimal quantities. The hyperreals (a.k.a. nonstandard reals) *R, are an extension of the real numbers R that contains numbers greater than anything of the form 1 + 1 + … + 1, which is infinite number, and its reciprocal is infinitesimal. Also, the set theory expands the concept of infinity with introduction of various orders of infinity using ordinal numbers.