Criminal Complaint and Affidavit
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Modeling and Evaluating the Resilience of Peer-To-Peer Botnets
P2PWNED: Modeling and Evaluating the Resilience of Peer-to-Peer Botnets Christian Rossow∗‡, Dennis Andriesse‡, Tillmann Werner¶, Brett Stone-Gross†, Daniel Plohmann§, Christian J. Dietrich∗, Herbert Bos‡ ∗ Institute for Internet Security, Gelsenkirchen, Germany {rossow,dietrich}@internet-sicherheit.de ‡ VU University Amsterdam, The Netherlands {d.a.andriesse,h.j.bos}@vu.nl § Fraunhofer FKIE, Bonn, Germany, [email protected] † Dell SecureWorks, [email protected] ¶ CrowdStrike, Inc. Abstract—Centralized botnets are easy targets for takedown disrupted using the traditional approach of attacking critical efforts by computer security researchers and law enforcement. centralized infrastructure. Thus, botnet controllers have sought new ways to harden the Even though active P2P botnets such as the Zeus P2P infrastructures of their botnets. In order to meet this objective, some botnet operators have (re)designed their botnets to use variant, Sality, ZeroAccess and Kelihos have survived in the Peer-to-Peer (P2P) infrastructures. Many P2P botnets are far wild for as long as five years, relatively little is known about more resilient to takedown attempts than centralized botnets, the sizes of these botnets. It is difficult to estimate a P2P because they have no single points of failure. However, P2P botnets are subject to unique classes of attacks, such as node botnet’s size, for a number of reasons. P2P botnets often enumeration and poisoning. In this paper, we introduce a use custom protocols, so that researchers must first reverse formal graph model to capture the intrinsic properties and engineer the protocol and encryption before they can track fundamental vulnerabilities of P2P botnets. We apply our the botnet’s population. -

Downloading and Running
City Research Online City, University of London Institutional Repository Citation: Meng, X. (2018). An integrated networkbased mobile botnet detection system. (Unpublished Doctoral thesis, City, Universtiy of London) This is the accepted version of the paper. This version of the publication may differ from the final published version. Permanent repository link: https://openaccess.city.ac.uk/id/eprint/19840/ Link to published version: Copyright: City Research Online aims to make research outputs of City, University of London available to a wider audience. Copyright and Moral Rights remain with the author(s) and/or copyright holders. URLs from City Research Online may be freely distributed and linked to. Reuse: Copies of full items can be used for personal research or study, educational, or not-for-profit purposes without prior permission or charge. Provided that the authors, title and full bibliographic details are credited, a hyperlink and/or URL is given for the original metadata page and the content is not changed in any way. City Research Online: http://openaccess.city.ac.uk/ [email protected] AN INTEGRATED NETWORK- BASED MOBILE BOTNET DETECTION SYSTEM Xin Meng Department of Computer Science City, University of London This dissertation is submitted for the degree of Doctor of Philosophy City University London June 2017 Declaration I hereby declare that except where specific reference is made to the work of others, the contents of this dissertation are original and have not been submitted in whole or in part for consideration for any other degree or qualification in this, or any other University. This dissertation is the result of my own work and includes nothing which is the outcome of work done in collaboration, except where specifically indicated in the text. -
![[Recognising Botnets in Organisations] Barry Weymes Number](https://docslib.b-cdn.net/cover/4207/recognising-botnets-in-organisations-barry-weymes-number-1684207.webp)
[Recognising Botnets in Organisations] Barry Weymes Number
[Recognising Botnets in Organisations] Barry Weymes Number: 662 A thesis submitted to the faculty of Computer Science, Radboud University in partial fulfillment of the requirements for the degree of Master of Science Eric Verheul, Chair Erik Poll Sander Peters (Fox-IT) Department of Computer Science Radboud University August 2012 Copyright © 2012 Barry Weymes Number: 662 All Rights Reserved ABSTRACT [Recognising Botnets in Organisations] Barry WeymesNumber: 662 Department of Computer Science Master of Science Dealing with the raise in botnets is fast becoming one of the major problems in IT. Their adaptable and dangerous nature makes detecting them difficult, if not impossible. In this thesis, we present how botnets function, how they are utilised and most importantly, how to limit their impact. DNS Dynamic Reputations Systems, among others, are an innovative new way to deal with this threat. By indexing individual DNS requests and responses together we can provide a fuller picture of what computer systems on a network are doing and can easily provide information about botnets within the organisation. The expertise and knowledge presented here comes from the IT security firm Fox-IT in Delft, the Netherlands. The author works full time as a security analyst there, and this rich environment of information in the field of IT security provides a deep insight into the current botnet environment. Keywords: [Botnets, Organisations, DNS, Honeypot, IDS] ACKNOWLEDGMENTS • I would like to thank my parents, whom made my time in the Netherlands possible. They paid my tuition, and giving me the privilege to follow my ambition of getting a Masters degree. • My dear friend Dave, always gets a mention in my thesis for asking the questions other dont ask. -

Kelihos Botnet: a Never-Ending Saga
2017 Annual ADFSL Conference on Digital Forensics, Security and Law Proceedings May 15th, 10:00 AM Kelihos Botnet: A Never-Ending Saga Arsh Arora University of Alabama, Birmingham, [email protected] Max Gannon University of Alabama, Birmingham, [email protected] Gary Warner University of Alabama, Birmingham, [email protected] Follow this and additional works at: https://commons.erau.edu/adfsl Part of the Defense and Security Studies Commons, Forensic Science and Technology Commons, Information Security Commons, OS and Networks Commons, Other Computer Sciences Commons, and the Science and Technology Studies Commons Scholarly Commons Citation Arora, Arsh; Gannon, Max; and Warner, Gary, "Kelihos Botnet: A Never-Ending Saga" (2017). Annual ADFSL Conference on Digital Forensics, Security and Law. 4. https://commons.erau.edu/adfsl/2017/papers/4 This Peer Reviewed Paper is brought to you for free and open access by the Conferences at Scholarly Commons. It has been accepted for inclusion in Annual ADFSL Conference on Digital Forensics, Security and Law by an (c)ADFSL authorized administrator of Scholarly Commons. For more information, please contact [email protected]. Kelihos Botnet: A Never-Ending Saga CDFSL Proceedings 2017 KELIHOS BOTNET: A NEVER-ENDING SAGA Arsh Arora, Max Gannon, Gary Warner University of Alabama at Birmingham 1201 University Blvd, Birmingham, AL 35233 fararora, gannonm, [email protected] ABSTRACT This paper investigates the recent behavior of the Kelihos botnet, a spam-sending botnet that accounts for many millions of emails sent each day. The paper demonstrates how a team of students are able to perform a longitudinal malware study, making significant observations and contributions to the understanding of a major botnet using tools and techniques taught in the classroom. -

Characterisation of the Kelihos.B Botnet
Characterisation of the Kelihos.B Botnet Max Kerkers, Jos´eJair Santanna and Anna Sperotto Design and Analysis of Communication Systems (DACS) University of Twente Enschede, The Netherlands [email protected], [email protected], [email protected] Abstract. Botnets are organized networks of infected computers that are used for malicious purposes. An example is Kelihos.B, a botnet of the Kelihos family used primarily for mining bitcoins, sending spam and stealing bitcoin wallets. A large part of the Kelihos.B botnet was sink- holed in early 2012 and since then bots are sending requests to controlled servers. In this paper, we analyze and characterize the behavior of Keli- hos.B. Our analysis is based on the log file of the bot request logged at the sinkhole from March 2012 to early November 2013. We investigate both the overall characteristics of the botnets, as well as on its evolu- tion over time since the time of the sinkholing. Our results indicate that, although this trend is decreasing, there are possibly still newly infected bots even more than a year from the original sinkholing. Keywords: Botnet, Kelihos.B, Hlux2, Characterisation, Sinkhole 1 Introduction Botnets are one of the modern threats to society. A botnet consists of several malware-infected computers (bots) that are controlled by the owners of the bot- net. Botnets have for example been used to send spam or to launch distributed denial of service (DDoS) attacks [1]. One of such botnets is Kelihos.B, which was primarily used for mining bitcoins, sending spam and stealing bitcoin wallets [2]. -

Email Threats 2017
Internet Security Threat Report ISTR Email Threats 2017 An ISTR Special Report Analyst: Ben Nahorney October 2017 Contents Executive summary and key findings Malware Spambots BEC scams Spam User email behavior Protection and best practices Internet Security Threat Report Contents 3 Executive summary and key findings 5 Big numbers 7 Malware 8 Impact 9 Malware distribution 11 Spambots 12 Necurs 12 BlankSlate 12 Fioesrat 13 Silentbrute 13 Pandex 13 Oliner 13 Sarvdap 13 Emotet 13 Waledac 14 BEC scams 15 Latest trends 16 Beyond wire transfers 16 Typosquatting 16 Phishing Figures and Tables 16 Phishing scams of note 8 Email users targeted by malware per month 17 Spam 8 Percent of email users targeted by malware by industry 18 Advertising spam 9 Top three malicious email themes 19 Other distribution methods 10 Downloader detections by month 19 The cost of spam 10 URL malware rate 12 Necurs botnet activity 21 User email behavior 13 Waledac (Kelihos) botnet activity 23 Protection and best practices 15 BEC emails received per organization 24 Email security 15 Top subject lines in BEC scam emails 24 CloudSOC 16 Phishing rate 24 Download Insight 18 Spam rate by half year 24 Advanced antivirus engine 18 Spam campaign advertising pharmaceuticals 24 SONAR behavior engine 19 Bitcoin scam email 24 Ongoing development 19 Example Tofsee email 25 Best practices 19 The website Tofsee email links to 26 About Symantec 22 Broadly shared emails with sensitive information 26 More Information 22 Number of registered TLS email domains Internet Security Threat Report Executive summary and key findings Section 00 00 Executive summary and key findings Page 4 Email Threats 2017 Executive summary Key findings Email is everywhere. -

Offensive Anti-‐Botnet
OFFENSIVE NTI A -‐BOTNET -‐ SO YOU WANT TO TAKE OVER A BOTNET… David Di�rich NANOG 59 University of Washington October 8, 2013 Phoenix, AZ Slides available at: h�p://staff.washington.edu/di�rich/talks/nanog59/ Copyright (C) 2013, David Di�rich. All rights reserved. 1 AGENDA “I’m figh�ng back. What’s the big deal?” Ethics and The Menlo Report What it takes to “do it right” Case studies (maybe not) and observa�ons Conclusions Copyright (C) 2013, David Di�rich. All rights reserved. 2 FRUSTRATION AND LOATHING "We will con�nue to fight the threat of botnets and the criminals behind them," says Davis. "We'll start by dismantling their infrastructure and won't stop un�l they're standing in front of a judge.” Chris Davis, CEO for Defence Intelligence (re: Mariposa Botnet) h�p://security.ulitzer.com/node/1305941 “Law enforcement is not doing their job.” “I’m �red of being passive and taking punches. It’s �me to go on the offensive.” “I have a right to self-‐defense.” S. Ortloff. FAQ: Disabling the new Hlux/Kelihos Botnet, March 2012. h�p://www.securelist.com/en/blog/208193438/FAQ_Disabling_the_new_Hlux_Kelihos_Botnet Copyright (C) 2013, David Di�rich. All rights reserved. 3 SINKHOLE AS A SERVICE? Copyright (C) 2013, David Di�rich. All rights reserved. 4 …OR AS SLIPPERY SLOPE? Copyright (C) 2013, David Di�rich. All rights reserved. 5 EXISTING ETHICS STANDARDS The IEEE, ACM, etc: Codes of Ethics The Belmont Report, the Na�onal Research Act, and Ins�tu�onal Review Boards (IRB) – 45 CFR 46 “Rules of Engagement” – The Law of Armed Conflict – Di�rich/Himma: Ac�ve Response Con�nuum Other Organiza�onal Codes (Universi�es, Corpora�ons, etc.) Copyright (C) 2013, David Di�rich. -

Promoting Stakeholder Action Against Botnets and Other Automated Threats
CROWDSTRIKE // SOLUTION BRIEF PROMOTING STAKEHOLDER ACTION AGAINST BOTNETS AND OTHER AUTOMATED THREATS NATIONAL TELECOMMUNICATIONS AND INFORMATION ADMINISTRATION, U.S. DEPARTMENT OF COMMERCE JULY 13, 2017 | WWW.CROWDSTRIKE.COM I. BACKGROUND In response to the U.S. Department of Commerce, National Telecommunications and Information Administration’s (NTIA) Request For Comment (RFC) on Promoting "Eight out of 10 attack Stakeholder Action Against Botnets and Other Automated Threats [1], CrowdStrike® offers the following views. We commend the focus on this critically important issue vectors that resulted in the May 11 Presidential Executive Order on Strengthening the Cybersecurity of Federal Networks and Critical Infrastructure [2] and this follow-through effort. in a successful The articulated intent, to "lead an open and transparent process to identify and promote action by appropriate stakeholders to improve the resilience of the Internet breach used fileless and communications ecosystem and to encourage collaboration with the goal of attack techniques.” dramatically reducing threats perpetrated by automated and distributed attacks (e.g., botnets)" is timely and appropriate. Source: CrowdStrike Cyber Intrusion Services Case Book As a leading provider of cybersecurity threat intelligence, services, and endpoint protection software, CrowdStrike has a unique vantage on this topic. The organization has assisted in multiple botnet investigation, disruption and takedown efforts, notably against the GameOver Zeus and Kelihos botnets [3] and actively monitors emerging threats along these lines. Some of the lessons learned during those efforts are captured herein. This comment does not seek to address every issue raised in the RFC; it is limited to areas for which CrowdStrike may offer particular insights. II. -
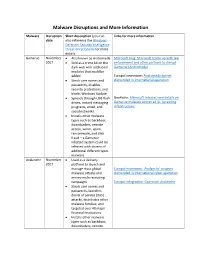
Malware Disruptions and More Information
Malware Disruptions and More Information Malware Disruption Short description (you can Links for more information date also reference the Windows Defender Security Intelligence threat encyclopedia for more details Gamarue November • Also known as Andromeda Microsoft blog: Microsoft teams up with law 2017 • Sold as a crime kit on the enforcement and other partners to disrupt dark web with additional Gamarue (Andromeda) modules that could be added Europol newsroom: Andromeda botnet • Steals user names and dismantled in international operation passwords, disables security protections, and blocks Windows Update • Spreads through USB flash Geekwire: Microsoft releases new details on drives, instant messaging Gamarue malware botnet ad its 'sprawling programs, email, and infrastructure' social networks • Installs other malware types such as backdoor, downloaders, remote access, worm, spam, ransomware, and click fraud – a Gamarue infected system could be infected with dozens of additional different types malware Avalanche November • Used as a delivery 2017 platform to launch and manage mass global Europol newsroom: 'Avalanche' network malware attacks and dismantled in international cyber operation money mule recruiting campaigns Europol infographic: Operation Avalanche • Steals user names and passwords, launches denial of service (DoS) attacks, distributes other malware families, and targeted over 40 major financial institutions • Installs other malware types such as backdoor, downloaders, remote access, worm, spam, and click fraud Barium November -

A Review of Zeroaccess Peer-To-Peer Botnet Ms
International Journal of Computer Trends and Technology (IJCTT) – volume 12 number 2 – Jun 2014 A Review of ZeroAccess peer-to-peer Botnet Ms. Cheenu M.TECH & Graphic Era Hill University Dehradun India Abstract— Today ZeroAccess is one of the widespread In a centralised architecture of C&C, bots contact the C&C threats over the internet. The total number of infected server in order to receive information from the botmaster. systems is in the tens of millions with the number of lively Generally, little time is spent in the transmission of a message infection. ZeroAccess is a Peer-to-peer botnet that affects from the botmaster to all the bots, and this represents one of Microsoft windows operating systems. It is used to the major advantages of this architecture. Its disadvantage is download other malware on an infected machine from a the fact that the C&C server constitutes a single point of Botnet and works as a platform. ZeroAccess is mostly failure. Thus, if the server shuts down, the complete network implicated in bitcoin mining and click fraud, while is shutdown. Examples of centralised botnets; Eggdrop [2], outstanding hidden on a system using rootkit techniques. Gt-Bot and Agobot [3] and Bobax [4]. In this survey, we will explain the Evolution of ZeroAccess In a distributed architecture, all the bots in the botnet act Botnet, the life cycle of ZeroAccess Botnet and concludes simultaneously as servers and clients. This philosophy avoids what are the challenges in ZeroAccess botnet. the existence of a single point of failure, and so this kind of botnet is more resistant than a centralised one. -

Civil Cyberconflict: Microsoft, Cybercrime, and Botnets Janine S
Santa Clara High Technology Law Journal Volume 31 | Issue 2 Article 1 January 2014 Civil Cyberconflict: Microsoft, Cybercrime, and Botnets Janine S. Hiller Follow this and additional works at: http://digitalcommons.law.scu.edu/chtlj Part of the Intellectual Property Law Commons, and the Science and Technology Law Commons Recommended Citation Janine S. Hiller, Civil Cyberconflict: Microsoft, yC bercrime, and Botnets, 31 Santa Clara High Tech. L.J. 163 (2015). Available at: http://digitalcommons.law.scu.edu/chtlj/vol31/iss2/1 This Article is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara High Technology Law Journal by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. 08_ARTICLE_HILLER (DO NOT DELETE) 5/27/2015 1:51 PM CIVIL CYBERCONFLICT: MICROSOFT, CYBERCRIME, AND BOTNETS Janine S. Hiller† Cyber “warfare” and hackback by private companies is a hot discussion topic for its potential to fight cybercrime and promote cybersecurity. In the shadow of this provocative discussion, Microsoft has led a concerted, sustained fight against cybercriminals by using traditional legal theories and court actions to dismantle criminal networks known as botnets. This article brings focus to the role of the private sector in cybersecurity in light of the aggressive civil actions by Microsoft to address a thorny and seemingly intractable global problem. A botnet is a network of computers infected with unauthorized code that is controlled from a distance by malicious actors. The extent of botnet activity is staggering, and botnets have been called the plague of the Internet. -

Executive Summary ——————————————————— 3
In t e r ne t Infrastructure vol.13 Rev iew November 2011 Infrastructure Security Incidents of the Fraudulent Issue of Public Key Certificates Messaging Technology Sender Authentication Technology Reaches the Practical Application Stage with a Focus on SPF Network Technology 100 Gigabit Ethernet In t e r ne t In f r ast r uc t ure Rev iew Vol.13 November 2011 Executive Summary —————————————————— 3 1. Infrastructure Security —————————————— 4 Table of Contents 1.1 Introduction —————————————————————— 4 1.2 Incident Summary —————————————————— 4 1.3 Incident Survey ———————————————————— 12 1.3.1 DDoS Attacks —————————————————————— 12 1.3.2 Malware Activities ———————————————————— 14 1.3.3 SQL Injection Attacks —————————————————— 18 1.4 Focused Research —————————————————— 19 1.4.1 Apache Killer and its Handling ————————————— 19 1.4.2 SpyEye ————————————————————————— 22 1.4.3 Incidents of the Fraudulent Issue of Public Key Certificates —————————————————— 25 1.5 Conclusion —————————————————————— 27 2. Messaging Technology ————————————— 28 2.1 Introduction ————————————————————— 28 2.2 Spam Trends ————————————————————— 28 2.2.1 Spam Volume Decline Stops——————————————— 28 2.2.2 China Remains in Top Spot ——————————————— 29 2.3 Trends in Email Technologies ——————————— 29 2.3.1 SPF Sender Implementation Status ——————————— 30 2.3.2 Global Penetration Rates ———————————————— 30 2.4 Conclusion —————————————————————— 30 3. Network Technology ——————————————— 31 3.1 Introduction ————————————————————— 31 3.2 100GbE ———————————————————————— 31 3.3 100GbE IX Joint Interoperability Test —————— 33 3.4 100GbE Optical Transceivers ——————————— 33 3.5 Conclusion —————————————————————— 34 Internet Topics: 4rd Proof-of-Concept Tests for IIJ’s Proprietary “SEIL” Routers — 35 n To download the latest issue of the Internet Infrastructure Review, please visit (http://www.iij.ad.jp/en/company/development/iir/).