Lorawan Empowers Very Low-Power, Wireless Applications
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Mediatek Linkit™ Development Platform for RTOS Get Started Guide
MediaTek LinkIt™ Development Platform for RTOS Get Started Guide Version: 3.0 Release date: 30 June 2016 © 2015 - 2016 MediaTek Inc. This document contains information that is proprietary to MediaTek Inc. (“MediaTek”) and/or its licensor(s). MediaTek cannot grant you permission for any material that is owned by third parties. You may only use or reproduce this document if you have agreed to and been bound by the applicable license agreement with MediaTek (“License Agreement”) and been granted explicit permission within the License Agreement (“Permitted User”). If you are not a Permitted User, please cease any access or use of this document immediately. Any unauthorized use, reproduction or disclosure of this document in whole or in part is strictly prohibited. THIS DOCUMENT IS PROVIDED ON AN “AS-IS” BASIS ONLY. MEDIATEK EXPRESSLY DISCLAIMS ANY AND ALL WARRANTIES OF ANY KIND AND SHALL IN NO EVENT BE LIABLE FOR ANY CLAIMS RELATING TO OR ARISING OUT OF THIS DOCUMENT OR ANY USE OR INABILITY TO USE THEREOF. Specifications contained herein are subject to change without notice. MediaTek LinkIt™ Development Platform for RTOS Get Started Guide Document Revision History Revision Date Description 1.0 24 March 2016 Initial version. 2.0 17 May 2016 Move the contents relative to flash, HDK, and build comments to corresponding documents. Add the support of Keil 3.0 30 June 2016 Add the support of IAR. Refine the architecture and provide more information on the SDK usage. © 2015 - 2016 MediaTek Inc. Page i of v This document contains information that is proprietary to MediaTek Inc. -

Hannes Tschofenig
Securing IoT applications with Mbed TLS Hannes Tschofenig Part#2: Public Key-based authentication March 2018 © 2018 Arm Limited Munich Agenda • For Part #2 of the webinar we are moving from Pre-Shared Secrets (PSKs) to certificated-based authentication. • TLS-PSK ciphersuites have • great performance, • low overhead, • small code size. • Drawback is the shared key concept. • Public key cryptography was invented to deal with this drawback (but itself has drawbacks). 2 © 2018 Arm Limited Public Key Infrastructure and certificate configuration © 2018 Arm Limited Public Key Infrastructure Various PKI deployments in existence Structure of our PKI The client has to store: self-signed • Client certificate plus corresponding private key. CA cert • CA certificate, which serves as the trust anchor. The server has to store: Signed by CA Signed by CA • Server certificate plus corresponding private key. Client cert Server cert (Some information for authenticating the client) 4 © 2018 Arm Limited Generating certificates (using OpenSSL tools) • When generating certificates you will be prompted to enter info. You are about to be asked to enter information that will be • The CA cert will end up in the trust incorporated into your certificate request. What you are about to enter is what is called a Distinguished anchor store of the client. Name or a DN. There are quite a few fields but you can leave some blank For some fields there will be a default value, • The Common Name used in the server If you enter '.', the field will be left blank. ----- cert needs to be resolvable via DNS Country Name (2 letter code) [AU]:. -

Case Studies
Case studies November 2006 Buyouts Chorion New investment - UK - Media In May 2006, 3i and funds completed the This strong relationship with Waheed Alli acquisition of Chorion, a UK-based coupled with 3i’s in-depth media sector intellectual property owning, brand creation knowledge, through deals such as and management business, in a €198 Sparrowhawk Media and Pinewood million public to private transaction. Shepperton, secured the investment opportunity. Chorion, previously listed on AIM, generates revenue by charging royalties on The investment in Chorion represented an toy merchandising, book publishing and TV. opportunity to acquire a portfolio of high-quality It operates on a global basis, with a brands which have a proven track record of portfolio which includes well recognised publishing success and which are ripe for classic children’s brands such as Noddy, further development. Chorion has an excellent Famous Five, and the Mr Men, as well as platform from which to expand into new the works of crime writers such as Agatha geographic markets, and a proven Christie (Miss Marple and Poirot) and management team which is well placed to Georges Simenon (Maigret). capitalise on this opportunity with the strategic support and financial backing of 3i. 3i worked exclusively with Chorion’s Chairman Waheed Alli and the incumbent management team, responsible for almost trebling the value of the business since 2002, for nearly a year before the deal completed. Buyouts Azzurri Communications Realisation - UK - Technology During the six years that 3i was invested Azzurri made 15 strategic acquisitions and, combined with strong organic growth, a business with revenues of £115 million (for the year to June 2006) was built as a result. -

Freescale Iot Solutions APF-SHB-T1454
Freescale IoT Solutions APF-SHB-T1454 James Huang | Asia MICRO Business Development M A Y . 2 0 1 5 TM External Use The Internet of Things is Driving Explosive Growth 50 In Connected Devices BILLION 25 BILLION 12.5 BILLION 7.6B 7.2B 6.8B 6.5B World 6.3B Population # Connected <1x 1x 2x 3.5x 6.5x Devices/Person 2003 2008 2010 2015 2020 TM External Use 1 * Sources: Ericsson, February 2011; Cisco Internet Business Solutions Group (IBSG), April 2011 IoT emerging as the next mega-trend Internet subscribers over time Source: Goldman Sachs Global Investment Research TM External Use 2 * Sources: Ericsson, February 2011; Cisco Internet Business Solutions Group (IBSG), April 2011 Our Products Power The Internet of Things Microcontrollers | Digital Networking | Auto MCU | Analog and Sensors | RF Traffic Monitoring Metro Cells Base Stations Small Cells Advanced Safety Security Networked Printers Infotainment Radar + Vision Enterprise Gateways, Cloud Data Switchers, Routers Computing Center Home Health Monitors + Fitness Energy Management, Wind + Solar Telehealth Industrial Smart Energy Connected Networking Connected Grid Farms Appliances Digital Power Conversion Energy Human – Machine Meters Interface Home Hubs Machine – Machine Security TM External Use 3 IoT Is More Than M2M The Internet of Things (IoT) is about Machine to Entity (M2E): • Machine to Machine: − Automatic diagnostics for cars: Automatic information collection from your car’s engine management system and sending real- time alerts to drivers or service centers Machine to • Machine to -

CR1000X Product Manual
Revision: 07/20/2021 Copyright © 2000 – 2021 Campbell Scientific, Inc. Table of Contents 1. Introduction 1 2. Precautions 2 3. Initial inspection 3 4. CR1000X data acquisition system components 4 4.1 The CR1000X Datalogger 5 4.1.1 Overview 5 4.1.2 Operations 6 4.1.3 Programs 6 4.2 Sensors 6 5. Wiring panel and terminal functions 8 5.1 Power input 11 5.1.1 Powering a data logger with a vehicle 12 5.1.2 Power LED indicator 12 5.2 Power output 12 5.3 Grounds 13 5.4 Communications ports 15 5.4.1 USB device port 15 5.4.2 Ethernet port 15 5.4.3 C terminals for communications 16 5.4.3.1 SDI-12 ports 16 5.4.3.2 RS-232, RS-422, RS-485, TTL, and LVTTL ports 16 5.4.3.3 SDM ports 16 5.4.4 CS I/O port 17 5.4.5 RS-232/CPI port 18 5.5 Programmable logic control 19 6. Setting up the CR1000X 21 6.1 Setting up communications with the data logger 21 6.1.1 USB or RS-232 communications 21 6.1.2 Virtual Ethernet over USB (RNDIS) 23 6.1.3 Ethernet communications option 24 Table of Contents - i 6.1.3.1 Configuring data logger Ethernet settings 25 6.1.3.2 Ethernet LEDs 26 6.1.3.3 Setting up Ethernet communications between the data logger and computer 26 6.2 Testing communications with EZSetup 27 6.3 Making the software connection 29 6.4 Creating a Short Cut data logger program 29 6.5 Sending a program to the data logger 32 7. -
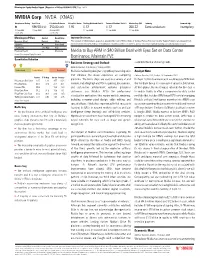
NVIDIA Corp NVDA (XNAS)
Morningstar Equity Analyst Report | Report as of 14 Sep 2020 04:02, UTC | Page 1 of 14 NVIDIA Corp NVDA (XNAS) Morningstar Rating Last Price Fair Value Estimate Price/Fair Value Trailing Dividend Yield % Forward Dividend Yield % Market Cap (Bil) Industry Stewardship Q 486.58 USD 250.00 USD 1.95 0.13 0.13 300.22 Semiconductors Exemplary 11 Sep 2020 11 Sep 2020 20 Aug 2020 11 Sep 2020 11 Sep 2020 11 Sep 2020 21:37, UTC 01:27, UTC Morningstar Pillars Analyst Quantitative Important Disclosure: Economic Moat Narrow Wide The conduct of Morningstar’s analysts is governed by Code of Ethics/Code of Conduct Policy, Personal Security Trading Policy (or an equivalent of), Valuation Q Overvalued and Investment Research Policy. For information regarding conflicts of interest, please visit http://global.morningstar.com/equitydisclosures Uncertainty Very High High Financial Health — Moderate Nvidia to Buy ARM in $40 Billion Deal with Eyes Set on Data Center Source: Morningstar Equity Research Dominance; Maintain FVE Quantitative Valuation NVDA Business Strategy and Outlook could limit Nvidia’s future growth. a USA Abhinav Davuluri, CFA, Analyst, 19 August 2020 Undervalued Fairly Valued Overvalued Nvidia is the leading designer of graphics processing units Analyst Note that enhance the visual experience on computing Abhinav Davuluri, CFA, Analyst, 13 September 2020 Current 5-Yr Avg Sector Country Price/Quant Fair Value 1.67 1.43 0.77 0.83 platforms. The firm's chips are used in a variety of end On Sept. 13, Nvidia announced it would acquire ARM from Price/Earnings 89.3 37.0 21.4 20.1 markets, including high-end PCs for gaming, data centers, the SoftBank Group in a transaction valued at $40 billion. -

QUALCOMM Incorporated (Exact Name of Registrant As Specified in Its Charter)
UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 _____________________ FORM 10-Q _____________________ (Mark one) x QUARTERLY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the quarterly period ended December 25, 2016 OR o TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to . Commission File Number 0-19528 QUALCOMM Incorporated (Exact name of registrant as specified in its charter) Delaware 95-3685934 (State or Other Jurisdiction of (I.R.S. Employer Incorporation or Organization) Identification No.) 5775 Morehouse Dr., San Diego, California 92121-1714 (Address of Principal Executive Offices) (Zip Code) (858) 587-1121 (Registrant’s telephone number, including area code) Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. Yes x No o Indicate by check mark whether the registrant has submitted electronically and posted on its corporate Web site, if any, every Interactive Data File required to be submitted and posted pursuant to Rule 405 of Regulation S-T (§ 232.405 of this chapter) during the preceding 12 months (or for such shorter period that the registrant was required to submit and post such files). Yes x No o Indicate by check mark whether the registrant is a large accelerated filer, an accelerated filer, a non-accelerated filer, or a smaller reporting company. -

IP Production IBC Preview Cloud Playout AMC/Sundance Q&A
IP production www.csimagazine.com IBC preview Cloud playout AMC/Sundance Q&A Welcome to High Dynamic Range television September 2015 cover.indd 1 19/08/2015 12:33:55 Expect More. AMOS Satellites. Meet us at More Coverage. More Throughput. More Services. IBC September 11-15, 2015 Across the Middle East, Europe, Africa and Asia. Amsterdam Hall 1, Booth C.65 Spacecom’s AMOS satellite constellation, consisting of AMOS-2 and AMOS-3 co-located at 4°W, AMOS-4 at 65°E and AMOS-5 at 17°E provides high-quality broadcast and communications services across Europe, Africa, Russia, Asia and the Middle East. With the upcoming launch of AMOS-6, Spacecom is expanding its coverage over Europe and Africa. The result: greater capacity, high-throughput Ka multibeam capabilities and affordable end-to-end satellite services. Spacecom. Expect More. EXPECT MORE www.amos-spacecom.com Untitled-2 1 10/08/2015 12:00:19 Contents IP production www.csimagazine.com IBC preview Cloud playout AMC/Sundance Q&A 30 Online piracy Editor Goran Nastic A new way of thinking about connected revenue security Commercial Welcome to High Dynamic Range television John Woods, Hammad Uddin September 2015 cover.indd 1 19/08/2015 12:33:55 36 Data corner A closer look at SVoD customers Design and production Matt Mills (Manager) 10 Analyst corner Jason Tucker With the first 4k channels launching in Europe, 40 IP production Matleena Lilja-Pelling an assessment of early services and the future It has its pros and cons, which broadcasters would do well to start preparing for Regular contributors 12 COVER STORY - HDR special Adrian Pennington, Philip Hunter, 44 Smart home David Adams, Stephen Cousins, High Dynamic Range really will take TV up a Anna Tobin level but it is not without challenges. -

Iot Development Platform
.org IoT Development Platform 1 Q&A . How many ARM cores shipped in 2012? 8,700,000,000 2020 . 2011 . Per Day: 23,835,616 . Per Hour: 993,151 150+ 25+ billion . Per Minute: 16,553 billion . Per Second: 276 2002 1+ billion 1998 2010 2020 2 ARM is a Semiconductor IP Company ARM’s Ecosystem Financial Tools/Technology IDM Foundry Fabless Semicon Co. Equipment Manufacturer ARM CPU GPU Software Platforms Networking Video RF Security DSP Other IP Carriers + Developers 3 ARM Cortex Advanced Processors Architectural innovation, compatibility across diverse application spectrum MP Cortex-A15 . ARM Cortex™-A family: ...2.5GHz . Applications processors for feature- Cortex-A9 rd rich OS and 3 party applications Cortex-A8 Cortex-A7 ARM Cortex-R family: Cortex-A5 . Cortex-R7 . Embedded processors for real-time Cortex-R5 signal processing, control applications Cortex-R4 Cortex-M4 . ARM Cortex-M family: Cortex-M3 Cortex-M1 . Microcontroller-oriented processors Cortex-M0 for MCU, ASSP, and SoC applications SC300 TM SC000 Applicability Unparalleled . ARM SecureCore Cortex-M0+ . Tamper-resistant security <12k gates... 4 ARM Cortex-M: Ultra Low Power, Size, + Cost 1.9 billion ARM Cortex-M devices shipped in 2012 by leading semiconductor companies MCUs radios sensors Think Powered by Watch Batteries & Energy Harvesting 5 MBED: Enabling Monetization of Disruption “By 2018, 50% of IoT solutions will be from start-ups less than 3 years old” - Gartner 6 From Sensor to Cloud Edge Clients Gateway Network Cloud Temp thin client Device Prox Provisioning and M2M Apps control Cortex-M Modem Diagnostics M2M Apps Smartphone / M2M Apps Short-Range Headless Radio e.g. -

Proceedings First Annual Palo Alto Conference
PROCEEDINGS OF THE FIRST ANNUAL PALO ALTO CONFERENCE An International Conference on the Mexican-American War and its Causes and Consequences with Participants from Mexico and the United States. Brownsville, Texas, May 6-9, 1993 Palo Alto Battlefield National Historic Site Southwest Region National Park Service I Cover Illustration: "Plan of the Country to the North East of the City of Matamoros, 1846" in Albert I C. Ramsey, trans., The Other Side: Or, Notes for the History of the War Between Mexico and the I United States (New York: John Wiley, 1850). 1i L9 37 PROCEEDINGS OF THE FIRST ANNUAL PALO ALTO CONFERENCE Edited by Aaron P. Mahr Yafiez National Park Service Palo Alto Battlefield National Historic Site P.O. Box 1832 Brownsville, Texas 78522 United States Department of the Interior 1994 In order to meet the challenges of the future, human understanding, cooperation, and respect must transcend aggression. We cannot learn from the future, we can only learn from the past and the present. I feel the proceedings of this conference illustrate that a step has been taken in the right direction. John E. Cook Regional Director Southwest Region National Park Service TABLE OF CONTENTS Introduction. A.N. Zavaleta vii General Mariano Arista at the Battle of Palo Alto, Texas, 1846: Military Realist or Failure? Joseph P. Sanchez 1 A Fanatical Patriot With Good Intentions: Reflections on the Activities of Valentin GOmez Farfas During the Mexican-American War. Pedro Santoni 19 El contexto mexicano: angulo desconocido de la guerra. Josefina Zoraida Vazquez 29 Could the Mexican-American War Have Been Avoided? Miguel Soto 35 Confederate Imperial Designs on Northwestern Mexico. -

Paradigm Shift: the Winners Are
PARADIGM SHIFT: THE WINNERS ARE Dr. Jeremy Wang Asia Pacific Executive Director, GSA July 30, 2008 GSA Mission Accelerate the growth and increase the return on invested capital of the global semiconductor industry by fostering a more effective fabless ecosystem through collaboration, integration and innovation. GSA Board of Directors Dwight Decker Sanjay Jha Jodi Shelton Danny Biran Rick Cassidy Guillame Aart de Geus Conexant Qualcomm Altera TSMC North d’Eyssautier Synopsys, America picoChip Inc. Jack Harding Colin Harris Kenneth Joyce Fu Tai Liou Steven Longoria Dr. Nicky Lu Chris eSilicon Corp PMC-Sierra, Amkor UMC IBM Etron Malachowsky Inc. Technology, Inc. NVIDIA Vahid Manian Michael Rekuc Walden Rhines Naveed Vincent Tong Dr. Albert Wu Dr. Tien Wu Broadcom Chartered Mentor Graphics Sherwani Xilinx Marvell ASE, Inc. Corporation Open-Silicon Asia-Pacific Leadership Council Chairman Dr. Chintay Shih Xiaolang Yan Ming Kai Tsai H.P. Lin Qin-Sheng Wang K.C. Shih Dr. Nicky Lu Special Advisor College of MediaTek Faraday IC China Semiconductor Global Unichip Etron Information Industry Association Science and Engineering Zhejiang University Special Advisor Gordon Gau Chou-Chye Wen-Chi Chen Dr. Woodward Dr. Zhonghan Dr. Shaojun Wei Holtek Huang VIA Yang (John) Deng Phoenix Sunplus Silicon7 Vimicro Microelectronics Jordan Wu Dr. Ki Soo Lun Zhao Dr. Ping Wu Himax Hwang Datang Spreadtrum Technologies Core Logic, Inc. Microelectronics Communications Inc. EMEA Leadership Council David Milne Jalal Bagherli David Baillie Kobi Ben-Zvi Stan Boland Wolfson Dialog CamSemi Wintegra Icera Microelectronics Semiconductor Warren East Guillame d’Eyssautier Danny Hachoen Gennady Krasnikov Chris Ladas ARM, Inc. picoChip DSP Group Mikron JSC CSR Key Topics •Analog/Mixed Signal •Wireless •Automotive Eric Mayer John Schmitz Infineon NXP Semiconductor VC Advisory Council Wayne Cantwell Steve Domenik Phillip T. -

Cybercrime Prevention Principles for Internet Service Providers
Shaping the Future of Cybersecurity and Digital Trust Cybercrime Prevention Principles for Internet Service Providers January 2020 World Economic Forum 91-93 route de la Capite CH-1223 Cologny/Geneva Switzerland Tel.: +41 (0)22 869 1212 Fax: +41 (0)22 786 2744 Email: [email protected] www.weforum.org © 2020 World Economic Forum. All rights reserved. No part of this publication may be reproduced or transmitted in any form or by any means, including photocopying and recording, or by any information storage and retrieval system. 1 Cybercrime Prevention: Principles for Internet Service Providers Contents Preface 3 Foreword 4 Executive Summary 5 Incentives for Action and Expected Outcomes 6 Context – Scale of the Threat 7 Principle 1. Protect consumers by default from widespread cyberattacks and act collectively with peers to identify and respond to known threats 8 1.1 What challenge does this principle address? 8 1.2 How can this principle create impact? 8 1.3 Recommendations for implementation 10 Principle 2. Take action to raise awareness and understanding of threats and support consumers in protecting themselves and their networks 11 2.1 What challenge does this principle address? 11 2.2 How can this principle create impact? 12 2.3 Recommendations for implementation 14 Principle 3. Work more closely with manufacturers and vendors of hardware, software and infrastructure to raise minimum levels of security 16 3.1 What challenge does this principle address? 16 3.2 How can this principle create impact? 16 3.3 Recommendations for implementation