Configuration Manager User Guide © 2019 Quest Software Inc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
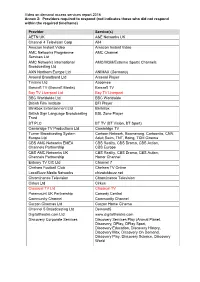
Annex 2: Providers Required to Respond (Red Indicates Those Who Did Not Respond Within the Required Timeframe)
Video on demand access services report 2016 Annex 2: Providers required to respond (red indicates those who did not respond within the required timeframe) Provider Service(s) AETN UK A&E Networks UK Channel 4 Television Corp All4 Amazon Instant Video Amazon Instant Video AMC Networks Programme AMC Channel Services Ltd AMC Networks International AMC/MGM/Extreme Sports Channels Broadcasting Ltd AXN Northern Europe Ltd ANIMAX (Germany) Arsenal Broadband Ltd Arsenal Player Tinizine Ltd Azoomee Barcroft TV (Barcroft Media) Barcroft TV Bay TV Liverpool Ltd Bay TV Liverpool BBC Worldwide Ltd BBC Worldwide British Film Institute BFI Player Blinkbox Entertainment Ltd BlinkBox British Sign Language Broadcasting BSL Zone Player Trust BT PLC BT TV (BT Vision, BT Sport) Cambridge TV Productions Ltd Cambridge TV Turner Broadcasting System Cartoon Network, Boomerang, Cartoonito, CNN, Europe Ltd Adult Swim, TNT, Boing, TCM Cinema CBS AMC Networks EMEA CBS Reality, CBS Drama, CBS Action, Channels Partnership CBS Europe CBS AMC Networks UK CBS Reality, CBS Drama, CBS Action, Channels Partnership Horror Channel Estuary TV CIC Ltd Channel 7 Chelsea Football Club Chelsea TV Online LocalBuzz Media Networks chizwickbuzz.net Chrominance Television Chrominance Television Cirkus Ltd Cirkus Classical TV Ltd Classical TV Paramount UK Partnership Comedy Central Community Channel Community Channel Curzon Cinemas Ltd Curzon Home Cinema Channel 5 Broadcasting Ltd Demand5 Digitaltheatre.com Ltd www.digitaltheatre.com Discovery Corporate Services Discovery Services Play -
Channel Guide August 2018
CHANNEL GUIDE AUGUST 2018 KEY HOW TO FIND WHICH CHANNELS YOU HAVE 1 PLAYER PREMIUM CHANNELS 1. Match your ENTERTAINMENT package 1 2 3 4 5 6 2 MORE to the column 100 Virgin Media Previews 3 M+ 101 BBC One If there’s a tick 4 MIX 2. 102 BBC Two in your column, 103 ITV 5 FUN you get that 104 Channel 4 6 FULL HOUSE channel ENTERTAINMENT SPORT 1 2 3 4 5 6 1 2 3 4 5 6 100 Virgin Media Previews 501 Sky Sports Main Event 101 BBC One HD 102 BBC Two 502 Sky Sports Premier 103 ITV League HD 104 Channel 4 503 Sky Sports Football HD 105 Channel 5 504 Sky Sports Cricket HD 106 E4 505 Sky Sports Golf HD 107 BBC Four 506 Sky Sports F1® HD 108 BBC One HD 507 Sky Sports Action HD 109 Sky One HD 508 Sky Sports Arena HD 110 Sky One 509 Sky Sports News HD 111 Sky Living HD 510 Sky Sports Mix HD 112 Sky Living 511 Sky Sports Main Event 113 ITV HD 512 Sky Sports Premier 114 ITV +1 League 115 ITV2 513 Sky Sports Football 116 ITV2 +1 514 Sky Sports Cricket 117 ITV3 515 Sky Sports Golf 118 ITV4 516 Sky Sports F1® 119 ITVBe 517 Sky Sports Action 120 ITVBe +1 518 Sky Sports Arena 121 Sky Two 519 Sky Sports News 122 Sky Arts 520 Sky Sports Mix 123 Pick 521 Eurosport 1 HD 132 Comedy Central 522 Eurosport 2 HD 133 Comedy Central +1 523 Eurosport 1 134 MTV 524 Eurosport 2 135 SYFY 526 MUTV 136 SYFY +1 527 BT Sport 1 HD 137 Universal TV 528 BT Sport 2 HD 138 Universal -

REPORT CARD: MAKING the HDTV PLUNGE by RON HRANAC
Originally appeared in the March 2009 issue of Communications Technology. REPORT CARD: MAKING THE HDTV PLUNGE By RON HRANAC After putting it off for several years, I finally joined the slightly more than one-third of Americans who have already done so, and got a high definition TV (HDTV) set for home use. I had all sorts of excuses for putting this off, among them cost, a 15+ year-old conventional TV set that still works fine, a wife who said the 15+ year-old TV set works just fine (see a trend here?), picture quality with standard definition (SD) sources, rear projection vs. liquid crystal display (LCD) vs. plasma, and even picture quality with HD sources. During the past few years, the cost of HD sets has come down dramatically. Technology has improved to the point where both SD and HD picture quality are quite good on many of the new sets, though there are still some HD sets that do an abysmal job displaying SD material. The latter is important because, quite frankly, a lot of video content is SD and will be for the foreseeable future. Then and now My first experience with HDTV goes back to a 1980s National Association of Broadcasters convention. The concept of high-def had been introduced as a way to provide widescreen TV viewing rivaling projected 35 mm motion pictures, accompanied by CD-quality audio. One of the hopes was that a global HDTV standard could be developed, avoiding the NTSC/PAL/SECAM format battles that have long plagued broadcast TV - OK, maybe that was wishful thinking. -

Globalization Strategies Utilized by Discovery Networks: a Case Study
Globalization Strategies Utilized by Discovery Networks: A Case Study A Thesis Submitted to the Faculty of Drexel University by Jingyi Yang in partial fulfillment of the requirements for the degree of Master of Science February 2014 ii iii © Copyright 2014 Jingyi Yang. All Rights Reserved. iv Table of Contents Table of Contents .................................................................................................. iv List of Tables ......................................................................................................... v CHAPTER 1: INTRODUCTION .......................................................................... 1 Introduction ................................................................................................................... 1 Purpose of the Study ..................................................................................................... 3 Statement of the Problem .............................................................................................. 4 Research Questions ....................................................................................................... 7 Definitions ..................................................................................................................... 8 Limitations .................................................................................................................. 10 CHAPTER 2: LITERATURE REVIEW ............................................................. 11 CHAPTER 3: METHODOLOGY ...................................................................... -

TV & Radio Channels Astra 2 UK Spot Beam
UK SALES Tel: 0345 2600 621 SatFi Email: [email protected] Web: www.satfi.co.uk satellite fidelity Freesat FTA (Free-to-Air) TV & Radio Channels Astra 2 UK Spot Beam 4Music BBC Radio Foyle Film 4 UK +1 ITV Westcountry West 4Seven BBC Radio London Food Network UK ITV Westcountry West +1 5 Star BBC Radio Nan Gàidheal Food Network UK +1 ITV Westcountry West HD 5 Star +1 BBC Radio Scotland France 24 English ITV Yorkshire East 5 USA BBC Radio Ulster FreeSports ITV Yorkshire East +1 5 USA +1 BBC Radio Wales Gems TV ITV Yorkshire West ARY World +1 BBC Red Button 1 High Street TV 2 ITV Yorkshire West HD Babestation BBC Two England Home Kerrang! Babestation Blue BBC Two HD Horror Channel UK Kiss TV (UK) Babestation Daytime Xtra BBC Two Northern Ireland Horror Channel UK +1 Magic TV (UK) BBC 1Xtra BBC Two Scotland ITV 2 More 4 UK BBC 6 Music BBC Two Wales ITV 2 +1 More 4 UK +1 BBC Alba BBC World Service UK ITV 3 My 5 BBC Asian Network Box Hits ITV 3 +1 PBS America BBC Four (19-04) Box Upfront ITV 4 Pop BBC Four (19-04) HD CBBC (07-21) ITV 4 +1 Pop +1 BBC News CBBC (07-21) HD ITV Anglia East Pop Max BBC News HD CBeebies UK (06-19) ITV Anglia East +1 Pop Max +1 BBC One Cambridge CBeebies UK (06-19) HD ITV Anglia East HD Psychic Today BBC One Channel Islands CBS Action UK ITV Anglia West Quest BBC One East East CBS Drama UK ITV Be Quest Red BBC One East Midlands CBS Reality UK ITV Be +1 Really Ireland BBC One East Yorkshire & Lincolnshire CBS Reality UK +1 ITV Border England Really UK BBC One HD Channel 4 London ITV Border England HD S4C BBC One London -

Pebble Discovery History by Phil St
Pebble Discovery History by Phil St. George, 2018 The discovery of Pebble took place through a progression of events and a series of exploration programs managed by Cominco Alaska. Several people discussed below were critical to the discovery as without their efforts we wouldn’t have progressed into the exploration of that area. The earliest exploration in the Southwest Alaska was a short sampling program recommended by Joe Piekenbrock in 1982. The first program was to scout out potential for tin and gold within a short 1 week helicopter program based out of Dillingham and included Joe Piekenbrock, Roy McMichael, Phil St. George and Helen Farnstom Robertson. Exploring north of Koliganek, in the Taylor Mountain USGS 1:25000 quadrangle. Tin was found at Sleitat Mountain, and other tin occurrences were found on hills south of the King Salmon River, a tributary to the Nushagak River. In late 1982 and early 1983, Roy McMichael, a senior geologist at Cominco created a joint venture with Enstar Natural Gas Company to do further exploration in the Taylor Mountain, Sleetmute, Iditarod and Lime Hills quadrangles, an area stretching from Koliganek to Flat, Lime Village and up to McGrath. An Area of Interest was signed in the Joint Venture agreement. Joe Piekenbrock managed this program and the discovery of a gold deposit on the south side of the Shotgun Hills was made by Joe and called Mose initially and then Shotgun by later workers. Rock sampling for tin at Sleitat Mountain indicated a potential ore deposit. In 1984, drilling was initiated at Sleitat Mountain, and then later at Mose. -
Channel Guide July 2019
CHANNEL GUIDE JULY 2019 KEY HOW TO FIND WHICH CHANNELS YOU CAN GET 1 PLAYER 1 MIXIT 1. Match your package 2. If there’s a tick in 3. If there’s a plus sign, it’s to the column your column, you available as part of a 2 MIX 2 MAXIT get that channel Personal Pick collection 3 FUN PREMIUM CHANNELS 4 FULL HOUSE + PERSONAL PICKS 1 2 3 4 5 6 101 BBC One/HD* + 110 Sky One ENTERTAINMENT SPORT 1 2 3 4 5 6 1 2 3 4 5 6 100 Virgin Media Previews HD 501 Sky Sports Main Event HD 101 BBC One/HD* 502 Sky Sports Premier League HD 102 BBC Two HD 503 Sky Sports Football HD 103 ITV/STV HD* 504 Sky Sports Cricket HD 104 Channel 4 505 Sky Sports Golf HD 105 Channel 5 506 Sky Sports F1® HD 106 E4 507 Sky Sports Action HD 107 BBC Four HD 508 Sky Sports Arena HD 108 BBC One HD/BBC Scotland HD* 509 Sky Sports News HD 109 Sky One HD 510 Sky Sports Mix HD + 110 Sky One 511 Sky Sports Main Event 111 Sky Witness HD 512 Sky Sports Premier League + 112 Sky Witness 513 Sky Sports Football 113 ITV HD* 514 Sky Sports Cricket 114 ITV +1 515 Sky Sports Golf 115 ITV2 516 Sky Sports F1® 116 ITV2 +1 517 Sky Sports Action 117 ITV3 518 Sky Sports Arena 118 ITV4 + 519 Sky Sports News 119 ITVBe + 520 Sky Sports Mix 120 ITVBe +1 + 521 Eurosport 1 HD + 121 Sky Two + 522 Eurosport 2 HD + 122 Sky Arts + 523 Eurosport 1 123 Pick + 524 Eurosport 2 + 124 GOLD HD 526 MUTV + 125 W 527 BT Sport 1 HD + 126 alibi 528 -

Voodoo Channel List
voodoo channel list ############################################################################## # English: 450-581 ############################################################################## # CBC HD Bravo USA CBS HF USA Space HD Global TV HD ABC HD USA AMC HD WPIX HD1 A/E USA LMN HD Fox HD USA Spike HD CNBC USA KTLA HD HIFI HD FX HD USA NBC HD CTV HD TNT HD E! HD SYFY HD USA Slice HD CP24 HD HBO HD Showcase HD Encore HD Showtime HD Start Movies HD Super CH 1 HD Super CH 2 HD TLC HD USA History HD USA History HD 2 National Geographic HD1 National Geographic USA Oasis HD Animal Planet HD USA Food Network HD USA HG TV USA Discovery HD USA Oasis Bloomberg HD USA CNN HD USA CNN Aljazeera English HLN Russia Today BBC News BBC 2 Bloomberg TV France 24 English Animal Planet Discovery Channel Discovery History Discovery Science Discovery History CBS Action CBS Drama CBS Reality Comedy Central Fashion TV Film4 Food Network FOX Investigation Discovery Lotus Movies MTV Music NASA TV Nat Geo Wild National Geographic Sky 2 Sky Living HYD Sky Movies Action Sky Movies Comedy Sky Movies Crime & Thriller Sky Movies Drama & Romance Sky Movies Family Sky Movies Premiere Sky Movies Sci-Fi & Horror Sky News Sky One SyFy Travel Channel True Movies 1, 2 UK Gold VH1 ############################################################################## # Sports: 600-643 ############################################################################## # TSN- 1, 2, 3, 4, 5 ESPN 2 USA NFL Network1 NBA TV Sportnet Ontario1 Sportnet World Sportnet 360 Tennis HD Sportsnet -

Discovery, Inc. Y
UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 FORM 10-K È ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2019 OR ‘ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to Commission File Number: 001-34177 Discovery, Inc. (Exact name of Registrant as specified in its charter) Delaware35-2333914 (State or other jurisdiction of (I.R.S. Employer incorporation or organization) Identification No.) 8403 Colesville Road Silver Spring, Maryland 20910 (Address of principal executive offices)(Zip Code) (240) 662-2000 (Registrant’s telephone number, including area code) Securities registered pursuant to Section 12(b) of the Act: Title of Each Class Trading Symbols Name of Each Exchange on Which Registered Series A Common Stock, par value $ 0.01 per share DISCA The Nasdaq Global Select Market Series B Common Stock, par value $ 0.01 per share DISCB The Nasdaq Global Select Market Series C Common Stock, par value $ 0.01 per share DISCK The Nasdaq Global Select Market Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the Registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes È No ‘ Indicate by check mark if the Registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes ‘ No È Indicate by check mark whether the Registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the Registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

Trends in Television Viewing 2014
TRENDS IN TELEVISION VIEWING 2014 Published: March 2015 TABLE 1 AVERAGE DAILY HOURS OF VIEWING - TOTAL TV ALL INDIVIDUALS Qtr 1 Qtr 2 Qtr 3 Qtr 4 FULL YEAR 1996 3.95 3.39 3.25 3.78 3.59 1997 3.89 3.41 3.29 3.77 3.59 1998 3.84 3.46 3.34 3.78 3.61 1991-2001 PANEL 1999 3.91 3.48 3.35 3.93 3.67 2000 3.86 3.49 3.43 3.91 3.67 2001 3.95 3.46 3.34 3.75 3.62 2002 3.54 3.47 3.36 3.80 3.54 2003 3.99 3.55 3.41 3.95 3.73 2004 4.00 3.50 3.46 3.89 3.71 2005 3.91 3.45 3.42 3.81 3.65 2002-2009 PANEL 2006 3.89 3.43 3.31 3.76 3.60 2007 3.85 3.46 3.38 3.83 3.63 2008 3.97 3.57 3.54 3.88 3.74 2009 3.96 3.56 3.54 3.94 3.75 2010 4.27 3.76 3.76 4.35 4.03 2011 4.21 3.86 3.83 4.22 4.03 CURRENT PANEL 2012 4.12 3.92 3.86 4.12 4.01 2013 4.20 3.72 3.53 4.00 3.87 2014 3.90 3.52 3.43 3.86 3.68 Average daily hours of viewing is in decimal form; i.e. 3.75 is equivalent to 3 hours and 45 minutes. -

Identification of Biomolecules Involved in the Adaptation to The
biomolecules Review Identification of Biomolecules Involved in the Adaptation to the Environment of Cold-Loving Microorganisms and Metabolic Pathways for Their Production Eva Garcia-Lopez, Paula Alcazar and Cristina Cid * Molecular Evolution Department, Centro de Astrobiologia (CSIC-INTA), Torrejón de Ardoz, 28850 Madrid, Spain; [email protected] or [email protected] (E.G.-L.); [email protected] (P.A.) * Correspondence: [email protected]; Tel.: +34-91-520-5455 Abstract: Cold-loving microorganisms of all three domains of life have unique and special abilities that allow them to live in harsh environments. They have acquired structural and molecular mecha- nisms of adaptation to the cold that include the production of anti-freeze proteins, carbohydrate-based extracellular polymeric substances and lipids which serve as cryo- and osmoprotectants by maintain- ing the fluidity of their membranes. They also produce a wide diversity of pigmented molecules to obtain energy, carry out photosynthesis, increase their resistance to stress and provide them with ultraviolet light protection. Recently developed analytical techniques have been applied as high- throughoutput technologies for function discovery and for reconstructing functional networks in psychrophiles. Among them, omics deserve special mention, such as genomics, transcriptomics, pro- teomics, glycomics, lipidomics and metabolomics. These techniques have allowed the identification of microorganisms and the study of their biogeochemical activities. They have also made it possible Citation: Garcia-Lopez, E.; Alcazar, P.; Cid, C. Identification of to infer their metabolic capacities and identify the biomolecules that are parts of their structures Biomolecules Involved in the or that they secrete into the environment, which can be useful in various fields of biotechnology. -

EXPAT PLATINUM List of Channels
EXPAT PLATINUM List of channels BBC TWO HQ ITV BE Documentary BOOMERANG ITV ENCORE ANIMAL PLANET DK BRAVO HD KANAL 4 ANIMAL PLANET GB C MORE FIRST KANAL 5 DK ANIMAL PLANET HQ C MORE HITS KANAL 5 SE CRIME AND INVESTIGATION C MORE SERIES KANAL 9 DISCOVERY CHANNEL CANAL 9 KTLA DISCOVERY DK CBBC KUNSKAPSKANALEN DISCOVERY HD CBS MAX DISCOVERY HISTORY CBS ACTION MORE 4 DISCOVERY HOME AND CBS HD NBC HD HEALTH CBS REALITY NBC HQ DISCOVERY NO CHANNEL 4 NRK 1 DISCOVERY SCIENCE CHANNEL 4 HQ NRK 2 DISCOVERY SE CHANNEL 5 NRK 3 DISCOVERY TURBO CHANNEL TV PICK DISCOVERY US COMEDY CENTRAL GB REALLY H2 COMEDY CENTRAL HD RTE 1 HISTORY GB COMEDY CENTRAL US RTE 2 HISTORY HD DAVE SHOWTIME HISTORY US DK 4 SHOWTIME HD INVESTIGATION DISCOVERY DR 1 SJUAN NAT GEO DR 2 SKY 1 NAT GEO HD DR 3 SKY 2 NAT GEO WILD DR K SKY ATLANTIC QUEST DR RAMASJANG SVT 1 Entertainment DR ULTRA SVT 2 E! ENTERTAINMENT SVTB/SVT24 5 STAR E4 TNT HQ 5 USA EDEN TV 10 6EREN FEM TV 12 SWEDEN A AND E FOX GB TV 2 BLISS ABC FOX US TV 2 CHARLIE ALIBI GOLD TV 2 DK AMC HOME TV 2 FRI AMC HD ITV 1 TV 2 NO BBC FOUR ITV 1 HQ TV 2 ZEBRA BBC ONE ITV 2 TV 2 ZULU BBC ONE HQ ITV 3 TV 3 DK BBC TWO ITV 4 TV 3 NO - 1/3 - EXPAT PLATINUM List of channels TV 3 PLUS HBO ZONE HQ ARENA SPORTS 3 HQ TV 3 PULS MOREMAX HQ ARENA SPORTS 4 HQ TV 3 SE MOVIES4MEN ARENA SPORTS 5 HQ TV 4 FAKTA SKY ACTION AT THE RACES TV 4 GULD SKY COMEDY AUSTRALIA PLUS TV 4 KOMEDI SKY CRIME BEIN SPORTS TV 6 NO SKY DRAMA BOX NATION TV 6 SE SKY FAMILY BRITISH EUROSPORT TV 8 SKY MODERN GREATS BRITISH EUROSPORT 2 TV NORGE SKY PREMIERE BT SPORT