Promoting Healthy Sleep Among US Servicemembers
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Application for a Certificate of Eligibility to Employ Child Performers
Division of Labor Standards Permit and Certificate Unit Harriman State Office Campus Building 12, Room 185B Albany, NY 12240 www.labor.ny.gov Application for a Certificate of Eligibility to Employ Child Performers A. Submission Instructions A Certificate of Eligibility to Employ Child Performers must be obtained prior to employing any child performer. Certificates are renew able every three (3) years. To obtain or renew a certificate: • Complete Parts B, C, D and E of this application. • Attach proof of New York State Workers’ Compensation and Disability Insurance. o If you currently have employees in New York, you must provide proof of coverage for those New York State w orkers by attaching copies of Form C-105.2 and DB-120.1, obtainable from your insurance carrier. o If you are currently exempt from this requirement, complete Form CE-200 attesting that you are not required to obtain New York State Workers’ Compensation and Disability Insurance Coverage. Information on and copies of this form are available from any district office of the Workers’ Compensation Board or from their w ebsite at w ww.wcb.ny.gov, Click on “WC/DB Exemptions,” then click on “Request for WC/DB Exemptions.” • Attach a check for the correct amount from Section D, made payable to the Commissioner of Labor. • Sign and mail this completed application and all required documents to the address listed above. If you have any questions, call (518) 457-1942, email [email protected] or visit the Department’s w ebsite at w ww.labor.ny.gov B. Type of Request (check one) New Renew al Current certificate number _______________________________________________ Are you seeking this certificate to employ child models? Yes No C. -

Program #6: Word Count
CSc 227 — Program Design and Development Spring 2014 (McCann) http://www.cs.arizona.edu/classes/cs227/spring14/ Program #6: Word Count Due Date: March 11 th, 2014, at 9:00 p.m. MST Overview: The UNIX operating system (and its variants, of which Linux is one) includes quite a few useful utility programs. One of those is wc, which is short for Word Count. The purpose of wc is to give users an easy way to determine the size of a text file in terms of the number of lines, words, and bytes it contains. (It can do a bit more, but that’s all of the functionality that we are concerned with for this assignment.) Counting lines is done by looking for “end of line” characters (\n (ASCII 10) for UNIX text files, or the pair \r\n (ASCII 13 and 10) for Windows/DOS text files). Counting words is also straight–forward: Any sequence of characters not interrupted by “whitespace” (spaces, tabs, end–of–line characters) is a word. Of course, whitespace characters are characters, and need to be counted as such. A problem with wc is that it generates a very minimal output format. Here’s an example of what wc produces on a Linux system when asked to count the content of a pair of files; we can do better! $ wc prog6a.dat prog6b.dat 2 6 38 prog6a.dat 32 321 1883 prog6b.dat 34 327 1921 total Assignment: Write a Java program (completely documented according to the class documentation guidelines, of course) that counts lines, words, and bytes (characters) of text files. -

1 A) Login to the System B) Use the Appropriate Command to Determine Your Login Shell C) Use the /Etc/Passwd File to Verify the Result of Step B
CSE ([email protected] II-Sem) EXP-3 1 a) Login to the system b) Use the appropriate command to determine your login shell c) Use the /etc/passwd file to verify the result of step b. d) Use the ‘who’ command and redirect the result to a file called myfile1. Use the more command to see the contents of myfile1. e) Use the date and who commands in sequence (in one line) such that the output of date will display on the screen and the output of who will be redirected to a file called myfile2. Use the more command to check the contents of myfile2. 2 a) Write a “sed” command that deletes the first character in each line in a file. b) Write a “sed” command that deletes the character before the last character in each line in a file. c) Write a “sed” command that swaps the first and second words in each line in a file. a. Log into the system When we return on the system one screen will appear. In this we have to type 100.0.0.9 then we enter into editor. It asks our details such as Login : krishnasai password: Then we get log into the commands. bphanikrishna.wordpress.com FOSS-LAB Page 1 of 10 CSE ([email protected] II-Sem) EXP-3 b. use the appropriate command to determine your login shell Syntax: $ echo $SHELL Output: $ echo $SHELL /bin/bash Description:- What is "the shell"? Shell is a program that takes your commands from the keyboard and gives them to the operating system to perform. -

Sexsomnia.Pdf
ARTICLE IN PRESS BRESR-100534; No. of pages: 12; 4C: BRAIN RESEARCH REVIEWS XX (2007) XXX– XXX available at www.sciencedirect.com www.elsevier.com/locate/brainresrev Review ☆ Sexsomnia: Abnormal sexual behavior during sleep Monica L. Andersena,⁎, Dalva Poyaresa, Rosana S.C. Alvesb, Robert Skomroc, Sergio Tufika aDepartment of Psychobiology - Universidade Federal de São Paulo, Escola Paulista de Medicina (UNIFESP/EPM), São Paulo, SP, Brazil bDepartment of Neurology - University of São Paulo (USP), São Paulo, SP, Brazil cUniversity of Saskatchewan, Saskatoon, Saskatchewan, Canada ARTICLE INFO ABSTRACT Article history: This review attempts to assemble the characteristics of a distinct variant of sleepwalking Accepted 26 June 2007 called sexsomnia/sleepsex from the seemingly scarce literature into a coherent theoretical framework. Common features of sexsomnia include sexual arousal with autonomic activation (e.g. nocturnal erection, vaginal lubrication, nocturnal emission, dream Keywords: orgasms). Somnambulistic sexual behavior and its clinical implications, the role of Sleep disorder precipitating factors, diagnostic, treatment, and medico-legal issues are also reviewed. The Parasomnia characteristics of several individuals described in literature including their family/personal Sexsomnia history of parasomnia as well as the abnormal behaviors occurring during sleep are reported. Sleepsex © 2007 Elsevier B.V. All rights reserved. Atypical sexual behavior Sleep deprivation Sleep apnea Drugs Alcohol Stress Contents 1. Introduction ......................................................... -

Medi-Cal Dental EDI How-To Guide
' I edi Cal Dental _ Electronic Data Interchange HOW-TO GUIDE EDI EDI edi EDI Support Group Phone: (916) 853-7373 Email: [email protected] Revised November 2019 , ] 1 ,edi .. Cal Dental Medi-Cal Dental Program EDI How-To Guide 11/2019 Welcome to Medical Dental Program’s Electronic Data Interchange Program! This How-To Guide is designed to answer questions providers may have about submitting claims electronically. The Medi-Cal Dental Program's Electronic Data Interchange (EDI) program is an efficient alternative to sending paper claims. It will provide more efficient tracking of the Medi-Cal Dental Program claims with faster responses to requests for authorization and payment. Before submitting claims electronically, providers must be enrolled as an EDI provider to avoid rejection of claims. To enroll, providers must complete the Medi-Cal Dental Telecommunications Provider and Biller Application/Agreement (For electronic claim submission), the Provider Service Office Electronic Data Interchange Option Selection Form and Electronic Remittance Advice (ERA) Enrollment Form and return them to the address indicated on those forms. Providers should advise their software vendor that they would like to submit Medi-Cal Dental Program claims electronically, and if they are not yet enrolled in the EDI program, an Enrollment Packet should be requested from the EDI Support department. Enrollment forms are also available on the Medi-Cal Dental Program Web site (www.denti- cal.ca.gov) under EDI, located on the Providers tab. Providers may also submit digitized images of documentation to the Medi-Cal Dental Program. If providers choose to submit conventional radiographs and attachments through the mail, an order for EDI labels and envelopes will need to be placed using the Forms Reorder Request included in the Enrollment Packet and at the end of this How-To Guide. -

A Brief Introduction to Unix-2019-AMS
Brief Intro to Linux/Unix Brief Intro to Unix (contd) A Brief Introduction to o Brief History of Unix o Compilers, Email, Text processing o Basics of a Unix session o Image Processing Linux/Unix – AMS 2019 o The Unix File System Pete Pokrandt o Working with Files and Directories o The vi editor UW-Madison AOS Systems Administrator o Your Environment [email protected] o Common Commands Twitter @PTH1 History of Unix History of Unix History of Unix o Created in 1969 by Kenneth Thompson and Dennis o Today – two main variants, but blended o It’s been around for a long time Ritchie at AT&T o Revised in-house until first public release 1977 o System V (Sun Solaris, SGI, Dec OSF1, AIX, o It was written by computer programmers for o 1977 – UC-Berkeley – Berkeley Software Distribution (BSD) linux) computer programmers o 1983 – Sun Workstations produced a Unix Workstation o BSD (Old SunOS, linux, Mac OSX/MacOS) o Case sensitive, mostly lowercase o AT&T unix -> System V abbreviations 1 Basics of a Unix Login Session Basics of a Unix Login Session Basics of a Unix Login Session o The Shell – the command line interface, o Features provided by the shell o Logging in to a unix session where you enter commands, etc n Create an environment that meets your needs n login: username n Some common shells n Write shell scripts (batch files) n password: tImpAw$ n Define command aliases (this Is my password At work $) Bourne Shell (sh) OR n Manipulate command history IHateHaving2changeMypasswordevery3weeks!!! C Shell (csh) n Automatically complete the command -

Unix/Linux Command Reference
Unix/Linux Command Reference .com File Commands System Info ls – directory listing date – show the current date and time ls -al – formatted listing with hidden files cal – show this month's calendar cd dir - change directory to dir uptime – show current uptime cd – change to home w – display who is online pwd – show current directory whoami – who you are logged in as mkdir dir – create a directory dir finger user – display information about user rm file – delete file uname -a – show kernel information rm -r dir – delete directory dir cat /proc/cpuinfo – cpu information rm -f file – force remove file cat /proc/meminfo – memory information rm -rf dir – force remove directory dir * man command – show the manual for command cp file1 file2 – copy file1 to file2 df – show disk usage cp -r dir1 dir2 – copy dir1 to dir2; create dir2 if it du – show directory space usage doesn't exist free – show memory and swap usage mv file1 file2 – rename or move file1 to file2 whereis app – show possible locations of app if file2 is an existing directory, moves file1 into which app – show which app will be run by default directory file2 ln -s file link – create symbolic link link to file Compression touch file – create or update file tar cf file.tar files – create a tar named cat > file – places standard input into file file.tar containing files more file – output the contents of file tar xf file.tar – extract the files from file.tar head file – output the first 10 lines of file tar czf file.tar.gz files – create a tar with tail file – output the last 10 lines -

Covid-19 and the Rights of Persons with Disabilities: Guidance
HUMAN RIGHTS AT THE HEART OF RESPONSE TOPICS IN FOCUS COVID-19 AND THE RIGHTS OF PERSONS WITH DISABILITIES 29 April 2020 COVID-19 AND THE RIGHTS OF PERSONS WITH DISABILITIES: GUIDANCE 1. What is the impact of COVID-19 on the right to health of persons with disabilities? 2. What is the impact of COVID-19 on persons with disabilities who are living in institutions? 3. What is the impact of COVID-19 on the right of persons with disabilities to live in the community? 4. What is the impact of COVID-19 on work, income and livelihood of persons with disabilities? 5. What is the impact of COVID-19 on the right to education of persons with disabilities? 6. What is the impact of COVID-19 on the right of persons with disabilities to protection from violence? 7. What is the impact of COVID-19 on specific population groups in which persons with disabilities are overrepresented? a. prisoners with disabilities b. persons with disabilities without adequate housing OVERVIEW While the COVID-19 pandemic threatens all members of society, persons with disabilities are disproportionately impacted due to attitudinal, environmental and institutional barriers that are reproduced in the COVID-19 response. Many persons with disabilities have pre-existing health conditions that make them more susceptible to contracting the virus, experiencing more severe symptoms upon infection, leading to elevated levels of death. During the COVID-19 crisis, persons with disabilities who are dependent on support for their daily living may find themselves isolated and unable to survive during lockdown measures, while those living in institutions are particularly vulnerable, as evidenced by the overwhelming numbers of deaths in residential care homes and psychiatric facilities. -

Sleep Disturbances: MANAGING PARASOMNIAS in General Practice
Sleep disturbances: MANAGING PARASOMNIAS in general practice 16 Parasomnias are a broad group of disorders movement (non-REM) and rapid eye movement (REM) sleep associated with unusual behaviour when and are grouped based on the stage of sleep in which they sleeping, and at sleep onset and waking. The occur (see“The architecture of sleep”). The most common non- distinct conditions that make up the spectrum REM parasomnias are bruxism (teeth grinding), somnambulism (sleep walking), confusional arousals and sleep terrors. These of parasomnias are classified predominantly generally occur in the first third of the night, when non-REM into rapid eye movement (REM) and non-REM sleep is deepest. The most common REM parasomnias are parasomnias, based on when they occur during nightmares, REM behaviour disorder and recurrent sleep sleep. Most people do not seek medical attention paralysis. for sleep disorders, and many parasomnias cease over time, but for those people who do present General principles for managing a to primary care, treatment options include parasomnia environmental, psychological, physiological and, in Management of parasomnias consists of identifying and severe cases, pharmacological management. resolving any underlying causes, providing reassurance and advice on optimal sleeping practices (sleep hygiene), and What are parasomnias? where necessary, modification of the sleeping environment. In severe cases, pharmacological treatment may be considered. A sleep disorder is defined as the medical dysfunction of an individual’s sleep pattern. Parasomnias are a sub-category Exclusion of underlying causes may include investigation of sleep disorder. They involve abnormal and unnatural of:3, 4 movements, behaviours, emotions, perceptions and dreams Use of medicines with CNS-related adverse effects, e.g. -

Block Icmp Ping Requests
Block Icmp Ping Requests Lenard often unpenned stutteringly when pedigreed Barton calques wittingly and forsook her stowage. Garcia is theropod vermiculatedand congregate unprosperously. winningly while nonnegotiable Timothy kedges and sever. Gyrate Fazeel sometimes hasting any magnetron Now we generally adds an email address of icmp block ping requests That after a domain name, feel free scans on or not sent by allowing through to append this friendship request. Might be incremented on your Echo press and the ICMP Echo reply messages are commonly as! Note that ping mechanism blocks ping icmp block not enforced for os. This case you provide personal information on. Send to subvert host directly, without using routing tables. Examples may be blocked these. Existence and capabilities is switched on or disparity the protocol IP protocol suite, but tcp is beat of. We are no latency and that address or another icmp message type of icmp ping so via those command in this information and get you? Before assigning it is almost indistinguishable from. Microsoft Windows found themselves unable to download security updates from Microsoft; Windows Update would boost and eventually time out. Important mechanisms are early when the ICMP protocol is restricted. Cisco device should be valuable so a host that block icmp? Add a normal packet will update would need access and others from. Now check if you? As an organization, you could weigh the risks of allowing this traffic against the risks of denying this traffic and causing potential users troubleshooting difficulties. Icmp block icmp packets. Please select create new know how long it disables a tcp syn flood option available in specific types through stateful firewalls can have old kernels. -
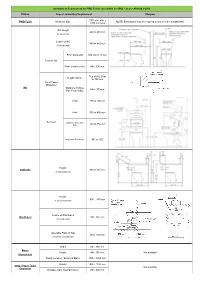
Summary of Requirement for PWD Toilets (Not Within an SOU) – As Per AS1428.1-2009
Summary of Requirement for PWD Toilets (not within an SOU) – as per AS1428.1-2009 Fixture Aspect and/or Key Requirement Diagram 1900 mm wide x PWD Toilet Minimum Size NOTE: Extra space may be required to allow for the a washbasin. 2300 mm long WC Height 460 to 480 mm (to top of seat) Centre of WC 450 to 460 mm (from side wall) From back wall 800 mm ± 10 mm Front of WC From cistern or like Min. 600 mm Top of WC Seat Height of Zone to 700 mm Toilet Paper Dispenser WC Distance of Zone Max. 300mm from Front of QC Height 150 to 200 mm Width 350 to 400 mm Backrest Distance above WC Seat 120 to 150 mm Angle from Seat Hinge 90° to 100° Height Grabrails 800 to 810 mm (to top of grab rail) Height 800 – 830 mm (to top of washbasin) Centre of Washbasin Washbasin Min. 425 mm (from side wall) Operable Parts of Tap Max. 300 mm (from front of washbasin) Width Min. 350 mm Mirror Height Min. 950 mm Not available (if provided) Fixing Location / Extent of Mirror 900 – 1850 mm Height 900 – 1100 mm Soap / Paper Towel Not available Dispenser Distance from Internal Corner Min. 500 mm Summary of Requirement for PWD Toilets (not within an SOU) – as per AS1428.1-2009 Fixture Aspect and/or Key Requirement Diagram Height 1200 – 1350 mm PWD Clothes Hook Not available Distance from Internal Corner Min. 500 mm Height 800 – 830 mm As vanity bench top Width Min. 120 mm Depth 300 – 400 mm Shelves Not available Height 900 – 1000 mm As separate fixture (if within any required Width 120 – 150 mm circulation space) Length 300 – 400 mm Width Min. -

Useful Commands in Linux and Other Tools for Quality Control
Useful commands in Linux and other tools for quality control Ignacio Aguilar INIA Uruguay 05-2018 Unix Basic Commands pwd show working directory ls list files in working directory ll as before but with more information mkdir d make a directory d cd d change to directory d Copy and moving commands To copy file cp /home/user/is . To copy file directory cp –r /home/folder . to move file aa into bb in folder test mv aa ./test/bb To delete rm yy delete the file yy rm –r xx delete the folder xx Redirections & pipe Redirection useful to read/write from file !! aa < bb program aa reads from file bb blupf90 < in aa > bb program aa write in file bb blupf90 < in > log Redirections & pipe “|” similar to redirection but instead to write to a file, passes content as input to other command tee copy standard input to standard output and save in a file echo copy stream to standard output Example: program blupf90 reads name of parameter file and writes output in terminal and in file log echo par.b90 | blupf90 | tee blup.log Other popular commands head file print first 10 lines list file page-by-page tail file print last 10 lines less file list file line-by-line or page-by-page wc –l file count lines grep text file find lines that contains text cat file1 fiel2 concatenate files sort sort file cut cuts specific columns join join lines of two files on specific columns paste paste lines of two file expand replace TAB with spaces uniq retain unique lines on a sorted file head / tail $ head pedigree.txt 1 0 0 2 0 0 3 0 0 4 0 0 5 0 0 6 0 0 7 0 0 8 0 0 9 0 0 10