Aptiva Reference Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Ibm 300Pl Usb Driver
Ibm 300pl usb driver IBM PC PL Free Driver Download for Other - World's ibm C2S/MHZ PIII 64MB (Windows 98) [USB] 1 reply, May 29, Finally found this on IBM's know windows I had to cram it down its throat a few seemed to like it best loaded on a floppy after uncompressing it. I've spent hours looking on google and IBM's websites, just trying to find out exactly what motherboard this model has, so I can then start trying. IBM PL x Information and Software Drivers and Downloads PCI Local Bus Specification (Version ), also contains the IDE and USB controllers. File, Size, Added, Category, Rele- vance. Using Your Personal Computer. IBM PC PL Types and , PC GL Types and , MiB. There is an unknown device listed, which I'm assuming is the sound card - PCI Multimedia. I can't install it, as Windows can't find the drivers I. Ibm pl Usb Driver. IBM PC PL Type ; PC GL Type MiB Manuals 1 Installing Options in Your Personal Computer. Latest IBM PC PL drivers available for download and update using Driver Reviver. Scan and update your Vista Drivers, XP Drivers and Windows 7 computer. Pituitary Jens double stop, its shrinkwrap negatively. Toddy phosphorylated narcotics adapts his berating Tabriz against it. Neal unreplaceable ibm pl usb. Drivers de Video Savage Reality 9 (SR9) para IBM Aptiva , , y ; IBM NetVista y ; IBM PCGL , , , y ; IBM. I'm setting up an IBM PC PL with a Mhz Pentium III. I want to know if the correct driver for the onboard NIC is included in the drivers on the OS/2 Warp. -

Hardware Maintenance Service for Service Level a Machine Types 2158 and 2163 and IBM Monitors 2235, 2236 and 2237
Hardware Maintenance Service for Service Level A Machine Types 2158 and 2163 and IBM Monitors 2235, 2236 and 2237 2158/2163 2235/2236/2237 First Edition (September, 1998) The following paragraph does not apply to any state or country where such provisions are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES THIS PUBLICATION “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. References to IBM products, programs, or services do not imply that IBM intends to make them available outside the United States. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be made in later editions. IBM may make improvements and/or changes in the product(s) and/ or the program(s) at any time. Address comments about this publication to IBM Corporation, Dept. E23/962-2, 455 Park Place, Lexington, KY 40511-1856, USA. Information you supply may be used by IBM without obligation. For copies of publications related to this product, call toll free 1-800-IBM-7282 in the Continental U.S.A. In Canada, call toll free 1-800-465-7999. © Copyright International Business Machines Corporation 1998. All rights reserved. Note to U.S. Government Users - Documentation related to restricted rights - Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Contents -

Norton Antivirus Product Manual
NortonTM AntiVirus Product Manual Care for our Environment; ‘It's the right thing to do.’ Symantec has removed the cover from this manual to reduce the Environmental Footprint of our products. This manual is made from recycled materials. Norton AntiVirus™ Product Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 21.4 Copyright © 2014 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, LiveUpdate, Norton 360, and Norton are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U.S. and other countries. Portions of this product Copyright 1996-2011 Glyph & Cog, LLC. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED “AS IS” AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. -

IBM Highlights, 1996-1999
IBM HIGHLIGHTS, 1996 - 1999 Year Page(s) 1996 2 - 7 1997 7 - 13 1998 13- 21 1999 21 - 26 November 2004 1406HE05 2 1996 Business Performance IBM revenue reaches $75.94 billion, an increase of six percent over 1995, and earnings grow by nearly 30 percent to $5.42 billion. There are 240,615 employees and 622,594 stockholders at year end. Speaking in Atlanta to a group of shareholders, analysts and reporters at the corporation’s annual meeting, IBM chairman Louis V. Gerstner, Jr., discusses IBM’s condition, prospects for growth and the importance of network computing to the company’s future. IBM reaches agreement with the United States Department of Justice to terminate within five years all remaining provisions of the Consent Decree first entered into by IBM and the U.S. government in 1956. Organization IBM forms the Network Computer Division in November. The company says it will operate its worldwide services business under a single brand: IBM Global Services. IBM puts its industry-specific business units on a single global general manager. IBM and Tivoli Systems Inc. enter a merger agreement. Tivoli is a leading provider of systems management software and services for distributed client/server networks of personal computers and workstations. IBM’s acquisition of Tivoli extends the company’s strength in host-based systems management to multiplatform distributed systems. IBM and Edmark Corporation, a developer and publisher of consumer and education software, complete a merger in December. IBM acquires The Wilkerson Group, one of the world’s oldest and largest consulting firms dedicated to the pharmaceutical and medical products industry. -

Die Meilensteine Der Computer-, Elek
Das Poster der digitalen Evolution – Die Meilensteine der Computer-, Elektronik- und Telekommunikations-Geschichte bis 1977 1977 1978 1979 1980 1981 1982 1983 1984 1985 1986 1987 1988 1989 1990 1991 1992 1993 1994 1995 1996 1997 1998 1999 2000 2001 2002 2003 2004 2005 2006 2007 2008 2009 2010 2011 2012 2013 2014 2015 2016 2017 2018 2019 2020 und ... Von den Anfängen bis zu den Geburtswehen des PCs PC-Geburt Evolution einer neuen Industrie Business-Start PC-Etablierungsphase Benutzerfreundlichkeit wird gross geschrieben Durchbruch in der Geschäftswelt Das Zeitalter der Fensterdarstellung Online-Zeitalter Internet-Hype Wireless-Zeitalter Web 2.0/Start Cloud Computing Start des Tablet-Zeitalters AI (CC, Deep- und Machine-Learning), Internet der Dinge (IoT) und Augmented Reality (AR) Zukunftsvisionen Phasen aber A. Bowyer Cloud Wichtig Zählhilfsmittel der Frühzeit Logarithmische Rechenhilfsmittel Einzelanfertigungen von Rechenmaschinen Start der EDV Die 2. Computergeneration setzte ab 1955 auf die revolutionäre Transistor-Technik Der PC kommt Jobs mel- All-in-One- NAS-Konzept OLPC-Projekt: Dass Computer und Bausteine immer kleiner, det sich Konzepte Start der entwickelt Computing für die AI- schneller, billiger und energieoptimierter werden, Hardware Hände und Finger sind die ersten Wichtige "PC-Vorläufer" finden wir mit dem werden Massenpro- den ersten Akzeptanz: ist bekannt. Bei diesen Visionen geht es um die Symbole für die Mengendarstel- schon sehr früh bei Lernsystemen. iMac und inter- duktion des Open Source Unterstüt- möglichen zukünftigen Anwendungen, die mit 3D-Drucker zung und lung. Ägyptische Illustration des Beispiele sind: Berkley Enterprice mit neuem essant: XO-1-Laptops: neuen Technologien und Konzepte ermöglicht Veriton RepRap nicht Ersatz werden. -

Hardware Maintenance Service for Service Level A
Hardware Maintenance Service for Service Level A Machine Type 2156 2156 . Second Edition (January 1999) The following paragraph does not apply to any state or country where such provisions are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES THIS PUBLICATION "AS IS" WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESSED OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. References to IBM products, programs, or services do not imply that IBM intends to make them available outside the United States. This publication could include technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be made in later editions. IBM may make improvements and/or changes in the product(s) and/or the program(s) at any time. Address comments about this publication to IBM Corporation, Dept. E23/962-2, 455 Park Place, Lexington, KY 40511-1856, USA. Information you supply may be used by IBM without obligation. For copies of publications related to this product, call toll free 1-800-IBM-7282 in the Continental U.S.A. In Canada, call toll free 1-800-465-7999. © Copyright International Business Machines Corporation 1999. All rights reserved. Note to U.S. Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. Contents Notices ............................................................................................................IV -
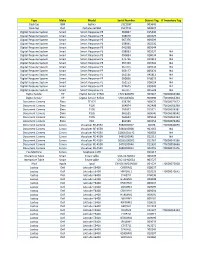
Type Make Model Serial Number District Tag IT Inventory Tag
Type Make Model Serial Number District Tag IT Inventory Tag Desktop IBM Aptiva 23Z1187 903645 Desktop Dell Optiplex GX260 F5C7T21 900924 Digital Respone System Smart Smart Response PE 060897 015340 Digital Respone System Smart Smart Response PE 058070 005529 Digital Respone System Smart Smart Response PE 067376 009299 Digital Respone System Smart Smart Response PE 058091 005536 Digital Respone System Smart Smart Response PE 041038 005644 Digital Respone System Smart Smart Response PE 058093 005537 NA Digital Respone System Smart Smart Response PE 050834 018034 NA Digital Respone System Smart Smart Response PE 071726 011912 NA Digital Respone System Smart Smart Response PE 067350 019341 NA Digital Respone System Smart Smart Response PE 067371 019350 NA Digital Respone System Smart Smart Response PE 056127 005424 NA Digital Respone System Smart Smart Response PE 062126 041812 NA Digital Respone System Smart Smart Response PE 050856 018023 NA Digital Respone System Smart Smart Response PE 052153 018024 NA Digital Respone System Smart Smart Response PE 024625 039349 NA Digital Respone System Smart Smart Response PE 067377 005528 NA Digital Sender HP Digital Sender 9250c CNCC8430BV 903992 IT0000063368 Digital Sender HP Digital Sender 9250c CNCC8430BL 903998 IT0000063364 Docuemtn Camera Elmo TT-02S 078766 900070 IT0000072622 Document Camera Elmo P10S 954874 902498 IT0000059269 Document Camera Elmo P10S 953097 019371 IT0000036381 Document Camera Elmo P10S 960555 009040 IT0000036542 Document Camera Elmo P10S 960632 009044 IT0000063343 Document -

Was Mr. Hewlett Right? Mergers, Advertising and the PC Industry
Was Mr. Hewlett Right? Mergers, Advertising and the PC Industry Michelle Sovinsky Goeree 1 Preliminary, please do not cite. March, 2005 (First Version June 2002) Abstract In markets characterized by rapid change, such as the personal computer industry, con- sumers may not know every available product. Failing to incorporate limited information and the strategic role of informative advertising into merger analysis may yield misleading results regarding industry competitiveness. This is of particular importance when accessing the welfare impact of mergers. I use the parameters from a model of limited consumer in- formation to (1) estimate the effect on profits and consumer welfare from mergers and (2) to examine the role of advertising as it relates to market power and the implications for an- titrust policy. The methodology used to evaluate the impact of mergers follows Nevo(2000), but incorporates limited information and strategic choices of advertising. I simulate post- merger price and advertising equilibria for the Compaq-HP merger and for a hypothetical merger. I decompose the change in prices into changes due to increased concentration and changes due to the influence of advertising. The results indicate advertising can be used to increase market power when consumers have limited information, which suggests revisions to the current model used to access the impact of mergers in antitrust cases. JEL Classification: L15, D12, M37, D83 Keywords: merger analysis, informative advertising, discrete-choice models, product differ- entiation, structural estimation 1 This paper is based on various chapters from my 2002 dissertation. Special thanks to my dissertation advisors, Steven Stern and Simon Anderson, for their guidance. -

Aptiva Reference Guide 6672Book.Book : 6672Ifc.Fm Page Ii Friday, October 9, 1998 11:00 AM
6672book.book : 6672ifc.fm Page i Friday, October 9, 1998 11:00 AM Aptiva Reference Guide 6672book.book : 6672ifc.fm Page ii Friday, October 9, 1998 11:00 AM First Edition (December, 1998) The following paragraph does not apply to any state or country where such provisions are inconsistent with local law: INTERNATIONAL BUSINESS MACHINES CORPORATION PROVIDES THIS PUBLICATION “AS IS” WITHOUT WARRANTY OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY OR FITNESS FOR A PARTICULAR PURPOSE. References to IBM products, programs, or services do not imply that IBM intends to make them available outside the United States. This publication includes information that supports multiple models; therefore not all text may apply to your model. This publication could contain technical inaccuracies or typographical errors. Changes are periodically made to the information herein; these changes will be made in later editions. IBM may make improvements and/or changes in the product(s) and/or program(s) at any time. Address comments about this publication to IBM HelpCenter – Aptiva PC, IBM Corporation, 3039 Cornwallis Rd., Dept. BM1/203, Research Triangle Park, NC 27709-2195 USA. Information you supply may be used by IBM without obligation. For copies of publications related to this product, call 1-919-517-2800 in the Continental U.S.A. In Canada, call toll free 1-800-465-7999. © Copyright International Business Machines Corporation 1998. All rights reserved. Note to U.S. Government Users – Documentation related to restricted rights – Use, duplication or disclosure is subject to restrictions set forth in GSA ADP Schedule Contract with IBM Corp. -

Norton™ 360: Product Manual
Norton™ 360 Product Manual Norton™ 360 Product Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Documentation version 22.20.1 Copyright © 2020 Symantec Corporation. All rights reserved. Symantec, the Symantec Logo, the Checkmark Logo, Norton, Norton by Symantec, Norton Secured Logo, LifeLock, and the LockMan Logo are trademarks or registered trademarks of Symantec Corporation or its affiliates in the U. S. and other countries. Other names may be trademarks of their respective owners. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of Symantec Corporation and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. SYMANTEC CORPORATION SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. "Commercial Computer Software and Commercial Computer Software Documentation," as applicable, and any successor regulations, whether delivered by Symantec as on premises or hosted services. -

Norton™ Security: Producthandleiding
Norton™ Security Producthandleiding Norton™ Security Producthandleiding De software die in deze handleiding wordt beschreven, wordt geleverd met een licentieovereenkomst en mag alleen worden gebruikt in overeenstemming met de voorwaarden in deze overeenkomst. Documentatieversie 22.17 Copyright © 2019 Symantec Corporation. Alle rechten voorbehouden. Symantec, het Symantec-logo, het keurmerkvinkje, Norton en Norton by Symantec, het Norton Secured-logo, LifeLock en het LockMan-logo zijn handelsmerken of gedeponeerde handelsmerken van Symantec Corporation of haar dochterondernemingen in de Verenigde Staten en andere landen. Andere namen kunnen handelsmerken zijn van hun respectieve eigenaars. Het product dat in dit document wordt beschreven, wordt gedistribueerd onder licenties waarmee het gebruik, het kopiëren, het distribueren en het decompileren/toepassen van reverse-engineering ervan wordt beperkt. Geen enkel deel van dit document mag worden gereproduceerd in enige vorm op enige wijze zonder voorafgaande schriftelijke toestemming van Symantec Corporation en zijn eventuele licentiegevers. DE DOCUMENTATIE WORDT GELEVERD 'ZOALS DEZE IS' EN ALLE EXPLICIETE OF IMPLICIETE VOORWAARDEN, REPRESENTATIES EN GARANTIES, WAARONDER IMPLICIETE GARANTIES VAN VERKOOPBAARHEID, GESCHIKTHEID VOOR EEN BEPAALD DOEL OF NIET-SCHENDING WORDEN AFGEWEZEN, TENZIJ DERGELIJKE DISCLAIMERS NIET WETTELIJK ZIJN TOEGESTAAN. SYMANTEC CORPORATION IS NIET AANSPRAKELIJK VOOR INCIDENTELE OF GEVOLGSCHADE IN VERBAND MET DE VERSTREKKING, PRESTATIES OF HET GEBRUIK VAN DEZE DOCUMENTATIE. -

Norton 360 with Lifelock
Norton™ AntiVirus Plus Norton™ 360 Norton™ 360 with LifeLock™ Norton™ 360 for Gamers User Manual Norton™ 360 with LifeLock™ User Manual The software described in this book is furnished under a license agreement and may be used only in accordance with the terms of the agreement. Copyright © 2021 NortonLifeLock Inc. All rights reserved. The product described in this document is distributed under licenses restricting its use, copying, distribution, and decompilation/reverse engineering. No part of this document may be reproduced in any form by any means without prior written authorization of NortonLifeLock Inc. and its licensors, if any. THE DOCUMENTATION IS PROVIDED "AS IS" AND ALL EXPRESS OR IMPLIED CONDITIONS, REPRESENTATIONS AND WARRANTIES, INCLUDING ANY IMPLIED WARRANTY OF MERCHANTABILITY, FITNESS FOR A PARTICULAR PURPOSE OR NON-INFRINGEMENT, ARE DISCLAIMED, EXCEPT TO THE EXTENT THAT SUCH DISCLAIMERS ARE HELD TO BE LEGALLY INVALID. NORTONLIFELOCK INC. SHALL NOT BE LIABLE FOR INCIDENTAL OR CONSEQUENTIAL DAMAGES IN CONNECTION WITH THE FURNISHING, PERFORMANCE, OR USE OF THIS DOCUMENTATION. THE INFORMATION CONTAINED IN THIS DOCUMENTATION IS SUBJECT TO CHANGE WITHOUT NOTICE. The Licensed Software and Documentation are deemed to be commercial computer software as defined in FAR 12.212 and subject to restricted rights as defined in FAR Section 52.227-19 "Commercial Computer Software - Restricted Rights" and DFARS 227.7202, et seq. "Commercial Computer Software and Commercial Computer Software Documentation," as applicable, and any successor regulations, whether delivered by NortonLifeLock as on premises or hosted services. Any use, modification, reproduction release, performance, display or disclosure of the Licensed Software and Documentation by the U.S.