China's Technology Protectionism and Its Non-Negotiable Rationales
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

United States Securities and Exchange Commission Washington, D.C
UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 Amendment No. 1 to FORM 20-F/A (Mark One) [_] REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR (g) OF THE SECURITIES EXCHANGE ACT OF 1934 OR [X] ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2002 OR [_] TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from ________to _________. Commission file number: 333-11724 NETEASE.COM, INC. ------------------------------------------------------------------ (Exact name of Registrant as specified in its charter) N/A ------------------------------------------------------------------ (Translation of Registrant's name into English) Cayman Islands ------------------------------------------------------------------ (Jurisdiction of incorporation or organization) Suite 1901, Tower E3 The Towers, Oriental Plaza, Dong Cheng District Beijing 100738, People's Republic of China ------------------------------------------------------------------ (Address of principal executive offices) Securities registered or to be registered pursuant to Section 12(b) of the Act. NONE ------------------------------------------------------------------ Securities registered or to be registered pursuant to Section 12(g) of the Act. Name of each exchange and Title of each class on which registered: American Depositary Shares, each representing 100 ordinary shares, par value US$0.0001 per share, Nasdaq National Market -

The9-2013-20F.Pdf
UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 FORM 20-F (Mark One) REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR 12(g) OF THE SECURITIES EXCHANGE ACT OF 1934 OR ⌧ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2013 OR TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to OR SHELL COMPANY REPORT PURSUANT TO SECTION 13 OR 15(D) OF THE SECURITIES EXCHANGE ACT OF 1934 Date of event requiring this shell company report Commission file number: 001-34238 THE9 LIMITED (Exact name of Registrant as specified in its charter) N/A (Translation of Registrant’s name into English) Cayman Islands (Jurisdiction of incorporation or organization) Building No. 3, 690 Bibo Road Zhang Jiang Hi-Tech Park Pudong New Area, Pudong Shanghai 201203 People’s Republic of China (Address of principal executive offices) George Lai, Chief Financial Officer Tel: +86-21-5172-9999 Facsimile number: +86-21-5172-9903 Building No. 3, 690 Bibo Road Zhang Jiang Hi-Tech Park Pudong New Area, Pudong Shanghai 201203 People’s Republic of China (Name, Telephone, E-mail and/or Facsimile number and Address of Company Contact Person) Securities registered or to be registered pursuant to Section 12(b) of the Act: Title of each class Name of each exchange on which registered American Depositary Shares, each representing Nasdaq Global Market one ordinary shares, par value $0.01 per share Securities registered or to be registered pursuant to Section 12(g) of the Act: None (Title of Class) Securities for which there is a reporting obligation pursuant to Section 15(d) of the Act: None (Title of Class) Indicate the number of outstanding shares of each of the issuer’s classes of capital or common stock as of the close of the period covered by the annual report. -

Dacast Ebook China
Video Hosting in China Online video is a massive and rapidly growing industry. Video streaming rose https://bit.ly/2I21JRl72.4% between Q1 2018 and Q1 2019 alone. The video streaming market is predicted to be worth $70.5https://bit.ly/2Mjm6hp billion by 2021. And https://bit.ly/2OF1aUayoung https://bit.ly/2OF1aUapeople are driving that growth—a sure sign that this trend will continue. Over the past decade, the number of people accessing the Internet in China has increased five-fold. However, it remains quite difficult for companies to deliver video in China. There are political and technical reasons for this challenge. But current barriers to China video delivery can also be overcome. This eBook will explore the topic of https://bit.ly/2YLq98dvideo https://www.dacast.com/video-hosting-china/hosting in China. We’ll start by examining the business-case for China video streaming. Next, we’ll dive into the challenges and problems that face businesses that choose to deliver video in China. Finally, we’ll present solutions and arrange of options to gain access to the China market. The Opportunity: Why You Video viewing growth in China is similarly stunning, with an estimated 37%https://bit.ly/2yEfeTd annual Should Be Delivering Videos https://www.dacast.com/webinars/everything-you-need-to-know-about-delivering-video-into-china/growth in the number of viewers. In 2007, a mere https://www.statista.com/statistics/279537/number-of-online-video-users-in-china/160 million Chinese had watched in China https://bit.ly/33dJORyvideos online. By 2014, this figure had tripled No matter what your industry, there may be to 433 million viewers. -

Skillful Craftsman Education Technology Ltd Form 20-F Filed
SECURITIES AND EXCHANGE COMMISSION FORM 20-F Annual and transition report of foreign private issuers pursuant to sections 13 or 15(d) Filing Date: 2021-07-20 | Period of Report: 2021-03-31 SEC Accession No. 0001104659-21-093937 (HTML Version on secdatabase.com) FILER Skillful Craftsman Education Technology Ltd Mailing Address Business Address FLOOR 4 BLDG 1 NO. 311 FLOOR 4 BLDG 1 NO. 311 CIK:1782309| IRS No.: 000000000 | State of Incorp.:E9 | Fiscal Year End: 0331 YANXIN RD YANXIN RD Type: 20-F | Act: 34 | File No.: 001-39360 | Film No.: 211101060 HUISHAN QU, WUXI SHI F4 HUISHAN QU, WUXI SHI F4 SIC: 8200 Educational services 214406 214406 13395136886 Copyright © 2021 www.secdatabase.com. All Rights Reserved. Please Consider the Environment Before Printing This Document UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 FORM 20-F REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR (g) OF THE SECURITIES EXCHANGE ACT ¨ OF 1934 OR ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 x For the fiscal year ended March 31, 2021 OR TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 ¨ For the transition period from _________ to _____________. OR SHELL COMPANY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF ¨ 1934 Date of event requiring this shell company report: Commission file number: 001-39360 Skillful Craftsman Education Technology Limited (Exact name of Registrant as Specified in its Charter) Cayman Islands (Jurisdiction of Incorporation or Organization) Floor 4, Building 1, No. -

Red Cloud Rising: Cloud Computing in China (Revised)
Red Cloud Rising: Cloud Computing in China by Leigh Ann Ragland, Joseph McReynolds, Matthew Southerland, and James Mulvenon Research Report Prepared on Behalf of the U.S.-China Economic and Security Review Commission September 5, 2013 Revised March 22, 2014 After the publication of this report on September 5, 2013, Microsoft brought to the authors’ attention new information about its partnership with Chinese company 21Vianet. The original version of the report inaccurately characterized certain aspects of the Microsoft-21Vianet partnership. A revised discussion of this partnership is provided on pages 32-34. The authors would like to thank Microsoft for their assistance in clarifying the details of 21Vianet’s Windows Azure service. Disclaimer: This research report was prepared at the request of the Commission to support its deliberations. Posting of the Report to the Commission's website is intended to promote greater public understanding of the issues addressed by the Commission in its ongoing assessment of U.S.-China economic relations and their implications for U.S. security, as mandated by Public Law 106-398 and Public Law 108-7. However, it does not necessarily imply an endorsement by the Commission or any individual Commissioner of the views or conclusions expressed in this commissioned research report. i About Defense Group Incorporated Defense Group Inc. (DGI) performs work in the national interest, advancing public safety and national security through innovative research, analysis and applied technology. The DGI enterprise conducts research and analysis in defense and intelligence problem areas, provides high-level systems engineering services to selected national and homeland security organizations, and produces hardware and software products for government and commercial consumers. -

The ICT Landscape in the PRC Market Trends and Investment Opportunities
33188 Public Disclosure Authorized The ICT Landscape in the PRC Market Trends and Investment Opportunities Public Disclosure Authorized FINAL REPORT Public Disclosure Authorized MARCH 2005 Public Disclosure Authorized Preface Information and Communications Technologies (ICT) are increasingly an important tool for supporting sustainable development and economic growth in developing markets. By embracing communications at unprecedented rates, people around the world have demonstrated their appreciation for the contribution of ICT to the betterment of their lives. It took 113 years from its invention for the fixed telephone to reach ten percent global penetration. It took 15 years from its invention for the mobile telephone to reach the same penetration, and ten percent of the World’s population are now Internet users less than twelve years after the birth of the World Wide Web. China’s growth story, for ICT companies specifically, has been astonishing. China, often referred to as the “factory of the world” has traditionally had a strong manufacturing base, including a core focus on the electronics industry. In addition, in the past 10 years, we have seen an explosion of the mobile phone population to over 300 million subscribers, larger than any other country in the world. Further, the country’s total number of Internet users has surpassed 90 million subscribers. Historically, sectors such as electronics manufacturing and mobile communications applications have enjoyed the benefit of growth, while we can already see new nascent sectors come up including media driven business, broadband applications and cutting-edge IC design houses. While much of the growth in the ICT sector has been funded by foreign investments, mainly through the private and public equity markets, it is anticipated that many sectors require substantial and ongoing funding. -

Prospectus, You Should Obtain Independent Professional Advice
Yankee_PPTUS Cover_Eng_OP2400.pdf 1 2018/6/25 下午 11:58:25 C M Y CM MY CY CMY K IMPORTANT If you are in any doubt about any of the contents of this prospectus, you should obtain independent professional advice. Inke Limited 映客互娛有限公司 (Incorporated in the Cayman Islands with limited liability) GLOBAL OFFERING Number of Offer Shares under the Global Offering : 302,340,000 Shares (subject to the Over-allotment Option) Number of Hong Kong Offer Shares : 30,234,000 Shares (subject to adjustment) Number of International Offer Shares : 272,106,000 Shares (subject to adjustment and the Over-allotment Option) Maximum Offer Price : HK$5.00 per Offer Share, plus brokerage of 1.0%, SFC transaction levy of 0.0027% and Stock Exchange trading fee of 0.005% (payable in full on application in Hong Kong dollars and subject to refund) If the Offer Price is set at 10% below the bottom end of the indicative Offer Price range after making a Downward Offer Price Adjustment, the Offer Price will be HK$3.47 per Hong Kong Offer Share. Nominal value : US$0.001 per Share Stock code : 3700 Joint Sponsors (in alphabetical order) Joint Global Coordinators, Joint Bookrunners and Joint Lead Managers Joint Bookrunners and Joint Lead Managers Joint Lead Manager Hong Kong Exchanges and Clearing Limited, The Stock Exchange of Hong Kong Limited and Hong Kong Securities Clearing Company Limited take no responsibility for the contents of this prospectus, make no representation as to its accuracy or completeness and expressly disclaim any liability whatsoever for any loss howsoever arising from or in reliance upon the whole or any part of the contents of this prospectus. -
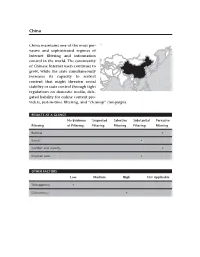
China Maintains One of the Most Per- Vasive and Sophisticated Regimes of Internet fi Ltering and Information Control in the World
China China maintains one of the most per- vasive and sophisticated regimes of Internet fi ltering and information control in the world. The community of Chinese Internet users continues to grow, while the state simultaneously increases its capacity to restrict content that might threaten social stability or state control through tight regulations on domestic media, dele- gated liability for online content pro- viders, just-in-time fi ltering, and “ cleanup ” campaigns. RESULTS AT A GLANCE No Evidence Suspected Selective Substantial Pervasive Filtering of Filtering Filtering Filtering Filtering Filtering Political • Social • Confl ict and security • Internet tools • OTHER FACTORS Low Medium High Not Applicable Transparency • Consistency • 272 China KEY INDICATORS GDP per capita, PPP (constant 2005 international dollars) 6,200 Life expectancy at birth, total (years) 73 Literacy rate, adult total (percent of people age 15+) 93.7 Human Ddevelopment Index (out of 169) 89 Rule of Law (out of 5) 2.2 Voice and Accountability (out of 5) 0.8 Democracy Index (out of 167) 136 (Authoritarian regime) Digital Opportunity Index (out of 181) 77 Internet penetration rate (percentage of population) 28.9 Source by indicator : World Bank 2009, World Bank 2008a, World Bank 2008b, UNDP 2010, World Bank Worldwide Governance Indicators 2009, Economist Intelligence Unit 2010, ITU 2007, ITU 2009. See Introduction to the Country Profi les, pp. 222 – 223. Background The People ’ s Republic of China (PRC) is a one-party state ruled by the Chinese Com- munist Party (CCP). Since the opening of its economy under the leadership of Deng Xiaoping in the 1980s, the country has undergone drastic changes. -

Online Education and Edtech Opportunities in China a FOCUS on the K-12 SECTOR
Online education and edtech opportunities in China A FOCUS ON THE K-12 SECTOR September 2017 Based on Chinese education megatrends to meet demand for flexible and innovative learning, and in line with the Australian International Education 2025 (AIE2025) Roadmap goal to embrace borderless learning opportunities, Austrade commissioned Grok Global Services to prepare this China market report on online education (including edtech) in the K-12 sector. This report aims to provide an in-depth understanding of the K-12 online education landscape in China and to provide insight and advice to Australian practitioners intending to enter this market. CONTENTS Executive summary 1 Market overview: K-12 education in China 2 Scale of China’s online K-12 education market 3 Current competitive landscape 4 A brief history of China’s online K-12 education market 4 Online K-12 education products and services in China 6 Main features of online K-12 education products and services 9 Trends in summary 9 Case studies of major international players 10 Regulatory environment in China 14 Brief overview of relevant regulatory bodies 14 Sino-Foreign partnerships in K-12 education 14 Foreign investments in the Chinese online education sector 15 Internet censorship 16 Indication of future trends related to regulations 16 Market entry advice 17 Market entry considerations 17 Targeting and prioritisation for market entry 17 Target demographics and products 17 Target regions - Tier 1 and 2 cities vs. lower-tier locations 18 Market entry strategies and distribution channels 19 In-market partnership 21 Public vs private procurement 21 Due diligence for business partner development in China 22 Recommended marketing channels for product promotion and distribution 23 Conclusion 24 Endnotes 25 Executive summary Online education has become a burgeoning industry in China, in part due to excitement over Massive Open Online Course (MOOC) platforms like Coursera and edX. -

Report on BEREC International Mission to China
BoR (19) 176 Report on BEREC International Mission to China 03 October, 2019 BoR (19) 176 Contents 1. Introduction and acknowledgements ......................................................................................... 3 2. General information about China ................................................................................................ 5 2.1. Provinces .............................................................................................................................................. 5 2.2. Beijing ................................................................................................................................................... 6 2.3. Hong Kong ............................................................................................................................................ 6 2.4. Shenzhen .............................................................................................................................................. 6 3. China’s communications market ................................................................................................ 7 3.1. Telecommunications market China ....................................................................................................... 7 3.1.1. China Mobile Ltd. ....................................................................................................................................... 8 3.1.2. China Telecom Corp. Ltd. .......................................................................................................................... -

China CDN Readiness Checklist V1
China CDN China Internet Expert Readiness +1 213-239-8878 Checklist Overview When looking to successfully launch a service into China, it is important to keep in mind that China’s Internet is a unique network operating within the China Firewall. Internet in China is connected internally and to global carriers by Chinese Internet Service Providers (ISPs), and governed by the laws and regulations of the People’s Republic of China. China Telecom is the largest ISP both in China and around the world. Although no longer a monopoly, China Telecom is joined by relatively few major carriers, with China Unicom (formerly China NetCom) and China Mobile being the only two other major providers. While foreign companies dominate global Internet, China has a thriving local services market delivered to users from local data centers by the major ISPs. For foreign hosted services, all traffic must enter Mainland China through a limited number of international gateways - all of which are filtered by network equipment commonly referred to as “China’s Great Firewall” or “The GFW”. As IP addresses are often shared by service providers (especially in the case of cloud providers), the default mechanism used to filter content is to scan the domain names and URLs for banned keywords or pre-identified problematic companies/providers, and deny those addresses. As such, a significant part of preparing to enter into China is to consider how your operations will look. How are your domain names currently used? What content will they be delivering? How will the China government perceive the business you are operating within the country? This document aims to provide a high level checklist for working through and integrating a China CDN into your service delivery plans. -
NETEASE.COM, INC. (Exact Name of Registrant As Specified in Its Charter)
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 FORM 20-F (Mark One) ☐ REGISTRATION STATEMENT PURSUANT TO SECTION 12(b) OR 12(g) OF THE SECURITIES EXCHANGE ACT OF 1934 OR ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2005 OR ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to . OR ☐ SHELL COMPANY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 Commission file number: 000-30666 NETEASE.COM, INC. (Exact name of Registrant as specified in its charter) N/A (Translation of Registrant’s name into English) Cayman Islands (Jurisdiction of incorporation or organization) 26/F, SP Tower D Tsinghua Science Park Building 8 No. 1 Zhongguancun East Road, Haidian District Beijing 100084, People’s Republic of China (Address of principal executive offices) Securities registered or to be registered pursuant to Section 12(b) of the Act. NONE Securities registered or to be registered pursuant to Section 12(g) of the Act. Name of each exchange and Title of each class on which registered : American Depositary Shares, each representing 25 ordinary shares, par value US$0.0001 per share, Nasdaq National Market (Title of Class) Securities for which there is a reporting obligation pursuant to Section 15(d) of the Act. NONE (Title of Class) Indicate the number of outstanding shares of each of the issuer’s classes of capital or common stock as of the close of the period covered by the annual report: 3,263,526,525 ordinary shares, par value US$0.0001 per share.