A Competence Management System Towards Increased Corporate Success
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

2009-08-21 La Cholla Final Sealed Special Provisions.Pdf
Special Provisions 8/21/2009 PCDOT La Cholla Boulevard, Ruthrauff Road to River Road Project No. 4LCITR INDEX TO THE SPECIAL PROVISIONS: LA CHOLLA BOULEVARD, RUTHRAUFF ROAD TO RIVER ROAD GENERAL NOTES .........................................................................................................................1 SECTION 101 - ABBREVIATIONS AND TERMS ....................................................................10 SECTION 102 - BIDDING REQUIREMENTS AND CONDITIONS ........................................10 SECTION 103 - AWARD AND EXECUTION OF CONTRACT ...............................................10 SECTION 104 - SCOPE OF WORK.............................................................................................11 SECTION 105 - CONTROL OF WORK ......................................................................................12 SECTION 106 - CONTROL OF MATERIAL ..............................................................................12 SECTION 107 - LEGAL RELATIONS AND RESPONSIBILITY TO PUBLIC ........................12 SECTION 108 - PROSECUTION AND PROGRESS ..................................................................17 SECTION 109 - MEASUREMENT AND PAYMENT ................................................................20 SECTION 202 - REMOVAL OF STRUCTURES AND OBSTRUCTIONS ...............................24 ITEM 2020005 – REMOVAL OF EXISTING PILES ..................................................................25 SECTION 203 - EARTHWORK ...................................................................................................26 -

Presentation Slides
ColdBox Platform 4.0 AND BEYOND Who am I? ● ColdFusion Architect (12 years) ● Geek ● Android Lover ● Blogger (codersrevolution.com) ● ColdBox Platform Evangelist ● Musician ● Shade-Tree Mechanic ● Husband (11 years) ● Dad (3 beautiful girls) What we will cover? History of ColdBox What is ColdBox? Why ColdBox? Major ColdBox Parts Demos History & Facts Did not start as open source Designed and built for a high availability application in 2005 1st Conventions CFML Framework in 2006 30 releases -> 3.8.1 Active roadmap, collaboration & development High-profile company adoptions Community Large and Active Community Incredible download rates Mailing List & Forums growth Many hours of video training ForgeBox : *Box CFML Community! Share modules, plugins, interceptors, contentbox, etc Professional Open Source Company backing and funding Professional Training Courses Books Support & Mentoring Plans Architecture & Design Sessions Server Tuning & Optimizations Code Reviews & Sanity Checks Dancing lessons Why use a framework? Common Vocabulary Separation of Concerns Tested in multiple environments Performance-tuned Reduces ramp up time for new developers Do not reinvent the wheel Should address most infrastructure concerns Increases Maintainability, Scalability, and keeps your sanity! What is ColdBox? A place for root beer? “Address most infrastructure concerns of typical ColdFusion applications” How we build our apps? Usually start with a need for MVC Requirements are more than just MVC MVC is not enough What about? SES/URL Mappings RESTful Services -

Professional Asp.Net Mvc 3
ffirs.indd ii 7/4/2011 4:27:38 PM Download from Wow! eBook <www.wowebook.com> ffirs.indd i i INTRODUCTION . INTRODUCTION FOREWORD. 3 MVC ASP.NET PROFESSIONAL INDEX . INDEX CHAPTER 14 CHAPTER 13 CHAPTER 12 CHAPTER 11 CHAPTER 10 CHAPTER 9 CHAPTER 8 CHAPTER 7 CHAPTER 6 CHAPTER 5 CHAPTER 4 CHAPTER 3 CHAPTER 2 CHAPTER 1 Advanced Topics . 339 . Extending315 MVC . Unit Testing 291 . Dependency Injection 271 . .239NuGet . .211Routing AJAX. 179 ApplicationSecuring Your . 135 Data Annotations and Validation . 117 . 93 Forms and HTML Helpers Models. 69 Views . 39 . 23 Controllers Getting. .1 Started 389 xxiii xxv 7/4/2011 4:27:37 PM 4:27:37 PM ffirs.indd ii 7/4/2011 4:27:38 PM PROFESSIONAL ASP.NET MVC 3 Jon Galloway Phil Haack Brad Wilson K. Scott Allen ffirs.indd iii 7/4/2011 4:27:38 PM Professional ASP.NET MVC 3 Published by John Wiley & Sons, Inc. 10475 Crosspoint Boulevard Indianapolis, IN 46256 www.wiley.com Copyright © 2011 by John Wiley & Sons, Inc. Indianapolis, Indiana Published simultaneously in Canada ISBN: 978-1-118-07658-3 ISBN: 978-1-118-15535-6 (ebk) ISBN: 978-1-118-15537-0 (ebk) ISBN: 978-1-118-15536-3 (ebk) Manufactured in the United States of America 10 9 8 7 6 5 4 3 2 1 No part of this publication may be reproduced, stored in a retrieval system or transmitted in any form or by any means, electronic, mechanical, photocopying, recording, scanning or otherwise, except as permitted under Sections 107 or 108 of the 1976 United States Copyright Act, without either the prior written permission of the Publisher, or authorization through payment of the appropriate per-copy fee to the Copyright Clearance Center, 222 Rosewood Drive, Danvers, MA 01923, (978) 750-8400, fax (978) 646-8600. -

Pilvandmetöötluse Rakendused
TALLINNA TEHNIKAÜLIKOOL Infotehnoloogia teaduskond Arvutitehnika instituut IAG40LT Anett Kann 120903 PILVANDMETÖÖTLUSE RAKENDUSED Bakalaureusetöö Juhendaja: Vladimir Viies PhD Dotsent Tallinn 2015 Autorideklaratsioon Olen koostanud antud töö iseseisvalt. Kõik töö koostamisel kasutatud teiste autorite tööd, olulised seisukohad, kirjandusallikatest ja mujalt pärinevad andmed on viidatud. Käesolevat tööd ei ole varem esitatud kaitsmisele kusagil mujal. Autor: Anett Kann 24.05.2015 2 BAKALAUREUSETÖÖ ÜLESANNE Üliõpilane: Anett Kann Matrikkel: 120903 Lõputöö teema eesti keeles: Pilvandmetöötluse rakendused Lõputöö teema inglise keeles: Cloud computing applications Juhendaja (nimi, töökoht, teaduslik kraad, allkiri): Vladimir Viies Konsultandid: - Lahendatavad küsimused ning lähtetingimused: Anda ülevaade rakenduse koostamise vahenditest pilvandmetöötluses, lähtudes Eestist. Koostada juhis rakenduse loomiseks ja realiseerida sellest lähtuvalt vabalt valitud näidisrakendus. Eritingimused: - Nõuded vormistamisele: Vastavalt Arvutitehnika instituudis kehtivatele nõuetele Lõputöö estamise tähtaeg: 08.06.2015 Ülesande vastu võtnud: ________________________________kuupäev: 24.05.2015 (lõpetaja allkiri) 3 Annotatsioon Käesolev töö uurib pilvandmetöötluse mõistet Eesti näitel, tüüplahenduste raamistikke ning lihtsa avalikel teenustel põhineva rakenduse loomise ülesehitust ning protsessi, milles realiseeritakse päikesekalkulaator. Iseloodud projekt põhineb Google Maps API’l, mis võimaldab rakenduses kasutada hõlpsasti maailmakaarti ja OpenWeatherMap -
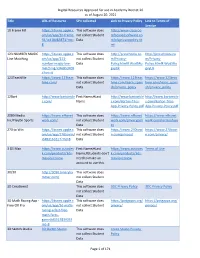
Digital Resources Approved for Use in Academy District 20 As Of
Digital Resources Approved for use in Academy District 20 as of August 20, 2021 Title URL of Resource SPII collected Link to Privacy Policy Link to Terms of Service 10 Frame Fill https://itunes.apple.c This software does http://www.classroo om/us/app/10-frame- not collect Student mfocusedsoftware.co fill/id418083871?mt= Data m/cfsprivacypolicy.ht 8 ml 123 NUMBER MAGIC https://itunes.apple.c This software does http://preschoolu.co http://preschoolu.co Line Matching om/us/app/123- not collect Student m/Privacy- m/Privacy- number-magic-line- Data Policy.html#.Wud5Ro Policy.html#.Wud5Ro matching/id46853409 gvyUk gvyUk 4?mt=8 123TeachMe https://www.123teac This software does https://www.123teac https://www.123teac hme.com/ not collect Student hme.com/learn_spani hme.com/learn_spani Data sh/privacy_policy sh/privacy_policy 12Bart http://www.bartontile First Name;#Last http://www.bartontile http://www.bartontile s.com/ Name s.com/Barton-Tiles- s.com/Barton-Tiles- App-Privacy-Policy.pdf App-Privacy-Policy.pdf 2080 Media https://www.nfhsnet This software does https://www.nfhsnet https://www.nfhsnet Inc/PlayOn Sports work.com/ not collect Student work.com/privacypoli work.com/termsofuse Data cy 270 to Win https://itunes.apple.c This software does https://www.270towi https://www.270towi om/us/app/270towin/ not collect Student n.com/privacy/ n.com/privacy/ id483161617?mt=8 Data 3 DS Max https://www.autodes First Name;#Last https://www.autodes Terms of Use k.com/products/3ds- Name;#Students don't k.com/products/3ds- max/overview need to make an max/overview account to use this. -

٢ SQL Server ﻣﺎﯾ ﺮوﺳﺎﻓﺖ ﺑﺎ ﻫﻤ ﺎری Sybase ﭘﺎﯾ ﺎه داده اﻧﺤﺼﺎری ﺧﻮد را اراﺋﻪ داده اﺳﺖ
داﻧﺸ ﺎه ﺷﻬﯿﺪ ﺑﻬﺸﺘ داﻧﺸ ﺪه ﻣﻬﻨﺪﺳ ﺑﺮق و ﮐﺎﻣﭙﯿﻮﺗﺮ ﭘﺮوژهی ﮐﺎرﺷﻨﺎﺳ ﻣﻬﻨﺪﺳ ﮐﺎﻣﭙﯿﻮﺗﺮ ﮔﺮاﯾﺶ ﻧﺮم اﻓﺰار ﻣﻮﺿﻮع ﭘﺮوژه: ﭼﻬﺎرﭼﻮب ﺗﻮﺳﻌﻪ وب اﻣﻦ اﺳﺘﺎد راﻫﻨﻤﺎ: ﺟﻨﺎب آﻗﺎی دﮐﺘﺮ ذاﮐﺮاﻟﺤﺴﯿﻨ ﮔﺮدآوردﻧﺪه: ﻋﺒﺎس ﻧﺎدری اﻓﻮﺷﺘﻪ [email protected] ﺑﻬﺎر ١٣٩١ ﭼ ﯿﺪه: وب ﺑﻪ ﻋﻨﻮان ﻣﻬﻤﺘﺮﯾﻦ ﺑﺴﺘﺮ اراﺋﻪ ﻧﺮماﻓﺰار و ﺳﺮوﯾﺲ، ﺗﺎ ﺟﺎﯾﯽ ﺟﻠﻮ رﻓﺘﻪ ﮐﻪ اﻣﺮوزه ﻣﺤﯿﻂﻫﺎی ﻪﻣﺎﻧﺮﺑﺳﺎزی و ﺣﺘ ﺳﯿﺴﺘﻢﻫﺎی ﻋﺎﻣﻞ ﺗﺤﺖ وب ﻗﺮار ﮔﺮﻓﺘﻪاﻧﺪ.وب ﯾ ﺑﺴﺘﺮ و ﭘﺮوﺗﮑﻞ ﺑﺴﯿﺎر ﺳﺎده اﺳﺖ ﮐﻪ ﺑﺎ اﻫﺪاف دﯾ ﺮی ﻃﺮاﺣ ﺷﺪه ﺑﻮده و ﺑﻪ ﺻﻮرت اﻧﻔﺠﺎری ﮔﺴﺘﺮش ﯾﺎﻓﺘﻪ اﺳﺖ، ﺑﻪ ﻫﻤﯿﻦ دﻟﯿﻞ ﺗﻮﻟﯿﺪ ﻧﺮم- اﻓﺰارﻫﺎی ﻣﺒﺘﻨ ﺑﺮ وب ﻧﯿﺎزﻣﻨﺪ ﭼﻬﺎرﭼﻮبﻫﺎی ﮔﺴﺘﺮده و ﻗﺪرﺗﻤﻨﺪی ﻫﺴﺘﻨﺪ. اﯾﻦ ﭼﻬﺎرﭼﻮبﻫﺎی ﻣﻌﻤﻮﻻ در اﻧﺠﻤﻦﻫﺎی ﻣﺘﻦﺑﺎز ﺷ ﻞ ﮔﺮﻓﺘﻪاﻧﺪ و ﻧﻘﺎط ﺿﻌﻒ اﻣﻨﯿﺘ دارﻧﺪ. در اﯾﻦ ﺳﻨﺪ ﭼﻬﺎرﭼﻮب ﺗﻮﺳﻌﻪ وب اﻣﻦ، ﺑﺎ اﺗﮑﺎ ﺑﻪ دو ﭼﻬﺎرﭼﻮب ﺗﻮﻟﯿﺪ ﺷﺪه ﺑﺎ ﺗﻮﺟﻪ ﺑﻪ اﻣﻨﯿﺖ وب ﻣﻄﺮح ﺷﺪهاﻧﺪ. اﺑﺘﺪا ﻣﻔﺎﻫﯿﻢ و ﺳﺎﺧﺘﺎر وب ﺑﻪ ﺗﻔﺼﯿﻞ ﺑﺤﺚ ﺷﺪه ﺗﺎ ﺧﻮاﻧﻨﺪه ﺑﺘﻮاﻧﺪ ﻧﯿﺎز و ﭘﺎﺳ را ﺑﻪ ﺧﻮﺑﯽ درک ﮐﻨﺪ. ﺳﭙﺲ ﻣﺨﺎﻃﺮات ﻣﻮﺟﻮد در اﻣﻨﯿﺖ وب ﻣﻄﺮح و ﺑﺮرﺳ ﺷﺪهاﻧﺪ و در ﺑﺨﺶ اﻧﺘﻬﺎﯾﯽ راﻫ ﺎرﻫﺎی ﻣﻘﺎﺑﻠﻪ ﺑﺎ اﯾﻦ ﻣﺨﺎﻃﺮات اراﺋﻪ ﺷﺪهاﻧﺪ. ﻣﻔﺎﻫﯿﻤ ﻣﺎﻧﻨﺪ ﻣﻌﻤﺎری وب، ﭘﺮوﺗﮑﻞﻫﺎی ﻣﺠﻮد در وب، ﺗﮑﻨﻮﻟﻮژیﻫﺎی ﻣﻮرد اﺳﺘﻔﺎده در وب، ﮐﺎوﺷ ﺮﻫﺎی وب، اﻣﻨﯿﺖ ﻋﻤﻮﻣ وب، اﻣﻨﯿﺖ ﻧﺮماﻓﺰار، MVC، ﭼﻬﺎرﭼﻮبﻫﺎی ﺗﻮﺳﻌﻪ وب و ﻧﯿﺎزﻣﻨﺪیﻫﺎی آﻧﺎن، ﻣﻌﻀﻼت ﻣﺨﺘﻠﻒ وب، ﺗﻌﺎرﯾﻒ اﻣﻨﯿﺖ اﻃﻼﻋﺎت، راﻫ ﺎرﻫﺎی ﺗﻔﺼﯿﻠ و ﻓﻨ ﻣﻘﺎﺑﻠﻪ ﺑﺎ ﻣﻌﻀﻼت اﻣﻨﯿﺘ و دﯾﺪﮔﺎه درﺳﺖ ﺑﻪ اﻣﻨﯿﺖ وب، ﺑﺮﺧ از ﻣﻄﺎﻟﺐ ﭘﻮﺷﺶ داده ﺷﺪه در اﯾﻦ ﺳﻨﺪ ﻣ ﺪﻨﺷﺎﺑ. ﮐﻠﻤﺎت ﮐﻠﯿﺪی: وب، اﻣﻨﯿﺖ، اﻣﻨﯿﺖ ﻧﺮماﻓﺰار، ﭼﻬﺎرﭼﻮب، ﻧﻔﻮذﮔﺮی، ﺗﻮﺳﻌﻪ ﻧﺮماﻓﺰار، ﻣﻬﻨﺪﺳ ﻧﺮماﻓﺰار ﺐﻟﺎﻄﻣ ﺖﺳﺮﻬﻓ 1 ﻪﻣﺪﻘﻣ .............................................................................١ 2 ﻓﺮﻌﻣ ......................................................................٣ 2.1 اﻣﻨﯿﺖ ﻧﺮم اﻓﺰار .............................................................. -

Coldbox Platform a Web Development Revolution
ColdBox Platform A Web Development Revolution What is ColdBox? Who Uses ColdBox? ColdBox is a conventions based ColdFusion development platform. It provides a set of reusable code and tools that can be used to increase your development productivity as well as a development standard for working in team environments. ColdBox is comprehensive and modular which helps address most infrastructure concerns of typical ColdFusion applications. Why ColdBox? n Conventions over configuration is our mantra n Developed with simplicity and extensibility in mind n ColdFusion ORM extensions and native Hibernate support classes to make querying and working with ORM objects a breeze n ColdBox Modules introduce modular architecture to your applications. No more hard to maintain monolithic applications n RESTFul architecture is at the core of every ColdBox application n ColdBox integration and unit testing support via TestBox n Fully documented, always find what you need n CLI and package management integration via CommandBox n An ever-growing community and professional support n Adobe ColdFusion Builder, Sublime and CFEclipse IDE integration. A Software with Experience ColdBox has been powering both small and enterprise level applications since 2005 and it is used by thousands of developers worldwide. We have a proven track record of stability, reliability and scalability. Used by clients like NASA JPL, NASA Kennedy Space Center, Adobe TV, IDG, eCivis, Equator Financial, FAA, US Air Force, State of Oregon, General Electric, ESRI and countless others. The ColdBox Platform has become the Object Oriented application framework of choice for premier ColdFusion developers around the world. ColdBox is Modular ColdBox is composed of an internal core library and 3 standalone frameworks that assemble themselves accordingly at runtime. -

Appendix a the Ten Commandments for Websites
Appendix A The Ten Commandments for Websites Welcome to the appendixes! At this stage in your learning, you should have all the basic skills you require to build a high-quality website with insightful consideration given to aspects such as accessibility, search engine optimization, usability, and all the other concepts that web designers and developers think about on a daily basis. Hopefully with all the different elements covered in this book, you now have a solid understanding as to what goes into building a website (much more than code!). The main thing you should take from this book is that you don’t need to be an expert at everything but ensuring that you take the time to notice what’s out there and deciding what will best help your site are among the most important elements of the process. As you leave this book and go on to updating your website over time and perhaps learning new skills, always remember to be brave, take risks (through trial and error), and never feel that things are getting too hard. If you choose to learn skills that were only briefly mentioned in this book, like scripting, or to get involved in using content management systems and web software, go at a pace that you feel comfortable with. With that in mind, let’s go over the 10 most important messages I would personally recommend. After that, I’ll give you some useful resources like important websites for people learning to create for the Internet and handy software. Advice is something many professional designers and developers give out in spades after learning some harsh lessons from what their own bitter experiences. -

Emergency Field Operations
WORLD HEALTH ORGANIZATION HANDBOOK FOR EMERGENCY FIELD OPERATIONS EHA/FIELD/99.1 Original English Distr.: Limited HANDBOOK FOR EMERGENCY FIELD OPERATIONS Acknowledgements The authors and editorial team (Stephen Bertrand, Sandro Colombo, Xavier Leus and Alessandro Loretti) would like to acknowledge the reference material, assistance and encouragement given by the following: Paul Acriviadis, Richard Alderslade, Andy Andreas, Tina Coleman-Appiah, Shigeki Asahi, Fabrizio Bassani, Angelo Belli, Frank and Ros Bertrand, Robin Biellik, Diego Buriot, Brandt Burkholder, Ildo Carvalho, Louisa Chan, Youcef Chellouche, Vincenzo Ciafré, Maire Connolly, Rosario D’Alessio, Danielle Deboutte, Claude De Ville Goyet, Pat Diskett, Rodger Doran, Jose Echevarria, Antonio Esteves, Cesare Forni, Gilles Forte, Magnus Grabe, Robin Gray, Robert Hagan, Heywote Hailemeskal, Laura Hammond, Laura Hawkins, Charlie Higgins, Paul Howard, ICRC, Randolph Kent, Peter King, Etsuko Kita, Adriaan Korver, Eliane Kristensen, Johanna Larusdottir, Laura Londen, Jean-Paul Menu, Dominique Metais, Luigi Migliorini, Najibullah Mojadiddi, MSF, Enrique Munoz, Gabriel Mweluko, Evaristo Njelesani, Eric Noji, Mastaneh Notz, Peter McAleese, OCHA, Enrico Pavignani, Pierre Perrin, Francoise Hery-Persin, Jean-Luc Poncelet, Gulam Popal, Garry Presthus, Trish Prosser, Margareta Rubin, Rino Scuccato, Archena Shah, Khalid Shibib, Rumishael Shoo, Luzitu Simao, Antonio Sitoi, Idrissa Sow, Julia Stuckey, Ganesan Sundaram, Daniel Tarantola, Yonas Tegegn, Nerayo Teklemichael, Jan Theunissen, Michel Thieren, Mike Toole, UNHCR, USAID, UNSECOORD, Stephan Van Dam, Hannu Vuori, WFP, Hillary Wild, Brad Woodruff, and Nevio Zagaria, Disclaimer “This document is not issued to the general public, and all rights are reserved by the World Health Organization (WHO). The document may not be reviewed, abstracted, quoted, reproduced or translated, in part or in whole, without the prior written permission of WHO. -

Download Resume
Kalen Gibbons KalenGibbons.com Software Engineer | 406-885-1687 | [email protected] Skills Overview I am a highly skilled programmer and application architect, that has been building enterprise- level applications for more than a decade. I have a strong understanding of programming principals, design patterns, and best practices; allowing my applications to be scalable, maintainable, reusable, and well written. Listed below are the technologies I commonly work with. Angular I have worked with Angular and AngularJS daily for several years and have built multiple of projects with it. I have a strong understanding of Angular architecture and how to write robust client-side applications. Node.js Several years of experience building Node.js applications with the Express framework. I understand event-driven architectures and how to build modular and scalable applications using JavaScript. MongoDB Experience with MongoDB and Mongoose, as well as other NoSQL data stores. I have built several projects with MongoDB and understand how to work with document-oriented data. Gulp / Jenkins I have used Gulp and Jenkins for building, running, testing, and deploying applications. I understand the workflows of these technologies and how they can be optimized to benefit a team. SQL / Databases Expertise with writing SQL and working SQL Server, MySQL, and other relational databases. I have experience creating models, normalizing and denormalizing data, and working with views, and stored procedures, etc. ActionScript 3.0 Extensive knowledge and experience with Adobe Flex, MXML, the Parsley framework and Cairngorm microarchitecture. ColdFusion Excellent understanding of object-oriented programming with ColdFusion, and the ColdBox Platform. I have experience with dependency injection, AOP, unit and integration testing, ORMs, and design patterns, methodologies, and best practices related to ColdFusion. -

Vue.Js (Evan You, Ancien De Google)
Crédits : Guillaume Rivière Axios Module d’expertise de 2e année Développer des applications full-web : Devenir développeur full-stack ! < 1. Introduction /> – ESTIA – Guillaume Rivière Dernière révision : mars 2019 1 Contexte . Technologies des GAFAM • Permet de déployer des applications et des services à l’échelle mondiale . Application riches . Progressive webapps . Single-Page Application (SPA) 2 Références . Youtube . Dooble . GMail . Amazon . Facebook . MS O365 . Twitter . Pinterest . Onshape.com . Odoo (OpenERP) 3 Transactions pages web classiques 4 Transactions application web : SPA 5 Histoire . HTML . HTML + CSS . XHTML4 . HTML5 + CSS3 . Ajax . Jquery . Bootstrap . AngularJS / Angular / React / Backbone.js 6 Application full-web . « Stack » • Front-end • API / webservice • Back-end • Base de données Développeur front-end Développeur || full-stack Développeur back-end www.alticreation.com, 2013 7 Webservice d’API : applis web / mobile 9 Cloud computing . SaaS . Google Cloud Platform . AWS . MS Azure 10 Front-end • Angular (TypeScript) • React • Vue Office québécois de la langue française : Application frontale 11 Back-end . Back-end • PHP • Symfony • Laravel • Javascript / Typescript • NodeJS • Python • Djando • Ruby • Rails • R • C++ • Crow • Silicon • Cppcms • Tntnet • ctml Office québécois de la langue française : Application dorsale 12 Base de données . Base de données • Relationnelle • MySQL • PostgreSQL • Not Only SQL (NOSQL) • PostgreSQL • MongoDB 13 Full-Stack . API / Webservice • REST • Format • JSON • XML • XML-RPC • GraphQL 14 Choix pour ce module . VueJS • Simple et facile à apprendre • Permet des projets d’ampleur • Reprend des aspects de React et Angular . Symfony • Très répandu • PHP = 80% des applications serveurs en 201X 15 Plan . VueJS 2 . Symfony 4 . VueJS + Symfony . Projet 16 Prérequis . HTML5 . CSS3 . MySQL . PHP5 . Programmation Orientée Objet . -

Coldbox from Hero to Superhero
ColdBox from Hero to SuperHero Description In this workshop you will be building a headless CMS (Content Management System) via a secure and versioned RESTFul API. You will be leveraging security best practices and securing the API using JWT tokens and cbSecurity (coldbox-security.ortusbooks.com). Everything will be built using Behavior and Test Driven Programming. Every crook and cranny will have automated tests. You will be using several of the most advanced features of the CFML engine and of ColdBox HMVC. From flexible resource routing, AOP interception points, logging, fluent query building, integration and unit testing and so much more. Prerequisites Please have the following software on your computer before the workshop. If everyone is downloading the software at once, it will slow everyone down, and we want to make the most of our time together. A Modern Computer Please make sure you have a computer that is modern. No running windows 95, 7 or something funky from the year 2000. Make sure you have plenty of FREE RAM (at least 4gb) and with a modern processor (at least an i5). Most of the hiccups in trainings are when people do not meet the appropriate requirements in their own machines. We will be running CFML engines and docker containers, so make sure you can run them. Windows PRO If you are in Windows you will need Windows PRO and not Windows Home in order for Docker Desktop to be installed. We will be using Docker for our data services so you MUST be able to install and run docker containers.