Long-Distance Distribution of Discrete and Continuous Variable Entanglement with Atomic Ensembles
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Alexander Karlberg Reciation Classes and Tutorials Lectures High
Alexander Karlberg Merton College, Merton Street, Oxford, OX1 4JD, United Kingdom +44 07784 623555 [email protected] EDUCATION DPhil in Theoretical Physics. University of Oxford, Rudolf Peierls Centre for Theo- retical Physics 2012-Present MSc in Physics. University of Copenhagen, Niels Bohr Institute 2010-2012 GPA: 11.9/12 (Top of class) Thesis: Space-Cone gauge and Scattering Amplitudes BSc in Physics. University of Copenhagen, Niels Bohr Institute 2007-2010 GPA: 11.9/12 (Top of class) EMPLOYMENT Non-stipendiary Lecturer. Merton College, University of Oxford 2013-Present Graduate Mentor. Merton College, University of Oxford 2012-Present High School Teacher (Arsvikar)˚ . Sankt Annæ Gymnasium 2010-2011 Teaching Assistant. Niels Bohr Institute, University of Copenhagen 2009-2012 TEACHING Reciation Classes and Tutorials EXPERIENCE Niels Bohr Institute Mechanics Electrodynamics Quantum Mechanics Thermodynamics Mathematical Methods Brush Up for new students Merton College Mathematical Methods Lectures Niels Bohr Institute Thermodynamics (4h) High School Level Sankt Annæ Gymnasium Responsibility for teaching a class of 30 students in preliminary maths (Mat C) with subsequent examination. Supervision Niels Bohr Institute Supervised two first-year projects in 2010 and 2011 respectively. CONFERENCES IPPP Senior Experimental Fellowships Kick-off Meeting (2014) AND SCHOOLS Spaatind 2014 - Nordic Conference on Particle Physics (2014) ATTENDED BUSSTEPP 2013 (summer school) - University of Sussex, Brighton (2013) Higgs Symposium, University of Edinburgh (2013) Spaatind 2013 - Nordic Winter School on Particle Physics (2013) Spaatind 2012 - Nordic Conference on Particle Physics (2012) Niels Bohr Summer Institute - Strings, Gauge Theory and the LHC (2011) CERN summer student (2010) TALKS GIVEN BUSSTEPP student talk (2013). Electroweak ZZjj production at NLO in QCD matched with parton shower in the POWHEG-BOX Kandidatdag (2012). -

Reaching for the Stars
REACHING FOR THE STARS – supporting excellent research Centers of Excellence 2002-2010 CENTER CENTER LEADER LOCATION Centers established in 2009/2010 Center on Autobiographical Memory Research Dorthe Berntsen Aarhus University Center for Particle Physics & Origin Mass Francesco Sannino University of Southern Denmark Center for Particle Physics Peter Hansen University of Copenhagen Centre for Symmetry and Deformation Jesper Grodal University of Copenhagen Centre for Materials Crystallography Bo Brummerstedt Iversen Aarhus University Center for GeoGenetics Eske Willerslev University of Copenhagen Centre for Quantum Geometry of Moduli Spaces Jørgen Ellegaard Andersen Aarhus University Center for Macroecology, Evolution and Climate Carsten Rahbek University of Copenhagen Centre for Star and Planet Formation Martin Bizzarro University of Copenhagen Centers established in 2007 Center for Research in Econometric Analysis of Time Series Niels Haldrup Aarhus University Center for Carbohydrate Recognition and Signalling Jens Stougaard Aarhus University Centre for Comparative Genomics Rasmus Nielsen University of Copenhagen Centre for DNA Nanotechnology Kurt Vesterager Gothelf Aarhus University Centre for Epigenetics Kristian Helin University of Copenhagen Centre for Ice and Climate Dorthe Dahl-Jensen University of Copenhagen Center for Massive Data Algorithmics Lars Arge Aarhus University Pumpkin – Membrane Pumps in Cells and Disease Poul Nissen Aarhus University Centers established in 2005 Nordic Center for Earth Evolution Don Canfield University of Southern Denmark Centre for Individual Nanoparticle Functionality Ib Chorkendorff Technical University of Denmark Centre for Inflammation and Metabolism Bente Klarlund Pedersen Copenhagen University Hospital Centre for Genotoxic Stress Jiri Lukas The Danish Cancer Society Centre for Social Evolution Jacobus J. Boomsma University of Copenhagen Centre for mRNP Biogenesis and Metaolism Torben Heick Jensen Aarhus University Centre for Insoluble Protein Structures Niels Chr. -

Physics Nobel Prize 1975
Physics Nobel Prize 1975 Nobel prize winners, left to right, A. Bohr, B. Mottelson and J. Rainwater. 0. Kofoed-Hansen (Photos Keystone Press, Photopress) Before 1949 every physicist knew that mooted, it was a major breakthrough from 1943-45. From December 1943 the atomic nucleus does not rotate. in thinking about the nucleus and he was actually in the USA. Back in The reasoning behind this erroneous opened a whole new field of research Denmark after the war, he obtained belief came from the following argu• in nuclear physics. This work has for his Ph. D. in 1954 for work on rota• ments. A quantum-mechanical rotator years been guided by the inspiration tional states in atomic nuclei. His with the moment of inertia J can take of Bohr and Mottelson. thesis was thus based on the work for up various energy levels with rota• An entire industry of nuclear which he has now been recognized at tional energies equal to h2(l + 1)| research thus began with Rainwater's the very highest level. He is Professor /8TC2J, where h is Planck's constant brief contribution to Physical Review at the Niels Bohr Institute of the ^nd I is the spin. As an example, I may in 1950 entitled 'Nuclear energy level University of Copenhagen and a nave values 0, 2, 4, ... etc. If the argument for a spheroidal nuclear member of the CERN Scientific Policy nucleus is considered as a rigid body, model'. Today a fair-sized library is Committee. then the moment of inertia J is very needed in order to contain all the Ben Mottelson was born in the USA large and the rotational energies papers written on deformed nuclei and in 1926 and has, for many years, become correspondingly very small. -
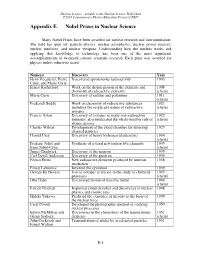
Appendix E Nobel Prizes in Nuclear Science
Nuclear Science—A Guide to the Nuclear Science Wall Chart ©2018 Contemporary Physics Education Project (CPEP) Appendix E Nobel Prizes in Nuclear Science Many Nobel Prizes have been awarded for nuclear research and instrumentation. The field has spun off: particle physics, nuclear astrophysics, nuclear power reactors, nuclear medicine, and nuclear weapons. Understanding how the nucleus works and applying that knowledge to technology has been one of the most significant accomplishments of twentieth century scientific research. Each prize was awarded for physics unless otherwise noted. Name(s) Discovery Year Henri Becquerel, Pierre Discovered spontaneous radioactivity 1903 Curie, and Marie Curie Ernest Rutherford Work on the disintegration of the elements and 1908 chemistry of radioactive elements (chem) Marie Curie Discovery of radium and polonium 1911 (chem) Frederick Soddy Work on chemistry of radioactive substances 1921 including the origin and nature of radioactive (chem) isotopes Francis Aston Discovery of isotopes in many non-radioactive 1922 elements, also enunciated the whole-number rule of (chem) atomic masses Charles Wilson Development of the cloud chamber for detecting 1927 charged particles Harold Urey Discovery of heavy hydrogen (deuterium) 1934 (chem) Frederic Joliot and Synthesis of several new radioactive elements 1935 Irene Joliot-Curie (chem) James Chadwick Discovery of the neutron 1935 Carl David Anderson Discovery of the positron 1936 Enrico Fermi New radioactive elements produced by neutron 1938 irradiation Ernest Lawrence -

The Early History of the Niels Bohr Institute
CHAPTER 4.1 Birthplace of a new physics - the early history of the Niels Bohr Institute Peter Robertson* Abstract SCI.DAN.M. The foundation in 1921 of the Niels Bohr Institute in Copenhagen was to prove an important event in the I birth of modern physics. From its modest beginnings as • ONE a small three-storey building and a handful of physicists, HUNDRED the Institute underwent a rapid expansion over the fol lowing years. Under Bohr’s leadership, the Institute provided the principal centre for the emergence of quan YEARS tum mechanics and a new understanding of Nature at OF the atomic level. Over sixty physicists from 17 countries THE came to collaborate with the Danish physicists at the In BOHR stitute during its first decade. The Bohr Institute was the ATOM: first truly international centre in physics and, indeed, one of the first in any area of science. The Institute pro PROCEEDINGS vided a striking demonstration of the value of interna tional cooperation in science and it inspired the later development of similar centres elsewhere in Europe and FROM the United States. In this article I will discuss the origins and early development of the Institute and examine the A CONFERENCE reasons why it became such an important centre in the development of modern physics. Keywords: Niels Bohr Institute; development of quan tum mechanics; international cooperation in science. * School of Physics, University of Melbourne, Melbourne, Vic. 3010, Australia. Email: [email protected]. 481 PETER ROBERTSON SCI.DAN.M. I 1. Planning and construction of the Institute In 1916 Niels Bohr returned home to Copenhagen over four years since his first visit to Cambridge, England, and two years after a second visit to Manchester, working in the group led by Ernest Ru therford. -

Heisenberg's Visit to Niels Bohr in 1941 and the Bohr Letters
Klaus Gottstein Max-Planck-Institut für Physik (Werner-Heisenberg-Institut) Föhringer Ring 6 D-80805 Munich, Germany 26 February, 2002 New insights? Heisenberg’s visit to Niels Bohr in 1941 and the Bohr letters1 The documents recently released by the Niels Bohr Archive do not, in an unambiguous way, solve the enigma of what happened during the critical brief discussion between Bohr and Heisenberg in 1941 which so upset Bohr and made Heisenberg so desperate. But they are interesting, they show what Bohr remembered 15 years later. What Heisenberg remembered was already described by him in his memoirs “Der Teil und das Ganze”. The two descriptions are complementary, they are not incompatible. The two famous physicists, as Hans Bethe called it recently, just talked past each other, starting from different assumptions. They did not finish their conversation. Bohr broke it off before Heisenberg had a chance to complete his intended mission. Heisenberg and Bohr had not seen each other since the beginning of the war in 1939. In the meantime, Heisenberg and some other German physicists had been drafted by Army Ordnance to explore the feasibility of a nuclear bomb which, after the discovery of fission and of the chain reaction, could not be ruled out. How real was this theoretical possibility? By 1941 Heisenberg, after two years of intense theoretical and experimental investigations by the drafted group known as the “Uranium Club”, had reached the conclusion that the construction of a nuclear bomb would be feasible in principle, but technically and economically very difficult. He knew in principle how it could be done, by Uranium isotope separation or by Plutonium production in reactors, but both ways would take many years and would be beyond the means of Germany in time of war, and probably also beyond the means of Germany’s adversaries. -

Release of Documents Relating to 1941 Bohr-Heisenberg Meeting
Release of documents relating to 1941 Bohr-Heisenberg meeting DOCUMENTS RELEASED 6 FEBRUARY 2002 The family of Niels Bohr has decided to release all documents deposited at the Niels Bohr Archive, either written or dictated by Niels Bohr, pertaining specifically to the meeting between Bohr and Heisenberg in September 1941. There are in all eleven documents. The decision has been made in order to avoid possible misunderstandings regarding the contents of the documents. The documents supplement and confirm previously published statements of Bohr's recollections of the meeting, especially those of his son, Aage Bohr. The documents have now been organised, transcribed and translated into English at the Niels Bohr Archive. Because of the overwhelming interest in the material, it has been decided that the material should be published in full instead of being made available to scholars upon individual application, as is normal practice at the Niels Bohr Archive. This has been done by placing facsimiles, transcriptions and translations on this website here. An illustrated edition of the transcriptions and translations is published in the journal Naturens Verden, Vol. 84, No. 8 - 9. Reprints can be obtained from the Niels Bohr Archive for USD8/EUR8/DKK50 (prepaid). Release of documents relating to 1941 Bohr-Heisenberg meeting. Document 1. Draft of letter from Bohr to Heisenberg, never sent. In the handwriting of Niels Bohr's assistant, Aage Petersen. Undated, but written after the first publication, in 1957, of the Danish translation of Robert Jungk, Heller als Tausend Sonnen, the first edition of Jungk's book to contain Heisenberg's letter. -

Absolute Zero, Absolute Temperature. Absolute Zero Is the Lowest
Contents Radioactivity: The First Puzzles................................................ 1 The “Uranic Rays” of Henri Becquerel .......................................... 1 The Discovery ............................................................... 2 Is It Really Phosphorescence? .............................................. 4 What Is the Nature of the Radiation?....................................... 5 A Limited Impact on Scientists and the Public ............................ 6 Why 1896? .................................................................. 7 Was Radioactivity Discovered by Chance? ................................ 7 Polonium and Radium............................................................. 9 Marya Skłodowska .......................................................... 9 Pierre Curie .................................................................. 10 Polonium and Radium: Pierre and Marie Curie Invent Radiochemistry.. 11 Enigmas...................................................................... 14 Emanation from Thorium ......................................................... 17 Ernest Rutherford ........................................................... 17 Rutherford Studies Radioactivity: ˛-and ˇ-Rays.......................... 18 ˇ-Rays Are Electrons ....................................................... 19 Rutherford in Montreal: The Radiation of Thorium, the Exponential Decrease........................................... 19 “Induced” and “Excited” Radioactivity .................................... 20 Elster -

Aage Bohr Copenhagen, Denmark, 19 June 1922 - 9 Sept
Aage Bohr Copenhagen, Denmark, 19 June 1922 - 9 Sept. 2009 Nomination 17 Apr. 1978 Field Physics Title Professor of Physics at the University of Copenhagen Commemoration – Aage Bohr was born in Copenhagen a few months before his father won the Nobel Prize. His father was Niels Bohr, one of the giants of physics in the early 20th century, who was able to untangle the confusing mysteries of quantum mechanics. Aage Bohr’s childhood was one in which a pantheon of great physicists were friends visiting the family home. The remarkable generation of scientists who came to join his father in his work became uncles for him. These uncles were Henrik Kramers from the Netherlands, Oskar Klein from Sweden, Yoshio Nishina from Japan, Werner Karl Heisenberg from Germany and Wolfgang Pauli from Austria. These are all giants of physics, so Aage Bohr is an example of what science means and what political violence means. In fact, three years after he was born, Hitler ordered the deportation of Danish Jews to concentration camps but the Bohrs, along with most of the other Danish Jews, were able to escape to Sweden. I would like to recall that, despite these great tragedies and political problems, Aage Bohr was able to follow his father’s track, contributing to clarify a very important problem in nuclear physics. He was able, together with Ben Roy Mottelson, to explain why the nuclei were not perfectly spherical. I remind you that the volume of the nucleus is 1 millionth of a billion, 10-15 smaller than the atom, and when Bohr was young the general feeling about nuclear physics was that the nuclei were perfectly symmetric, perfect spheres, platonically perfect spheres, and here comes the contribution of Aage Bohr with Mottelson, because some experiments were showing that this was probably not true. -

Evolving the Structure of Hidden Markov Models Kyoung-Jae Won, Adam Prügel-Bennett, and Anders Krogh
IEEE TRANSACTIONS ON EVOLUTIONARY COMPUTATION, VOL. 10, NO. 1, FEBRUARY 2006 39 Evolving the Structure of Hidden Markov Models Kyoung-Jae Won, Adam Prügel-Bennett, and Anders Krogh Abstract—A genetic algorithm (GA) is proposed for finding the being imposed faithfully captures some biological constraints, structure of hidden Markov Models (HMMs) used for biological it should not significantly increase the approximation error. As sequence analysis. The GA is designed to preserve biologically the generalization error is the sum of the estimation and approx- meaningful building blocks. The search through the space of HMM structures is combined with optimization of the emis- imation error, imposing a meaningful structure on the HMM sion and transition probabilities using the classic Baum–Welch should give good generalization performance. By automatically algorithm. The system is tested on the problem of finding the optimizing the HMM architecture, we are potentially throwing promoter and coding region of C. jejuni. The resulting HMM has away the advantage over other machine learning techniques, a superior discrimination ability to a handcrafted model that has namely their amenability to incorporate biological information been published in the literature. in their structure. That is, we risk finding a model that “overfits” Index Terms—Biological sequence analysis, genetic algorithm the data. (GA), hidden Markov model (HMM), hybrid algorithm, machine The aim of the research presented in this paper is to utilize learning. the flexibility provided by genetic algorithms (GAs) to gain the advantage of automatic structure discovery, while retaining I. INTRODUCTION some of the benefits of a hand-designed architecture. That is, by IDDEN MARKOV models (HMMs) are probabilistic fi- choosing the representation and genetic operators, we attempt H nite-state machines used to find structures in sequential to bias the search toward biologically plausible HMM architec- data. -

Astronomy Astrophysics
A&A 433, 113–116 (2005) Astronomy DOI: 10.1051/0004-6361:20042030 & c ESO 2005 Astrophysics GRB 040403: A faint X-ray rich gamma-ray burst discovered by INTEGRAL S. Mereghetti1,D.Götz1,2,M.I.Andersen3, A. Castro-Tirado4, F. Frontera5,6, J. Gorosabel4,D.H.Hartmann7, J. Hjorth8,R.Hudec9, K. Hurley10, G. Pizzichini6, N. Produit11,A.Tarana12, M. Topinka9, P. Ubertini12, and A. de Ugarte4 1 Istituto di Astrofisica Spaziale e Fisica Cosmica – CNR, Sezione di Milano “G.Occhialini”, via Bassini 15, 20133 Milano, Italy e-mail: [email protected] 2 Dipartimento di Fisica, Università degli Studi di Milano Bicocca, P.zza della Scienza 3, 20126 Milano, Italy 3 Astrophysikalisches Institut Potsdam, An der Sternwarte 16, 14482 Potsdam, Germany 4 Instituto de Astrofísica de Andalucía (IAA-CSIC), Apartado de Correos 3004, 18080 Granada, Spain 5 Physics Department, University of Ferrara, via Paradiso 12, 44100 Ferrara, Italy 6 Istituto di Astrofisica Spaziale e Fisica Cosmica – CNR, Sezione di Bologna, via Gobetti 101, 40129 Bologna, Italy 7 Clemson University, Department of Physics & Astronomy, Clemson, SC 29634-0978, USA 8 Niels Bohr Institute, Astronomical Observatory, University of Copenhagen, Juliane Maries Vej 30, 2100 Copenhagen, Denmark 9 Astronomical Institute, Academy of Sciences of the Czech Republic, 251 65 Ondrejov, Czech Republic 10 University of California at Berkeley, Space Sciences Laboratories, Berkeley, CA 94720-7450, USA 11 Integral Science Data Centre, Chemin d’Écogia 16, 1290 Versoix, Switzerland 12 Istituto di Astrofisica Spaziale e Fisica Cosmica – CNR, Sezione di Roma, via Fosso del Cavaliere 100, 00133 Roma, Italy Received 20 September 2004 / Accepted 1 December 2004 Abstract. -

James Rainwater 1 9 1 7 — 1 9 8 6
NATIONAL ACADEMY OF SCIENCES JAMES RAINWATER 1 9 1 7 — 1 9 8 6 A Biographical Memoir by VAL L. FITCH Any opinions expressed in this memoir are those of the author and do not necessarily reflect the views of the National Academy of Sciences. Biographical Memoir COPYRIGHT 2009 NATIONAL ACADEMY OF SCIENCES WASHINGTON, D.C. Photograph Courtesy AIP Emilio Segré Archives. JAMES RAINWATER December 9, 1917–May 31, 1986 BY VAL L . FITCH . I. RABI, THE COLUMBIA University physics department’s lead- Iing researcher, chairman, and then after his retirement, wise old man, disliked the notion that physicists had divided themselves into two groups: experimental and theoretical. “There is only Physics,” he said, “with a capital P.” His strong feeling always manifested itself in his insistence that those who did experimental theses have a rigorous grounding in theoretical subjects and that theorists know something about experiment. He had two outstanding examples of such people in the department. One was Willis Lamb, who had done his thesis with Robert Oppenheimer and after a series of notable theoretical papers had won the Nobel Prize for an experiment. Rabi never forgave Lamb for leaving Columbia and going back to his native California. And then there was Jim Rainwater, the subject of this memoir, who had done his thesis with John Dunning, a consummate experimental- ist, and had gone on to win the Nobel Prize for theoretical work. Rainwater spent his entire career at Columbia, first as a graduate student and then as a member of the faculty. He enjoyed Rabi’s highest accolades.