Novemberjuly 2015
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Pro Bono at Venable
Venable Cares SPRING 2007 Those Who Can, “One has only to agree Should. to represent a pro bono Amy J. McMaster client to realize that the While interning with the Legal Aid Society my fi rst summer rewards are plentiful; after law school, I gained a new appreciation for attorneys one might even say, who choose a life of public service. Thinly staffed, the two addictive.” attorneys I supported managed more cases between them over the course of that summer than many do in a lifetime. it, in fact. For a variety of reasons, such cases often Although a career in public service may arrive at an attorney’s doorstep like an impetuous not be for everyone, I am always surprised at orphan - demanding and in need of immediate how some attorneys are willing to perform CONTENTS 1 attention - affording their new caregiver precious hundreds of hours of pro bono work each little time to get up to speed on the facts of the year, while others would not think twice about case before jumping in with both feet. But jump 1 Those Who Can, Should. checking the “seldom to never” category in an they must. Pro bono clients typically seek attorney survey. It certainly doesn’t seem to representation only in the midst of an active 2 Letter from the have anything to do with how busy they are. confl ict involving emotionally-wrought issues, Like so many things, if you need an attorney to Pro Bono Chair such as: shelter, livelihood, welfare or medical handle a pro bono case, ask one who’s busy. -
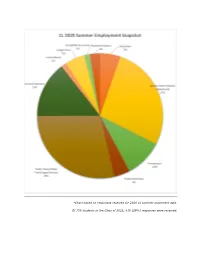
*Chart Based on Responses Received for 2020 1L Summer Placement Data
*Chart based on responses received for 2020 1L summer placement data. Of 708 students in the Class of 2022, 418 (59%) responses were received. Government (Federal/State/Local) California Dept. of Justice, Consumer Law Section (San Diego, CA) Council of the DC, Judiciary and Public Safety Committee (Washington, DC) Criminal Justice Coordinating Council - CJCC (Washington, DC) DC Dept. of Health (Washington, DC) DC Dept. of Consumer and Regulatory Affairs (DCRA) (Washington, DC) DC Public Schools, Office of General Counsel (Washington, DC) Environmental Defense Fund (Boulder, CO) Federal Aviation Administration - FAA, Office of the Chief Counsel, Airports & Environmental Law Branch (Washington, DC) Federal Circuit Bar Association (Washington, DC) Federal Communications Commission (FCC), Wireless Telecommunications Bureau (Washington, DC) Federal Communications Commission (Washington, DC) Federal Communications Commission, Media Bureau (Washington, DC) Federal Communications Commission, Office of Legislative Affairs (Washington, DC) Federal Energy Regulatory Commission - FERC (Washington, DC) Federal Labor Relations Authority (FLRA) (Washington, DC) Federal Reserve Bank of New York (New York, NY) Federal Reserve Board, Office of the Inspector General (Washington, DC) Federal Trade Commission (FTC) (Washington, DC) Federal Trade Commission (FTC), Bureau of Competition (Washington, DC) Government Accountability Project (Washington, DC) Government of the DC; Dept. of Housing and Community Development (Washington, DC) Governor's Office of General Counsel (Harrisburg, PA) National Labor Relations Board, Office of General Counsel (Washington, DC) National Labor Relations Board, Region 9 (Cincinnati, OH) New York City Law Dept. (New York, NY) NYC Law Dept. (New York, NY) Office of Police Accountability (Seattle, WA) Office of Special Counsel (Washington, DC) Office of the Tenant Advocate (Washington, DC) U.S. -

Most Influential Minority Lawyers in Los Angeles
CUSTOM CONTENT JANUARY 28, 2019 MOST INFLUENTIAL Minority Attorneys IN LOS ANGELES 087-103_MinoritySupp.indd 87 1/23/19 12:18 PM 88 LOS ANGELES BUSINESS JOURNAL – CUSTOM CONTENT JANUARY 28, 2019 MOST INFLUENTIAL MINORITY ATTORNEYS NEERAJ ARORA TERRY B. BATES SABRINA A. BELDNER WILLIAM J. BRIGGS, II Partner Partner Partner Partner Morgan, Lewis & Bockius LLP Reed Smith LLP McGuireWoods LLP Venable LLP eeraj Arora’s work also involves erry Bates is a litigation partner with cGuireWoods partner Sabrina Beldner’s illiam J. Briggs, II, a partner with representing clients such as Prudential Reed Smith’s Los Angeles’ office and has clients refer to her as their “Swiss Army Venable LLP in Los Angeles, is NCapital Group, in connection with a $100 Tsubstantial first chair trial experience MKnife” for employment matters. She is Wrecognized as a leading trial lawyer million private placement to a wholly owned for both plaintiffs and defendants. He is a a go-to attorney in high-stakes employment and civil litigator, with extensive experience subsidiary of a global developer of solar energy member of Reed Smith’s Complex Litigation discrimination, wage and hour litigation in the entertainment industry. He provides resources for construction debt used to finance Group where he serves as Deputy Practice and traditional labor matters. Beldner also counsel to some of the most recognizable a new 75 MW solar photovoltaic generating Group Leader. He is also a member of Reed represents the next generation of leadership names in the film, television, music, and facility located in North Carolina. He worked Smith’s Diversity and Inclusion Committee’s within McGuireWoods. -

The Download DEVELOPMENTS in E-COMMERCE, PRIVACY, INTERNET ADVERTISING, MARKETING and INFORMATION SERVICES LAW and POLICY
the download DEVELOPMENTS IN E-COMMERCE, PRIVACY, INTERNET ADVERTISING, MARKETING AND INFORMATION SERVICES LAW AND POLICY Winner of Chambers USA "Award of Excellence" for the top FEBRUARY 2011 privacy practice in the United States ……………………………. Special Report: California Supreme Court Winner of Chambers USA "Award of Excellence" for the top Announces State Law Prohibits Marketing advertising practice in United States Requests for ZIP Codes ……………………………. Two of the "Top 25 Privacy Experts" by Computerworld In a case with major implications for retailers and marketers, the Supreme ……………………………. Court of California ruled on February 10, 2011 that state law prohibits "Winning particular plaudits" for businesses from requesting and recording ZIP codes from consumers "sophisticated enforcement work" prior to credit card transactions, including requests for use in marketing. – Chambers and Partners Pineda v. Williams-Sonoma Stores, Inc., S178241 (Cal., Feb. 10, 2011). ……………………………. Numerous other states have laws similar to California’s that regulate Recognized in the Legal 500 as a merchant practices with respect to collecting and recording personal top law firm for its outstanding information in connection with a credit card purchase. data protection and privacy practice The impact of the Court’s decision is not limited to future practices. The Court also held that its interpretation of the statute applies retroactively, ISSUE EDITORS thereby opening the door to class action consumer lawsuits based on businesses’ prior requests for ZIP codes for marketing purposes. Within days of the Court’s ruling, over a dozen cases have already been filed in California against major retailers. Courts can impose statutory damages of up to $1000 per violation of the law. -

The Connection Alumni Newsletter I Spring 2014
the connection Alumni Newsletter I Spring 2014 IN THIS ISSUE Alumni Event 1 Alumni Event Recap We Are Pleased to Announce “An Evening with Jeffrey Toobin” 2-3 Event Photos A high-profile senior analyst for CNN and staff writer for The 4 Firm Report New Yorker, Jeffrey Toobin is one of the country’s most respected experts on politics, media and the law. The author of critically 5 Awards and Recognition acclaimed best sellers, Mr. Toobin delved into the historical, political and personal inner workings of the Supreme Court and Connecting in Our its justices in his book The Nine: Inside the Secret World of the Supreme Court. The 6 Communities Nine spent more than four months on the New York Times Best Seller list and was named one of the best books of the year by Time, Newsweek, Entertainment Weekly 7 Events of Interest and the Economist. His newest book, The Oath, a sequel to The Nine, is a gripping insider’s account of the momentous ideological war between the John Roberts 7 California Update Supreme Court and the Obama administration. At the podium, Mr. Toobin is an unbiased, deeply analytic (and often very funny) expert on all matters of American law, politics and media. He provides a unique look into the inner workings of The Supreme Court and its influence, as well as how upcoming elections will shape the court and, in turn, the nation. His relaxed style, sense of humor and unprejudiced, forthright analysis make for a fascinating presentation. Please mark your calendar. Wednesday, June 25 Thursday, June 26 Venable’s Washington office Venable’s Baltimore office VENABLE SNAPSHOT 6:30 p.m. -

Venable Names Douglas C. Emhoff Managing Director, West Coast and Mitchell Evall Partner-In-Charge of Its Los Angeles Office | Abo…
11/21/2020 Venable Names Douglas C. Emhoff Managing Director, West Coast and Mitchell Evall Partner-in-Charge of its Los Angeles Office | Abo… [ Press Release. (Aug. 13, 2015). Venable Names Douglas C. Emhoff Managing Director, West Coast and Mitchell Evall Partner-in-Charge of its Los Angeles Office. Venable LLP. Reproduced for educational purposes only. Fair Use relied upon. ] Venable Names Douglas C. Emhoff Managing Director, West Coast and Mitchell Evall Partner-in- Charge of its Los Angeles Office Douglas C. Emhoff, Mitchell Evall, James E. Nelson and James L, Shea Los Angeles, CA - August 13, 2015 - Venable LLP announced this morning that Douglas C. Emhoff, former Partner-in-Charge of its Los Angeles ofce, has been named Managing Director, West Coast with oversight over the rm's current ofces in Los Angeles and San Francisco. Mitch Evall has assumed the position of Partner- in-Charge of the Los Angeles ofce. Jim Nelson will remain as Partner-in-Charge of the rm's growing San Francisco ofce. In a memo to the rm, Chairman James L. Shea noted that Mr. Emhoff joined the rm in 2006 as one of the founding Los Angeles ofce partners, and has served as Partner-in-Charge of that ofce for the past eight years while continuing to build his business and entertainment litigation practice. During that time, the ofce has experienced signicant growth and is now nearly 70 attorneys in litigation, entertainment, labor and employment, corporate, real estate, intellectual property, bankruptcy, tax and estate planning. Doug also helped found the San Francisco ofce in 2013, and will continue to serve clients from both California ofces. -

Digital Transparency Task Force Report and Recommendations
FAIR POLITICAL PRACTICES COMMISSION DIGITAL TRANSPARENCY TASK FORCE 2021 INTRODUCTION FROM THE CHAIR In the fall of 2019, the California Fair Political Practices Commission authorized the creation of a task force to examine issues surrounding the ever-growing and ever-changing nature and practice of digital political advertising. Abundant documentation shows what was once a novelty is now not only a widespread and common practice, but a continually growing norm of political communication. The rise in this practice of digital political discourse raises questions regarding the adequacy of the current transparency of the sources of these communications. A common and constant refrain from many in the political world is the law generally does not keep up with reality in the realm of political practices. The creation of the FPPC’s Digital Transparency Task Force (“DTTF”) was designed to bridge that gap – to gather information and bring together ideas to help create and modify regulations and laws to align them with the reality of the breadth and sophistication of digital political advertising. In compiling the makeup of the DTTF, the Commission was mindful of the scope of voices involved and the need for all to be heard. Thus, the DTTF specifically sought and embraced a wide variety of viewpoints. Members include representation from the digital platforms themselves, political scientists and academics who study the phenomenon and its effects on our political landscape, the very political practitioners currently using digital technology in their advertising and outreach, as well as groups devoted to transparency and general ‘good government’ practices. Along with the varied makeup of the DTTF itself, the subsequent public meetings included an even wider variety of voices, providing information, answering questions, offering examples of regulation and practices in a variety of other state and local jurisdictions, as well as providing advice and potential solutions to vexing questions posed by the DTTF. -

An Evening with LSC Thursday, May 11, 2017
Home, Stability, Family, Respect, Equity, Safety, Community, Generosity, Hope, Opportunity, Justice, Advocacy, Leadership An Evening With LSC Thursday, May 11, 2017 Featuring Guest Speaker Steve Phillips Founder of Democracy in Color, national political leader, civil rights lawyer and author of the New York Times bestselling Brown is the New White Pro Bono Leadership Award Honorees Benjamin Craven, Jones Day Tala Hartsough, Attorney at Law Asa M. Wynn-Grant, DLA Piper Cy Pres Award Honoree Adam Belsky, Gross Belsky Alonso LLP Home, Stability, Family, Respect, Equity, Safety, Community, Generosity, Hope, Opportunity, Justice, Advocacy, Leadership Home, Stability, Family, Respect, Equity, Safety, Community, Generosity, Hope, Opportunity, Justice, Advocacy, Leadership EVENT COMMITTEE Puppet Mills Mark Chavez Ann Alpers, Co-Chair Directly, Inc. Chavez & Gertler LLP S.H. Cowell Foundation Laura Ruettgers Lily Colby Carol Morganstern, Co-Chair Severson & Werson National Center for Youth Law Major, Lindsey & Africa Suzanne Stuckwisch Donna Wickham Furth Susan Tunnell, Co-Chair Alvarez & Marsal Disputes Attorney at Law Attorney at Law and Investigations, LLC Mikiko Huang Darren Teshima California Pacific Medical Center Simona Agnolucci Orrick Herrington & Sutcliffe LLP Scott Karchmer Keker, Van Nest & Peters LLP Kim Thompson Morgan Lewis & Bockius LLP Mark Chavez PricewaterhouseCoopers LLP Sharon Meadows Chavez & Gertler LLP Christopher Zand USF School of Law Arthur Cirulnick Brouwer & Janachowski, LLC Puppet Mills Venable LLP Directly, Inc. Nell Clement BOARD OF DIRECTORS John O’Toole Farella Braun + Martel LLP Ann Alpers, Chair Attorney at Law Ashley Vinson Crawford S.H. Cowell Foundation James Schurz Akin Gump Strauss Hauer & Feld LLP Kim Thompson, Vice Chair Morrison & Foerster LLP Erin E. Dolly PricewaterhouseCoopers LLP Janet Sherwood Hirschfeld Kraemer LLP Suzanne Stuckwisch, Treasurer Advokids Sarah K. -

Government Affairs Compliance Tune-Up
Government Affairs Compliance Tune-Up January 16, 2014 Today’s Presenters Larry Norton Alexandra Megaris Ron Jacobs 202.344.4541 212.370.6210 202.344.8215 [email protected] [email protected] [email protected] www.venable.com/political-law-practices www.PoliticalLawBriefing.com Subscribe to Blog © 2014 Venable LLP 2 Agenda 1. Political Activity 3. Gifts & • PACs Entertainment • Super PACs • Common • Other Ideas Exemptions • Transparency • Hosting Events • Pay-to-Play • State trends 2. Lobbying • Federal • State • Enforcement Trends 3 © 2014 Venable LLP Risks and Rewards • Protect your business • Laws vary widely • New opportunities • Many traps • Enhance reputation • Impact on business and personal activity • Favorable regulatory climate • Scrutiny from: Regulators Media Competitors Watchdogs • Compliance must involve entire company © 2014 Venable LLP 43 Political Activities Menu of Political Options Corporate Contributions Create PAC Candidate Events Create Super PAC Donate to Super PAC Donate to 501(c)(4) © 2014 Venable LLP 6 Corporate Campaign Contributions • Permitted in some states • Beware of “pay-to-play” laws Washington Maine Montana North Dakota Minnesota Oregon New Hampshire Wisconsin Vermont Idaho South Dakota New York Massachusetts Wyoming Michigan Rhode Island Iowa Pennsylvania Nevada Nebraska Connecticut Ohio Utah Illinois Indiana New Jersey Colorado West Virginia Delaware Kansas Missouri California Virginia Maryland Kentucky Tennessee North Carolina Oklahoma Arizona Arkansas New Mexico South Carolina Alabama -

Closing Night Reception – Tuesday, March 20Th Attendee Tote Bags
PRESIDENTIAL SPONSORS Closing Night Reception – Tuesday, March 20th Contact: www.exiger.com Learn more about Exiger (PDF) Attendee Tote Bags Greenberg Traurig has one of the broadest and deepest broker-dealer practices in the country, with team members located in key geographic locations nationwide. We help our clients formulate strategies and take steps to limit litigation and regulatory risk. We regularly serve as lead defense counsel in complex, high stakes enforcement matters before the SEC, FINRA and state regulators. Our trial experience in court and arbitration across the nation is unparalleled: the members of our team have collectively tried to conclusion well over one thousand matters involving a wide variety of issues facing the financial services industry. The value we can provide is enhanced by our commitment to work closely with attorneys in related disciplines throughout the firm. Contact: William D. Briendel, Co-Chair, Securities Litigation Practice, Greenberg Traurig LLP, MetLife Building, 200 Park Avenue, New York, NY 10166 | 212.801.2107 | [email protected] | Tracy L. Gerber, Co-Chair, Securities Litigation Practice, 777 South Flagler Drive, Suite 300 East, West Palm Beach, FL 33401 | 561.650.7985 | [email protected] | www.gtlaw.com Event Mobile App Lunch & Learn – Tuesday, March 20th Two (2) Light Boxes QuisLex is an award-winning legal services provider that specializes in managed document review, contract management, compliance services, legal spend management, and legal operations consulting. We employ operational excellence, Six Sigma based quality processes and ISO certified data security to support large-scale, complex legal projects for companies and law firms. Our full-time highly trained attorneys, process experts, statisticians and linguists work closely with our clients to help reduce cost, mitigate risk and maximize efficiency. -

No. 05-13990-B UNITED STATES
No. 05-13990-B UNITED STATES COURT OF APPEALS FOR THE ELEVENTH CIRCUIT THE NATIONAL FEDERATION OF THE BLIND, THE NATIONAL FEDERATION OF THE BLIND OF FLORIDA, KATHERYN DAVIS, JOHN DAVID TOWNSEND, CHAD BUCKINS, PETER CERULLO, AND RYAN MANN, Plaintiffs/Appellants v. VOLUSIA COUNTY, and ANN McFALL, as Supervisor of Elections of Volusia County, Defendants/Appellees APPEAL FROM THE UNITED STATES DISTRICT COURT MIDDLE DISTRICT OF FLORIDA AMICI CURIAE BRIEF OF ELECTRONIC FRONTIER FOUNDATION, HANDICAPPED ADULTS OF VOLUSIA COUNTY, VERIFIEDVOTING.ORG, COMPUTER PROFESSIONALS FOR SOCIAL RESPONSIBILITY, AND VOTERS UNITE! IN SUPPORT OF APPELLEES AND AFFIRMANCE Cindy A. Cohn Cal. Bar No. 145997 Electronic Frontier Foundation 454 Shotwell Street San Francisco, CA 94110 (415) 436-9333 (415) 436-9993 (fax) Attorneys for Amici Curiae UNITED STATES COURT OF APPEALS FOR THE ELEVENTH CIRCUIT THE NATIONAL FEDERATION OF THE BLIND, THE NATIONAL Docket No. 05-13990-B FEDERATION OF THE APPEAL BLIND OF FLORIDA, KATHERYN DAVIS, JOHN DAVID TOWNSEND, CHAD BUCKINS, PETER CERULLO, AND RYAN MANN, Plaintiffs/Appellants, v. VOLUSIA COUNTY, and ANN McFALL, as Supervisor of Elections of Volusia County, Defendants/Appellees. CERTIFICATE OF INTERESTED PERSONS AND CORPORATE DISCLOSURE STATEMENT Amici Curiae Electronic Frontier Foundation, Handicapped Adults of Volusia County, Verifiedvoting.Org, Computer Professionals For Social Responsibility, and Voters Unite! hereby disclose the following pursuant to FRAP 29-2 and FRAP 26.1: Judge The Honorable James I. Cohn, United States District Judge, United States District Court, Southern District of Florida C-1 of 3 Parties National Federation of the Blind, Plaintiff/Appellant National Federation of the Blind of Florida, Plaintiff/Appellant Katheryn Davis, Plaintiff/Appellant John David Townsend, Plaintiff/Appellant Chad Buckins, Plaintiff/Appellant Peter Cerullo, Plaintiff/Appellant Ryan Mann, Plaintiff/Appellant Attorneys Miguel de la O, Attorney for Plaintiffs-Appellants de la O & Marko, Attorney for Plaintiffs-Appellants Daniel F. -

Government Investigations and Controversies Key Legal and Communications Strategies for Nonprofits to Prepare for and Manage the Crisis
Government Investigations and Controversies Key Legal and Communications Strategies for Nonprofits to Prepare for and Manage the Crisis Wednesday, April 26, 2017, 12:30 pm – 2:00 pm ET Venable LLP, Washington, DC Moderator Jeffrey S. Tenenbaum, Esq. Partner and Chair of the Nonprofit Organizations Practice, Venable LLP Speakers Erik Jones, Esq. Partner, Investigations Practice, Venable LLP Alexandra Megaris, Esq. Counsel, Investigations Practice, Venable LLP Tracy Schmaler Managing Director, Crisis Communications, Litigation, and Issues Management Practices, Kivvit © 2017 Venable LLP Presentation Government Investigations and Controversies Key Legal and Communications Strategies for Nonprofits to Prepare for and Manage the Crisis Wednesday, April 26, 2017, 12:30 pm – 2:00 pm ET Venable LLP, Washington, DC Moderator Jeffrey S. Tenenbaum, Esq. Partner and Chair of the Nonprofit Organizations Practice, Venable LLP Speakers Erik Jones, Esq. Partner, Investigations Practice, Venable LLP Alexandra Megaris, Esq. Counsel, Investigations Practice, Venable LLP Tracy Schmaler Managing Director, Crisis Communications, Litigation, and Issues Management Practices, Kivvit © 2017 Venable LLP CAE Credit Information *Please note that CAE credit is available only to registered participants in the live program. As a CAE Approved Provider educational program related to the CAE exam content outline, this program may be applied for 1.5 credits toward your CAE application or professional development renewal requirements. Venable LLP is a CAE Approved Provider. This program meets the requirements for fulfilling the professional development requirements to earn or maintain the Certified Association Executive credential. Every program we offer that qualifies for CAE credit will clearly identify the number of CAE credits granted for full, live participation, and we will maintain records of your participation in accordance with CAE policies.