Why Approval Voting Is Unworkable in Contested Elections
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Critical Strategies Under Approval Voting: Who Gets Ruled in and Ruled Out
Critical Strategies Under Approval Voting: Who Gets Ruled In And Ruled Out Steven J. Brams Department of Politics New York University New York, NY 10003 USA [email protected] M. Remzi Sanver Department of Economics Istanbul Bilgi University 80310, Kustepe, Istanbul TURKEY [email protected] January 2005 2 Abstract We introduce the notion of a “critical strategy profile” under approval voting (AV), which facilitates the identification of all possible outcomes that can occur under AV. Included among AV outcomes are those given by scoring rules, single transferable vote, the majoritarian compromise, Condorcet systems, and others as well. Under each of these systems, a Condorcet winner may be upset through manipulation by individual voters or coalitions of voters, whereas AV ensures the election of a Condorcet winner as a strong Nash equilibrium wherein voters use sincere strategies. To be sure, AV may also elect Condorcet losers and other lesser candidates, sometimes in equilibrium. This multiplicity of (equilibrium) outcomes is the product of a social-choice framework that is more general than the standard preference-based one. From a normative perspective, we argue that voter judgments about candidate acceptability should take precedence over the usual social-choice criteria, such as electing a Condorcet or Borda winner. Keywords: approval voting; elections; Condorcet winner/loser; voting games; Nash equilibrium. Acknowledgments. We thank Eyal Baharad, Dan S. Felsenthal, Peter C. Fishburn, Shmuel Nitzan, Richard F. Potthoff, and Ismail Saglam for valuable suggestions. 3 1. Introduction Our thesis in this paper is that several outcomes of single-winner elections may be socially acceptable, depending on voters’ individual views on the acceptability of the candidates. -

Brake & Branscomb
Colorado Secretary of State 8/3/2021 Election Rulemaking These proposed edits to the SOS draft are contributed by Emily Brake (R) and Harvie Branscomb (D), and approved by Frank Atwood, Chair of the Approval Voting Party This document may be found on http://electionquality.com version 1.3 8/10/2021 15:50 Only portions of the recent draft rule text are included here with inline edits and comments highlighted as follows: Comments are highlighted in yellow. INSERTS ARE IN GREEN AND LARGE FONT deletions are in red and include strikeout Other indications of strikeout are from the original tabulation process 2.13.2 In accordance with section 1-2-605(7), C.R.S., no later than 90 days following a General Election, the county clerk in each county must SECRETARY OF STATE WILL PROPOSE cancelLATION OF the registrations of electors TO EACH COUNTY CLERK: [Comment: SOS taking responsibility from counties will lead to less verification and less resilience. The SOS office has not been subject to watcher access but will be as various steps of the conduct of election are taken over.] (a) Whose records have been marked “Inactive – returned mail”, “Inactive – undeliverable ballot”, or “Inactive – NCOA”; AND (b) Who have been mailed a confirmation card; and (c) Who have since THEREAFTER failed to vote in two consecutive general elections. New Rule 2.13.3, amendments to current Rule 2.13.3, repeal of 2.13.5, and necessary renumbering:VOTERS WHO REQUEST AN EMERGENCY BALLOT BE SENT TO THEM ELECTRONICALLY MUST BE DIRECTED BY THE COUNTY CLERK TO THE ONLINE BALLOT DELIVERY SYSTEM MAINTAINED BY THE SECRETARY OF STATE TO RECEIVE THEIR BALLOT ELECTRONICALLY. -

Influences in Voting and Growing Networks
UC Berkeley UC Berkeley Electronic Theses and Dissertations Title Influences in Voting and Growing Networks Permalink https://escholarship.org/uc/item/0fk1x7zx Author Racz, Miklos Zoltan Publication Date 2015 Peer reviewed|Thesis/dissertation eScholarship.org Powered by the California Digital Library University of California Influences in Voting and Growing Networks by Mikl´osZolt´anR´acz A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Statistics in the Graduate Division of the University of California, Berkeley Committee in charge: Professor Elchanan Mossel, Chair Professor James W. Pitman Professor Allan M. Sly Professor David S. Ahn Spring 2015 Influences in Voting and Growing Networks Copyright 2015 by Mikl´osZolt´anR´acz 1 Abstract Influences in Voting and Growing Networks by Mikl´osZolt´anR´acz Doctor of Philosophy in Statistics University of California, Berkeley Professor Elchanan Mossel, Chair This thesis studies problems in applied probability using combinatorial techniques. The first part of the thesis focuses on voting, and studies the average-case behavior of voting systems with respect to manipulation of their outcome by voters. Many results in the field of voting are negative; in particular, Gibbard and Satterthwaite showed that no reasonable voting system can be strategyproof (a.k.a. nonmanipulable). We prove a quantitative version of this result, showing that the probability of manipulation is nonnegligible, unless the voting system is close to being a dictatorship. We also study manipulation by a coalition of voters, and show that the transition from being powerless to having absolute power is smooth. These results suggest that manipulation is easy on average for reasonable voting systems, and thus computational complexity cannot hide manipulations completely. -

Are Condorcet and Minimax Voting Systems the Best?1
1 Are Condorcet and Minimax Voting Systems the Best?1 Richard B. Darlington Cornell University Abstract For decades, the minimax voting system was well known to experts on voting systems, but was not widely considered to be one of the best systems. But in recent years, two important experts, Nicolaus Tideman and Andrew Myers, have both recognized minimax as one of the best systems. I agree with that. This paper presents my own reasons for preferring minimax. The paper explicitly discusses about 20 systems. Comments invited. [email protected] Copyright Richard B. Darlington May be distributed free for non-commercial purposes Keywords Voting system Condorcet Minimax 1. Many thanks to Nicolaus Tideman, Andrew Myers, Sharon Weinberg, Eduardo Marchena, my wife Betsy Darlington, and my daughter Lois Darlington, all of whom contributed many valuable suggestions. 2 Table of Contents 1. Introduction and summary 3 2. The variety of voting systems 4 3. Some electoral criteria violated by minimax’s competitors 6 Monotonicity 7 Strategic voting 7 Completeness 7 Simplicity 8 Ease of voting 8 Resistance to vote-splitting and spoiling 8 Straddling 8 Condorcet consistency (CC) 8 4. Dismissing eight criteria violated by minimax 9 4.1 The absolute loser, Condorcet loser, and preference inversion criteria 9 4.2 Three anti-manipulation criteria 10 4.3 SCC/IIA 11 4.4 Multiple districts 12 5. Simulation studies on voting systems 13 5.1. Why our computer simulations use spatial models of voter behavior 13 5.2 Four computer simulations 15 5.2.1 Features and purposes of the studies 15 5.2.2 Further description of the studies 16 5.2.3 Results and discussion 18 6. -

MGF 1107 FINAL EXAM REVIEW CHAPTER 9 1. Amy (A), Betsy
MGF 1107 FINAL EXAM REVIEW CHAPTER 9 1. Amy (A), Betsy (B), Carla (C), Doris (D), and Emilia (E) are candidates for an open Student Government seat. There are 110 voters with the preference lists below. 36 24 20 18 8 4 A E D B C C B C E D E D C B C C B B D D B E D E E A A A A A Who wins the election if the method used is: a) plurality? b) plurality with runoff? c) sequential pairwise voting with agenda ABEDC? d) Hare system? e) Borda count? 2. What is the minimum number of votes needed for a majority if the number of votes cast is: a) 120? b) 141? 3. Consider the following preference lists: 1 1 1 A C B B A D D B C C D A If sequential pairwise voting and the agenda BACD is used, then D wins the election. Suppose the middle voter changes his mind and reverses his ranking of A and B. If the other two voters have unchanged preferences, B now wins using the same agenda BACD. This example shows that sequential pairwise voting fails to satisfy what desirable property of a voting system? 4. Consider the following preference lists held by 5 voters: 2 2 1 A B C C C B B A A First, note that if the plurality with runoff method is used, B wins. Next, note that C defeats both A and B in head-to-head matchups. This example shows that the plurality with runoff method fails to satisfy which desirable property of a voting system? 5. -

On the Distortion of Voting with Multiple Representative Candidates∗
The Thirty-Second AAAI Conference on Artificial Intelligence (AAAI-18) On the Distortion of Voting with Multiple Representative Candidates∗ Yu Cheng Shaddin Dughmi David Kempe Duke University University of Southern California University of Southern California Abstract voters and the chosen candidate in a suitable metric space (Anshelevich 2016; Anshelevich, Bhardwaj, and Postl 2015; We study positional voting rules when candidates and voters Anshelevich and Postl 2016; Goel, Krishnaswamy, and Mu- are embedded in a common metric space, and cardinal pref- erences are naturally given by distances in the metric space. nagala 2017). The underlying assumption is that the closer In a positional voting rule, each candidate receives a score a candidate is to a voter, the more similar their positions on from each ballot based on the ballot’s rank order; the candi- key questions are. Because proximity implies that the voter date with the highest total score wins the election. The cost would benefit from the candidate’s election, voters will rank of a candidate is his sum of distances to all voters, and the candidates by increasing distance, a model known as single- distortion of an election is the ratio between the cost of the peaked preferences (Black 1948; Downs 1957; Black 1958; elected candidate and the cost of the optimum candidate. We Moulin 1980; Merrill and Grofman 1999; Barbera,` Gul, consider the case when candidates are representative of the and Stacchetti 1993; Richards, Richards, and McKay 1998; population, in the sense that they are drawn i.i.d. from the Barbera` 2001). population of the voters, and analyze the expected distortion Even in the absence of strategic voting, voting systems of positional voting rules. -
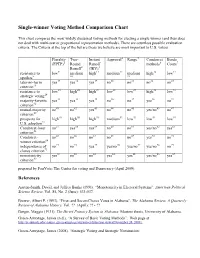
Single-Winner Voting Method Comparison Chart
Single-winner Voting Method Comparison Chart This chart compares the most widely discussed voting methods for electing a single winner (and thus does not deal with multi-seat or proportional representation methods). There are countless possible evaluation criteria. The Criteria at the top of the list are those we believe are most important to U.S. voters. Plurality Two- Instant Approval4 Range5 Condorcet Borda (FPTP)1 Round Runoff methods6 Count7 Runoff2 (IRV)3 resistance to low9 medium high11 medium12 medium high14 low15 spoilers8 10 13 later-no-harm yes17 yes18 yes19 no20 no21 no22 no23 criterion16 resistance to low25 high26 high27 low28 low29 high30 low31 strategic voting24 majority-favorite yes33 yes34 yes35 no36 no37 yes38 no39 criterion32 mutual-majority no41 no42 yes43 no44 no45 yes/no 46 no47 criterion40 prospects for high49 high50 high51 medium52 low53 low54 low55 U.S. adoption48 Condorcet-loser no57 yes58 yes59 no60 no61 yes/no 62 yes63 criterion56 Condorcet- no65 no66 no67 no68 no69 yes70 no71 winner criterion64 independence of no73 no74 yes75 yes/no 76 yes/no 77 yes/no 78 no79 clones criterion72 81 82 83 84 85 86 87 monotonicity yes no no yes yes yes/no yes criterion80 prepared by FairVote: The Center for voting and Democracy (April 2009). References Austen-Smith, David, and Jeffrey Banks (1991). “Monotonicity in Electoral Systems”. American Political Science Review, Vol. 85, No. 2 (June): 531-537. Brewer, Albert P. (1993). “First- and Secon-Choice Votes in Alabama”. The Alabama Review, A Quarterly Review of Alabama History, Vol. ?? (April): ?? - ?? Burgin, Maggie (1931). The Direct Primary System in Alabama. -

Approval Voting Under Dichotomous Preferences: a Catalogue of Characterizations
Draft – June 25, 2021 Approval Voting under Dichotomous Preferences: A Catalogue of Characterizations Florian Brandl Dominik Peters University of Bonn Harvard University [email protected] [email protected] Approval voting allows every voter to cast a ballot of approved alternatives and chooses the alternatives with the largest number of approvals. Due to its simplicity and superior theoretical properties it is a serious contender for use in real-world elections. We support this claim by giving eight characterizations of approval voting. All our results involve the reinforcement axiom, which requires choices to be consistent across different electorates. In addition, we consider strategyproofness, consistency with majority opinions, consistency under cloning alternatives, and invariance under removing inferior alternatives. We prove our results by reducing them to a single base theorem, for which we give a simple and intuitive proof. 1 Introduction Around the world, when electing a leader or a representative, plurality is by far the most common voting system: each voter casts a vote for a single candidate, and the candidate with the most votes is elected. In pioneering work, Brams and Fishburn (1983) proposed an alternative system: approval voting. Here, each voter may cast votes for an arbitrary number of candidates, and can thus choose whether to approve or disapprove of each candidate. The election is won by the candidate who is approved by the highest number of voters. Approval voting allows voters to be more expressive of their preferences, and it can avoid problems such as vote splitting, which are endemic to plurality voting. Together with its elegance and simplicity, this has made approval voting a favorite among voting theorists (Laslier, 2011), and has led to extensive research literature (Laslier and Sanver, 2010). -

Governance in Decentralized Networks
Governance in decentralized networks Risto Karjalainen* May 21, 2020 Abstract. Effective, legitimate and transparent governance is paramount for the long-term viability of decentralized networks. If the aim is to design such a governance model, it is useful to be aware of the history of decision making paradigms and the relevant previous research. Towards such ends, this paper is a survey of different governance models, the thinking behind such models, and new tools and structures which are made possible by decentralized blockchain technology. Governance mechanisms in the wider civil society are reviewed, including structures and processes in private and non-profit governance, open-source development, and self-managed organisations. The alternative ways to aggregate preferences, resolve conflicts, and manage resources in the decentralized space are explored, including the possibility of encoding governance rules as automatically executed computer programs where humans or other entities interact via a protocol. Keywords: Blockchain technology, decentralization, decentralized autonomous organizations, distributed ledger technology, governance, peer-to-peer networks, smart contracts. 1. Introduction This paper is a survey of governance models in decentralized networks, and specifically in networks which make use of blockchain technology. There are good reasons why governance in decentralized networks is a topic of considerable interest at present. Some of these reasons are ideological. We live in an era where detailed information about private individuals is being collected and traded, in many cases without the knowledge or consent of the individuals involved. Decentralized technology is seen as a tool which can help protect people against invasions of privacy. Decentralization can also be viewed as a reaction against the overreach by state and industry. -

Single Transferable Vote Resists Strategic Voting
Single Transferable Vote Resists Strategic Voting John J. Bartholdi, III School of Industrial and Systems Engineering Georgia Institute of Technology, Atlanta, GA 30332 James B. Orlin Sloan School of Management Massachusetts Institute of Technology, Cambridge, MA 02139 November 13, 1990; revised April 4, 2003 Abstract We give evidence that Single Tranferable Vote (STV) is computation- ally resistant to manipulation: It is NP-complete to determine whether there exists a (possibly insincere) preference that will elect a favored can- didate, even in an election for a single seat. Thus strategic voting under STV is qualitatively more difficult than under other commonly-used vot- ing schemes. Furthermore, this resistance to manipulation is inherent to STV and does not depend on hopeful extraneous assumptions like the presumed difficulty of learning the preferences of the other voters. We also prove that it is NP-complete to recognize when an STV elec- tion violates monotonicity. This suggests that non-monotonicity in STV elections might be perceived as less threatening since it is in effect “hid- den” and hard to exploit for strategic advantage. 1 1 Strategic voting For strategic voting the fundamental problem for any would-be manipulator is to decide what preference to claim. We will show that this modest task can be impractically difficult under the voting scheme known as Single Transferable Vote (STV). Furthermore this difficulty pertains even in the ideal situation in which the manipulator knows the preferences of all other voters and knows that they will vote their complete and sincere preferences. Thus STV is apparently unique among voting schemes in actual use today in that it is computationally resistant to manipulation. -

Ranked-Choice Voting from a Partisan Perspective
Ranked-Choice Voting From a Partisan Perspective Jack Santucci December 21, 2020 Revised December 22, 2020 Abstract Ranked-choice voting (RCV) has come to mean a range of electoral systems. Broadly, they can facilitate (a) majority winners in single-seat districts, (b) majority rule with minority representation in multi-seat districts, or (c) majority sweeps in multi-seat districts. Such systems can be combined with other rules that encourage/discourage slate voting. This paper describes five major versions used in U.S. public elections: Al- ternative Vote (AV), single transferable vote (STV), block-preferential voting (BPV), the bottoms-up system, and AV with numbered posts. It then considers each from the perspective of a `political operative.' Simple models of voting (one with two parties, another with three) draw attention to real-world strategic issues: effects on minority representation, importance of party cues, and reasons for the political operative to care about how voters rank choices. Unsurprisingly, different rules produce different outcomes with the same votes. Specific problems from the operative's perspective are: majority reversal, serving two masters, and undisciplined third-party voters (e.g., `pure' independents). Some of these stem from well-known phenomena, e.g., ballot exhaus- tion/ranking truncation and inter-coalition \vote leakage." The paper also alludes to vote-management tactics, i.e., rationing nominations and ensuring even distributions of first-choice votes. Illustrative examples come from American history and comparative politics. (209 words.) Keywords: Alternative Vote, ballot exhaustion, block-preferential voting, bottoms- up system, exhaustive-preferential system, instant runoff voting, ranked-choice voting, sequential ranked-choice voting, single transferable vote, strategic coordination (10 keywords). -

Democracy Lost: a Report on the Fatally Flawed 2016 Democratic Primaries
Democracy Lost: A Report on the Fatally Flawed 2016 Democratic Primaries Election Justice USA | ElectionJusticeUSA.org | [email protected] Table of Contents I. INTRODUCTORY MATERIAL........................................................................................................2 A. ABOUT ELECTION JUSTICE USA...............................................................................................2 B. EXECUTIVE SUMMARY...............................................................................................................2 C. ACKNOWLEDGEMENTS..............................................................................................................7 II. SUMMARY OF DIRECT EVIDENCE FOR ELECTION FRAUD, VOTER SUPPRESSION, AND OTHER IRREGULARITIES.......................................................................................................7 A. VOTER SUPPRESSION..................................................................................................................7 B. REGISTRATION TAMPERING......................................................................................................8 C. ILLEGAL VOTER PURGING.........................................................................................................8 D. EVIDENCE OF FRAUDULENT OR ERRONEOUS VOTING MACHINE TALLIES.................9 E. MISCELLANEOUS........................................................................................................................10 F. ESTIMATE OF PLEDGED DELEGATES AFFECTED................................................................11