Single Transferable Vote Resists Strategic Voting
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Case for Electoral Reform: a Mixed Member Proportional System
1 The Case for Electoral Reform: A Mixed Member Proportional System for Canada Brief by Stephen Phillips, Ph.D. Instructor, Department of Political Science, Langara College Vancouver, BC 6 October 2016 2 Summary: In this brief, I urge Parliament to replace our current Single-Member Plurality (SMP) system chiefly because of its tendency to distort the voting intentions of citizens in federal elections and, in particular, to magnify regional differences in the country. I recommend that SMP be replaced by a system of proportional representation, preferably a Mixed Member Proportional system (MMP) similar to that used in New Zealand and the Federal Republic of Germany. I contend that Parliament has the constitutional authority to enact an MMP system under Section 44 of the Constitution Act 1982; as such, it does not require the formal approval of the provinces. Finally, I argue that a national referendum on replacing the current SMP voting system is neither necessary nor desirable. However, to lend it political legitimacy, the adoption of a new electoral system should only be undertaken with the support of MPs from two or more parties that together won over 50% of the votes cast in the last federal election. Introduction Canada’s single-member plurality (SMP) electoral system is fatally flawed. It distorts the true will of Canadian voters, it magnifies regional differences in the country, and it vests excessive political power in the hands of manufactured majority governments, typically elected on a plurality of 40% or less of the popular vote. The adoption of a voting system based on proportional representation would not only address these problems but also improve the quality of democratic government and politics in general. -

Are Condorcet and Minimax Voting Systems the Best?1
1 Are Condorcet and Minimax Voting Systems the Best?1 Richard B. Darlington Cornell University Abstract For decades, the minimax voting system was well known to experts on voting systems, but was not widely considered to be one of the best systems. But in recent years, two important experts, Nicolaus Tideman and Andrew Myers, have both recognized minimax as one of the best systems. I agree with that. This paper presents my own reasons for preferring minimax. The paper explicitly discusses about 20 systems. Comments invited. [email protected] Copyright Richard B. Darlington May be distributed free for non-commercial purposes Keywords Voting system Condorcet Minimax 1. Many thanks to Nicolaus Tideman, Andrew Myers, Sharon Weinberg, Eduardo Marchena, my wife Betsy Darlington, and my daughter Lois Darlington, all of whom contributed many valuable suggestions. 2 Table of Contents 1. Introduction and summary 3 2. The variety of voting systems 4 3. Some electoral criteria violated by minimax’s competitors 6 Monotonicity 7 Strategic voting 7 Completeness 7 Simplicity 8 Ease of voting 8 Resistance to vote-splitting and spoiling 8 Straddling 8 Condorcet consistency (CC) 8 4. Dismissing eight criteria violated by minimax 9 4.1 The absolute loser, Condorcet loser, and preference inversion criteria 9 4.2 Three anti-manipulation criteria 10 4.3 SCC/IIA 11 4.4 Multiple districts 12 5. Simulation studies on voting systems 13 5.1. Why our computer simulations use spatial models of voter behavior 13 5.2 Four computer simulations 15 5.2.1 Features and purposes of the studies 15 5.2.2 Further description of the studies 16 5.2.3 Results and discussion 18 6. -
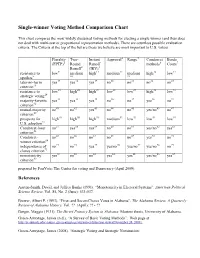
Single-Winner Voting Method Comparison Chart
Single-winner Voting Method Comparison Chart This chart compares the most widely discussed voting methods for electing a single winner (and thus does not deal with multi-seat or proportional representation methods). There are countless possible evaluation criteria. The Criteria at the top of the list are those we believe are most important to U.S. voters. Plurality Two- Instant Approval4 Range5 Condorcet Borda (FPTP)1 Round Runoff methods6 Count7 Runoff2 (IRV)3 resistance to low9 medium high11 medium12 medium high14 low15 spoilers8 10 13 later-no-harm yes17 yes18 yes19 no20 no21 no22 no23 criterion16 resistance to low25 high26 high27 low28 low29 high30 low31 strategic voting24 majority-favorite yes33 yes34 yes35 no36 no37 yes38 no39 criterion32 mutual-majority no41 no42 yes43 no44 no45 yes/no 46 no47 criterion40 prospects for high49 high50 high51 medium52 low53 low54 low55 U.S. adoption48 Condorcet-loser no57 yes58 yes59 no60 no61 yes/no 62 yes63 criterion56 Condorcet- no65 no66 no67 no68 no69 yes70 no71 winner criterion64 independence of no73 no74 yes75 yes/no 76 yes/no 77 yes/no 78 no79 clones criterion72 81 82 83 84 85 86 87 monotonicity yes no no yes yes yes/no yes criterion80 prepared by FairVote: The Center for voting and Democracy (April 2009). References Austen-Smith, David, and Jeffrey Banks (1991). “Monotonicity in Electoral Systems”. American Political Science Review, Vol. 85, No. 2 (June): 531-537. Brewer, Albert P. (1993). “First- and Secon-Choice Votes in Alabama”. The Alabama Review, A Quarterly Review of Alabama History, Vol. ?? (April): ?? - ?? Burgin, Maggie (1931). The Direct Primary System in Alabama. -

Legislature by Lot: Envisioning Sortition Within a Bicameral System
PASXXX10.1177/0032329218789886Politics & SocietyGastil and Wright 789886research-article2018 Special Issue Article Politics & Society 2018, Vol. 46(3) 303 –330 Legislature by Lot: Envisioning © The Author(s) 2018 Article reuse guidelines: Sortition within a Bicameral sagepub.com/journals-permissions https://doi.org/10.1177/0032329218789886DOI: 10.1177/0032329218789886 System* journals.sagepub.com/home/pas John Gastil Pennsylvania State University Erik Olin Wright University of Wisconsin–Madison Abstract In this article, we review the intrinsic democratic flaws in electoral representation, lay out a set of principles that should guide the construction of a sortition chamber, and argue for the virtue of a bicameral system that combines sortition and elections. We show how sortition could prove inclusive, give citizens greater control of the political agenda, and make their participation more deliberative and influential. We consider various design challenges, such as the sampling method, legislative training, and deliberative procedures. We explain why pairing sortition with an elected chamber could enhance its virtues while dampening its potential vices. In our conclusion, we identify ideal settings for experimenting with sortition. Keywords bicameral legislatures, deliberation, democratic theory, elections, minipublics, participation, political equality, sortition Corresponding Author: John Gastil, Department of Communication Arts & Sciences, Pennsylvania State University, 232 Sparks Bldg., University Park, PA 16802, USA. Email: [email protected] *This special issue of Politics & Society titled “Legislature by Lot: Transformative Designs for Deliberative Governance” features a preface, an introductory anchor essay and postscript, and six articles that were presented as part of a workshop held at the University of Wisconsin–Madison, September 2017, organized by John Gastil and Erik Olin Wright. -

14 Facts Abouty Voting in Federal Elections
U.S. Election Assistance Commission FACTS About Voting in Federal Elections From registering to vote through casting a ballot on election day, informed voters are empowered voters. Here are 14 answers to 14 common questions from citizens about voting in Federal elections. Voter’s Checklist— Am I Eligible In Person Things To Do Before Election Day 1 To Vote? Apply to register to vote at— ■ Confirm you are registered to vote several State or local voter registration You are eligible to vote if— ■ weeks before election day. or election offices. You are a U.S. citizen. ■ Update your registration if your address, ■ ■ The department of motor name, or political affil iation has changed. ■ You meet your State’s residen vehicles. cy requirements. ■ Know how and when to apply for an absentee ■ Public assistance agencies. You are 18 years old. Some ballot if you are unable to vote at your polling ■ Armed services recruitment States allow 17-year-olds to ■ place on election day. centers. vote in primaries and/or reg ■ Know your options for early voting. ister to vote if they will be 18 ■ State-funded programs that before the general election. serve people with disabilities. ■ Know the voter identification requirements in your State. ■ Any public facility that a State has designated as a voter ■ Know your polling place and how to get there. How Do I Register registration agency. 2 To Vote? ■ Familiarize yourself with the voting device Online used in your jurisdic tion. Learn how the device You may choose to apply for is accessible to voters with disabilities. -
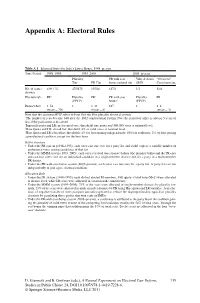
Appendix A: Electoral Rules
Appendix A: Electoral Rules Table A.1 Electoral Rules for Italy’s Lower House, 1948–present Time Period 1948–1993 1993–2005 2005–present Plurality PR with seat Valle d’Aosta “Overseas” Tier PR Tier bonus national tier SMD Constituencies No. of seats / 6301 / 32 475/475 155/26 617/1 1/1 12/4 districts Election rule PR2 Plurality PR3 PR with seat Plurality PR (FPTP) bonus4 (FPTP) District Size 1–54 1 1–11 617 1 1–6 (mean = 20) (mean = 6) (mean = 4) Note that the acronym FPTP refers to First Past the Post plurality electoral system. 1The number of seats became 630 after the 1962 constitutional reform. Note the period of office is always 5 years or less if the parliament is dissolved. 2Imperiali quota and LR; preferential vote; threshold: one quota and 300,000 votes at national level. 3Hare Quota and LR; closed list; threshold: 4% of valid votes at national level. 4Hare Quota and LR; closed list; thresholds: 4% for lists running independently; 10% for coalitions; 2% for lists joining a pre-electoral coalition, except for the best loser. Ballot structure • Under the PR system (1948–1993), each voter cast one vote for a party list and could express a variable number of preferential votes among candidates of that list. • Under the MMM system (1993–2005), each voter received two separate ballots (the plurality ballot and the PR one) and cast two votes: one for an individual candidate in a single-member district; one for a party in a multi-member PR district. • Under the PR-with-seat-bonus system (2005–present), each voter cast one vote for a party list. -

Canvasser's Manual
STV MESSAGE TESTING: CANVASSER’S MANUAL CONTENTS 1 INTRODUCTION ....................................................................................................................................... 2 1.1 BACKGROUND ........................................................................................................................................... 2 1.2 CASELOAD SUMMARY ................................................................................................................................. 2 1.3 CONTACTS ................................................................................................................................................ 2 2 THE “TREATMENTS” ................................................................................................................................ 3 2.1 THE MESSAGES .......................................................................................................................................... 3 2.2 THE ENDORSERS ........................................................................................................................................ 4 2.3 THE PLACEBO TREATMENT ........................................................................................................................... 4 3 DAILY DOCUMENTS ................................................................................................................................. 5 3.1 DAILY SHEETS ........................................................................................................................................... -

Another Consideration in Minority Vote Dilution Remedies: Rent
Another C onsideration in Minority Vote Dilution Remedies : Rent -Seeking ALAN LOCKARD St. Lawrence University In some areas of the United States, racial and ethnic minorities have been effectively excluded from the democratic process by a variety of means, including electoral laws. In some instances, the Courts have sought to remedy this problem by imposing alternative voting methods, such as cumulative voting. I examine several voting methods with regard to their sensitivity to rent-seeking. Methods which are less sensitive to rent-seeking are preferred because they involve less social waste, and are less likely to be co- opted by special interest groups. I find that proportional representation methods, rather than semi- proportional ones, such as cumulative voting, are relatively insensitive to rent-seeking efforts, and thus preferable. I also suggest that an even less sensitive method, the proportional lottery, may be appropriate for use within deliberative bodies, where proportional representation is inapplicable and minority vote dilution otherwise remains an intractable problem. 1. INTRODUCTION When President Clinton nominated Lani Guinier to serve in the Justice Department as Assistant Attorney General for Civil Rights, an opportunity was created for an extremely valuable public debate on the merits of alternative voting methods as solutions to vote dilution problems in the United States. After Prof. Guinier’s positions were grossly mischaracterized in the press,1 the President withdrew her nomination without permitting such a public debate to take place.2 These issues have been discussed in academic circles,3 however, 1 Bolick (1993) charges Guinier with advocating “a complex racial spoils system.” 2 Guinier (1998) recounts her experiences in this process. -

Report 2020:14
Report Swedish National Election Studies Department of Political Science University of Gothenburg 2020:14 2020.12.15 www.gu.se/en/snes Exploring split ticket voting motives Sara Persson Valforskningsprogrammets rapportserie Sedan 1950-talet genomför forskare knutna till Valforskningsprogrammet i Göteborg empiriska undersökningar av hur den svenska demokratin mår och utvecklas. Rapport- serien är vår viktigaste publikationskanal för att bidra till samhällets kunskapsförsörj- ning på demokratiområdet. Målsättningen är att sprida grundläggande fakta och forsk- ningsresultat som rör val och väljarbeteende till en bred publik av forskare, studenter, journalister, politiker och allmänhet. SNES Program Report Series Since the 1950s, the researchers associated with the Swedish National Election Studies Program at the Department of Political Science, University of Gothenburg, conducts empirical research on the well-being and development of the Swedish democracy. The Report Series is one of our main publication outlets. The aim is to publish basic facts and research results about elections and voting behaviour to a broad audience of researchers, students, journalists, politicians and the public. Citation: Persson, Sara (2020). Exploring split ticket voting motives. Swedish National Election Studies Program Report Series 2020:14. University of Gothenburg, Department of Political Science. Editor of the SNES Program Report Series: Henrik Ekengren Oscarsson Exploring split ticket voting motives SARA PERSSON Department of Political Science University of Gothenburg Abstract Split ticket voting is becoming increasingly common in most political systems. Tenden- cies to split votes has grown steadily during the last decades (Dalton, 2014: 197). Split ticket voting refers to the act of splitting one’s vote on several candidates or parties in elections and can occur in two different ways: by the division of votes to several, equivalent offices (horizontal voting) or to multiple levels of government (vertical voting) (Burden & Helmke, 2009:2). -

If You Like the Alternative Vote (Aka the Instant Runoff)
Electoral Studies 23 (2004) 641–659 www.elsevier.com/locate/electstud If you like the alternative vote (a.k.a. the instant runoff), then you ought to know about the Coombs rule Bernard Grofman a,Ã, Scott L. Feld b a Department of Political Science and Institute for Mathematical Behavioral Science, University of California, Irvine, CA 92697-5100, USA b Department of Sociology, Louisiana State University,Baton Rouge, LA 70803, USA Received 1 July2003 Abstract We consider four factors relevant to picking a voting rule to be used to select a single candidate from among a set of choices: (1) avoidance of Condorcet losers, (2) choice of Condorcet winners, (3) resistance to manipulabilityvia strategic voting, (4) simplicity. However, we do not tryto evaluate all voting rules that might be used to select a single alternative. Rather, our focus is restricted to a comparison between a rule which, under the name ‘instant runoff,’ has recentlybeen pushed byelectoral reformers in the US to replace plurality-based elections, and which has been advocated for use in plural societies as a means of mitigating ethnic conflict; and another similar rule, the ‘Coombs rule.’ In both rules, voters are required to rank order candidates. Using the instant runoff, the candidate with the fewest first place votes is eliminated; while under the Coombs rule, the candidate with the most last place votes is eliminated. The instant runoff is familiar to electoral sys- tem specialists under the name ‘alternative vote’ (i.e., the single transferable vote restricted to choice of a single candidate). The Coombs rule has gone virtuallyunmentioned in the electoral systems literature (see, however, Chamberlin et al., 1984). -

The Many Faces of Strategic Voting
Revised Pages The Many Faces of Strategic Voting Strategic voting is classically defined as voting for one’s second pre- ferred option to prevent one’s least preferred option from winning when one’s first preference has no chance. Voters want their votes to be effective, and casting a ballot that will have no influence on an election is undesirable. Thus, some voters cast strategic ballots when they decide that doing so is useful. This edited volume includes case studies of strategic voting behavior in Israel, Germany, Japan, Belgium, Spain, Switzerland, Canada, and the United Kingdom, providing a conceptual framework for understanding strategic voting behavior in all types of electoral systems. The classic definition explicitly considers strategic voting in a single race with at least three candidates and a single winner. This situation is more com- mon in electoral systems that have single- member districts that employ plurality or majoritarian electoral rules and have multiparty systems. Indeed, much of the literature on strategic voting to date has considered elections in Canada and the United Kingdom. This book contributes to a more general understanding of strategic voting behavior by tak- ing into account a wide variety of institutional contexts, such as single transferable vote rules, proportional representation, two- round elec- tions, and mixed electoral systems. Laura B. Stephenson is Professor of Political Science at the University of Western Ontario. John Aldrich is Pfizer- Pratt University Professor of Political Science at Duke University. André Blais is Professor of Political Science at the Université de Montréal. Revised Pages Revised Pages THE MANY FACES OF STRATEGIC VOTING Tactical Behavior in Electoral Systems Around the World Edited by Laura B. -

Political Knowledge and the Paradox of Voting
Political Knowledge and the Paradox of Voting Edited by Sofia Magdalena Olofsson We have long known that Americans pay local elections less attention than they do elections for the Presidency and Congress. A recent Portland State University study showed that voter turnout in ten of America’s 30 largest cities sits on average at less than 15% of eligible voters. Just pause and think about this. The 55% of voting age citizens who cast a ballot in last year’s presidential election – already a two-decade low and a significant drop from the longer-term average of 65-80% – still eclipses by far the voter turnout at recent mayoral elections in Dallas (6%), Fort Worth (6%), and Las Vegas (9%). What is more, data tells us that local voter turnout is only getting worse. Look at America’s largest city: New York. Since the 1953 New York election, when 93% of residents voted, the city’s mayoral contests saw a steady decline, with a mere 14% of the city’s residents voting in the last election. Though few might want to admit it, these trends suggest that an unspoken hierarchy exists when it comes to elections. Atop this electoral hierarchy are national elections, elections that are widely considered the most politically, economically, and culturally significant. Extensively covered by the media, they are viewed as high-stakes moral contests that naturally attract the greatest public interest. Next, come state elections: though still important compared to national elections, their political prominence, media coverage, and voter turnout is already waning. At the bottom of this electoral hierarchy are local elections that, as data tells us, a vast majority of Americans now choose not to vote in.