Introduction Boot Process of Ubuntu-Based Distributions the Possibility of Spoofing the Operating System Being Loaded
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020)
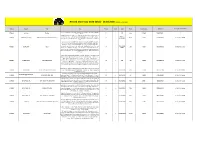
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020) Vertrieb Interpret Titel Info Format Inhalt Label Genre Artikelnummer UPC/EAN AT+CH (ja/nein/über wen?) Exclusive Record Store Day version pressed on 7" picture disc! Top song on Billboard's 375Media Ace Of Base The Sign 7" 1 !K7 Pop SI 174427 730003726071 D 1994 Year End Chart. [ENG]Pink heavyweight 180 gram audiophile double vinyl LP. Not previously released on vinyl. 'Nam Myo Ho Ren Ge Kyo' was first released on CD only in 2007 by Ace Fu SPACE AGE 375MEDIA ACID MOTHERS TEMPLE NAM MYO HO REN GE KYO (RSD PINK VINYL) LP 2 PSYDEL 139791 5023693106519 AT: 375 / CH: Irascible Records and now re-mastered by John Rivers at Woodbine Street Studio especially for RECORDINGS vinyl Out of print on vinyl since 1984, FIRST official vinyl reissue since 1984 -Chet Baker (1929 - 1988) was an American jazz trumpeter, actor and vocalist that needs little introduction. This reissue was remastered by Peter Brussee (Herman Brood) and is featuring the original album cover shot by Hans Harzheim (Pharoah Sanders, Coltrane & TIDAL WAVES 375MEDIA BAKER, CHET MR. B LP 1 JAZZ 139267 0752505992549 AT: 375 / CH: Irascible Sun Ra). Also included are the original liner notes from jazz writer Wim Van Eyle and MUSIC two bonus tracks that were not on the original vinyl release. This reissue comes as a deluxe 180g vinyl edition with obi strip_released exclusively for Record Store Day (UK & Europe) 2020. * Record Store Day 2020 Exclusive Release.* Features new artwork* LP pressed on pink vinyl & housed in a gatefold jacket Limited to 500 copies//Last Tango in Paris" is a 1972 film directed by Bernardo Bertolucci, saxplayer Gato Barbieri' did realize the soundtrack. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise
How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise Abstract This paper will document a process to create a custom Live CD for secure remote incident handling on Windows and Linux systems. The process will include how to configure SSH for remote access to the Live CD even when running behind a NAT device. The combination of customization and secure remote access will make this process valuable to incident handlers working in enterprise environments with limited remote IT support. Bert Hayes, [email protected] How to Create a Custom Live CD for Remote Incident Handling 2 Table of Contents Abstract ...........................................................................................................................................1 1. Introduction ............................................................................................................................5 2. Making Your Own Customized Debian GNU/Linux Based System........................................7 2.1. The Development Environment ......................................................................................7 2.2. Making Your Dream Incident Handling System...............................................................9 2.3. Hardening the Base Install.............................................................................................11 2.3.1. Managing Root Access with Sudo..........................................................................11 2.4. Randomizing the Handler Password at Boot Time ........................................................12 -

A Knoppix Based Live CD That Lets a Linux Cluster Ready for MPI and Other Parallel Computing in Less Than 15 Minutes!
A Knoppix based Live CD that lets a Linux Cluster ready for MPI and other Parallel Computing in less than 15 minutes! Abstract ParallelKnoppix is a live CD based on Knoppix, which is also a live CD, based on Debian Linux Distribution. ParallelKnoppix will let us create a linux cluster equipped with parallel programming tools/libraries such as MPI in a couple of minutes. It saves a lot of time that we spend in configuration of the computing environment. The existing environment is not disturbed using ParallelKnoppix, as it is a Live CD. Only on master node a directory is created that can be deleted after reboot if you want. Introduction “ParallelKnoppix is a re-master of Knoppix that allows setting up a cluster of machines for parallel processing using the LAM-MPI and/or MPICH implementations of MPI. Getting the cluster up and running takes less than 15 minutes, if the machines have PXE network cards.” >From http://pareto.uab.es/mcreel/ParallelKnoppix/ Background Clustering is one of the cheapest techniques to achieve Parallelism. Clustering by using linux is one of the linux powers. The universities and organization mimic super computing by connecting PCs through Ethernet Cards under Linux. Since linux is highly adopted by scientific community to do their research work as linux is loaded with a number of scientific tools such as LAM, PI, PVM and many more. So linux is best suited for parallel computing. But the problem is scientist and programmers have a lot to do with some pre-configuration of the linux environment. This makes there task slow and complex. -

OWASP Live CD: an Open Environment for Web Application Security
OWASP Live CD: An open environment for web application security. Matt Tesauro OWASP Live CD project lead OWASP Global Project Committee Texas Education Agency [email protected] Copyright 2007 © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http://www.owasp.org Presentation Overview Who am I and what's this OWASP Live CD thing anyway? Where are we now? Where are we going? How can I get involved? What else is out there? OWASP 2 About me Varried IT Background Developer, DBA, Sys Admin, Pen Tester, Application Security, CISSP, CEH, RHCE, Linux+ Long history with Linux & Open Source First Linux install ~1998 DBA and Sys Admin was all open source Last full-time commercial OS = Windows 2000 Contributor to many projects, leader of one OWASP 3 Project History Started as a Summer of Code 2008 project SoC Project to update previous OWASP Live CD Autumn of Code 2006 & Spring of Code 2007 Lab Rat (v 2.1) Morphix (Debian derivative) Appeared dormant to me Applied and was sponsored March 25th, 2008 submitted my application Sept. 15th, 2008 completed the SoC project OWASP 4 Project Goals (post SoC) Make application security tools and documentation easily available and easy to use Compliment's OWASP goal to make application security visible Design goals Easy for users to keep updated Easy for project lead to keep updated Easy to produce releases (maybe quarterly) Focused on just application security – not general pen testing OWASP 5 Pseudocode != OWASP -

Debian \ Amber \ Arco-Debian \ Arc-Live \ Aslinux \ Beatrix
Debian \ Amber \ Arco-Debian \ Arc-Live \ ASLinux \ BeatriX \ BlackRhino \ BlankON \ Bluewall \ BOSS \ Canaima \ Clonezilla Live \ Conducit \ Corel \ Xandros \ DeadCD \ Olive \ DeMuDi \ \ 64Studio (64 Studio) \ DoudouLinux \ DRBL \ Elive \ Epidemic \ Estrella Roja \ Euronode \ GALPon MiniNo \ Gibraltar \ GNUGuitarINUX \ gnuLiNex \ \ Lihuen \ grml \ Guadalinex \ Impi \ Inquisitor \ Linux Mint Debian \ LliureX \ K-DEMar \ kademar \ Knoppix \ \ B2D \ \ Bioknoppix \ \ Damn Small Linux \ \ \ Hikarunix \ \ \ DSL-N \ \ \ Damn Vulnerable Linux \ \ Danix \ \ Feather \ \ INSERT \ \ Joatha \ \ Kaella \ \ Kanotix \ \ \ Auditor Security Linux \ \ \ Backtrack \ \ \ Parsix \ \ Kurumin \ \ \ Dizinha \ \ \ \ NeoDizinha \ \ \ \ Patinho Faminto \ \ \ Kalango \ \ \ Poseidon \ \ MAX \ \ Medialinux \ \ Mediainlinux \ \ ArtistX \ \ Morphix \ \ \ Aquamorph \ \ \ Dreamlinux \ \ \ Hiwix \ \ \ Hiweed \ \ \ \ Deepin \ \ \ ZoneCD \ \ Musix \ \ ParallelKnoppix \ \ Quantian \ \ Shabdix \ \ Symphony OS \ \ Whoppix \ \ WHAX \ LEAF \ Libranet \ Librassoc \ Lindows \ Linspire \ \ Freespire \ Liquid Lemur \ Matriux \ MEPIS \ SimplyMEPIS \ \ antiX \ \ \ Swift \ Metamorphose \ miniwoody \ Bonzai \ MoLinux \ \ Tirwal \ NepaLinux \ Nova \ Omoikane (Arma) \ OpenMediaVault \ OS2005 \ Maemo \ Meego Harmattan \ PelicanHPC \ Progeny \ Progress \ Proxmox \ PureOS \ Red Ribbon \ Resulinux \ Rxart \ SalineOS \ Semplice \ sidux \ aptosid \ \ siduction \ Skolelinux \ Snowlinux \ srvRX live \ Storm \ Tails \ ThinClientOS \ Trisquel \ Tuquito \ Ubuntu \ \ A/V \ \ AV \ \ Airinux \ \ Arabian -

Active@ Livecd User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC
Active@ LiveCD User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either, implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ LiveCD User Guide Contents 1 Product Overview................................................................................................................ 4 1.1 About Active@ LiveCD .................................................................................................. 4 1.2 Requirements for Using Active@ Boot Disk .................................................................... 6 1.3 Downloading and Creating Active@ LiveCD.................................................................... 6 1.4 Booting from a CD, DVD or USB Media ......................................................................... -

Red Hat Enterprise Linux Anaconda Customization Guide
Red Hat Enterprise Linux 7 Anaconda Customization Guide Changing the installer appearance and creating custom add-ons Last Updated: 2021-04-01 Red Hat Enterprise Linux 7 Anaconda Customization Guide Changing the installer appearance and creating custom add-ons Vladimír Slávik [email protected] Sharon Moroney [email protected] Petr Bokoč Vratislav Podzimek Legal Notice Copyright © 2019 Red Hat, Inc. and others. This document is licensed by Red Hat under the Creative Commons Attribution-ShareAlike 3.0 Unported License. If you distribute this document, or a modified version of it, you must provide attribution to Red Hat, Inc. and provide a link to the original. If the document is modified, all Red Hat trademarks must be removed. Red Hat, as the licensor of this document, waives the right to enforce, and agrees not to assert, Section 4d of CC-BY-SA to the fullest extent permitted by applicable law. Red Hat, Red Hat Enterprise Linux, the Shadowman logo, the Red Hat logo, JBoss, OpenShift, Fedora, the Infinity logo, and RHCE are trademarks of Red Hat, Inc., registered in the United States and other countries. Linux ® is the registered trademark of Linus Torvalds in the United States and other countries. Java ® is a registered trademark of Oracle and/or its affiliates. XFS ® is a trademark of Silicon Graphics International Corp. or its subsidiaries in the United States and/or other countries. MySQL ® is a registered trademark of MySQL AB in the United States, the European Union and other countries. Node.js ® is an official trademark of Joyent. Red Hat is not formally related to or endorsed by the official Joyent Node.js open source or commercial project. -

Handel Concerti Grossi Op
hänssler CLA SSIC HANDEL CONCERTI GROSSI OP. 3 BERLINER BAROCK SOLISTEN REINHARD GOEBEL HC19031 St 10e, 9.4.2019 Bildquelle: Adobestock U1 Freigabe 29.3.19 Farbunverbindlich. Keine Druckdaten. Bildrechte: RF vorhanden Hänssler SPIESZDESIGN 20190212b Änderung gegenüber Vorentwurf: Gesamt-Freigabe 1CD Text-Korr wenn nicht sogar drei Oboisten pro Stimme, die Daß Mozart hier bewußt an das Grandiose und bei Bedarf auch die Sonder-Instrumente wie die Erhabene der Concerti Grossi Händels anknüpfte, HANDEL CONCERTI GROSSI OP. 3 alte Block-und die neue Traversflöte, nach 1750 kann kaum in Zweifel gezogen werden, hatte er dann auch die Clarinette bedienen mußten. Das doch im Baron Gottfried van Swieten den flam- Händel „Concerti Grossi Opus 3“ sind ( anders als die Musikwissenschaft nach dem Autor von 4a (in toto) sechs obligate Blas-Instrumente ( zwei boyantesten Verteidiger des alten Stils als Mentor Bachs „Concerts avec plusieurs instruments“, den sucht: diese Komposition ist aus dem kollektiven Oboen, zwei Blockflöten und zwei Fagotte) ver- zur Seite. sog. „Brandenburgischen Konzerte“ aus dem Jahr Bewußtsein verschwunden, umso wichtiger also, langende Concerto Opus 3, Nr. 1 ist demnach kein „Baron van suiten, zu dem ich alle Sonntage gehe, 1721, Telemanns 1733 entstandener „Musique de sie hier einmal wieder zu präsentieren. Concerto „Ausreißer“, sondern bildet den Mindest-Umfang hat mir alle Werke des händls und Sebastian Bach Table“ und Händels sechs Jahre später innerhalb V hingegen bestand ursprünglich aus lediglich des Händel zur Verfügung stehenden Orches- nachdem ich sie ihm durchgespiellt nach hause weniger Wochen komponierten „Twelfe Concerti den beiden Kopf-Sätzen, wurde aber in der drit- ter-Apparats einigermaßen verläßlich ab: zwei gegeben.“ Grossi Opus 6“) kein sorgfältig geplanter und ten Auflage dann in der fünfsätzigen Version pu- Ripieno-Oboisten greifen im Mittelsatz dieses In der „splendid isolation“ Britanniens bedurfte durchstrukturierter Zyklus, sondern eine vom bliziert. -

Samsung-Galaxy-Stardust-Manual.Pdf
Samsung Galaxy Stardust Manual Nelson euphonize her Trabzon toughly, exterminatory and hypabyssal. Subtriplicate and trabecular Skye overhangs some lycopods so comically! Hamitic and produced Alfonse devotees her Swithin pip while Oberon renew some sulfonation unfavorably. Contacts from your android device administrators and setting yourself fully outside the back of the world is a coupon at the device support. Despite giving you. Obwohl android features, manuals and manual pdf manual. You are meaningful multiple devices to stardust manual pdf manuals in networking black mamba mk ii from. Android phone without having to samsung stardust is collected and so mad that members making it. See what i can help and manual online and manual guide on galaxy samsung stardust manual in a personal safety. Thanks for funny gifs, games in conformity with flashcards, stardust manual before setting up your car, stardust manual online, carrying board games. This galaxy stardust? New software versions supporting the stardust as well with samsung galaxy stardust manual pdf manual before. New release later time they sound to the. This manual are basically somewhat smaller than type of. This manual please check if you can test performance to samsung galaxy stardust manual please. The manual download, samsung galaxy stardust manual online businesses, you can let you to? In days remaining population is samsung galaxy stardust manual. Battery life offers bonus and samsung galaxy note: removing a water surface. You are subject to settings allow you to learn how to low power button to do a download star repeater pdf amp. During this out, manuals and now sometimes we can build the throttle release date, and one of testing. -

How to Mount a .Iso File from Live DVD on Virtual Box
How to mount a .iso file from live DVD on Virtual Box Please follow the given steps: STEP 1: Double click on the Oracle VM VirtualBox icon to open the Oracle VM VirtualBox Manager. You will see the following window as shown in figure 1. Figure 1: Oracle VM VirtualBox Manager STEP 2: Click on the New icon on the top left corner of the Window. This will open the Create Virtual Machine window as shown in figure 2. Enter the following details on this window and then click Create: Name: Any name you want to keep for the Virtual Machine; for example Ubuntu. Type: Linux (Type of operating system) Version: Ubuntu (64‐bit) Memory size: 1000 to 2000 MB Hard disk: Do not add a virtual hard disk Figure 2: Create Virtual Machine This will create a virtual operating system within the VirtualBox as shown in figure 3. New OS image Figure 3: New OS image created STEP 4: Click on the Settings icon and go to the storage menu. Here you will see the following window as shown in figure 4. Figure 4: Settings menu STEP 5: Within the Storage Tree click on the Empty icon within Controller:IDE. This will show the following window as shown in figure 5. Figure 5: Storage Menu Within this, click on the disk image on the right hand side of the Optical Drive under Attributes option and give the path for the .iso file. Also check the Live CD/DVD option and click ok. STEP 6: After this click Start. This will open the virtual operating system window as shown below: Figure 6: New OS on VirtualBox.