Automated Deploy for Chrome OS Testing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux and Electronics
Linux and Electronics Urs Lindegger Linux and Electronics Urs Lindegger Copyright © 2019-11-25 Urs Lindegger Table of Contents 1. Introduction .......................................................................................................... 1 Note ................................................................................................................ 1 2. Printed Circuits ...................................................................................................... 2 Printed Circuit Board design ................................................................................ 2 Kicad ....................................................................................................... 2 Eagle ..................................................................................................... 13 Simulation ...................................................................................................... 13 Spice ..................................................................................................... 13 Digital simulation .................................................................................... 18 Wings 3D ....................................................................................................... 18 User interface .......................................................................................... 19 Modeling ................................................................................................ 19 Making holes in Wings 3D ....................................................................... -

Open Source Used in Influx1.8 Influx 1.9
Open Source Used In Influx1.8 Influx 1.9 Cisco Systems, Inc. www.cisco.com Cisco has more than 200 offices worldwide. Addresses, phone numbers, and fax numbers are listed on the Cisco website at www.cisco.com/go/offices. Text Part Number: 78EE117C99-1178791953 Open Source Used In Influx1.8 Influx 1.9 1 This document contains licenses and notices for open source software used in this product. With respect to the free/open source software listed in this document, if you have any questions or wish to receive a copy of any source code to which you may be entitled under the applicable free/open source license(s) (such as the GNU Lesser/General Public License), please contact us at [email protected]. In your requests please include the following reference number 78EE117C99-1178791953 Contents 1.1 golang-protobuf-extensions v1.0.1 1.1.1 Available under license 1.2 prometheus-client v0.2.0 1.2.1 Available under license 1.3 gopkg.in-asn1-ber v1.0.0-20170511165959-379148ca0225 1.3.1 Available under license 1.4 influxdata-raft-boltdb v0.0.0-20210323121340-465fcd3eb4d8 1.4.1 Available under license 1.5 fwd v1.1.1 1.5.1 Available under license 1.6 jaeger-client-go v2.23.0+incompatible 1.6.1 Available under license 1.7 golang-genproto v0.0.0-20210122163508-8081c04a3579 1.7.1 Available under license 1.8 influxdata-roaring v0.4.13-0.20180809181101-fc520f41fab6 1.8.1 Available under license 1.9 influxdata-flux v0.113.0 1.9.1 Available under license 1.10 apache-arrow-go-arrow v0.0.0-20200923215132-ac86123a3f01 1.10.1 Available under -
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -

Oracle Solaris: the Carrier-Grade Operating System Technical Brief
An Oracle White Paper February 2011 Oracle Solaris: The Carrier-Grade Operating System Oracle White Paper—Oracle Solaris: The Carrier-Grade OS Executive Summary.............................................................................1 ® Powering Communication—The Oracle Solaris Ecosystem..............3 Integrated and Optimized Stack ......................................................5 End-to-End Security ........................................................................5 Unparalleled Performance and Scalability.......................................6 Increased Reliability ........................................................................7 Unmatched Flexibility ......................................................................7 SCOPE Alliance ..............................................................................7 Security................................................................................................8 Security Hardening and Monitoring .................................................8 Process and User Rights Management...........................................9 Network Security and Encrypted Communications .......................10 Virtualization ......................................................................................13 Oracle VM Server for SPARC .......................................................13 Oracle Solaris Zones .....................................................................14 Virtualized Networking...................................................................15 -

Buildbot Documentation Release 1.6.0
Buildbot Documentation Release 1.6.0 Brian Warner Nov 17, 2018 Contents 1 Buildbot Tutorial 3 1.1 First Run.................................................3 1.2 First Buildbot run with Docker......................................6 1.3 A Quick Tour...............................................9 1.4 Further Reading............................................. 17 2 Buildbot Manual 23 2.1 Introduction............................................... 23 2.2 Installation................................................ 29 2.3 Concepts................................................. 41 2.4 Secret Management........................................... 50 2.5 Configuration............................................... 53 2.6 Customization.............................................. 251 2.7 Command-line Tool........................................... 278 2.8 Resources................................................. 289 2.9 Optimization............................................... 289 2.10 Plugin Infrastructure in Buildbot..................................... 289 2.11 Deployment............................................... 290 2.12 Upgrading................................................ 292 3 Buildbot Development 305 3.1 Development Quick-start......................................... 305 3.2 General Documents........................................... 307 3.3 APIs................................................... 391 3.4 Python3 compatibility.......................................... 484 3.5 Classes................................................. -
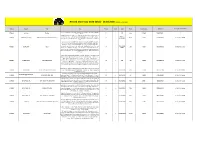
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020)
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020) Vertrieb Interpret Titel Info Format Inhalt Label Genre Artikelnummer UPC/EAN AT+CH (ja/nein/über wen?) Exclusive Record Store Day version pressed on 7" picture disc! Top song on Billboard's 375Media Ace Of Base The Sign 7" 1 !K7 Pop SI 174427 730003726071 D 1994 Year End Chart. [ENG]Pink heavyweight 180 gram audiophile double vinyl LP. Not previously released on vinyl. 'Nam Myo Ho Ren Ge Kyo' was first released on CD only in 2007 by Ace Fu SPACE AGE 375MEDIA ACID MOTHERS TEMPLE NAM MYO HO REN GE KYO (RSD PINK VINYL) LP 2 PSYDEL 139791 5023693106519 AT: 375 / CH: Irascible Records and now re-mastered by John Rivers at Woodbine Street Studio especially for RECORDINGS vinyl Out of print on vinyl since 1984, FIRST official vinyl reissue since 1984 -Chet Baker (1929 - 1988) was an American jazz trumpeter, actor and vocalist that needs little introduction. This reissue was remastered by Peter Brussee (Herman Brood) and is featuring the original album cover shot by Hans Harzheim (Pharoah Sanders, Coltrane & TIDAL WAVES 375MEDIA BAKER, CHET MR. B LP 1 JAZZ 139267 0752505992549 AT: 375 / CH: Irascible Sun Ra). Also included are the original liner notes from jazz writer Wim Van Eyle and MUSIC two bonus tracks that were not on the original vinyl release. This reissue comes as a deluxe 180g vinyl edition with obi strip_released exclusively for Record Store Day (UK & Europe) 2020. * Record Store Day 2020 Exclusive Release.* Features new artwork* LP pressed on pink vinyl & housed in a gatefold jacket Limited to 500 copies//Last Tango in Paris" is a 1972 film directed by Bernardo Bertolucci, saxplayer Gato Barbieri' did realize the soundtrack. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

Preview Dart Programming Tutorial
Dart Programming About the Tutorial Dart is an open-source general-purpose programming language. It is originally developed by Google and later approved as a standard by ECMA. Dart is a new programming language meant for the server as well as the browser. Introduced by Google, the Dart SDK ships with its compiler – the Dart VM. The SDK also includes a utility -dart2js, a transpiler that generates JavaScript equivalent of a Dart Script. This tutorial provides a basic level understanding of the Dart programming language. Audience This tutorial will be quite helpful for all those developers who want to develop single-page web applications using Dart. It is meant for programmers with a strong hold on object- oriented concepts. Prerequisites The tutorial assumes that the readers have adequate exposure to object-oriented programming concepts. If you have worked on JavaScript, then it will help you further to grasp the concepts of Dart quickly. Copyright & Disclaimer © Copyright 2017 by Tutorials Point (I) Pvt. Ltd. All the content and graphics published in this e-book are the property of Tutorials Point (I) Pvt. Ltd. The user of this e-book is prohibited to reuse, retain, copy, distribute or republish any contents or a part of contents of this e-book in any manner without written consent of the publisher. We strive to update the contents of our website and tutorials as timely and as precisely as possible, however, the contents may contain inaccuracies or errors. Tutorials Point (I) Pvt. Ltd. provides no guarantee regarding the accuracy, timeliness or completeness of our website or its contents including this tutorial. -

What Is Dart?
1 Dart in Action By Chris Buckett As a language on its own, Dart might be just another language, but when you take into account the whole Dart ecosystem, Dart represents an exciting prospect in the world of web development. In this green paper based on Dart in Action, author Chris Buckett explains how Dart, with its ability to either run natively or be converted to JavaScript and coupled with HTML5 is an ideal solution for building web applications that do not need external plugins to provide all the features. You may also be interested in… What is Dart? The quick answer to the question of what Dart is that it is an open-source structured programming language for creating complex browser based web applications. You can run applications created in Dart by either using a browser that directly supports Dart code, or by converting your Dart code to JavaScript (which happens seamlessly). It is class based, optionally typed, and single threaded (but supports multiple threads through a mechanism called isolates) and has a familiar syntax. In addition to running in browsers, you can also run Dart code on the server, hosted in the Dart virtual machine. The language itself is very similar to Java, C#, and JavaScript. One of the primary goals of the Dart developers is that the language seems familiar. This is a tiny dart script: main() { #A var d = “Dart”; #B String w = “World”; #C print(“Hello ${d} ${w}”); #D } #A Single entry point function main() executes when the script is fully loaded #B Optional typing (no type specified) #C Static typing (String type specified) #D Outputs “Hello Dart World” to the browser console or stdout This script can be embedded within <script type=“application/dart”> tags and run in the Dartium experimental browser, converted to JavaScript using the Frog tool and run in all modern browsers, or saved to a .dart file and run directly on the server using the dart virtual machine executable. -

Google Security Chip H1 a Member of the Titan Family
Google Security Chip H1 A member of the Titan family Chrome OS Use Case [email protected] Block diagram ● ARM SC300 core ● 8kB boot ROM, 64kB SRAM, 512kB Flash ● USB 1.1 slave controller (USB2.0 FS) ● I2C master and slave controllers ● SPI master and slave controllers ● 3 UART channels ● 32 GPIO ports, 28 muxed pins ● 2 Timers ● Reset and power control (RBOX) ● Crypto Engine ● HW Random Number Generator ● RD Detection Flash Memory Layout ● Bootrom not shown ● Flash space split in two halves for redundancy ● Restricted access INFO space ● Header fields control boot flow ● Code is in Chrome OS EC repo*, ○ board files in board/cr50 ○ chip files in chip/g *https://chromium.googlesource.com/chromiumos/platform/ec Image Properties Chip Properties 512 byte space Used as 128 FW Updates INFO Space Bits 128 Bits Bitmap 32 Bit words Board ID 32 Bit words Bitmap Board ID ● Updates over USB or TPM Board ID Board ID ~ Board ID ● Rollback protections Board ID mask Version Board Flags ○ Header versioning scheme Board Flags ○ Flash map bitmap ● Board ID and flags Epoch ● RO public key in ROM Major ● RW public key in RO Minor ● Both ROM and RO allow for Timestamp node locked signatures Major Functions ● Guaranteed Reset ● Battery cutoff ● Closed Case Debugging * ● Verified Boot (TPM Services) ● Support of various security features * https://www.chromium.org/chromium-os/ccd Reset and power ● Guaranteed EC reset and battery cutoff ● EC in RW latch (guaranteed recovery) ● SPI Flash write protection TPM Interface to AP ● I2C or SPI ● Bootstrap options ● TPM -

Introduction to Unix
Introduction to Unix Rob Funk <[email protected]> University Technology Services Workstation Support http://wks.uts.ohio-state.edu/ University Technology Services Course Objectives • basic background in Unix structure • knowledge of getting started • directory navigation and control • file maintenance and display commands • shells • Unix features • text processing University Technology Services Course Objectives Useful commands • working with files • system resources • printing • vi editor University Technology Services In the Introduction to UNIX document 3 • shell programming • Unix command summary tables • short Unix bibliography (also see web site) We will not, however, be covering these topics in the lecture. Numbers on slides indicate page number in book. University Technology Services History of Unix 7–8 1960s multics project (MIT, GE, AT&T) 1970s AT&T Bell Labs 1970s/80s UC Berkeley 1980s DOS imitated many Unix ideas Commercial Unix fragmentation GNU Project 1990s Linux now Unix is widespread and available from many sources, both free and commercial University Technology Services Unix Systems 7–8 SunOS/Solaris Sun Microsystems Digital Unix (Tru64) Digital/Compaq HP-UX Hewlett Packard Irix SGI UNICOS Cray NetBSD, FreeBSD UC Berkeley / the Net Linux Linus Torvalds / the Net University Technology Services Unix Philosophy • Multiuser / Multitasking • Toolbox approach • Flexibility / Freedom • Conciseness • Everything is a file • File system has places, processes have life • Designed by programmers for programmers University Technology Services -

Gerrit J.J. Van Den Burg, Phd London, UK | Email: [email protected] | Web: Gertjanvandenburg.Com
Gerrit J.J. van den Burg, PhD London, UK | Email: [email protected] | Web: gertjanvandenburg.com Summary I am a research scientist with a PhD in machine learning and 8+ years of experience in academic research. I am currently looking to transition to industry to work on complex, large-scale problems that can have a positive real-world impact. I have extensive experience with machine learning modeling, algorithm design, and software engineering in Python, C, and R. My goal is to use my expertise and technical skills to address ongoing research challenges in machine learning and AI. Research Experience Postdoctoral Researcher — The Alan Turing Institute, UK 2018–2021 • Introduced a memorization score for probabilistic deep generative models and showed that neural networks can remember part of their input data, which has important implications for data privacy • Created a method for structure detection in textual data files that improved on the Python builtin method by 21%. Developed this into a Python package that has received over 600,000 downloads • Developed a robust Bayesian matrix factorization algorithm for time series modeling and forecasting that improved imputation error up to 60% while maintaining competitive runtime • Established the first benchmark dataset for change point detection on general real-world time series and determined the best performing methods, with consequences for research and practice • Collaborated with other researchers to design a unified interface for AI-powered data cleaning tools Doctoral Researcher