Open Source Software and Live Linux Cds: Elements of Successful Lab Modules
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Linux on a Stick Everyone Knows You Can Boot Linux from a Live CD, but Have You Thought About Putting Linux on a Compact and Highly Portable USB
KNOW HOW Memory Stick Linux Booting Linux from a USB Memory Stick Linux on a Stick Everyone knows you can boot Linux from a live CD, but have you thought about putting Linux on a compact and highly portable USB memory stick? BY FABRIZIO CIACCHI bootable “live” CD like Knoppix much more common. Part of our pur- ent from DSL, but it includes more [1] or Kanotix [2] gives the user a pose is to create an inexpensive system, software (about 14 MB plus), and it Afully portable operating environ- so I will base this discussion on the stan- has already been refined and tested for ment. You can carry your system with dard and very common 128 MB size. USB devices. you and boot it from anywhere. However, the procedure I describe in this • Flonix [8]: Flonix is also based on Your tools, your files, and your work- article can also be used to put a larger DSL, but it uses some different pro- space will follow you wherever you go – Knoppix-based distribution on a larger grams (for instance, IceWM instead even to another PC with a different USB memory stick. of Fluxbox). The Flonix project also operating system. Live CDs are also used Assuming you want room to work and introduced a useful web install by system administrators for trouble- store documents, it is a good idea to only process. Ultimately, Flonix was so shooting computers that won’t boot use half of the available space (64 MB) successful that it become a commer- normally. for the Linux system and related tools. -
Backbox Penetration Testing Never Looked So Lovely
DISTROHOPPER DISTROHOPPER Our pick of the latest releases will whet your appetite for new Linux distributions. Picaros Diego Linux for children. here are a few distributions aimed at children: Doudou springs to mind, Tand there’s also Sugar on a Stick. Both of these are based on the idea that you need to protect children from the complexities of the computer (and protect the computer from the children). Picaros Diego is different. There’s nothing stripped- down or shielded from view. Instead, it’s a normal Linux distro with a brighter, more kid-friendly interface. The desktop wallpaper perhaps best We were too busy playing Secret Mario on Picaros Diego to write a witty or interesting caption. exemplifies this. On one hand, it’s a colourful cartoon image designed to interest young file manager. In the programming category, little young for a system like this, but the it children. Some of the images on the we were slightly disappointed to discover it may well work for children on the upper end landscape are icons for games, and this only had Gambas (a Visual Basic-like of that age range. should encourage children to investigate the language), and not more popular teaching Overall, we like the philosophy of wrapping system rather than just relying on menus. languages like Scratch or a Python IDE. Linux is a child-friendly package, but not On the other hand, it still displays technical However, it’s based on Debian, so you do dumbing it down. Picaros Diego won’t work details such as the CPU usage and the RAM have the full range of software available for every child, but if you have a budding and Swap availability. -
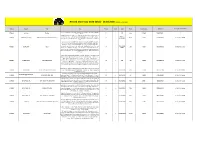
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020)
Record Store Day 2020 (GSA) - 18.04.2020 | (Stand: 05.03.2020) Vertrieb Interpret Titel Info Format Inhalt Label Genre Artikelnummer UPC/EAN AT+CH (ja/nein/über wen?) Exclusive Record Store Day version pressed on 7" picture disc! Top song on Billboard's 375Media Ace Of Base The Sign 7" 1 !K7 Pop SI 174427 730003726071 D 1994 Year End Chart. [ENG]Pink heavyweight 180 gram audiophile double vinyl LP. Not previously released on vinyl. 'Nam Myo Ho Ren Ge Kyo' was first released on CD only in 2007 by Ace Fu SPACE AGE 375MEDIA ACID MOTHERS TEMPLE NAM MYO HO REN GE KYO (RSD PINK VINYL) LP 2 PSYDEL 139791 5023693106519 AT: 375 / CH: Irascible Records and now re-mastered by John Rivers at Woodbine Street Studio especially for RECORDINGS vinyl Out of print on vinyl since 1984, FIRST official vinyl reissue since 1984 -Chet Baker (1929 - 1988) was an American jazz trumpeter, actor and vocalist that needs little introduction. This reissue was remastered by Peter Brussee (Herman Brood) and is featuring the original album cover shot by Hans Harzheim (Pharoah Sanders, Coltrane & TIDAL WAVES 375MEDIA BAKER, CHET MR. B LP 1 JAZZ 139267 0752505992549 AT: 375 / CH: Irascible Sun Ra). Also included are the original liner notes from jazz writer Wim Van Eyle and MUSIC two bonus tracks that were not on the original vinyl release. This reissue comes as a deluxe 180g vinyl edition with obi strip_released exclusively for Record Store Day (UK & Europe) 2020. * Record Store Day 2020 Exclusive Release.* Features new artwork* LP pressed on pink vinyl & housed in a gatefold jacket Limited to 500 copies//Last Tango in Paris" is a 1972 film directed by Bernardo Bertolucci, saxplayer Gato Barbieri' did realize the soundtrack. -

Chapter 3. Booting Operating Systems
Chapter 3. Booting Operating Systems Abstract: Chapter 3 provides a complete coverage on operating systems booting. It explains the booting principle and the booting sequence of various kinds of bootable devices. These include booting from floppy disk, hard disk, CDROM and USB drives. Instead of writing a customized booter to boot up only MTX, it shows how to develop booter programs to boot up real operating systems, such as Linux, from a variety of bootable devices. In particular, it shows how to boot up generic Linux bzImage kernels with initial ramdisk support. It is shown that the hard disk and CDROM booters developed in this book are comparable to GRUB and isolinux in performance. In addition, it demonstrates the booter programs by sample systems. 3.1. Booting Booting, which is short for bootstrap, refers to the process of loading an operating system image into computer memory and starting up the operating system. As such, it is the first step to run an operating system. Despite its importance and widespread interests among computer users, the subject of booting is rarely discussed in operating system books. Information on booting are usually scattered and, in most cases, incomplete. A systematic treatment of the booting process has been lacking. The purpose of this chapter is to try to fill this void. In this chapter, we shall discuss the booting principle and show how to write booter programs to boot up real operating systems. As one might expect, the booting process is highly machine dependent. To be more specific, we shall only consider the booting process of Intel x86 based PCs. -

How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise
How to Create a Custom Live CD for Secure Remote Incident Handling in the Enterprise Abstract This paper will document a process to create a custom Live CD for secure remote incident handling on Windows and Linux systems. The process will include how to configure SSH for remote access to the Live CD even when running behind a NAT device. The combination of customization and secure remote access will make this process valuable to incident handlers working in enterprise environments with limited remote IT support. Bert Hayes, [email protected] How to Create a Custom Live CD for Remote Incident Handling 2 Table of Contents Abstract ...........................................................................................................................................1 1. Introduction ............................................................................................................................5 2. Making Your Own Customized Debian GNU/Linux Based System........................................7 2.1. The Development Environment ......................................................................................7 2.2. Making Your Dream Incident Handling System...............................................................9 2.3. Hardening the Base Install.............................................................................................11 2.3.1. Managing Root Access with Sudo..........................................................................11 2.4. Randomizing the Handler Password at Boot Time ........................................................12 -

Lightweight Distros on Test
GROUP TEST LIGHTWEIGHT DISTROS LIGHTWEIGHT DISTROS GROUP TEST Mayank Sharma is on the lookout for distros tailor made to infuse life into his ageing computers. On Test Lightweight distros here has always been a some text editing, and watch some Linux Lite demand for lightweight videos. These users don’t need URL www.linuxliteos.com Talternatives both for the latest multi-core machines VERSION 2.0 individual apps and for complete loaded with several gigabytes of DESKTOP Xfce distributions. But the recent advent RAM or even a dedicated graphics Does the second version of the distro of feature-rich resource-hungry card. However, chances are their does enough to justify its title? software has reinvigorated efforts hardware isn’t supported by the to put those old, otherwise obsolete latest kernel, which keeps dropping WattOS machines to good use. support for older hardware that is URL www.planetwatt.com For a long time the primary no longer in vogue, such as dial-up VERSION R8 migrators to Linux were people modems. Back in 2012, support DESKTOP LXDE, Mate, Openbox who had fallen prey to the easily for the i386 chip was dropped from Has switching the base distro from exploitable nature of proprietary the kernel and some distros, like Ubuntu to Debian made any difference? operating systems. Of late though CentOS, have gone one step ahead we’re getting a whole new set of and dropped support for the 32-bit SparkyLinux users who come along with their architecture entirely. healthy and functional computers URL www.sparkylinux.org that just can’t power the newer VERSION 3.5 New life DESKTOP LXDE, Mate, Xfce and others release of Windows. -

A Knoppix Based Live CD That Lets a Linux Cluster Ready for MPI and Other Parallel Computing in Less Than 15 Minutes!
A Knoppix based Live CD that lets a Linux Cluster ready for MPI and other Parallel Computing in less than 15 minutes! Abstract ParallelKnoppix is a live CD based on Knoppix, which is also a live CD, based on Debian Linux Distribution. ParallelKnoppix will let us create a linux cluster equipped with parallel programming tools/libraries such as MPI in a couple of minutes. It saves a lot of time that we spend in configuration of the computing environment. The existing environment is not disturbed using ParallelKnoppix, as it is a Live CD. Only on master node a directory is created that can be deleted after reboot if you want. Introduction “ParallelKnoppix is a re-master of Knoppix that allows setting up a cluster of machines for parallel processing using the LAM-MPI and/or MPICH implementations of MPI. Getting the cluster up and running takes less than 15 minutes, if the machines have PXE network cards.” >From http://pareto.uab.es/mcreel/ParallelKnoppix/ Background Clustering is one of the cheapest techniques to achieve Parallelism. Clustering by using linux is one of the linux powers. The universities and organization mimic super computing by connecting PCs through Ethernet Cards under Linux. Since linux is highly adopted by scientific community to do their research work as linux is loaded with a number of scientific tools such as LAM, PI, PVM and many more. So linux is best suited for parallel computing. But the problem is scientist and programmers have a lot to do with some pre-configuration of the linux environment. This makes there task slow and complex. -

Introduction to Linux
Presentation to U3A - Linux Introduction 8 June 2019 – Terry Schuster - [email protected] What is Linux? https://en.wikipedia.org/wiki/Linux https://www.iotforall.com/linux-operating-system-iot-devices/ In simple terms, Linux is an operating system which was developed to be a home-built version of UNIX, one of the first operating systems which could be run on different brands of mainframe computers with quite different types of hardware. Linux has developed to the extent that it is the leading operating system on servers and other big iron systems such as mainframe computers, and the only OS used on TOP500 supercomputers (since November 2017, having gradually eliminated all competitors). It is used by around 2.3 percent of desktop computers. The Chromebook, which runs the Linux kernel-based Chrome OS, dominates the US K–12 education market. In the mid 2000’s, Linux was quickly seen as a good building block for smartphones, as it provided an out- of-the-box modern, full-featured Operating System with very good device driver support, and that was considered both scalable for the new generation of devices and had the added benefit of being royalty free. It is now becoming very common in IoT devices, such as smart watches/refrigerators, home controllers, etc. etc. BTW, Tux is a penguin character and the official brand character of the Linux kernel. Originally created as an entry to a Linux logo competition, Tux is the most commonly used icon for Linux, although different Linux distributions depict Tux in various styles. The character is used in many other Linux programs and as a general symbol of Linux. -

Introduction to Fmxlinux Delphi's Firemonkey For
Introduction to FmxLinux Delphi’s FireMonkey for Linux Solution Jim McKeeth Embarcadero Technologies [email protected] Chief Developer Advocate & Engineer For quality purposes, all lines except the presenter are muted IT’S OK TO ASK QUESTIONS! Use the Q&A Panel on the Right This webinar is being recorded for future playback. Recordings will be available on Embarcadero’s YouTube channel Your Presenter: Jim McKeeth Embarcadero Technologies [email protected] | @JimMcKeeth Chief Developer Advocate & Engineer Agenda • Overview • Installation • Supported platforms • PAServer • SDK & Packages • Usage • UI Elements • Samples • Database Access FireDAC • Migrating from Windows VCL • midaconverter.com • 3rd Party Support • Broadway Web Why FMX on Linux? • Education - Save money on Windows licenses • Kiosk or Point of Sale - Single purpose computers with locked down user interfaces • Security - Linux offers more security options • IoT & Industrial Automation - Add user interfaces for integrated systems • Federal Government - Many govt systems require Linux support • Choice - Now you can, so might as well! Delphi for Linux History • 1999 Kylix: aka Delphi for Linux, introduced • It was a port of the IDE to Linux • Linux x86 32-bit compiler • Used the Trolltech QT widget library • 2002 Kylix 3 was the last update to Kylix • 2017 Delphi 10.2 “Tokyo” introduced Delphi for x86 64-bit Linux • IDE runs on Windows, cross compiles to Linux via the PAServer • Designed for server side development - no desktop widget GUI library • 2017 Eugene -

OWASP Live CD: an Open Environment for Web Application Security
OWASP Live CD: An open environment for web application security. Matt Tesauro OWASP Live CD project lead OWASP Global Project Committee Texas Education Agency [email protected] Copyright 2007 © The OWASP Foundation Permission is granted to copy, distribute and/or modify this document under the terms of the OWASP License. The OWASP Foundation http://www.owasp.org Presentation Overview Who am I and what's this OWASP Live CD thing anyway? Where are we now? Where are we going? How can I get involved? What else is out there? OWASP 2 About me Varried IT Background Developer, DBA, Sys Admin, Pen Tester, Application Security, CISSP, CEH, RHCE, Linux+ Long history with Linux & Open Source First Linux install ~1998 DBA and Sys Admin was all open source Last full-time commercial OS = Windows 2000 Contributor to many projects, leader of one OWASP 3 Project History Started as a Summer of Code 2008 project SoC Project to update previous OWASP Live CD Autumn of Code 2006 & Spring of Code 2007 Lab Rat (v 2.1) Morphix (Debian derivative) Appeared dormant to me Applied and was sponsored March 25th, 2008 submitted my application Sept. 15th, 2008 completed the SoC project OWASP 4 Project Goals (post SoC) Make application security tools and documentation easily available and easy to use Compliment's OWASP goal to make application security visible Design goals Easy for users to keep updated Easy for project lead to keep updated Easy to produce releases (maybe quarterly) Focused on just application security – not general pen testing OWASP 5 Pseudocode != OWASP -

Debian \ Amber \ Arco-Debian \ Arc-Live \ Aslinux \ Beatrix
Debian \ Amber \ Arco-Debian \ Arc-Live \ ASLinux \ BeatriX \ BlackRhino \ BlankON \ Bluewall \ BOSS \ Canaima \ Clonezilla Live \ Conducit \ Corel \ Xandros \ DeadCD \ Olive \ DeMuDi \ \ 64Studio (64 Studio) \ DoudouLinux \ DRBL \ Elive \ Epidemic \ Estrella Roja \ Euronode \ GALPon MiniNo \ Gibraltar \ GNUGuitarINUX \ gnuLiNex \ \ Lihuen \ grml \ Guadalinex \ Impi \ Inquisitor \ Linux Mint Debian \ LliureX \ K-DEMar \ kademar \ Knoppix \ \ B2D \ \ Bioknoppix \ \ Damn Small Linux \ \ \ Hikarunix \ \ \ DSL-N \ \ \ Damn Vulnerable Linux \ \ Danix \ \ Feather \ \ INSERT \ \ Joatha \ \ Kaella \ \ Kanotix \ \ \ Auditor Security Linux \ \ \ Backtrack \ \ \ Parsix \ \ Kurumin \ \ \ Dizinha \ \ \ \ NeoDizinha \ \ \ \ Patinho Faminto \ \ \ Kalango \ \ \ Poseidon \ \ MAX \ \ Medialinux \ \ Mediainlinux \ \ ArtistX \ \ Morphix \ \ \ Aquamorph \ \ \ Dreamlinux \ \ \ Hiwix \ \ \ Hiweed \ \ \ \ Deepin \ \ \ ZoneCD \ \ Musix \ \ ParallelKnoppix \ \ Quantian \ \ Shabdix \ \ Symphony OS \ \ Whoppix \ \ WHAX \ LEAF \ Libranet \ Librassoc \ Lindows \ Linspire \ \ Freespire \ Liquid Lemur \ Matriux \ MEPIS \ SimplyMEPIS \ \ antiX \ \ \ Swift \ Metamorphose \ miniwoody \ Bonzai \ MoLinux \ \ Tirwal \ NepaLinux \ Nova \ Omoikane (Arma) \ OpenMediaVault \ OS2005 \ Maemo \ Meego Harmattan \ PelicanHPC \ Progeny \ Progress \ Proxmox \ PureOS \ Red Ribbon \ Resulinux \ Rxart \ SalineOS \ Semplice \ sidux \ aptosid \ \ siduction \ Skolelinux \ Snowlinux \ srvRX live \ Storm \ Tails \ ThinClientOS \ Trisquel \ Tuquito \ Ubuntu \ \ A/V \ \ AV \ \ Airinux \ \ Arabian -

Active@ Livecd User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC
Active@ LiveCD User Guide Copyright © 1999-2015, LSOFT TECHNOLOGIES INC. All rights reserved. No part of this documentation may be reproduced in any form or by any means or used to make any derivative work (such as translation, transformation, or adaptation) without written permission from LSOFT TECHNOLOGIES INC. LSOFT TECHNOLOGIES INC. reserves the right to revise this documentation and to make changes in content from time to time without obligation on the part of LSOFT TECHNOLOGIES INC. to provide notification of such revision or change. LSOFT TECHNOLOGIES INC. provides this documentation without warranty of any kind, either, implied or expressed, including, but not limited to, the implied warranties of merchantability and fitness for a particular purpose. LSOFT may make improvements or changes in the product(s) and/or the program(s) described in this documentation at any time. All technical data and computer software is commercial in nature and developed solely at private expense. As the User, or Installer/Administrator of this software, you agree not to remove or deface any portion of any legend provided on any licensed program or documentation contained in, or delivered to you in conjunction with, this User Guide. LSOFT.NET logo is a trademark of LSOFT TECHNOLOGIES INC. Other brand and product names may be registered trademarks or trademarks of their respective holders. 2 Active@ LiveCD User Guide Contents 1 Product Overview................................................................................................................ 4 1.1 About Active@ LiveCD .................................................................................................. 4 1.2 Requirements for Using Active@ Boot Disk .................................................................... 6 1.3 Downloading and Creating Active@ LiveCD.................................................................... 6 1.4 Booting from a CD, DVD or USB Media .........................................................................