The Enigma Encryption Machine and Its Electronic Variant
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Mathemathics of Secrets.Pdf
THE MATHEMATICS OF SECRETS THE MATHEMATICS OF SECRETS CRYPTOGRAPHY FROM CAESAR CIPHERS TO DIGITAL ENCRYPTION JOSHUA HOLDEN PRINCETON UNIVERSITY PRESS PRINCETON AND OXFORD Copyright c 2017 by Princeton University Press Published by Princeton University Press, 41 William Street, Princeton, New Jersey 08540 In the United Kingdom: Princeton University Press, 6 Oxford Street, Woodstock, Oxfordshire OX20 1TR press.princeton.edu Jacket image courtesy of Shutterstock; design by Lorraine Betz Doneker All Rights Reserved Library of Congress Cataloging-in-Publication Data Names: Holden, Joshua, 1970– author. Title: The mathematics of secrets : cryptography from Caesar ciphers to digital encryption / Joshua Holden. Description: Princeton : Princeton University Press, [2017] | Includes bibliographical references and index. Identifiers: LCCN 2016014840 | ISBN 9780691141756 (hardcover : alk. paper) Subjects: LCSH: Cryptography—Mathematics. | Ciphers. | Computer security. Classification: LCC Z103 .H664 2017 | DDC 005.8/2—dc23 LC record available at https://lccn.loc.gov/2016014840 British Library Cataloging-in-Publication Data is available This book has been composed in Linux Libertine Printed on acid-free paper. ∞ Printed in the United States of America 13579108642 To Lana and Richard for their love and support CONTENTS Preface xi Acknowledgments xiii Introduction to Ciphers and Substitution 1 1.1 Alice and Bob and Carl and Julius: Terminology and Caesar Cipher 1 1.2 The Key to the Matter: Generalizing the Caesar Cipher 4 1.3 Multiplicative Ciphers 6 -

Historical Ciphers Systems Top 10 Open Problems May 5, 2016 George Lasry [email protected] Open Problems - Criteria
Historical Ciphers Systems Top 10 Open Problems May 5, 2016 George Lasry [email protected] Open Problems - Criteria • Generic method vs. deciphering a document • System details are known – For many there are simulators • Published methods vs. classified • General vs. special case solutions – Ciphertext only vs. known plaintext – Single message vs. in-depth messages – Short vs. long messages – Long vs. short keys • Brute force not feasible – But computer most likely required George Lasry May 2016 2 Top 10 Open Problems 1. SIGABA 2. KL-7 3. Siemens T52D “Sturgeon” 4. Hagelin CX-52 5. Fialka 6. Lorenz SZ42 “Tunny” – Ψ1 limitation 7. Hagelin M-209 – short messages 8. Double Transposition – long random keys 9. Enigma – short message 10. Chaocipher – single message George Lasry May 2016 3 Problem 1: SIGABA (US) • Possible keys (WWII): 2 96 = 10 29 • Best published: known-plaintext 2 60 = 10 18 steps George Lasry May 2016 4 Problem 2: KL-7 (US) • Details of the machine known (+ simulator) • Best published cryptanalytic method: None! George Lasry May 2016 5 Problem 3: Siemens & Halske T52D • Successor of T52a/b/c: Irregular wheel stepping • Possible key settings: 2 73 = 10 24 • Best published method: > 5 messages in depth George Lasry May 2016 6 Problem 4: Hagelin CX-52 • Successor of C38/M209: Irregular wheel stepping • Possible key settings: 2 439 = 10 132 • Best published method: Known-plaintext George Lasry May 2016 7 Problem 5: Fialka M-125 (Russia) • Possible key settings: 2 250 = 10 75 • Best published method: None! George -

The the Enigma Enigma Machinemachine
TheThe EnigmaEnigma MachineMachine History of Computing December 6, 2006 Mike Koss Invention of Enigma ! Invented by Arthur Scherbius, 1918 ! Adopted by German Navy, 1926 ! Modified military version, 1930 ! Two Additional rotors added, 1938 How Enigma Works Scrambling Letters ! Each letter on the keyboard is connected to a lamp letter that depends on the wiring and position of the rotors in the machine. ! Right rotor turns before each letter. How to Use an Enigma ! Daily Setup – Secret settings distributed in code books. ! Encoding/Decoding a Message Setup: Select (3) Rotors ! We’ll use I-II-III Setup: Rotor Ring Settings ! We’ll use A-A-A (or 1-1-1). Rotor Construction Setup: Plugboard Settings ! We won’t use any for our example (6 to 10 plugs were typical). Setup: Initial Rotor Position ! We’ll use “M-I-T” (or 13-9-20). Encoding: Pick a “Message Key” ! Select a 3-letter key (or indicator) “at random” (left to the operator) for this message only. ! Say, I choose “M-C-K” (or 13-3-11 if wheels are printed with numbers rather than letters). Encoding: Transmit the Indicator ! Germans would transmit the indicator by encoding it using the initial (daily) rotor position…and they sent it TWICE to make sure it was received properly. ! E.g., I would begin my message with “MCK MCK”. ! Encoded with the daily setting, this becomes: “NWD SHE”. Encoding: Reset Rotors ! Now set our rotors do our chosen message key “M-C-K” (13-3-11). ! Type body of message: “ENIGMA REVEALED” encodes to “QMJIDO MZWZJFJR”. -

Thaumatotibia Leucotreta (Meyrick) (Lepidoptera: Tortricidae) Population Ecology in Citrus Orchards: the Influence of Orchard Age
Thaumatotibia leucotreta (Meyrick) (Lepidoptera: Tortricidae) population ecology in citrus orchards: the influence of orchard age Submitted in fulfilment of the requirements for the degree of DOCTOR OF PHILOSOPHY at RHODES UNIVERSITY by Sonnica Albertyn December 2017 ABSTRACT 1 Anecdotal reports in the South African citrus industry claim higher populations of false codling moth (FCM), Thaumatotibia (Cryptophlebia) leucotreta (Meyr) (Lepidoptera: Tortricidae), in orchards during the first three to five harvesting years of citrus planted in virgin soil, after which, FCM numbers seem to decrease and remain consistent. Various laboratory studies and field surveys were conducted to determine if, and why juvenile orchards (four to eight years old) experience higher FCM infestation than mature orchards (nine years and older). In laboratory trials, Washington Navel oranges and Nova Mandarins from juvenile trees were shown to be significantly more susceptible to FCM damage and significantly more attractive for oviposition in both choice and no-choice trials, than fruit from mature trees. Although fruit from juvenile Cambria Navel trees were significantly more attractive than mature orchards for oviposition, they were not more susceptible to FCM damage. In contrast, fruit from juvenile and mature Midnight Valencia orchards were equally attractive for oviposition, but fruit from juvenile trees were significantly more susceptible to FCM damage than fruit from mature trees. Artificial diets were augmented with powder from fruit from juvenile or mature Washington Navel orchards at 5%, 10%, 15% or 30%. Higher larval survival of 76%, 63%, 50% and 34%, respectively, was recorded on diets containing fruit powder from the juvenile trees than on diets containing fruit powder from the mature trees, at 69%, 57%, 44% and 27% larval survival, respectively. -
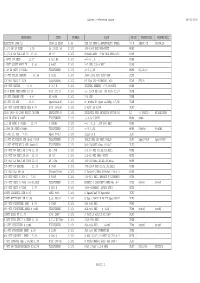
Subject Reference Dbase 09-05-2006
Subject reference dbase 09-05-2006 ONDERWERP TYPE NUMMER BIJZ GROEP TREFWOORD1 TREFWOORD2 ELECTRON 1958.12 1958.12 ELEC Z 46 TEK CX GEVR L,KWANTONETC KUBEL TS-N KERST CX LW,KW,LO 0,5/1 KW LW SEND 2.39 As 33/A1 34 Z 101 100-1000 KHZ MOB+FEST MOBS 0,7/1,4 KW SEND AS 60 10.40 AS 60 Z 101 FRUEHE AUSF 3-24 MHZ MOB+FEST MOBS 1 KWTT KW SEND 11.37 S 521 Bs Z 101 =+/-G 1,5.... MOBS 1 KWTT SHORT WAVE TR 5.36 S 486F Z 101 3-7 UND 2,5-6 MHZ MOBS 1 kW KW SEND S 521Bs TELEFUNKEN Z 172 +/-G 1,2K MOBS G1,2K+/- 10 WTT TELEF SENDER 10.34 S 318H Z 101 1500-3333 KHZ GUSS GEH SCHS 100 WTT SEND S 317H TELEFUNKEN Z 172 RS 31g 100-800METER alt SCHS S317H 100 WTT SENDER 4.33 S 317 H Z 101 UNIVERS SENDER 377-3000KHZ MOBS 15 W EINK SEND EMPF 10.35 Stat 272 B Z 101 +/- 15 W SE 469 SE 5285 F1/37 TRSE 15 WTT KARREN STN 4.40 SE 469A Z 101 3-5 MHZ TRSE 15 WTT KW STN 10.35 Spez804/445 Z 101 S= 804Bs E= Spez 445dBg 3-7,5M TRSE 150 WTT LANGW SENDE ANL 8.39 Stat 1006aF Z 101 S 427F SA 429F FLFU 1898-1938 40 JAAR RADIO IN NED SWIERSTRA R. Z 143 INLEGVEL VAN SWIERSTA PRIVE'38 LI 40 RADIO!! WILHELMINA 1kW KW SEND S 486F TELEFUNKEN Z 172 +/-2,5-7,5MHZ MOBS S486 1,5 LW SEND S 366Bs 11.37 S 366Bs Z 101 =+/- G1,5...100-600 KHZ MOBS 1,5kW LW SEND S366Bs TELEFUNKEN Z 172 +/-G 1,5L MOBS S366Bs S366BS 20 WTT FL STN 3.35 Spez 378mF Z 101 TELEF D B FLFU 20 WTT FLUGZEUG STN Spez 378nF TELEFUNKEN Z 172 URALT ANL LW FEST FREQU FLFU Spez378nF Spez378NF 20 WTT MITTELWELL GER Stat901 TELEFUNKEN Z 172 500-1500KHZ Stat 901A/F FLFU 200 WTT KW SEND AS 1008 11.39 AS 1008 Z 101 2,5-10 MHZ A1,A2,A3,HELL -

Enigma 2000 Newsletter
ENIGMA 2000 NEWSLETTER http://www.enigma2000.org.uk BAe Systems Type 101 Mobile Air Defence Radar System. A fully automatic system capable of firing devices without human intervention. Located in Kent Tnx Male Anon ISSUE 72 September 2012 http://www.enigma2000.org.uk 1 Editorial, Issue 72 Variable signals across the month of July; rapidly changeable weather leading to some peculiar conditions with QRN rearing its ugly head. To break this cycle we offer the cover story before our station round up. Cover pic story Olympics and the Aether Anon In case anyone is still unaware London is hosting the 2012 Olympics, in fact by the time you read this it will all be over. Among the preparations is the need to ensure sufficient radio frequencies are available to meet an unprecedented demand. As the world's media descend on East London there will be a need for a huge range of services from satellite links to mobile phones, Wi-Fi, 2-way radios, radio links and wireless microphones. The job of providing all this falls to the British regulator Ofcom. One of our members living close to London has stumbled across what may be a strange side effect of this process. As a monitor of all things radio he regularly scans the FM broadcast band, logging illegal "pirate" stations centred on the capital. For the past few years the band has been seemingly abandoned to the pirates, for Ofcom, once a proactive body, now only acts when an interference complaint is received. Many of the stations run twenty four-hours a day, seven days a week, with others adding to the mix at weekends. -

A Complete Bibliography of Publications in Cryptologia
A Complete Bibliography of Publications in Cryptologia Nelson H. F. Beebe University of Utah Department of Mathematics, 110 LCB 155 S 1400 E RM 233 Salt Lake City, UT 84112-0090 USA Tel: +1 801 581 5254 FAX: +1 801 581 4148 E-mail: [email protected], [email protected], [email protected] (Internet) WWW URL: http://www.math.utah.edu/~beebe/ 04 September 2021 Version 3.64 Title word cross-reference 10016-8810 [?, ?]. 1221 [?]. 125 [?]. 15.00/$23.60.0 [?]. 15th [?, ?]. 16th [?]. 17-18 [?]. 18 [?]. 180-4 [?]. 1812 [?]. 18th (t; m)[?]. (t; n)[?, ?]. $10.00 [?]. $12.00 [?, ?, ?, ?, ?]. 18th-Century [?]. 1930s [?]. [?]. 128 [?]. $139.99 [?]. $15.00 [?]. $16.95 1939 [?]. 1940 [?, ?]. 1940s [?]. 1941 [?]. [?]. $16.96 [?]. $18.95 [?]. $24.00 [?]. 1942 [?]. 1943 [?]. 1945 [?, ?, ?, ?, ?]. $24.00/$34 [?]. $24.95 [?, ?]. $26.95 [?]. 1946 [?, ?]. 1950s [?]. 1970s [?]. 1980s [?]. $29.95 [?]. $30.95 [?]. $39 [?]. $43.39 [?]. 1989 [?]. 19th [?, ?]. $45.00 [?]. $5.95 [?]. $54.00 [?]. $54.95 [?]. $54.99 [?]. $6.50 [?]. $6.95 [?]. $69.00 2 [?, ?]. 200/220 [?]. 2000 [?]. 2004 [?, ?]. [?]. $69.95 [?]. $75.00 [?]. $89.95 [?]. th 2008 [?]. 2009 [?]. 2011 [?]. 2013 [?, ?]. [?]. A [?]. A3 [?, ?]. χ [?]. H [?]. k [?, ?]. M 2014 [?]. 2017 [?]. 2019 [?]. 20755-6886 [?, ?]. M 3 [?]. n [?, ?, ?]. [?]. 209 [?, ?, ?, ?, ?, ?]. 20th [?]. 21 [?]. 22 [?]. 220 [?]. 24-Hour [?, ?, ?]. 25 [?, ?]. -Bit [?]. -out-of- [?, ?]. -tests [?]. 25.00/$39.30 [?]. 25.00/839.30 [?]. 25A1 [?]. 25B [?]. 26 [?, ?]. 28147 [?]. 28147-89 000 [?]. 01Q [?, ?]. [?]. 285 [?]. 294 [?]. 2in [?, ?]. 2nd [?, ?, ?, ?]. 1 [?, ?, ?, ?]. 1-4398-1763-4 [?]. 1/2in [?, ?]. 10 [?]. 100 [?]. 10011-4211 [?]. 3 [?, ?, ?, ?]. 3/4in [?, ?]. 30 [?]. 310 1 2 [?, ?, ?, ?, ?, ?, ?]. 312 [?]. 325 [?]. 3336 [?, ?, ?, ?, ?, ?]. affine [?]. [?]. 35 [?]. 36 [?]. 3rd [?]. Afluisterstation [?, ?]. After [?]. Aftermath [?]. Again [?, ?]. Against 4 [?]. 40 [?]. 44 [?]. 45 [?]. 45th [?]. 47 [?]. [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. Age 4in [?, ?]. [?, ?]. Agencies [?]. Agency [?, ?, ?, ?, ?, ?, ?, ?, ?, ?, ?]. -

George Lasry: Modern Cryptanalysis of Historical Ciphers
Modern Cryptanalysis of Historical Ciphers November 1, 2019 George Lasry Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 2 Agenda • Introduction – Motivation – Difficulty – Generic approaches • Case studies – Hagelin M-209 – Playfair – Double transposition – SIGABA George Lasry 3 Motivation • Historical cryptanalysis • Undecrypted texts • Public challenges • Fun George Lasry 4 Difficulty - Factors • System design – Diffusion – Confusion – Weaknesses • Key – Key space/length • Ciphertext – Length – Language George Lasry 5 Difficulty Easy Moderate Hard Very hard Intractable? Monoalphabetic Playfair Playfair Playfair Fialka substitution (long ciphertext) (short ciphertext) (very short) Transposition Transposition ADFGVX Double transposition Double transposition (short key) (long key) (long random key) Vigenere Enigma Enigma SIGABA (long ciphertext) (short ciphertext) (known plaintext) Hagelin M-209 Hagelin M-209 (long ciphertext) (short ciphertext) Hagelin M-209 Sturgeon T52 Sturgeon T52 (known plaintext) (regular stepping) (irregular stepping) George Lasry 6 Generic Approaches - 1 Exhaustive Combinatorial Stochastic Search Search Search ● Simple brute force ● Backtracking ● Hill climbing ● Dictionary search ● Meet in the Middle ● Simulated annealing (MITM) ● Hybrid (e.g., nested) ● Match some ● Others (e.g., genetic constraints (e.g., ● Match some algorithms) known plaintext) constraints ● Or optimize a scoring ● Optimize a fitness -

Female Mtis Celebrate Women's History Month
A PUBLICATION OF THE 502nd AIR BASE WING JOINT BASE SAN ANTONIO-LACKLAND, TEXAS • Vol. 72 No. 13 • April 3, 2015 Female MTIs celebrate Women's History Month Photo by Benjamin Faske In honor of Women’s History Month, an all-female fl ight of military training instructors marched down the bomb run during the Basic Military Training graduation, March 27. All of the leadership positions for the entire parade were fi lled by female military training instructors. INSIDE | Commentary 2 News 3 Community Briefs 10 Sports 16 ONLINE | http://www.jbsa.af.mil PAGE 2 commentary TALESPINNER April 3, 2015 Joint Base San Antonio- Lackland Make a list, check it twice: Editorial Staff BRIG. GEN. BOB LABRUTTA 502ND AIR BASE WING/JBSA Ensure your day counts! COMMANDER TODD G. WHITE 502ND AIR BASE WING/JBSA By Lt. Col. David Woodley backs, and things will not always go our have given up. PUBLIC AFFAIRS DIRECTOR 71st OSS commander, Vance Air Force Base, Okla. way. It will happen more than we want. Why? Most set a goal of something like How do you overcome these obstacles? losing 50 pounds. Great goal, but it will OSCAR BAllADARES ach day is a gift, and we need to I use the 24 hour rule. not happen overnight. So most people JBSA-LacKLAND PUBLIC AFFAIRS CHIEF ensure we make every day count After a setback give yourself 24 hours will focus on losing that 50 pounds, and to the fullest. But with everything to get mad, reflect and accept. in four weeks, when they only lose eight SENIOR AIRMAN LYNSIE NICHOLS E EDITOR else in life, many people do not know Get mad that it happened. -

Enigma Sim Manual
ENIGMA SIM MANUAL About the Enigma Sim The program is an exact simulation of the 3-rotor Wehrmacht & Luftwaffe, the 3-rotor Kriegsmarine M3, and the famous 4-rotor Kriegsmarine M4 model of the German Enigma cipher machine, as they were used during World War II from 1939 until 1945. You can select between the three models, choose different rotors or 'Walzen', preset the rotor wiring positions or 'Ringstellung' and switch letters by using plugs or 'Stecker'. The internal wiring of all rotors is identical to those used by the Wehrmacht, Luftwaffe and Kriegsmarine. This simulator is therefore fully compatible with the real Enigma-machine and you can decipher original messages and encipher your own messages. This manual explains how to use the Enigma simulator, describes the message procedures as used by the German Armed Forces, a complete technical description and a brief history of the Enigma. For more information, please visit Cipher Machines & Cryptology http://users.telenet.be/d.rijmenants Copyright Information THE ENIGMA SIMULATOR SOFTWARE IS FREEWARE AND CAN BE USED AND DISTRIBUTED UNDER THE FOLLOWING RESTRICTIONS: IT IS STRICTLY FORBIDDEN TO USE THIS SOFTWARE OR COPIES OR PARTS OF IT FOR COMMERCIAL PURPOSES, OR TO SELL, LEASE OR MAKE PROFIT FROM THIS PROGRAM BY ANY MEANS. THIS SOFTWARE MAY ONLY BE USED IF YOU AGREE TO THESE CONDITIONS. Picture Gallery Copyrights: © Tom Perera, Enigma Museum - http://w1tp.com/mcpu.htm © KMi The Open University DISCLAIMER OF WARRANTIES THIS SOFTWARE AND THE ACCOMPANYING FILES ARE SUPPLIED "AS IS" AND WITHOUT WARRANTIES OF ANY KIND, EITHER EXPRESSED OR IMPLIED, WITH RESPECT TO THIS PRODUCT, ITS QUALITY, PERFORMANCE, MERCHANTABILITY, OR FITNESS FOR ANY PARTICULAR PURPOSE. -

GOST 29C3 Talk
Cryptanalysis of GOST Nicolas T. Courtois University College London , UK GOST, Self-Similarity and Cryptanalysis of Block Ciphers Outline 1. Cold War cryptography 2. GOST: Russian encryption standard 3. GOST submission to ISO in 2010 4. How GOST can eventually be broken… >60 distinct attacks … Best = 2101 2011/626 updated 2 © Nicolas T. Courtois, 2006-2015 GOST, Self-Similarity and Cryptanalysis of Block Ciphers Main Themes: 1. Self-Similarity: extremely rich universe of distinct non-trivial attacks which generalize many known attacks but are non of these. 2. Algebraic Complexity Reduction: Magical “tricks” to black -box reduce an attack on a cipher with 32 rounds to an attack on 8 or 4 rounds. 3 © Nicolas T. Courtois, 2006-2015 GOST, Self-Similarity and Cryptanalysis of Block Ciphers Main Themes: 1. Self-Similarity: extremely rich universe of distinct non-trivial attacks which generalize many known attacks but are non of these. 2. Algebraic Complexity Reduction: Magical “tricks” to black -box reduce an attack on a cipher with 32 rounds to an attack on 8 or 4 rounds. *Bonus: How to measure security: discovery that single-key attacks are NOT the right notion to evaluate key length w.r.t. realistic attacks. 4 © Nicolas T. Courtois, 2006-2015 GOST, Self-Similarity and Cryptanalysis of Block Ciphers History: Cold War Russia vs. USA 5 © Nicolas T. Courtois, 2006-2015 GOST, Self-Similarity and Cryptanalysis of Block Ciphers - My Favourite Groups 6 © Nicolas T. Courtois, 2006-2015 GOST, Self-Similarity and Cryptanalysis of Block Ciphers Russian Subtitles On: code breakers == взломщики кодов 7 © Nicolas T. -

The Future of Internet Security: How New Technologies Will Shape the Internet and Affect the Law, 13 Santa Clara High Tech
Santa Clara High Technology Law Journal Volume 13 | Issue 1 Article 6 January 1997 The uturF e of Internet Security: How New Technologies Will Shape the Internet and Affect the Law William A. Hodkowski Follow this and additional works at: http://digitalcommons.law.scu.edu/chtlj Part of the Law Commons Recommended Citation William A. Hodkowski, The Future of Internet Security: How New Technologies Will Shape the Internet and Affect the Law, 13 Santa Clara High Tech. L.J. 217 (1997). Available at: http://digitalcommons.law.scu.edu/chtlj/vol13/iss1/6 This Comment is brought to you for free and open access by the Journals at Santa Clara Law Digital Commons. It has been accepted for inclusion in Santa Clara High Technology Law Journal by an authorized administrator of Santa Clara Law Digital Commons. For more information, please contact [email protected]. THE FUTURE OF INTERNET SECURITY: HOW NEW TECHNOLOGIES WILL SHAPE THE INTERNET AND AFFECT THE LAW* William A. Hodkowskit I. Introduction ............................................................................ 218 II. The Internet ............................................................................ 221 Im. A Security Primer .................................................................. 223 A. Important Concepts ......................................................... 224 B. Problems Arising from a Lack of Security ..................... 225 C. Existing Security Solutions ............................................ 227 1. Secret Key Encryption .............................................