Performance Analysis of Joint Radio Resource Management Strategies for Beyond 3G Networks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Shenandoah Telecommunications Company
UNITED STATES OF AMERICA SECURITIES AND EXCHANGE COMMISSION Washington, D. C. 20549 FORM 10-K (Mark One) ☒ ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended December 31, 2020 ☐ TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from__________ to __________ Commission File No.: 000-09881 SHENANDOAH TELECOMMUNICATIONS COMPANY (Exact name of registrant as specified in its charter) Virginia 54-1162807 (State or other jurisdiction of incorporation or organization) (I.R.S. Employer Identification No.) 500 Shentel Way, Edinburg, Virginia 22824 (Address of principal executive offices) (Zip Code) (540) 984-4141 (Registrant's telephone number, including area code) SECURITIES REGISTERED PURSUANT TO SECTION 12(B) OF THE ACT: Common Stock (No Par Value) SHEN NASDAQ Global Select Market 49,932,073 (The number of shares of the registrant's common stock outstanding on (Title of Class) (Trading Symbol) (Name of Exchange on which Registered) February 23, 2021) SECURITIES REGISTERED PURSUANT TO SECTION 12(G) OF THE ACT: NONE Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ☒ No ☐ Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Exchange Act. Yes ☐ No ☒ Note - Checking the box above will not relieve any registrant required to file reports pursuant to Section 13 or 15(d) of the Exchange Act from their obligations under those Sections. -

Tarifat E Shërbimit Nga Rrjete Celulare Në Shqipëri
TARIFAT E SHËRBIMIT NGA RRJETE CELULARE NË SHQIPËRI Dhjetor 2020 Përmbajtja I. HYRJE ................................................................................................................................................ 3 II. PERMBLEDHJE E PAKETAVE STANDARDE .............................................................................. 4 III. TARIFAT STANDARDE PER SHERBIMIN CELULAR ................................................................. 6 1. Tarifat e shërbimeve për planet standarde me parapagesë ............................................................... 6 2. Tarifat e shërbimeve për planet standarde me kontratë ................................................................... 6 IV. PLANET TARIFORE, PAKETAT DHE OFERTAT ......................................................................... 7 1. Albtelecom ...................................................................................................................................... 7 1.1. Shërbimet Celulare me Parapagesë ......................................................................................... 7 1.2. Shërbimet celulare me kontratë ............................................................................................... 8 1.3. Paketat dhe Ofertat ................................................................................................................ 10 2. One Telecommunications.............................................................................................................. 11 1.4. Shërbimet celulare me parapagesë -

5G Implementation in Non-EU Countries of Europe Region
5G IMPLEMENTATION IN NON-EU COUNTRIES OF THE EUROPE REGION ITU Regional Initiative for Europe on Broadband Infrastructure, Broadcasting and Spectrum Management © ITU November 2020 Version 1.2 5G Implementation in non-EU countries of the Europe Region ACKNOWLEDGMENTS This paper was developed by the ITU Office for Europe within the framework of the ITU Regional Initiative for Europe on broadband infrastructure, broadcasting and spectrum management. It was elaborated by ITU Office for Europe team including Mr. Iago Bojczuk, Junior Policy Analyst, and Mr. Julian McNeill, Consultant, under the supervision and direction of Mr. Jaroslaw Ponder, Head of ITU Office for Europe. Moreover, important feedback has been provided to this report by: - Electronic and Postal Communications Authority (AKEP), Albania; - Ministry of Infrastructure and Energy, Albania; - Communications Regulatory Agency (CRA), Bosnia and Herzegovina; - Post and Telecom Administration (PTA), Iceland; - Ministry of Communications of Israel; - Office for Communications of Liechtenstein; - Ministry of Economy and Infrastructure of Moldova; - National Regulatory Agency for Electronic Communications and Information Technology (ANRCETI); - Ministry of Economy, Montenegro; - Agency for Electronic Communications and Postal Services (EKIP), Montenegro; - Ministry of Information Society and Administration, North Macedonia; - Agency for Electronic Communications of North Macedonia; - Ministry of Trade, Tourism and Telecommunications, Serbia; - Information and Communication Technologies Authority, Turkey; - National Commission for the State Regulation of Communications and Informatization, Ukraine; - Department for Digital, Culture, Media & Sport (DCMS), United Kingdom; - Dicastero per la Comunicazione - Direzione Tecnologica, Vatican City. The paper was prepared as the background contribution to the ITU Regional Forum for Europe on 5G strategies, policies and implementation, held on 22 and 23 October 2020. -

Telecommunications Provider Locator
Telecommunications Provider Locator Industry Analysis & Technology Division Wireline Competition Bureau February 2003 This report is available for reference in the FCC’s Information Center at 445 12th Street, S.W., Courtyard Level. Copies may be purchased by calling Qualex International, Portals II, 445 12th Street SW, Room CY- B402, Washington, D.C. 20554, telephone 202-863-2893, facsimile 202-863-2898, or via e-mail [email protected]. This report can be downloaded and interactively searched on the FCC-State Link Internet site at www.fcc.gov/wcb/iatd/locator.html. Telecommunications Provider Locator This report lists the contact information and the types of services sold by 5,364 telecommunications providers. The last report was released November 27, 2001.1 All information in this report is drawn from providers’ April 1, 2002, filing of the Telecommunications Reporting Worksheet (FCC Form 499-A).2 This report can be used by customers to identify and locate telecommunications providers, by telecommunications providers to identify and locate others in the industry, and by equipment vendors to identify potential customers. Virtually all providers of telecommunications must file FCC Form 499-A each year.3 These forms are not filed with the FCC but rather with the Universal Service Administrative Company (USAC), which serves as the data collection agent. Information from filings received after November 22, 2002, and from filings that were incomplete has been excluded from the tables. Although many telecommunications providers offer an extensive menu of services, each filer is asked on Line 105 of FCC Form 499-A to select the single category that best describes its telecommunications business. -

Telecommunications Provider Locator
Telecommunications Provider Locator November 2001 Katie Rangos Kenneth Lynch Industry Analysis Division Common Carrier Bureau This report is available for reference in the FCC’s Information Center at 445 12th Street, S.W., Courtyard Level. Copies may be purchased by calling Qualex International, Portals II, 445 12th Street SW, Room CY-B402, Washington, DC 20554, telephone 202-863-2893, facsimile 202-863-2898, or via e-mail [email protected]. The report can also be downloaded [file names: LOCAT01.ZIP, LOCAT01.PDF] from the FCC-State Link Internet site at www.fcc.gov/ccb/stats. Telecommunications Provider Locator This report lists the contact information and the types of services sold by 5,679 telecommunications providers operating as of December 31, 2000. All information in this report is drawn from providers’ April 1, 2001 filing of the Telecommunications Reporting Worksheet (FCC Form 499-A). This report can be used by customers to identify and locate telecommunications providers, by telecommunications providers to identify and locate others in the industry, and by equipment vendors to identify potential customers. Virtually all providers of telecommunications must file FCC Form 499-A each year.1 These forms are not filed directly with the FCC but rather with the Universal Service Administrative Company (USAC), which serves as the data collection agent. The worksheets were due April 1, 2001, but some providers filed late or updated their filing after that date. By October 1, 2001, the database contained contact information and revenue data from 5,679 filers. Information from filings received after October 1 and from filings that were incomplete has been excluded from the tables. -

País Operador Código Apresentado Na Fatura Detalhada AFEGANISTAO
Código apresentado País Operador na fatura detalhada AFEGANISTAO MTN AFGHANISTAN AFGAR AFGHAN WIRELESS COMMUNICATION AFEGANISTAO AFGAW COMPANY AFEGANISTAO ETISALAT AFGHANISTAN AFGEA AFRICA DO SUL MTN MOBILE TELEPHONE NETWORK S ZAFMN AFRICA DO SUL Cell C (Pty) Ltd ZAFCC AFRICA DO SUL Vodacom (PTY) Ltd. ZAFVC ALBANIA TELEKOM ALBANIA SH.A ALBAM ALBANIA ALBTELECOM SH.A, ALBEM ALBANIA PLUS COMMUNICATION ALBM4 ALEMANHA VODAFONE GMBH, GERMANY DEUD2 ALEMANHA MOBILCOM MULTIMEDIA GMBH DEU13 ALEMANHA TELEKOM DEUTSCHLAND GMBH, DEUD1 ALEMANHA Telefónica Germany DEUO2 ALEMANHA Telefónica Germany DEUE2 ALEMANHA E-Plus Mobilfunk GmbH & Co. KG DEUE1 ALEMANHA GROUP 3G DEU3G ANDORRA ANDORRA TELECOM SAU ANDMA ANGOLA UNITEL AGOUT ANGOLA MOVICEL AGOMV CABLE & WIRELESS (WEST INDIES) - ANGUILLA AIACW ANGUILLA ANTIGUA E BARBUDA CABLE & WIRELESS (WEST INDIES) - ANTIGUA ATGCW ANTIGUA E BARBUDA APUA PCS ATG03 ANTILHAS HOLANDESAS UTS SETEL ANTUT ANTILHAS HOLANDESAS TELCELL NV ANTTC ANTILHAS HOLANDESAS DIGICEL CURACAU ANTCT ARABIA SAUDITA ZAIN SAUDI ARABIA SAUZN ETIHAD ETISALAT COMPANY - MOBILY SAUDI ARABIA SAUDITA SAUET ARABIA ARABIA SAUDITA EAE-ALJAWWAL SAUEJ ARABIA SAUDITA STC SAUAJ ARGELIA OPTIMUM TELECOM ALGERIE SPA DZAOT ARGELIA ALGERIE TELECOM MOBILE DZAA1 ARGENTINA TELEFÓNICA MOVILES ARGENTINA S.A ARGTM 1 ARGENTINA Claro Argentina ARGCM ARGENTINA TELECOM PERSONAL S.A ARGTP ARGENTINA NEXTEL ARGENTINA ARGNC ARMENIA ARMENTEL ARM01 ARMENIA K TELECOM CJSC (VIVACELL-MTS) ARM05 Servicio di Telecomunicacion di Aruba (SETAR) ARUBA ABWSE N.V. ARUBA DIGICEL ABWDC AUSTRALIA VODAFONE HUTCHISON AUSTRALIA AUSVF AUSTRALIA ONE.TEL AUSOT AUSTRALIA SingTel Optus Pty Limited AUSOP AUSTRALIA Telstra AUSTA VODAFONE HUTCHISON AUSTRALIA PTY AUSTRALIA AUSHU LIMITED AUSTRIA A1 Telekom Austria AG AUTPT AUSTRIA A1 TELEKOM AUSTRIA AG AUTON AUSTRIA T-Mobile Austria GmbH AUTMM AUSTRIA T-MOBILE AUSTRIA GMBH AUTTR AUSTRIA HUTCHISON DREI AUSTRIA GMBH AUTHU AUSTRIA HUTCHISON DREI AUSTRIA GMBH AUTCA AVIOES ONAIR SWITZERLAND SARL CHEOA AVIOES AEROMOBILE AS NORAM AZERBEIJAO Bakcell Ltd. -
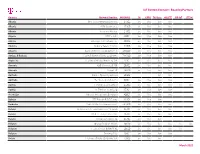
Iot Custom Connect - Roaming Partners
IoT Custom Connect - Roaming Partners Country Column1 Network Provider Column2MCCMNCColumn10 Column32G Column4GPRS Column53G Data Column64G/LTE Column7NB-IoT LTE-M Albania One Telecommunications sh.a 27601 live live live live Albania ALBtelecom sh.a. 27603 live live live live Albania Vodafone Albania 27602 live live live live Algeria ATM Mobilis 60301 live live live live Algeria Wataniya Telecom Algerie 60303 live live live live Andorra Andorra Telecom S.A.U. 21303 live live live live Anguilla Cable and Wireless (Anguilla) Ltd 365840 live live live live Antigua & Barbuda Cable & Wireless (Antigua) Limited 344920 live live live live Argentina Telefónica Móviles Argentina S.A. 72207 live live live live Armenia VEON Armenia CJSC 28301 live live live live Armenia Ucom LLC 28310 live live live live Australia SingTel Optus Pty Limited 50502 live live Australia Telstra Corporation Ltd 50501 live live live live Austria T-Mobile Austria GmbH 23203 live live live live live live Austria A1 Telekom Austria AG 23201 live live live live Azerbaijan Bakcell Limited Liable Company 40002 live live live live Bahrain STC Bahrain B.S.C Closed 42604 live live live Barbados Cable & Wireless Barbados Ltd. 342600 live live live live Belarus Belarusian Telecommunications Network 25704 live live live live Belarus Mobile TeleSystems JLLC 25702 live live live live Belarus Unitary Enterprise A1 25701 live live live Belgium Orange Belgium NV/SA 20610 live live live live live live Belgium Telenet Group BVBA/SPRL 20620 live live live live live Belgium Proximus PLC 20601 live live live live Bolivia Telefonica Celular De Bolivia S.A. 73603 live live live March 2021 IoT Custom Connect - Roaming Partners Country Column1 Network Provider Column2MCCMNCColumn10 Column32G Column4GPRS Column53G Data Column64G/LTE Column7NB-IoT LTE-M Bosnia and Herzegovina PUBLIC ENTERPRISE CROATIAN TELECOM Ltd. -

Tarifat E Shërbimit Nga Rrjete Celulare Në Shqipëri
TARIFAT E SHËRBIMIT NGA RRJETE CELULARE NË SHQIPËRI Maj 2021 Përmbajtja I. HYRJE ..................................................................................................................................................... 3 II. PERMBLEDHJE E PAKETAVE STANDARDE KRYESORE ............................................................................ 4 III. TARIFAT STANDARDE PER SHERBIMIN CELULAR .................................................................................. 7 1. Tarifat e shërbimeve për planet standarde me parapagesë ................................................................ 7 2. Tarifat e shërbimeve për planet standarde me kontratë .................................................................... 8 IV. PLANET TARIFORE, PAKETAT DHE OFERTAT ......................................................................................... 9 1. Albtelecom ........................................................................................................................................ 9 1.1. Shërbimet Celulare me Parapagesë ........................................................................................... 9 1.2. Shërbimet celulare me kontratë ............................................................................................... 10 1.3. Paketat dhe Ofertat .................................................................................................................. 12 2. One Telecommunications .............................................................................................................. -

Report on the State of the Telecommunications Market in Poland in 2018
Report on the state of the telecommunications market in Poland in 2018 Warsaw, June 2019 CONTENTS TELECOMMUNICATIONS MARKET 1. INTERNET ACCESS 5 2. MOBILE TELEPHONY 17 3. BUNDLED SERVICES 32 4. FIXED-LINE TELEPHONY 39 5. VOIP TELEPHONY 47 TELECOMMUNICATIONS INFRASTRUCTURE 1. STATISTICS OF DATA COLLECTED DURING THE INVENTORY 50 2. NODES OF TELECOMMUNICATIONS NETWORKS 54 3. TELECOMMUNICATIONS NETWORK COVERAGE 64 4. WIRED NETWORK ROUTES 74 INTRODUCTION We are pleased to provide you with the Report In this segment, the number of active SIM cards is on the telecommunications market in 2018. Like last systematically falling. In 2018, a total of 51.6 million of them year, the publication covers two issues. The first was recorded, i.e. 3% less than in 2017. The penetration concerns the market itself, the second concerns of mobile telephony services also dropped, reaching 134%. the telecommunications infrastructure. However, the trend of increasing the number of M2M cards has been maintained. Last year, 3.3 million M2M cards were It is worth noting the changes in the annual reporting used, an increase by 15%, compared to 2017. of telecommunications undertakings that entered into force on 12 December 2018. In the light of the new regulations, As a consequence of the Roam Like at Home principle each telecommunications entrepreneur was obliged introduced in 2017, there was a 32% increase in the duration to submit reports on telecommunications activities using of voice calls made by Poles staying abroad. a dedicated Electronic Services Platform. The conclusions presented to you in the report have been prepared on In the area of bundled services, a further upward trend can the basis of current data as of 31 December 2018. -

TARIFAT E SHERBIMIT NGA RRJETE FIKSE DHE INTERNET BROADBAND NE SHQIPERI Përmbajtja
TARIFAT E SHERBIMIT NGA RRJETE FIKSE DHE INTERNET BROADBAND NE SHQIPERI Maj 2021 Përmbajtja I. HYRJE .................................................................................................................................................. 3 II. TARIFAT E TELEFONISË FIKSE ..................................................................................................... 4 1. Albtelecom ........................................................................................................................................ 4 1.1. Programet standarte të shërbimit të telefonisë fikse ............................................................... 4 1.2. Paketat familjare ALB TV. .......................................................................................................... 6 1.3. Paketat dhe Ofertat e shërbimit fiks Albtelecom. .................................................................... 6 1.4. Shërbimi internet ...................................................................................................................... 7 2. One Telecommunications ................................................................................................................. 9 2.1. Telefonia fikse ........................................................................................................................... 9 2.2. Shërbimi internet broadband ................................................................................................. 10 3. Vodafone Albania-Abcom .............................................................................................................. -
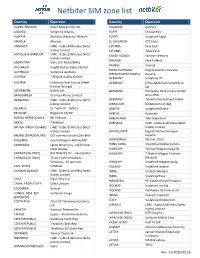
Netbiter SIM Zone List
Netbiter SIM zone list Country Operator Country Operator ALAND, FINLAND Aland Mobiltelefon Ab ECUADOR Conecel ALBANIA Vodafone Albania EGYPT Etisalat Misr ALGERIA Ooredoo Wataniya Telecom EGYPT Vodafone Egypt ANGOLA Movicel EL SALVADOR CTE Claro ANGUILLA LIME - Cable & Wireless (West ESTONIA Elisa Eesti Indies) Limited ESTONIA Tele2 Eesti ANTIGUA & BARBUDA LIME - Cable & Wireless (West FAROE ISLANDS Faroese Telecom Indies) Limited FINLAND Elisa Finland ARGENTINA Claro (CTI Móvil/AMx) FRANCE Vivendi AUSTRALIA Singtel Optus, Optus Pty Ltd FRENCH GUYANA Digicel Antilles Française AUSTRALIA Vodafone Australia (FRENCH WEST INDIES) Guyane AUSTRIA T-Mobile Austria GmbH GERMANY Vodafone D2 AUSTRIA Hutchison Drei Austria GmbH GERMANY E-Plus Mobilfunk GmbH & Co. (former Orange) KG AZERBAIJAN Bakcel Ltd. GERMANY Telefonica O2 Germany GmbH BANGLADESH GrameenPhone Limited & Co.OHG BARBADOS LIME - Cable & Wireless (West GERMANY Telekom Deutschland GmbH Indies) Limited GIBRALTAR Gibtelecom Limited BELARUS FE “Velcom” (MDC) GREECE Vodafone Greece BELGIUM Belgacom SA/NV GREECE Cosmote BOSNIA HERZEGOVINA BH Telecom GREENLAND Tele Greenland BRAZIL TIM Brazil GRENADA LIME - Cable & Wireless (West BRITISH VIRGIN ISLANDS LIME - Cable & Wireless (West Indies) Limited Indies) Limited GUADELOUPE Digicel Antilles Française BRUNEI (DARUSSALAM) DST communications Sdn Bhd Guyane BULGARIA Cosmo Bulgaria Mobile EAD GUATEMALA Sercom, Claro CAMBODIA Latelz (Smart) Co., Ltd (former HONG KONG SmartOne Mobile Comms Hello Axiata) HUNGARY Telenor Magyarorszag Zrt. CANADA (3G ONLY) Bell Mobility Inc. - 3G operator HUNGARY T-Mobile Magyar Telekom CANADA (3G ONLY) TELUS Communications (Westel) Company - 3G operator HUNGARY Vodafone Magyarország CAPE VERDE CVMovel ICELAND Vodafone Iceland CAYMAN ISLANDS LIME - Cable & Wireless (West INDIA Unitech Wireless Indies) Limited INDIA Vodafone Essar CHILE Claro Chile S.A. -
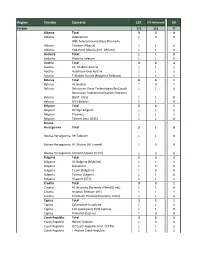
Prepared for Upload GCD Wls Networks
Region Country Operator LTE LTE‐Advanced 5G Europe 171 123 77 Albania Total 32 0 Albania ALBtelecom 10 0 ONE Telecommunications (formerly Albania Telekom Albania) 11 0 Albania Vodafone Albania (incl. ABCom) 11 0 Andorra Total 11 0 Andorra Andorra Telecom 11 0 Austria Total 33 3 Austria A1 Telekom Austria 11 1 Austria Hutchison Drei Austria 11 1 Austria T‐Mobile Austria (Magenta Telekom) 11 1 Belarus Total 43 1 Belarus A1 Belarus 10 1 Belarus Belarusian Cloud Technologies (beCloud) 11 0 Belarusian Telecommunications Network Belarus (BeST, life:)) 11 0 Belarus MTS Belarus 11 0 Belgium Total 33 1 Belgium Orange Belgium 11 0 Belgium Proximus 11 1 Belgium Telenet (incl. BASE) 11 0 Bosnia‐ Herzegovina Total 31 0 Bosnia‐Herzegovina BH Telecom 11 0 Bosnia‐Herzegovina HT Mostar (HT Eronet) 10 0 Bosnia‐Herzegovina Telekom Srpske (m:tel) 10 0 Bulgaria Total 53 2 Bulgaria A1 Bulgaria (Mobiltel) 11 1 Bulgaria Bulsatcom 10 0 Bulgaria T.com (Bulgaria) 10 0 Bulgaria Telenor Bulgaria 11 0 Bulgaria Vivacom (BTC) 11 1 Croatia Total 33 1 Croatia A1 Hrvatska (formerly VIPnet/B.net) 11 0 Croatia Hrvatski Telekom (HT) 11 1 Croatia Telemach Hrvatska (formerly Tele2) 11 0 Cyprus Total 32 1 Cyprus Cytamobile‐Vodafone 11 1 Cyprus Epic (previously MTN Cyprus) 11 0 Cyprus PrimeTel (Cyprus) 10 0 Czech Republic Total 43 3 Czech Republic Nordic Telecom 10 0 Czech Republic O2 Czech Republic (incl. CETIN) 11 1 Czech Republic T‐Mobile Czech Republic 11 1 Czech Republic Vodafone Czech Republic 11 1 Denmark Total 54 4 Denmark Hi3G Access (3) 11 1 Denmark Net 1 Denmark 10 0 Denmark TDC (incl.