The Xirrus Wi-Fi Array XS4, XS8 Security Policy Xirrus, Inc
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Xirrus Management System
Xirrus Management System DATASHEET Introducing the Xirrus Management System Monitoring Views The Xirrus Management System (XMS) is a wireless network management platform that provides full monitoring and Dashboard View management of the Xirrus wireless Array network via a web Summary view of Xirrus Wireless network that is widget based. based application with graphical map views. XMS scales from Each widget shows different summary statistics such as Array/ small to large networks and from one location to multiple SSID status information, security status, and station information. locations, as well as large campus environments with thousands The Dashboard view is fully customizable to add or remove of wireless users. XMS provides help desk, as well as network desired widgets, select data categories displayed, and change operations and management capabilities for the Xirrus wireless the widget layout on a per user basis. network. XMS has a flexible license scheme based on the size of the wireless network, and is available as an application to run on legacy Windows Server systems, as well as a virtualized server environment. XMS is also offered on Xirrus Management appliances, for those that prefer a turnkey solution. At A Glance • Web based implementation, monitoring and management of a Xirrus wireless network • Single management application for small to large Xirrus Wireless Array Networks • Monitor wireless network performance, traffic and client stations • Manage configuration of the wireless network and management system • Configuration templates for bulk configuration changes Maps View • Automated installation and configuration of Xirrus Wireless View hierarchical maps showing floor plans or images for each Array Network allowing simplified deployment of Arrays location with Xirrus Array placement and selectable layered information views with configurable filters for information • Graphical maps showing wireless coverage heat maps, displayed. -

Wi-Fi Array Wi-Fi Array Architecture
Wi-Fi Array Wi-Fi Array Architecture Cellular Array Antennas Wi-Fi Array Antennas Cellular Wi-Fi Array Antenna Array Antenna • Multiple radios = more bandwidth and user density • Directional antennas = stronger signal strength and increased coverage • Sectored RF patterns = better RF management and load balancing • Fewer devices = cost, installation, and management savings 1 Xirrus Wi-Fi Arrays combine sectored array antennas and network switching into a single device. L2/L3 Switch Wi-Fi Array Switch • Distributed to the edge = more efficient switching decisions • Intelligence at the edge = more efficient QoS and VLAN-tagging • Security at the edge = better protection of all network traffic • More bandwidth = enhanced user experience and network efficiency 2 Xirrus Differentiators The Xirrus Wi-Fi Array replaces Ethernet workgroup switches by distributing the network intelligence and security to the network edge along with mobility and flexibility. VS. 24-Port Ethernet Xirrus XN8 Workgroup Switch Wi-Fi Array Users 24 24 Link Bandwidth 1Gbps 300Mbps Uplinks 2GigE 2GigE Mobility No Yes Security Very Good Very Good Availability Very Good Very Good Management Very Good Very Good Moves/Adds/Changes Average Very Good Installation Poor (Cables, Jacks, Very Good (Fewer Cables, Jumpers, Switches) No Closet Equipment) # of Devices Same Same # of Cables Poor (10X More) Excellent (90% Less) Cost Per User Good Very Good 3 It’s time to replace switched Ethernet to the desktop with Wi-Fi as the primary network connection. The Xirrus Wi-Fi Array obsoletes all other Wi-Fi offerings by delivering 400% more coverage, bandwidth, and user connections while using 75% fewer devices, cables, and switch ports. -
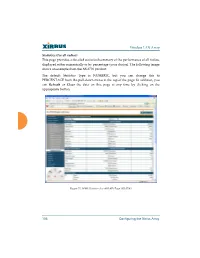
Wireless LAN Array 106 Configuring the Xirrus Array
Wireless LAN Array Statistics (for all radios) This page provides a detailed statistical summary of the performance of all radios, displayed either numerically or by percentage (your choice). The following image shows an example from the XS-3700 product. The default Statistics Type is NUMERIC, but you can change this to PERCENTAGE from the pull-down menu at the top of the page. In addition, you can Refresh or Clear the data on this page at any time by clicking on the appropriate button. Figure 74. WMI: Statistics for All IAPs Page (XS-3700) 106 Configuring the Xirrus Array Wireless LAN Array SSID This is a status only page that allows you to review SSID (Service Set IDentifier) assignments. It includes the SSID name, whether or not an SSID is visible on the network, any security and QoS parameters defined for each SSID, associated VLAN IDs, and radio availability per SSID. There are no configuration options available on this page, but if you are experiencing problems or reviewing SSID management parameters, you may want to print this page for your records. For information to help you understand SSIDs and how multiple SSIDs are managed by the XS-3900, go to the Multiple SSIDs section of “Frequently Asked Questions” on page 222. Figure 75. WMI: SSID Page Configuring the Xirrus Array 107 Wireless LAN Array Understanding SSIDs The SSID (Service Set Identifier) is a unique identifier that wireless networking devices use to establish and maintain wireless connectivity. Multiple access points on a network or sub-network can use the same SSIDs. -

Download the Programme Preview Here
THE STADIUM BUSINEss SUMMIT LONDON • 3-5 JUNE 2014 CONFERENCE PROGRAMME & EVENT GUIDE INCORPORATING PREMIUM SEAT SEMINAR FAN EXPERIENCE FORUM 2 MANICA kansas city | london | shanghai manicaarchitecture.com WELCOME HELLO WEMBLEY! Thanks for joining us at the ‘home of football’. After Dublin, Barcelona, Turin and Manchester, TheStadiumBusiness Summit is delighted to be in London for its fifth anniversary –"most especially at the reinvigorated sports and entertainment destination that is Wembley. You’ll find the full event schedule in the following pages. Alongside the main Summit conference programme, we’re hosting our specialist pre-Summit meetings at the Hilton Wembley to give the Premium Seat Seminar and Fan Experience Forum audiences maximum networking opportunities. We kickoff with an ‘expert’s tour’ and welcome reception of the world’s most famous stadium – courtesy of Wembley Stadium Consultancy. As always, the highlight of the programme is *DON’T FORGET! TheStadiumBusiness Awards evening where we will once again recognise our industry’s achievements, If you have purchased creativity and leaders. This year we’re at the historic RAF Museum with our hosts Centerplate. a ticket to TheStadium Business Awards Gala Our thanks go to all our speakers (for sharing their knowledge so freely), our sponsors (for backing us and keeping our industry moving forward), our partners (for making it easier to put this event Dinner please collect on), and our host venue (a great stadium with great people!). no later than from 14.00 the on Wednesday Finally – above all – our thanks to YOU for joining us. We wish you a great ‘visitor experience’ at registration desk.. -

City of Redondo Beach Deploys Xirrus High Performance Wi-Fi to Improve Staff/Public Experience and Operational Efficiency
City of Redondo Beach Deploys Xirrus High Performance Wi-Fi to Improve Staff/Public Experience and Operational Efficiency “Other than basic Overview management, we THE CITY OF REDONDO BEACH is a coastal Southern California town located 20 miles from haven’t had to downtown Los Angeles. With white sand beaches and year-round sunny weather, Redondo spend any time Beach is a preferred resort destination and one of the most desirable areas to live in the troubleshooting or country. fixing anything. For a The city boasts its own police department, fire and public works departments, two public department with our libraries, 15 parks and 13 parkettes, a large recreational and commercial harbor as well as the staffing level, that’s a Redondo Beach Pier and Seaside Lagoon. Redondo Beach outfitted its city buildings, libraries and performing arts center with Wi-Fi access to create more dynamic recreational experiences big plus.” for the public and increase productivity for the city’s 420 employees and 15 departments. CHRISTOPHER BENSON, IT TECHNOLOGY DIRECTOR, CITY OF REDONDO BEACH The Challenge Installed in 2006, the incumbent controller-based Wi-Fi solution was difficult to manage and rapidly becoming outdated. The IT team began to experience equipment failure leading to wireless outages. Additionally, performance did not match the density requirements of the areas served. Due to the rigidity of the system, the staff spent a significant amount of time managing and repairing the network when it failed. These compounding issues resulted in City staff receiving complaints about the spotty access and poor network speed. City administrators began to evaluate alternative Wi-Fi vendors and looked at Xirrus Wi- Fi through the company’s partnership with Avaya. -

Xirrus Wi-Fi Designertm
Xirrus Wi-Fi Designer TM DATASHEET Xirrus Wi-Fi Designer The Xirrus Wi-Fi Designer is the ultimate 802.11 wireless site survey solution specifically architected to understand the multi- radio architecture of Xirrus Wireless Arrays. Wi-Fi Designer is offered in two forms: • A cloud based predictive planning tool that can be used from most common browsers • A Windows based application Wi-Fi Designer Cloud allows for predictive surveys in the very early stages of a project, to get a good estimate of the location and number of Xirrus Arrays as well as coverage and capacity. It is accessible from the Xirrus website, and supports most common browsers. All surveys created using the tool are stored in the cloud and easily accessible at any time through a convenient user account. At A Glance The Windows based application enables network architects • Predictive surveys help to plan a Wi-Fi network strategy to use predictive analysis and active site surveys to plan a with the optimal number of Xirrus Wireless Arrays and their best-fit wireless network strategy to minimize infrastructure recommended placement requirements while maximizing coverage and capacity. Once the Xirrus Wireless Arrays are implemented the Xirrus Wi-Fi • Quickly complete Active Surveys onsite with Xirrus Wireless Designer can verify the results of implementation and ensure Arrays taking real-time measurements to qualify the design for that design criteria has been met. the Xirrus implementation guarantee • Model different site conditions, Array configurations and positioning -

Xirrus Management System
Xirrus Management System DATASHEET Xirrus Management System The Xirrus Management System is a wireless network lifecycle management platform enabling network administrators to ef- ficiently operate, configure and maintain Xirrus Wireless Arrays from a single vantage point. The Xirrus Management System (XMS) automatically discovers, configures, and monitors a Wireless Array network, and can scale from single site to large scale, multi-site deployments. Network administrators choose from a range of installation op- tions including on-premise software, pre-configured appliances, or a Cloud based NMS option, providing the flexibility needed for fast implementation and lowest costs to best fit the company operating requirements. At A Glance • Centrally define and manage configurations and policies • Monitor wireless network performance Centralized Administration & Management • Drill down reporting and analytics Network administrators simplify their day-to-day activities through the centralized management console where they can • Security monitoring & alerting manage and maintain multiple configuration settings and secu- rity policies to selectively apply across the Xirrus Wireless Array • Simplified troubleshooting and ongoing maintenance network. Administrators can continuously monitor wireless net- work performance and security policy compliance to ensure end user productivity while reducing the risks of security breaches. Network architects can use the drill down reports and analytics XIRRUS MANAGEMENT SYSTEM HEAT MAP provide the actionable -

Pushing the Limits of Indoor Localisation in Today's Wi-Fi Networks
Pushing the Limits of Indoor Localisation in Today’s Wi-Fi Networks JIE XIONG A dissertation submitted in partial fulfillment of the requirements for the degree of Doctor of Philosophy of the University College London. Department of Computer Science University College London Aug 2015 2 I, JIE XIONG, confirm that the work presented in this thesis is my own. Where information has been derived from other sources, I confirm that this has been indicated in the thesis. Abstract Wi-Fi networks are ubiquitous nowadays and play an increasingly important role in our everyday lives. Many emerging applications including augmented reality, indoor navigation and human tracking, rely heavily on Wi-Fi. One key component for the success of these applications is accurate localisation. While we have GPS in the outdoor environment, indoor localisation at a sub-metre granularity remains challenging. On the other hand, Wi-Fi technology has developed significantly evolving from 802.11b/a/g to the latest 802.11ac standard. In Wi-Fi’s development, one interesting trend is the increasing number of antennas attached to a single access point (AP). An- other trend is the presence of frequency-agile radios and larger bandwidths in the latest 802.11n/ac standards. These opportunities are leveraged to increase the accuracy of indoor localisation significantly. ArrayTrack employs multi-antenna APs for angle-of-arrival (AoA) information to localise clients accurately indoors. It is the first indoor Wi-Fi localisation system able to achieve below half metre median accuracy. Innovative multipath identification scheme is proposed to handle the challenging multipath issue in indoor environment. -

(12) United States Patent (10) Patent No.: US 9,591,529 B2 Gates Et Al
USO0959.1529B2 (12) United States Patent (10) Patent No.: US 9,591,529 B2 Gates et al. (45) Date of Patent: Mar. 7, 2017 (54) ACCESS POINT PROVIDING MULTIPLE (56) References Cited SINGLE-USER WIRELESS NETWORKS U.S. PATENT DOCUMENTS (71) Applicant: Xirrus, Inc., Thousand Oaks, CA (US) 7,298,702 B1 1 1/2007 Jones et al. 8.498,278 B2 7/2013 Beach (72) Inventors: Dirk Gates, Westlake Village, CA (US); 8,885,539 B2 11/2014 Trudeau et al. Patrick Parker, Moorpark, CA (US); 8,923,265 B2 12/2014 Kuo et al. Jack Horner, Thousand Oaks, CA 2004/O185845 A1 9, 2004 Abhishek et al. 2005.0185626 A1 8, 2005 Meier et al. (US); Alan Russell, Lubbock, TX (US) 2007.008911.0 A1* 4/2007 Li ................................. 717/178 2008/0293404 A1* 11/2008 Scherzer et al. 455,426.1 (73) Assignee: Xirrus, Inc., Thousand Oaks, CA (US) 2012/0209934 A1* 8, 2012 Smedman ....... TO9,208 2013/0170432 A1* 7, 2013 O'Brien et al. .............. 370,328 (*) Notice: Subject to any disclaimer, the term of this 2014/O196126 A1 7/2014 Peterson et al. patent is extended or adjusted under 35 2015/0208242 A1* 7, 2015. Ji .................................. 455,411 U.S.C. 154(b) by 5 days. * cited by examiner (21) Appl. No.: 14/717,946 Primary Examiner — Michael J Moore, Jr. (22) Filed: May 20, 2015 Assistant Examiner — Saba Tsegaye (74) Attorney, Agent, or Firm — SoCal IP Law Group (65) Prior Publication Data LLP: John E. Gunther; Steven C. Sereboff US 2016/0345208 A1 Nov. 24, 2016 (57) ABSTRACT (51) Int. -

Technical Report on Dark Energy Camera E Manoj
TECHNICAL REPORT ON DARK ENERGY CAMERA E MANOJ (13L228) Dissertation submitted in partial fulfillment of the requirements for the degree of BACHELOR OF ENGINEERING Branch: ELECTRONICS AND COMMUNICATION ENGINEERING of Anna University June - 2014 i DEPARTMENT OF ELECTRONICS AND COMMUNICATION ENGINEERING PSG COLLEGE OF TECHNOLOGY (Autonomous Institution)COIMBATORE – 641 004 TECHNICAL REPORT ON DARK ENERGY CAMERA Bona fide record of work done by D GOVARDHANAN (13L115) Dissertation submitted in partial fulfillment of the requirements for the degree of BACHELOR OF ENGINEERING Branch: ELECTRONICS AND COMMUNICATION ENGINEERING of Anna University June 2014 ...……………………… …………..………………. Dr. S.Subha Rani ii Faculty guide Head of the Department \ ACKNOWLEDGEMENT I would like to extend my sincere thanks to Dr. R. RUDHRAMOORTHY, Principal, PSG College of Technology, for his kind patronage. I am indebted to Dr. S. SUBHA RANI, Professor and Head of the Department of Electronics and Communication Engineering, for her continued support and motivation. I would like to express my gratitude to my technical report guide Mrs. RAMYA, Assistant Professor(SR), Mr. K.R. RADHAKRISHNAN, Assistant Professor and Dr. U. SARAVANAKUMAR, Assistant Professor Department of Electronics and Communication Engineering, for their constant motivation, direction and guidance throughout the entire course of our technical report. I am grateful to the support extended by my class advisor Dr. SIVARAJ, Assistant Professor, Department of Electronics and Communication Engineering. I thank all the staff members of the Department of Electronics and Communication Engineering for their support.Last but not the least I thank the Almighty and my family members who have been a guiding light in all our endeavors. -

This Offering Memorandum Provides Information on the Notes. for Convenience, Selected Information Is Presented on This Cover Page
Book-Entry Only Form Rating: S&P “A-1+” See “RATING” herein This Offering Memorandum provides information on the Notes. For convenience, selected information is presented on this cover page. To make an informed decision regarding the Notes, a prospective investor should read this Offering Memorandum in its entirety. Unless otherwise indicated, capitalized terms have the meanings given in this Offering Memorandum. CARNEGIE MELLON UNIVERSITY TAXABLE COMMERCIAL PAPER NOTES Not to exceed $70,000,000 BofA Merrill Lynch, Dealer Taxable Commercial Paper The Taxable Commercial Paper Notes (the “Notes”) will be issued by Carnegie Mellon University (the “University”), as fully-registered notes and, when initially issued, will be registered in the name of Cede & Co., as nominee for DTC, which will act as securities depository for the Notes. Purchases of beneficial ownership interests in the Notes will be made in book-entry form only in the principal amount of $100,000 or any integral multiple of $1,000 in excess thereof. Beneficial owners of the Notes will not receive physical delivery of note certificates so long as DTC or a successor securities depository acts as the securities depository with respect to the Notes. Interest on each Note will be payable on the maturity date of the applicable Note. So long as DTC or its nominee is the registered owner of the Notes, payments of the principal of and interest on the Notes will be made directly to DTC. Disbursements of such payments to DTC participants is the responsibility of DTC, and disbursement of such payments to the beneficial owners is the responsibility of DTC participants. -

A Comparison of Wi-Fi and Wimax with Case Studies Ming-Chieh Wu
Florida State University Libraries Electronic Theses, Treatises and Dissertations The Graduate School 2007 A Comparison of Wi-Fi and WiMAX with Case Studies Ming-Chieh Wu Follow this and additional works at the FSU Digital Library. For more information, please contact [email protected] THE FLORIDA STATE UNIVERSITY COLLEGE OF ENGINEERING A COMPARISON OF WI-FI AND WIMAX WITH CASE STUDIES By Ming-Chieh Wu A Thesis submitted to the Department of Electrical and Computer Engineering in partial fulfillment of the requirements for the degree of Master of Science Degree Awarded: Fall Semester, 2007 The members of the Committee approve the Thesis of Ming-Chieh Wu defended on October 30th, 2007. Bruce A. Harvey Professor Directing Thesis Ming Yu Committee Member Simon Y. Foo Committee Member Approved: Victor DeBrunner, Chair, Department of Electrical and Computer Engineering Ching-Jen Chen, Dean, FAMU-FSU College of Engineering The Office of Graduate Studies has verified and approved the above named committee members. ii TABLE OF CONTENTS List of Tables…………………………..………….………………………………………..……vi List of Figures………………………………….…………………………………………….…vii List of Abbreviations……………………..………….………………………………………….ix ABSTRACT……………………………………………..……………………………………...xii CHAPTER ONE 1. Introduction …………………………………………………………………………………....1 CHAPTER TWO 2. 3G…………………………………..…………………………………………………………..5 2.1. Introduction………………………………………………………………………...…..5 2.2. Technologies…………………………………………………………………………...5 2.2.1. WCDMA……………………………….………………………………………..5 2.2.2. CDMA2000………………………………………………………………….…..6 2.2.3. TD-SCDMA……………………………………………………………….…….6 2.3. Development…………………………………………………..……………………….7 2.4. Cases………………………………………………………………..…………….…….8 2.5. Conclusion……………………………………………………………………….……..9 CHAPTER THREE 3. IEEE 802.11, Wireless LAN…………………………………………………...……………..10 3.1. The background of IEEE 802.11…………………………………………….………10 3.2. Capacity……………………………………………………………………….….….11 3.3. The Physical Layer and MAC Layer…………………………………………...……14 3.3.1. The Physical Layer………………………………………………..……….….14 3.3.1.1.