Introduction to Awk Programming (Block Course)
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

At—At, Batch—Execute Commands at a Later Time
at—at, batch—execute commands at a later time at [–csm] [–f script] [–qqueue] time [date] [+ increment] at –l [ job...] at –r job... batch at and batch read commands from standard input to be executed at a later time. at allows you to specify when the commands should be executed, while jobs queued with batch will execute when system load level permits. Executes commands read from stdin or a file at some later time. Unless redirected, the output is mailed to the user. Example A.1 1 at 6:30am Dec 12 < program 2 at noon tomorrow < program 3 at 1945 pm August 9 < program 4 at now + 3 hours < program 5 at 8:30am Jan 4 < program 6 at -r 83883555320.a EXPLANATION 1. At 6:30 in the morning on December 12th, start the job. 2. At noon tomorrow start the job. 3. At 7:45 in the evening on August 9th, start the job. 4. In three hours start the job. 5. At 8:30 in the morning of January 4th, start the job. 6. Removes previously scheduled job 83883555320.a. awk—pattern scanning and processing language awk [ –fprogram–file ] [ –Fc ] [ prog ] [ parameters ] [ filename...] awk scans each input filename for lines that match any of a set of patterns specified in prog. Example A.2 1 awk '{print $1, $2}' file 2 awk '/John/{print $3, $4}' file 3 awk -F: '{print $3}' /etc/passwd 4 date | awk '{print $6}' EXPLANATION 1. Prints the first two fields of file where fields are separated by whitespace. 2. Prints fields 3 and 4 if the pattern John is found. -

TDS) EDEN PG MV® Pigment Ink for Textile
Technical Data Sheet (TDS) EDEN PG MV® Pigment Ink for Textile Product Description: Applications: EDEN PG MV water based pigment Ink is ideal for high-speed direct digital printing on all standard fabrics available on the market. The ink prints on all types of fabrics with equal quality and coverage without color shifts or patches. EDEN PG MV Pigment Ink may be used on cotton, cotton blends, polyester, polyamide (nylon) and treated & untreated fabrics. EDEN PG MV is ideal for a wide range of applications including sportswear, footwear, fashion, home décor and home textile and is designed for indoor and outdoor applications. This ink is manufactured using cutting edge technology and • Home textile • Bags • Indoor furnishing high-performance pigments, for optimal ink fluidity and • Décor • Sport apparel • Fashion & apparel printability through piezo printheads without bleeding or • Footwear migration. Compatible Print Head Technology: Ricoh Gen 4 & Gen 5 Industrial print heads based printers. Pre-treatment: The use of Bordeaux EDEN PG™ OS® (pretreatment liquid) is Product Line: recommended in order to achieve higher chemical attributes (see table below for comparison). The pretreatment process for fabrics is done offline using a standard textile padder. Red Cleaning Print procedure: Cyan Magenta Yellow Black Magenta Liquid The printing process can be done either inline or in individual segments. Inline printing allows the printed fabric to be fed Material Compatibility: through a standard textile dryer directly. Alternatively, if the printing stage is separated from the drying stage, drying is • Cotton required before rolling the fabric. • Viscose • Polyester • Lycra Drying Working Parameters: • Silk Recommended drying time: 3 minutes • Polyamide Recommended temperature: 150°C (302°F) • Leather • Synthetic leather Post-treatment: No chemical post treatment is needed. -

UNIX Workshop Series: Quick-Start Objectives
Part I UNIX Workshop Series: Quick-Start Objectives Overview – Connecting with ssh Command Window Anatomy Command Structure Command Examples Getting Help Files and Directories Wildcards, Redirection and Pipe Create and edit files Overview Connecting with ssh Open a Terminal program Mac: Applications > Utilities > Terminal ssh –Y [email protected] Linux: In local shell ssh –Y [email protected] Windows: Start Xming and PuTTY Create a saved session for the remote host name centos.css.udel.edu using username Connecting with ssh First time you connect Unix Basics Multi-user Case-sensitive Bash shell, command-line Commands Command Window Anatomy Title bar Click in the title bar to bring the window to the front and make it active. Command Window Anatomy Login banner Appears as the first line of a login shell. Command Window Anatomy Prompts Appears at the beginning of a line and usually ends in $. Command Window Anatomy Command input Place to type commands, which may have options and/or arguments. Command Window Anatomy Command output Place for command response, which may be many lines long. Command Window Anatomy Input cursor Typed text will appear at the cursor location. Command Window Anatomy Scroll Bar Will appear as needed when there are more lines than fit in the window. Command Window Anatomy Resize Handle Use the mouse to change the window size from the default 80x24. Command Structure command [arguments] Commands are made up of the actual command and its arguments. command -options [arguments] The arguments are further broken down into the command options which are single letters prefixed by a “-” and other arguments that identify data for the command. -

Reasoning About Programs Need: Definition of Works/Correct: a Specification (And Bugs) but Programs Fail All the Time
Good programs, broken programs? Goal: program works (does not fail) Reasoning about Programs Need: definition of works/correct: a specification (and bugs) But programs fail all the time. Why? A brief interlude on 1. Misuse of your code: caller did not meet assumptions specifications, assertions, and debugging 2. Errors in your code: mistake causes wrong computation 3. Unpredictable external problems: • Out of memory, missing file, network down, … • Plan for these problems, fail gracefully. 4. Wrong or ambiguous specification, implemented correctly Largely based on material from University of Washington CSE 331 A Bug's Life, ca. 1947 A Bug's Life Defect: a mistake in the code Think 10 per 1000 lines of industry code. We're human. -- Grace Hopper Error: incorrect computation Because of defect, but not guaranteed to be visible Failure: observable error -- program violates its specification Crash, wrong output, unresponsive, corrupt data, etc. Time / code distance between stages varies: • tiny (<second to minutes / one line of code) • or enormous (years to decades to never / millons of lines of code) "How to build correct code" Testing 1. Design and Verify Make correctness more likely or provable from the start. • Can show that a program has an error. 2. Program Defensively • Can show a point where an error causes a failure. Plan for defects and errors. • Cannot show the error that caused the failure. • make testing more likely to reveal errors as failures • Cannot show the defect that caused the error. • make debugging failures easier 3. Test and Validate Try to cause failures. • Can improve confidence that the sorts of errors/failures • provide evidence of defects/errors targeted by the tests are less likely in programs similar • or increase confidence of their absence to the tests. -

Unix/Linux Command Reference
Unix/Linux Command Reference .com File Commands System Info ls – directory listing date – show the current date and time ls -al – formatted listing with hidden files cal – show this month's calendar cd dir - change directory to dir uptime – show current uptime cd – change to home w – display who is online pwd – show current directory whoami – who you are logged in as mkdir dir – create a directory dir finger user – display information about user rm file – delete file uname -a – show kernel information rm -r dir – delete directory dir cat /proc/cpuinfo – cpu information rm -f file – force remove file cat /proc/meminfo – memory information rm -rf dir – force remove directory dir * man command – show the manual for command cp file1 file2 – copy file1 to file2 df – show disk usage cp -r dir1 dir2 – copy dir1 to dir2; create dir2 if it du – show directory space usage doesn't exist free – show memory and swap usage mv file1 file2 – rename or move file1 to file2 whereis app – show possible locations of app if file2 is an existing directory, moves file1 into which app – show which app will be run by default directory file2 ln -s file link – create symbolic link link to file Compression touch file – create or update file tar cf file.tar files – create a tar named cat > file – places standard input into file file.tar containing files more file – output the contents of file tar xf file.tar – extract the files from file.tar head file – output the first 10 lines of file tar czf file.tar.gz files – create a tar with tail file – output the last 10 lines -

Bash Crash Course + Bc + Sed + Awk∗
Bash Crash course + bc + sed + awk∗ Andrey Lukyanenko, CSE, Aalto University Fall, 2011 There are many Unix shell programs: bash, sh, csh, tcsh, ksh, etc. The comparison of those can be found on-line 1. We will primary focus on the capabilities of bash v.4 shell2. 1. Each bash script can be considered as a text file which starts with #!/bin/bash. It informs the editor or interpretor which tries to open the file, what to do with the file and how should it be treated. The special character set in the beginning #! is a magic number; check man magic and /usr/share/file/magic on existing magic numbers if interested. 2. Each script (assume you created “scriptname.sh file) can be invoked by command <dir>/scriptname.sh in console, where <dir> is absolute or relative path to the script directory, e.g., ./scriptname.sh for current directory. If it has #! as the first line it will be invoked by this command, otherwise it can be called by command bash <dir>/scriptname.sh. Notice: to call script as ./scriptname.sh it has to be executable, i.e., call command chmod 555 scriptname.sh before- hand. 3. Variable in bash can be treated as integers or strings, depending on their value. There are set of operations and rules available for them. For example: #!/bin/bash var1=123 # Assigns value 123 to var1 echo var1 # Prints ’var1’ to output echo $var1 # Prints ’123’ to output var2 =321 # Error (var2: command not found) var2= 321 # Error (321: command not found) var2=321 # Correct var3=$var2 # Assigns value 321 from var2 to var3 echo $var3 # Prints ’321’ to output -

Relational Constraint Driven Test Case Synthesis for Web Applications
Relational Constraint Driven Test Case Synthesis for Web Applications Xiang Fu Hofstra University Hempstead, NY 11549 [email protected] This paper proposes a relational constraint driven technique that synthesizes test cases automatically for web applications. Using a static analysis, servlets can be modeled as relational transducers, which manipulate backend databases. We present a synthesis algorithm that generates a sequence of HTTP requests for simulating a user session. The algorithm relies on backward symbolic image computation for reaching a certain database state, given a code coverage objective. With a slight adaptation, the technique can be used for discovering workflow attacks on web applications. 1 Introduction Modern web applications usually rely on backend database systems for storing important system infor- mation or supporting business decisions. The complexity of database queries, however, often complicates the task of thoroughly testing a web application. To manually design test cases involves labor intensive initialization of database systems, even with the help of unit testing tools such as SQLUnit [25] and DBUnit [8]. It is desirable to automatically synthesize test cases for web applications. There has been a strong interest recently in testing database driven applications and database man- agement systems (see e.g., [12, 4, 20]). Many of them are query aware, i.e., given a SQL query, an initial database (DB) instance is generated to make that query satisfiable. The DB instance is fed to the target web application as input, so that a certain code coverage goal is achieved. The problem we are trying to tackle is one step further – it is a synthesis problem: given a certain database state (or a relational constraint), a call sequence of web servlets is synthesized to reach the given DB state. -

Project1: Build a Small Scanner/Parser
Project1: Build A Small Scanner/Parser Introducing Lex, Yacc, and POET cs5363 1 Project1: Building A Scanner/Parser Parse a subset of the C language Support two types of atomic values: int float Support one type of compound values: arrays Support a basic set of language concepts Variable declarations (int, float, and array variables) Expressions (arithmetic and boolean operations) Statements (assignments, conditionals, and loops) You can choose a different but equivalent language Need to make your own test cases Options of implementation (links available at class web site) Manual in C/C++/Java (or whatever other lang.) Lex and Yacc (together with C/C++) POET: a scripting compiler writing language Or any other approach you choose --- must document how to download/use any tools involved cs5363 2 This is just starting… There will be two other sub-projects Type checking Check the types of expressions in the input program Optimization/analysis/translation Do something with the input code, output the result The starting project is important because it determines which language you can use for the other projects Lex+Yacc ===> can work only with C/C++ POET ==> work with POET Manual ==> stick to whatever language you pick This class: introduce Lex/Yacc/POET to you cs5363 3 Using Lex to build scanners lex.yy.c MyLex.l lex/flex lex.yy.c a.out gcc/cc Input stream a.out tokens Write a lex specification Save it in a file (MyLex.l) Compile the lex specification file by invoking lex/flex lex MyLex.l A lex.yy.c file is generated -

GNU M4, Version 1.4.7 a Powerful Macro Processor Edition 1.4.7, 23 September 2006
GNU M4, version 1.4.7 A powerful macro processor Edition 1.4.7, 23 September 2006 by Ren´eSeindal This manual is for GNU M4 (version 1.4.7, 23 September 2006), a package containing an implementation of the m4 macro language. Copyright c 1989, 1990, 1991, 1992, 1993, 1994, 2004, 2005, 2006 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.2 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled “GNU Free Documentation License.” i Table of Contents 1 Introduction and preliminaries ................ 3 1.1 Introduction to m4 ............................................. 3 1.2 Historical references ............................................ 3 1.3 Invoking m4 .................................................... 4 1.4 Problems and bugs ............................................. 8 1.5 Using this manual .............................................. 8 2 Lexical and syntactic conventions ............ 11 2.1 Macro names ................................................. 11 2.2 Quoting input to m4........................................... 11 2.3 Comments in m4 input ........................................ 11 2.4 Other kinds of input tokens ................................... 12 2.5 How m4 copies input to output ................................ 12 3 How to invoke macros........................ -
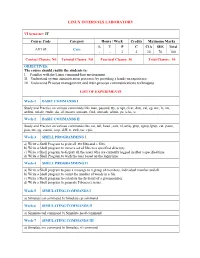
LINUX INTERNALS LABORATORY III. Understand Process
LINUX INTERNALS LABORATORY VI Semester: IT Course Code Category Hours / Week Credits Maximum Marks L T P C CIA SEE Total AIT105 Core - - 3 2 30 70 100 Contact Classes: Nil Tutorial Classes: Nil Practical Classes: 36 Total Classes: 36 OBJECTIVES: The course should enable the students to: I. Familiar with the Linux command-line environment. II. Understand system administration processes by providing a hands-on experience. III. Understand Process management and inter-process communications techniques. LIST OF EXPERIMENTS Week-1 BASIC COMMANDS I Study and Practice on various commands like man, passwd, tty, script, clear, date, cal, cp, mv, ln, rm, unlink, mkdir, rmdir, du, df, mount, umount, find, unmask, ulimit, ps, who, w. Week-2 BASIC COMMANDS II Study and Practice on various commands like cat, tail, head , sort, nl, uniq, grep, egrep,fgrep, cut, paste, join, tee, pg, comm, cmp, diff, tr, awk, tar, cpio. Week-3 SHELL PROGRAMMING I a) Write a Shell Program to print all .txt files and .c files. b) Write a Shell program to move a set of files to a specified directory. c) Write a Shell program to display all the users who are currently logged in after a specified time. d) Write a Shell Program to wish the user based on the login time. Week-4 SHELL PROGRAMMING II a) Write a Shell program to pass a message to a group of members, individual member and all. b) Write a Shell program to count the number of words in a file. c) Write a Shell program to calculate the factorial of a given number. -

EMERSON CENTER: HARDWARE Comp.Chem.20
EMERSON CENTER: HARDWARE comp.chem.20 ssh –Y [email protected] euch4e.chem.emory.edu Passwd: HOME=/home/chemistry/ch_res/eclab cd spark cd star cd fire $HOME/spark $HOME/star $HOME/fire mkdir USER mkdir USER mkdir USER cd USER cd USER cd USER # Nodes = 36 # Nodes = 36 # Nodes = 16 + 1 GPU # Cores/node = 24 # Cores/node = 24, 16 # Cores/node = 56 + 5000 # Speed = 2.6 GHz # Speed = 2.5 GHz # Speed = 2.6 GHz # Memory = 96 GB # Memory = 80 GB # Memory = 196 GB # Classes = spark24p # Classes = star24p # Classes = fire28p spark12p star16p fire-gpu star8p stars (1 core) spark (or spark.chem.emory.edu) star (or star.chem.emory.edu) fire (or fire.chem.emory.edu) Login the Emerson Center’s Computers From a Unix/MAC/iPad/iPhone terminal ssh -Y [email protected] From PC 1) Download and run PuTTY (www.putty.org) 2) Enable X-forwarding (Connection -> SSH -> Tunnels) 3) Under Session, choose SSH on port 22 4) Type euch4e.chem.emory.edu as host name 5) Click Open A few UNIX commands and vi Editor UNIX Tree Structure: Files and Directories cd - change directory: cd directory_name rm - remove command: rm file_name: also: rmdir, rm –I mv - move comman: mv file_name mkdir - make directory: mkdir directory_name cp - copy command: cp file_name_1 file_name_2 ls - list command VI (View) Command mode and Insert mode vi file_name Type i for insert command Use backspace in order to correct mistake :w :w! or :wq :wq! Write or write and quit :q :q! quit dd n delete o Insert line EMERSON CENTER: Software (Selected List) Electronic Structure MD Simulation & Modeling Gaussian-16, 09 GROMACS-19.1 Molpro-15.1 NAMD-2.6 MOLCAS Rosetta GAMESS Amber-14 TURBOMOLE ORCA VASP-5.2 DFTB+ Graphics & Programming MATLAB 2019 Mathematica 12.0 Gauss View 6 Command file (for LoadLeveler only): #!/bin/ksh # ### # @ error = errcl.log # # @ initialdir = /star/chemistry/eclab/YOUR # @ requirements = (Arch == "R6000") && (OpSys == "AIX53") # @ notify_user = name@euch4e # @ class = star16p # @ group = ch_res # @ queue # INPF= test_inp OUTF= test_out . -

GNU M4, Version 1.4.19 a Powerful Macro Processor Edition 1.4.19, 28 May 2021
GNU M4, version 1.4.19 A powerful macro processor Edition 1.4.19, 28 May 2021 by Ren´eSeindal, Fran¸coisPinard, Gary V. Vaughan, and Eric Blake ([email protected]) This manual (28 May 2021) is for GNU M4 (version 1.4.19), a package containing an implementation of the m4 macro language. Copyright c 1989{1994, 2004{2014, 2016{2017, 2020{2021 Free Software Foundation, Inc. Permission is granted to copy, distribute and/or modify this document under the terms of the GNU Free Documentation License, Version 1.3 or any later version published by the Free Software Foundation; with no Invariant Sections, no Front-Cover Texts, and no Back-Cover Texts. A copy of the license is included in the section entitled \GNU Free Documentation License." i Table of Contents 1 Introduction and preliminaries ::::::::::::::::: 3 1.1 Introduction to m4 :::::::::::::::::::::::::::::::::::::::::::::: 3 1.2 Historical references :::::::::::::::::::::::::::::::::::::::::::: 3 1.3 Problems and bugs ::::::::::::::::::::::::::::::::::::::::::::: 4 1.4 Using this manual :::::::::::::::::::::::::::::::::::::::::::::: 5 2 Invoking m4::::::::::::::::::::::::::::::::::::::: 7 2.1 Command line options for operation modes ::::::::::::::::::::: 7 2.2 Command line options for preprocessor features ::::::::::::::::: 8 2.3 Command line options for limits control ::::::::::::::::::::::: 10 2.4 Command line options for frozen state ::::::::::::::::::::::::: 11 2.5 Command line options for debugging :::::::::::::::::::::::::: 11 2.6 Specifying input files on the command line :::::::::::::::::::::