Physical Selection in Ubiquitous Computing
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Research Journal of Pharmaceutical, Biological and Chemical Sciences
ISSN: 0975-8585 Research Journal of Pharmaceutical, Biological and Chemical Sciences A Novel Framework for Fall Detection by Using Ambient Sensors and Voice Recording. P Megana Santhoshi1*, and Mythili Thirugnanam2. 1PhD scholar, School of Computer Science and Engineering (SCOPE), VIT University, Tamil Nadu, India 2School of Computer Science and Engineering (SCOPE), VIT University, Vellore-632014, Tamil Nadu, India. ABSTRACT Now a day’s falls are the second ruling cause to unintentional injury death of elderly person. Fall detection methods are introduced to assist the elderly person. For any type of patient irrespective of age, first one to two hours treatment is crucial at the time of emergency. Before starting the treatment, it would be very helpful if caregivers know exact injury type. This paper aims to propose a framework on IoT and cloud computing based fall detection scheme using ambient sensors along with voice recording. With the help of voice clip and fall alarm, patient had a feasibility to inform exact injury to hospital. Hospital people will facilitate relevant department services to start quick treatment. Keywords: Ambience based fall detection; voice recorder based health system; wireless sensor networks (WSN’s); IoT (Internet of Things); Cloud computing; smart health care system. *Corresponding author September – October 2016 RJPBCS 7(5) Page No. 2097 ISSN: 0975-8585 INTRODUCTION The number of persons above the age of 60 years is huge growing, especially in India. As per Indian government ministry of statistics, India is the second population country in the world having 1.21 Billion people. In that 35.5% of people are at or over the age of 60. -

Nokia 6010 User Guide
510636_6820_US/Eng_UG 12/18/03 10:36 AM Page 1 Thank you for purchasing your new Nokia phone. We’re here for you! www.nokiahowto.com Learn how to use your new Nokia phone. www.nokia.com/us Get answers to your questions. Register your phone’s limited warranty so we can better serve your needs! Nokia Inc. 7725 Woodland Center Boulevard, Suite 150, Tampa FL 33614 . Phone: 1.888.NOKIA.2U (1.888.665.4228) Fax: 1.813.249.9619 . Text Telephone/Telecommunication Device User Guide for the Deaf (TTY/TDD) Users: 1.800.24.NOKIA (1.800.246.6542) PRINTED IN CANADA 9311367 NOKIA 6820 Nokia 6010 User Guide What information is Numbers Where is the number? needed? My number Wireless service provider Voice mail number Wireless service provider Wireless provider’s Wireless service provider number Wireless provider’s Wireless service provider customer care Model number 6010 Label on back of phone (under battery) Phone type number NPM-10 Label on back of phone NPM-10X (under battery) International mobile Label on back of phone (under equipment identity battery). See “Find information (IMEI) about your phone” on page 7. LEGAL INFORMATION Part No. 9311233, Issue No. 1 Copyright © 2004 Nokia. All rights reserved. Nokia, Nokia Connecting People, Air Glide, Bowling, Backgammon, Sky Diver, Nokia 6010, Xpress-on, and the Nokia Original Enhancements logos are trademarks or registered trademarks of Nokia Corporation. Other company and product names mentioned herein may be trademarks or trade names of their respective owners. Printed in Canada 01/04 US Patent No 5818437 and other pending patents. -

THE UNIVERSITY of CALGARY Contextual Locations in the Home by Kathryn Kylie Elliot a THESIS SUBMITTED to the FACULTY of GRADUATE
THE UNIVERSITY OF CALGARY Contextual Locations in the Home by Kathryn Kylie Elliot A THESIS SUBMITTED TO THE FACULTY OF GRADUATE STUDIES IN PARTIAL FULFILMENT OF THE REQUIREMENTS FOR THE DEGREE OF MASTER OF SCIENCE DEPARTMENT OF COMPUTER SCIENCE CALGARY, ALBERTA DECEMBER, 2006 © Kathryn Kylie Elliot 2006 Approval Page THE UNIVERSITY OF CALGARY FACULTY OF GRADUATE STUDIES The undersigned certify that they have read, and recommend to the Faculty of Graduate Studies for acceptance, a thesis entitled “Contextual Locations in the Home” submitted by Kathryn Kylie Elliot in partial fulfillment of the requirements for the degree of Master of Science. Supervisor, Saul Greenberg Department of Computer Science Sheelagh Carpendale Department of Computer Science External Examiner, Barry Wylant Faculty of Environmental Design University of Calgary Date - ii - Abstract In this thesis, I address the problem of designing technology for communication and coordination information management in the home. First, I use contextual interviews to examine how households currently manage this information. From these interviews, I identify five types of communicative information. I then discuss how these types are created and understood by home inhabitants as a function of contextual locations within the home. The choice of location for a piece of information is important to the functioning of the home, and is highly nuanced. Location helps home inhabitants understand time, ownership and awareness. Finally, I show how this understanding can be applied in design through two case studies in location-based home technology design. This will provide practitioners and designers with a more complete view of information in the home, and a better understanding of how technology embedded within the home can augment communication and coordination of home inhabitants. -

Nokia 3300 Manual
Copyright © 2003 Nokia. All rights reserved. The wireless phone described in this guide is approved for use in 850 and 1900 GSM networks. LEGAL INFORMATION Part No. 9355979, Issue No. 1 Copyright ©2003 Nokia. All rights reserved. Nokia, Nokia Connecting People, Water Rapids, Virtual Me, Snake EX2, DJ, Nokia 3300, Xpress-on, and the Nokia Original Accessories logos are trademarks or registered trademarks of Nokia Corporation. All other product and company names mentioned herein may be trademarks or tradenames of their respective owners. Printed in Canada 06/2003 US Patent No 5818437 and other pending patents. Includes RSA BSAFE cryptographic or security protocol software from RSA Security. Java is a trademark of Sun Microsystems, Inc. The information in this user guide was written for the Nokia 3300 music phone. Nokia operates a policy of ongoing development. Nokia reserves the right to make changes and improvements to any of the products described in this document without prior notice. UNDER NO CIRCUMSTANCES SHALL NOKIA BE RESPONSIBLE FOR ANY LOSS OF DATA OR INCOME OR ANY SPECIAL, INCIDENTAL, AND CONSEQUENTIAL OR INDIRECT DAMAGES HOWSOEVER CAUSED. THE CONTENTS OF THIS DOCUMENT ARE PROVIDED “AS IS.” EXCEPT AS REQUIRED BY APPLICABLE LAW, NO WARRANTIES OF ANY KIND, EITHER EXPRESS OR IMPLIED, INCLUDING, BUT NOT LIMITED TO, THE IMPLIED WARRANTIES OF MERCHANTABILITY AND FITNESS FOR A PARTICULAR PURPOSE, ARE MADE IN RELATION TO THE ACCURACY AND RELIABILITY OR CONTENTS OF THIS DOCUMENT. NOKIA RESERVES THE RIGHT TO REVISE THIS DOCUMENT OR WITHDRAW IT AT ANY TIME WITHOUT PRIOR NOTICE. Copyright © 2003 Nokia. All rights reserved. EXPORT CONTROLS This product contains commodities, technology or software exported from the United States in accordance with the Export Administration regulations. -

Integrating Usability Models Into Pervasive Application Development
Integrating Usability Models into Pervasive Application Development Paul Holleis München 2008 Integrating Usability Models into Pervasive Application Development Paul Holleis Dissertation an der Fakultät für Mathematik, Informatik und Statistik der Ludwig-Maximilians-Universität München vorgelegt von Paul Holleis aus Bad Reichenhall München, den 15.12.2008 Erstgutachter: Prof. Dr. Albrecht Schmidt Zweitgutachter: Prof. Dr. Heinrich Hußmann Externer Gutachter: Prof. Dr. Antonio Krüger Tag der mündlichen Prüfung: 19.01.2009 To my dad, who would have enjoyed reading this thesis. Table of Contents vii Table of Contents 1 INTRODUCTION AND STRUCTURE .......................................................................................................... 1 1.1 GOALS AND CONTRIBUTIONS .......................................................................................................................... 1 1.2 STRUCTURE ................................................................................................................................................. 2 2 DEVELOPING PERVASIVE APPLICATIONS ................................................................................................ 3 2.1 PERVASIVE COMPUTING ................................................................................................................................. 3 2.1.1 Brief History and Overview .............................................................................................................. 3 2.1.2 Applications and Related Terms ..................................................................................................... -

Internet of Nano-Things, Things and Everything: Future Growth Trends
future internet Review Internet of Nano-Things, Things and Everything: Future Growth Trends Mahdi H. Miraz 1 ID , Maaruf Ali 2, Peter S. Excell 3,* and Richard Picking 3 1 Centre for Financial Regulation and Economic Development (CFRED), The Chinese University of Hong Kong, Sha Tin, Hong Kong, China; [email protected] 2 International Association of Educators and Researchers (IAER), Kemp House, 160 City Road, London EC1V 2NX, UK; [email protected] 3 Faculty of Art, Science and Technology, Wrexham Glyndwrˆ University, Wrexham LL11 2AW, UK; [email protected] * Correspondence: [email protected]; Tel.: +44-797-480-6644 Received: 22 June 2018; Accepted: 25 July 2018; Published: 28 July 2018 Abstract: The current statuses and future promises of the Internet of Things (IoT), Internet of Everything (IoE) and Internet of Nano-Things (IoNT) are extensively reviewed and a summarized survey is presented. The analysis clearly distinguishes between IoT and IoE, which are wrongly considered to be the same by many commentators. After evaluating the current trends of advancement in the fields of IoT, IoE and IoNT, this paper identifies the 21 most significant current and future challenges as well as scenarios for the possible future expansion of their applications. Despite possible negative aspects of these developments, there are grounds for general optimism about the coming technologies. Certainly, many tedious tasks can be taken over by IoT devices. However, the dangers of criminal and other nefarious activities, plus those of hardware and software errors, pose major challenges that are a priority for further research. Major specific priority issues for research are identified. -

Ambient Intelligence: Principles, Current Trends, Future Directions Manas Kumar Yogi * K
International Journals of Advanced Research in Computer Science and Software Engineering Research Article February ISSN: 2277-128X (Volume-8, Issue-2) a 2018 Ambient Intelligence: Principles, Current Trends, Future Directions Manas Kumar Yogi * K. Chandrasekhar Bhanu Prakash Asst. Prof., CSE Department, Asst. Prof., CSE Department, B.Tech II Year Student, CSE Pragati Engineering College, Pragati Engineering College, Department, Pragati Engineering Andhra Pradesh, India Andhra Pradesh, India College, Andhra Pradesh, India [email protected] [email protected] [email protected] Abstract— In this paper we have presented the involved principles, trends, future directions of ambient intelligence. in the first section we have elucidated concept of ambient intelligence with the prevalent need of intelligent communication with the help of designing knowledgeable entities. We have presented the design process of I-blocks with its inherent merits. we have also discussed the various design concepts of ambient intelligence objects. Finally, we presented the current research directions to motivate societal needs of human beings. Keywords— ambient, Computer Vision, intelligence, smart, ubiquitous I. INTRODUCTION This introductory paper describes Ambient Intelligence (AmI) from the perspectives of researchers working in the field of Artificial Intelligence and Computer Vision. It is for the reader to get acquainted with some of the ideas .That will be explored in greater detail in the following content .Ambient Intelligence is a term that was introduced by the European community to identify a paradigm to equip environments with advanced technology and computing to create an ergonomic space for the occupant user. Here the term ergonomic is used in a broad sense, encompassing both better living environment, secure space, but also an active, almost living space around us; capable of aiding us with daily chores and professional duties. -

Smarterforms Agents and Brokers Frequently Asked Question
EDGEWATER HOLDINGS, LTD. SmarterFORMS Agents and Brokers Frequently Asked Question A. Finding the SmarterFORM Online Q: Where is the SmarterFORM application? Your agent or broker may have sent to you, via email or text, a QR code to scan to take you to the form online using your default browser. Q: Is there a SmarterFORM app I need to download? No. SmarterFORM does not require any special downloads. Q: Which internet browsers work with SmarterFORM on my smartphone? SmarterFORM is compatible with: Safari on Apple devices, such as iPhones and iPads Chrome on Android devices, such as Samsung and Microsoft Windows brand phones Q: Which internet browsers will not work with SmarterFORM? Currently, Internet Explorer is not compatible. If you are using a Windows phone, you can use these alternate browsers instead: Maxthon (www.maxthon.com) UC Browser HD (www.ucweb.com) SurfCube (www.kinabaluinnovation.com) Nokia Xpress phone users: Nokia has a cloud-based browser app for Windows phone. The app can be downloaded from the Microsoft store (www.microsoft.com/en-us/store/apps/nokia- xpress/9wzdncrfhvgr) Q: Which internet browsers work with SmarterFORM on my desktop computer? SmarterFORM is compatible with most browsers, although we suggest using Safari on your Apple Macs and Chrome on desktops with a Windows operating system installed, such as Windows 7/8/8.1. Edge on Windows 10 is also compatible. Q: Which internet browsers will not work with SmarterFORM on my desktop computer? Currently, Internet Explorer is not compatible. Q: I did receive a QR Code of the application from my broker/agent on my smartphone? What is this thing and how do I use it? QR stands for Quick Response. -

Ambient Sensors for Elderly Care and Independent Living: a Survey
sensors Review Ambient Sensors for Elderly Care and Independent Living: A Survey Md. Zia Uddin * ID , Weria Khaksar and Jim Torresen Department of Informatics, University of Oslo, 0316 Oslo, Norway; weriak@ifi.uio.no (W.K.); jimtoer@ifi.uio.no (J.T.) * Correspondence: mdzu@ifi.uio.no; Tel.: +47-22-85-44-09 Received: 9 May 2018; Accepted: 18 June 2018; Published: 25 June 2018 Abstract: Elderly care at home is a matter of great concern if the elderly live alone, since unforeseen circumstances might occur that affect their well-being. Technologies that assist the elderly in independent living are essential for enhancing care in a cost-effective and reliable manner. Elderly care applications often demand real-time observation of the environment and the resident’s activities using an event-driven system. As an emerging area of research and development, it is necessary to explore the approaches of the elderly care system in the literature to identify current practices for future research directions. Therefore, this work is aimed at a comprehensive survey of non-wearable (i.e., ambient) sensors for various elderly care systems. This research work is an effort to obtain insight into different types of ambient-sensor-based elderly monitoring technologies in the home. With the aim of adopting these technologies, research works, and their outcomes are reported. Publications have been included in this survey if they reported mostly ambient sensor-based monitoring technologies that detect elderly events (e.g., activities of daily living and falls) with the aim of facilitating independent living. Mostly, different types of non-contact sensor technologies were identified, such as motion, pressure, video, object contact, and sound sensors. -

Indoor Localization Using Accidental Infrastructure
Delft University of Technology Master’s Thesis in Embedded Systems Indoor Localization using Accidental Infrastructure Zsolt Kocsi-Horvath´ Indoor Localization using Accidental Infrastructure Master’s Thesis in Embedded Systems Embedded Software Section Faculty of Electrical Engineering, Mathematics and Computer Science Delft University of Technology Mekelweg 4, 2628 CD Delft, The Netherlands Zsolt Kocsi-Horvath´ [email protected] 4th January 2013 Author Zsolt Kocsi-Horvath´ ([email protected]) Title Indoor Localization using Accidental Infrastructure MSc presentation 15. January 2013 Graduation Committee prof. dr. K. G. Langendoen (chair) Delft University of Technology dr. ir. A. Phillips ARM R&D, Cambridge ir. H. Vincent ARM R&D, Cambridge dr. S.O. Dulman Delft University of Technology dr. A. Iosup Delft University of Technology Abstract The level of the technological development of embedded devices is at a constant rise. We can foresee a near-future scenario where a huge number of semi-intelligent devices are part of our everyday environment, our homes, the public places and the office as well. The intelligent thermostat uploads the temperature readings to an on- line database; the fridge sends a tweet when we are out of milk; the coffee machine texts us when the coffee is ready. Each device has a unique and individual purpose. But what if they could be grouped together as a so-called accidental infrastructure to serve a more advanced cause? We have set out to demonstrate the possibilities of such an accidental infrastructure in the field of indoor localization. An ambient device in itself is not intentionally prepared for localization purposes, but using many of them together and combining the collected data can surpass the devices’ limited individual capabilities. -
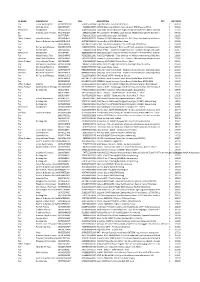
Amazon-62.Pdf
GL NAME SUBCATDESC Asin EAN DESCRIPTION QTY UNIT RETAIL Toy Junior Building Sets B01D9QON2W 5702015593946 Lego Star Wars 75159 Death Star‚?? 1 474,99 Toy All Other Dolls B00AK7SBPY 762988649687 HPI LRP Electronic 109291 - Sprint 2 Sport RTR Mustang RTR-X 1 419,92 Electronics Headphones B01LD5GO5U 4548736032804 Sony MDR-1000X kabelloser High-Resolution Kopfh??rer (Noise Cancelling, Sense Engine,1 351,05 NFC, Bluetooth, bis zu 20 Stunden Akkulaufzeit) schwarz PC Business Laser Printers B014VY6LD0 600169311384 HP LaserJet Pro M426fdw Laserdrucker Multifunktionsger?§t (Drucker, Scanner, Kopierer,1 349,00 Fax, WLAN, LAN, Duplex, HP ePrint, Airprint, NFC, USB, 4800 x 600 dpi) wei?ü Toy B077TZTDF6 5702016173536 Lego 10256 construcor,, 90721905 1 310,95 Office Product Voice Recorders B07F889RXN 4545350052072 Olympus DS-2600 Diktierger?§t inkl. DSS Player Standard-Lizenz (Mac & PC), LI-92B1 Lithium-Ionen-Akku, 275,60 KP30 Micro-USB-Kabel, CS151 Transporttasche Toy Electric & Battery Car SetsB07BPBH3KR / Access 4007486300026 Carrera Digital 132 DRM Retro Race 1 265,99 Toy B07DD8B92G 8411845011540 Feber - Ma Licorne Magique 12v, V?©hicule ?©lectrique 1 258,99 Toy Ps Figures & Playsets B002HDOOO6 4020972099051 Hochwertiges Reitpferd "Blitz" aus Pl??sch, zur echten Fortbewegung, mit Rollen und1 Lenkung, 256,00 ab 5 Jahren Toy Fashion Dolls B00T03U6AC 768421117614 Barbie FFY84 - Traumvilla Puppenhaus mit 7 Zimmer, Garage und Zubeh??r, mit Lichter1 und 254,17 Ger?§uschen, ca. 115 cm hoch, M?§dchen Spielzeug ab 3 Jahren Electronics Headphones B0178FT6BI -

TEI 2011 Work in Progress
Proceedings Editors: Ellen Yi-Luen Do (Georgia Tech, USA) Mark D. Gross (Carnegie Mellon University, USA) Ian Oakley (University of Madeira, Portugal) Cover Design: Mayur Karnik (University of Madeira, Portugal) Back Cover Photo: Antonio Gomes (Carnegie Mellon University, USA / University of Madeira, Portugal) TEI ʻ11 Work-in-Progress Table of Contents • Introduction: Work-in-Progress – Tangible, Embedded and Embodied Interaction ..............................................i • In Transit: Roam and Apparent Wind interaction design concepts..............................................................................1 Teresa Almeida (LASALLE College of the Arts) • The Milkscanner.................................................................................................................................................................................7 Friedrich Kirschner (Independent Researcher) • Ambient Storytelling: The Million Story Building...............................................................................................................13 Jennifer Stein, Scott S. Fisher (USC School of Cinematic Arts) • Interactive Blossoms......................................................................................................................................................................19 Shani Sharif, Martin L. Demaine (Massachusetts Institute of Technology) • “Assertive” Haptics for Music....................................................................................................................................................25