Optimization of Combinational Logic Circuits Based on Compatible Gates
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Logic Optimization and Synthesis: Trends and Directions in Industry
Logic Optimization and Synthesis: Trends and Directions in Industry Luca Amaru´∗, Patrick Vuillod†, Jiong Luo∗, Janet Olson∗ ∗ Synopsys Inc., Design Group, Sunnyvale, California, USA † Synopsys Inc., Design Group, Grenoble, France Abstract—Logic synthesis is a key design step which optimizes of specific logic styles and cell layouts. Embedding as much abstract circuit representations and links them to technology. technology information as possible early in the logic optimiza- With CMOS technology moving into the deep nanometer regime, tion engine is key to make advantageous logic restructuring logic synthesis needs to be aware of physical informations early in the flow. With the rise of enhanced functionality nanodevices, opportunities carry over at the end of the design flow. research on technology needs the help of logic synthesis to capture In this paper, we examine the synergy between logic synthe- advantageous design opportunities. This paper deals with the syn- sis and technology, from an industrial perspective. We present ergy between logic synthesis and technology, from an industrial technology aware synthesis methods incorporating advanced perspective. First, we present new synthesis techniques which physical information at the core optimization engine. Internal embed detailed physical informations at the core optimization engine. Experiments show improved Quality of Results (QoR) and results evidence faster timing closure and better correlation better correlation between RTL synthesis and physical implemen- between RTL synthesis and physical implementation. We elab- tation. Second, we discuss the application of these new synthesis orate on synthesis aware technology development, where logic techniques in the early assessment of emerging nanodevices with synthesis enables a fair system-level assessment on emerging enhanced functionality. -

Basic Boolean Algebra and Logic Optimization
Fundamental Algorithms for System Modeling, Analysis, and Optimization Edward A. Lee, Jaijeet Roychowdhury, Sanjit A. Seshia UC Berkeley EECS 144/244 Fall 2011 Copyright © 2010-11, E. A. Lee, J. Roychowdhury, S. A. Seshia, All rights reserved Lec 3: Boolean Algebra and Logic Optimization - 1 Thanks to S. Devadas, K. Keutzer, S. Malik, R. Rutenbar for several slides RTL Synthesis Flow FSM, HDL Verilog, HDL Simulation/ VHDL Verification RTL Synthesis a 0 d q Boolean circuit/network 1 netlist b Library/ s clk module logic generators optimization a 0 d q Boolean circuit/network netlist b 1 s clk physical design Graph / Rectangles layout K. Keutzer EECS 144/244, UC Berkeley: 2 Reduce Sequential Ckt Optimization to Combinational Optimization B Flip-flops inputs Combinational outputs Logic Optimize the size/delay/etc. of the combinational circuit (viewed as a Boolean network) EECS 144/244, UC Berkeley: 3 Logic Optimization 2-level Logic opt netlist tech multilevel independent Logic opt logic Library optimization tech dependent Generic Library netlist Real Library EECS 144/244, UC Berkeley: 4 Outline of Topics Basics of Boolean algebra Two-level logic optimization Multi-level logic optimization Boolean function representation: BDDs EECS 144/244, UC Berkeley: 5 Definitions – 1: What is a Boolean function? EECS 144/244, UC Berkeley: 6 Definitions – 1: What is a Boolean function? Let B = {0, 1} and Y = {0, 1} Input variables: X1, X2 …Xn Output variables: Y1, Y2 …Ym A logic function ff (or ‘Boolean’ function, switching function) in n inputs and m -

The Basics of Logic Design
C APPENDIX The Basics of Logic Design C.1 Introduction C-3 I always loved that C.2 Gates, Truth Tables, and Logic word, Boolean. Equations C-4 C.3 Combinational Logic C-9 Claude Shannon C.4 Using a Hardware Description IEEE Spectrum, April 1992 Language (Shannon’s master’s thesis showed that C-20 the algebra invented by George Boole in C.5 Constructing a Basic Arithmetic Logic the 1800s could represent the workings of Unit C-26 electrical switches.) C.6 Faster Addition: Carry Lookahead C-38 C.7 Clocks C-48 AAppendixC-9780123747501.inddppendixC-9780123747501.indd 2 226/07/116/07/11 66:28:28 PPMM C.8 Memory Elements: Flip-Flops, Latches, and Registers C-50 C.9 Memory Elements: SRAMs and DRAMs C-58 C.10 Finite-State Machines C-67 C.11 Timing Methodologies C-72 C.12 Field Programmable Devices C-78 C.13 Concluding Remarks C-79 C.14 Exercises C-80 C.1 Introduction This appendix provides a brief discussion of the basics of logic design. It does not replace a course in logic design, nor will it enable you to design signifi cant working logic systems. If you have little or no exposure to logic design, however, this appendix will provide suffi cient background to understand all the material in this book. In addition, if you are looking to understand some of the motivation behind how computers are implemented, this material will serve as a useful intro- duction. If your curiosity is aroused but not sated by this appendix, the references at the end provide several additional sources of information. -

Gate Logic Logic Optimization Overview
Lecture 5: Gate Logic Logic Optimization MAH, AEN EE271 Lecture 5 1 Overview Reading McCluskey, Logic Design Principles- or any text in boolean algebra Introduction We could design at the level of irsim - Think about transistors as switches - Build collections of switches that do useful stuff - Don’t much care whether the collection of transistors is a gate, switch logic, or some combination. It is a collection of switches. But this is pretty complicated - Switches are bidirectional, charge-sharing, - Need to worry about series resistance… MAH, AEN EE271 Lecture 5 2 Logic Gates Constrain the problem to simplify it. • Constrain how one can connect transistors - Create a collection of transistors where the Output is always driven by a switch-network to a supply (not an input) And the inputs to this unit only connect the gate of the transistors • Model this collection of transistors by a simpler abstraction Units are unidirectional Function is modelled by boolean operations Capacitance only affects speed and not functionality Delay through network is sum of delays of elements This abstract model is one we have used already. • It is a logic gate MAH, AEN EE271 Lecture 5 3 Logic Gates Come in various forms and sizes In CMOS, all of the primitive gates1 have one inversion from each input to the output. There are many versions of primitive gates. Different libraries have different collections. In general, most libraries have all 3 input gates (NAND, NOR, AOI, and OAI gates) and some 4 input gates. Most libraries are much richer, and have a large number of gates. -

Deep Learning for Logic Optimization Algorithms
Deep Learning for Logic Optimization Algorithms Winston Haaswijky∗, Edo Collinsz∗, Benoit Seguinx∗, Mathias Soekeny, Fred´ eric´ Kaplanx, Sabine Susstrunk¨ z, Giovanni De Micheliy yIntegrated Systems Laboratory, EPFL, Lausanne, VD, Switzerland zImage and Visual Representation Lab, EPFL, Lausanne, VD, Switzerland xDigital Humanities Laboratory, EPFL, Lausanne, VD, Switzerland ∗These authors contributed equally to this work Abstract—The slowing down of Moore’s law and the emergence to the state-of-the-art. Finally, our algorithm is a generic of new technologies puts an increasing pressure on the field optimization method. We show that it is capable of performing of EDA. There is a constant need to improve optimization depth optimization, obtaining 92.6% of potential improvement algorithms. However, finding and implementing such algorithms is a difficult task, especially with the novel logic primitives and in depth optimization of 3-input functions. Further, the MCNC potentially unconventional requirements of emerging technolo- case study shows that we unlock significant depth improvements gies. In this paper, we cast logic optimization as a deterministic over the academic state-of-the-art, ranging from 12.5% to Markov decision process (MDP). We then take advantage of 47.4%. recent advances in deep reinforcement learning to build a system that learns how to navigate this process. Our design has a II. BACKGROUND number of desirable properties. It is autonomous because it learns automatically and does not require human intervention. A. Deep Learning It generalizes to large functions after training on small examples. With ever growing data sets and increasing computational Additionally, it intrinsically supports both single- and multi- output functions, without the need to handle special cases. -
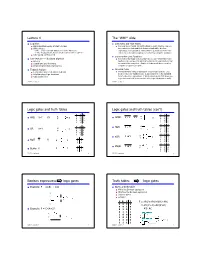
Logic Gates, Truth Tables and Canonical Forms
Lecture 4 The “WHY” slide ◆ Logistics ◆ Logic Gates and Truth Tables ■ HW1 due Wednesday at start of class ■ Now you know 0’s and 1’s and the basic Boolean algebra, now you ■ Office Hours: are ready to go back and forth between truth table, Boolean µ Me: 12:20-1:00 CSE 668 plus one later this week expression, and logic gates. This ability to go back and forth is an µ TAs: Today at 3:30, tomorrow at 12:30 & 2:30 in CSE 220 extremely useful skill designing and optimizing computer hardware. ■ Lab2 going on this week ◆ Implementing Logic Functions ◆ Last lecture --- Boolean algebra ■ Now with these basic tools you learned, you can “implement” logic ■ Axioms functions. We use Boolean algebra to implement logic functions that ■ Useful laws and theorems are used in the computers. And these logic functions are used by ■ Simplifying Boolean expressions computer programs you write. ◆ Today’s lecture ◆ Canonical forms ■ Logic gates and truth tables in detail ■ There are many forms to expression one Boolean function. It is ■ Implementing logic functions good to have one standard way. A canonical form is the standard ■ Canonical forms form for Boolean expressions. It has a nice property that allows you to go back and forth between truth table/expressions/gates easily. CSE370, Lecture 4 1 CSE370, Lecture 4 2 Logic gates and truth tables Logic gates and truth tables (con’t) XYZ XYZ X 0 0 0 X 0 0 1 ◆ Z ◆ NAND • Z AND X•Y XY Y 0 1 0 X Y XY Y 0 1 1 1 0 0 1 0 1 1 1 1 1 1 0 XYZ XYZ ◆ + X 0 0 1 NOR X Y Z 0 1 0 ◆ OR X+Y X Z 0 0 0 Y Y 0 1 1 1 0 0 1 1 0 1 0 1 -

Sequential Optimization for Low Power Digital Design
Sequential Optimization for Low Power Digital Design Aaron P. Hurst Electrical Engineering and Computer Sciences University of California at Berkeley Technical Report No. UCB/EECS-2008-75 http://www.eecs.berkeley.edu/Pubs/TechRpts/2008/EECS-2008-75.html May 30, 2008 Copyright © 2008, by the author(s). All rights reserved. Permission to make digital or hard copies of all or part of this work for personal or classroom use is granted without fee provided that copies are not made or distributed for profit or commercial advantage and that copies bear this notice and the full citation on the first page. To copy otherwise, to republish, to post on servers or to redistribute to lists, requires prior specific permission. Acknowledgement Advisor: Robert Brayton Sequential Optimization for Low Power Digital Design by Aaron Paul Hurst B.S. (Carnegie Mellon University) 2002 M.S. (Carnegie Mellon University) 2002 A dissertation submitted in partial satisfaction of the requirements for the degree of Doctor of Philosophy in Electrical Engineering and Computer Science in the GRADUATE DIVISION of the UNIVERSITY OF CALIFORNIA, BERKELEY Committee in charge: Professor Robert K. Brayton, Chair Professor Andreas Kuehlmann Professor Margaret Taylor Spring 2008 The dissertation of Aaron Paul Hurst is approved. Chair Date Date Date University of California, Berkeley Spring 2008 Sequential Optimization for Low Power Digital Design Copyright c 2008 by Aaron Paul Hurst Abstract Sequential Optimization for Low Power Digital Design by Aaron Paul Hurst Doctor of Philosophy in Electrical Engineering and Computer Science University of California, Berkeley Professor Robert K. Brayton, Chair The power consumed by digital integrated circuits has grown with increasing tran- sistor density and system complexity. -

Synthesis and Optimization of Synchronous Logic Circuits
SYNTHESIS AND OPTIMIZATION OF SYNCHRONOUS LOGIC CIRCUITS disserttion sumi ttedtothe deprtmentofeletrilengi neering ndtheommitteeongrdutestudies ofstnforduniversi ty in prtilfulfillmentoftherequirements forthedegreeof dotorofphilosophy By Maurizio Damiani May, 1994 I certify that I have read this thesis and that in my opinion it is fully adequate, in scope and in quality, as a dissertation for the degree of Doctor of Philosophy. Giovanni De Micheli (Principal Adviser) I certify that I have read this thesis and that in my opinion it is fully adequate, in scope and in quality, as a dissertation for the degree of Doctor of Philosophy. David L. Dill I certify that I have read this thesis and that in my opinion it is fully adequate, in scope and in quality, as a dissertation for the degree of Doctor of Philosophy. Teresa Meng Approved for the University Committee on Graduate Stud- ies: Dean of Graduate Studies ii Abstract The design automation of complex digital circuits offers important benefits. It allows the designer to reduce design time and errors, to explore more thoroughly the design space, and to cope effectively with an ever-increasing project complexity. This dissertation presents new algorithms for the logic optimization of combinational and synchronous digital circuits. These algorithms rely on a common paradigm. Namely, global optimization is achieved by the iterative local optimization of small subcircuits. The dissertation first explores the combinational case. Chapter 2 presents algorithms for the optimization of subnetworks consisting of a single-output subcircuit. The design space for this subcircuit is described implicitly by a Boolean function, a so-called don’t care function. Efficient methods for extracting this function are presented. -

Routing Architectures for Hierarchical Field Programmable Gate Arrays
Routing Architectures for Hierarchical Field Programmable Gate Arrays Aditya A. Aggarwal and David M. Lewis University of Toronto Department of Electrical and Computer Engineering Toronto, Ontario, Canada Abstract architecture to that of a symmetrical FPGA, and holding all other features constant, we hope to clarify the impact of This paper evaluates an architecture that implements a HFPGA architecture in isolation. hierarchical routing structure for FPGAs, called a hierarch- ical FPGA (HFPGA). A set of new tools has been used to The remainder of this paper studies the effect of rout- place and route several circuits on this architecture, with ing architectures in HFPGAs as an independent architec- the goal of comparing the cost of HFPGAs to conventional tural feature. It first defines an architecture for HFPGAs symmetrical FPGAs. The results show that HFF'GAs can with partially populated switch pattems. Experiments are implement circuits with fewer routing switches, and fewer then presented comparing the number of routing switches switches in total, compared to symmetrical FGPAs, required to the number required by a symmetrical FPGA. although they have the potential disadvantage that they Results for the total number of switches and tracks are also may require more logic blocks due to coarser granularity. given. 1. Introduction 2. Architecture and Area Models for HPFGAs Field programmable gate array architecture has been Figs. l(a) and I@) illustrate the components in a the subject of several studies that attempt to evaluate vari- HFPGA. An HFPGA consists of two types of primitive ous logic blocks and routing architectures, with the goals blocks, or level-0 blocks: logic blocks and U0 blocks. -

Testing and Logic Optimization Techniques for Systems on Chip
Linköping Studies in Science and Technology Dissertations. No. 1490 Testing and Logic Optimization Techniques for Systems on Chip by Tomas Bengtsson Department of Computer and Information Science Linköpings universitet SE-581 83 Linköping, Sweden Linköping 2012 Copyright © 2012 Tomas Bengtsson ISBN 978917519-7425 ISSN 03457524 Printed by LiU-Tryck 2012 URL: http://urn.kb.se/resolve?urn=urn:nbn:se:liu:diva-84806 Abstract Today it is possible to integrate more than one billion transistors onto a single chip. This has enabled implementation of complex functionality in hand held gadgets, but handling such complexity is far from trivial. The challenges of handling this complexity are mostly related to the design and testing of the digital components of these chips. A number of well-researched disciplines must be employed in the efficient design of large and complex chips. These include utilization of several abstraction levels, design of appropriate architectures, several different classes of optimization methods, and development of testing techniques. This thesis contributes mainly to the areas of design optimization and testing methods. In the area of testing this thesis contributes methods for testing of on-chip links connecting different clock domains. This includes testing for defects that introduce unacceptable delay, lead to excessive crosstalk and cause glitches, which can produce errors. We show how pure digital components can be used to detect such defects and how the tests can be scheduled efficiently. To manage increasing test complexity, another contribution proposes to raise the abstraction level of fault models from logic level to system level. A set of system level fault models for a NoC-switch is proposed and evaluated to demonstrate their potential. -

Lecture 1: Introduction to Digital Logic Design
CSE 140, Lecture 2 Combinational Logic CK Cheng CSE Dept. UC San Diego 1 Combinational Logic Outlines 1. Introduction • Scope • Boolean Algebra (Review) • Switching Functions, Logic Diagram and Truth Table • Handy Tools: DeMorgan’s Theorem, Consensus Theorem and Shannon’s Expansion 2. Specification 3. Synthesis 2 1.1 Combinational Logic: Scope • Description – Language: e.g. C Programming, BSV, Verilog, VHDL – Boolean algebra – Truth table: Powerful engineering tool • Design – Schematic Diagram – Inputs, Gates, Nets, Outputs • Goal – Validity: correctness, turnaround time – Performance: power, timing, cost – Testability: yield, diagnosis, robustness 3 Scope: Boolean algebra, switching algebra, logic • Boolean Algebra: multiple-valued logic, i.e. each variable have multiple values. • Switching Algebra: binary logic, i.e. each variable can be either 1 or 0. • Boolean Algebra ≠ Switching Algebra Switching Algebra BB Two Level Logic Boolean Algebra <4> Scope: Switching Algebra (Binary Values) • Typically consider only two discrete values: – 1’s and 0’s – 1, TRUE, HIGH – 0, FALSE, LOW • 1 and 0 can be represented by specific voltage levels, rotating gears, fluid levels, etc. • Digital circuits usually depend on specific voltage levels to represent 1 and 0 • Bit: Binary digit Copyright © 2007 1-<5> 5 Elsevier Scope: Levels of Logic • Multiple Level Logic: Many layers of two level logic with some inverters, e.g. (((a+bc)’+ab’)+b’c+c’d)’bc+c’e (A network of two level logic) • Two Level Logic: Sum of products, or product of sums, e.g. ab + a’c + a’b’, (a’+c )(a+b’)(a+b+c’) Features of Digital Logic Design • Multiple Outputs Boolean Algebra • Don’t care sets Switching Algebra BB Two Level Logic <6> 1.2 George Boole, 1815 - 1864 • Born to working class parents: Son of a shoemaker • Taught himself mathematics and joined the faculty of Queen’s College in Ireland. -

Automatic Implementation of a Re-Configurable Logic Over ASIC
FACULDADE DE ENGENHARIA DA UNIVERSIDADE DO PORTO Automatic implementation of a re-configurable logic over ASIC design flow José Delfim Ribeiro Valverde Mestrado Integrado em Engenharia Eletrotécnica e de Computadores Advisor: Prof. João Canas Ferreira Second Advisor: Eng. Luis Cruz July 4, 2017 © José Delfim Ribeiro Valverde, 2017 Resumo A indústria semicondutora tem enfrentado desafios devido à evolução dos circuitos integrados (Integrated Circuits, IC) para System–on–a–Chip (SoC), cujo design se encontra cada vez mais complexo. Assim, tem-se intensificado a necessidade de se efetuarem validações extensas dos circuitos, antes do processo de fabrico, de forma a assegurar um circuito produzido mais correto. Simultaneamente, com o intuito de dar resposta à atual procura de ciclos de produção mais rápidos, têm sido executados importantes testes de interoperabilidade no circuito final, em silício. Contudo, destes testes poderão resultar erros inesperados, obrigando à completa recusa do chip produzido e à necessidade de se iniciar novamente todo o ciclo de produção, despendendo tempo e recursos extra. Uma das soluções para este tipo de problemas corresponde à substituição do circuito original, de lógica fixa, por um implementado em lógica reconfigurável. Ao recorrer a este tipo de arquiteturas, o projetista fica habilitado a realizar pequenas alter- ações, localmente e em tempo útil, alterando algumas funcionalidades e corrigindo pequenos erros, resultantes dos testes de interoperabilidade efetuados em silício. De forma a incluir cir- cuitos reconfiguráveis em projetos para SoC, alguns fornecedores produzem e vendem núcleos programáveis do tipo hard para serem incluídos em projetos. Em oposição, outros fornecedores utilizam uma abordagem chamada soft, na qual vendem uma versão RTL (Register Transfer Level) da lógica programável, que pode ser sintetizada utilizando uma abordagem standard cell.