Basic Web Security Model
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Incoherencies in Web Browser Access Control Policies
On the Incoherencies in Web Browser Access Control Policies Kapil Singh∗, Alexander Moshchuk†, Helen J. Wang† and Wenke Lee∗ ∗Georgia Institute of Technology, Atlanta, GA Email: {ksingh, wenke}@cc.gatech.edu †Microsoft Research, Redmond, WA Email: {alexmos, helenw}@microsoft.com Abstract—Web browsers’ access control policies have evolved Inconsistent principal labeling. Today’s browsers do piecemeal in an ad-hoc fashion with the introduction of new not have the same principal definition for all browser re- browser features. This has resulted in numerous incoherencies. sources (which include the Document Object Model (DOM), In this paper, we analyze three major access control flaws in today’s browsers: (1) principal labeling is different for different network, cookies, other persistent state, and display). For resources, raising problems when resources interplay, (2) run- example, for the DOM (memory) resource, a principal is time changes to principal identities are handled inconsistently, labeled by the origin defined in the same origin policy and (3) browsers mismanage resources belonging to the user (SOP) in the form of <protocol, domain, port> [4]; but principal. We show that such mishandling of principals leads for the cookie resource, a principal is labeled by <domain, to many access control incoherencies, presenting hurdles for > web developers to construct secure web applications. path . Different principal definitions for two resources are A unique contribution of this paper is to identify the com- benign as long as the two resources do not interplay with patibility cost of removing these unsafe browser features. To do each other. However, when they do, incoherencies arise. For this, we have built WebAnalyzer, a crawler-based framework example, when cookies became accessible through DOM’s for measuring real-world usage of browser features, and used “document” object, DOM’s access control policy, namely the it to study the top 100,000 popular web sites ranked by Alexa. -

Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing
Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing VOLUME 2014 NO. 1 $ 7 . 9 9 PURITAS SPRINGS SOFTWARE Best Home Pages We think the importance of the through which you accessed INSIDE THIS ISSUE: home page has been greatly the world wide web. Once 1-3 reduced due to the invention of tabbed browsers arrived on the tabbed browsers. Although scene it was possible to create 1,4,5 conceived a group of 4 earlier in 1988, home pages Digital Inklings 6,7 tabbed brows- with each page Child Support 8 ing didn’t go being able to Spousal Support 10 mainstream “specialize” in a Uniform DR Forms 12 until the re- specific area of lease of Micro- your interest. Family Law Documents 13 soft’s Windows Take the Probate Forms 14 Internet Ex- weather for Ohio Estate Tax 16 plorer 7 in example. Every U.S. Income Tax (1041) 18 2006. Until then, your Home good home page should have Ohio Fiduciary Tax 19 page was the sole portal a minimal weather information; (Continued on page 2) Ohio Adoption Forms 20 OH Guardianship Forms 21 OH Wrongful Death 22 Loan Amortizer 23 # More Law Office Tech Tips Advanced Techniques 24 Deed & Document Pro 25 Bankruptcy Forms 26 XX. Quick Launch. The patch the application that you’re Law Office Management 28 of little icons to the right of the working in is maximized. If OH Business Forms 30 Start button is called the Quick you’re interested, take a look Launch toolbar. Sure, you can at the sidebar on page XX of Business Dissolutions 31 put much-used shortcuts on this issue. -

Ag Ex Factsheet 8
YouTube – Set up an Account Launched in 2005, YouTube is a video-sharing website, on which users can upload, view and share videos. Unregistered users can watch videos, but if you wish to upload your won videos, or post comments on other videos, you will need to set up an account. YouTube can be found at www.youtube.com As YouTube is now owned by Google, if you have a Google account, you will be able to sign in to YouTube by entering your Google Account What is a Google Account? username and password. If you're already signed into your Google Account on a different Google service, you'll be automatically signed in Google Accounts is a when you visit YouTube as well. If you don’t have a Google account, unified sign-in system that you will need to create one, in order to sign in to YouTube. gives you access to Google products, including iGoogle, 1. To create a Google account, follow this link: Gmail, Google Groups, https://accounts.google.com/SignUp?service=youtube Picasa, Web History, 2. Choose a username and enter in your contact information YouTube, and more. 3. Click “Next Step”. If you've used any of these 4. The next step is setting up your profile. You can upload or take a products before, you photo (if you have a webcam on your computer). You can skip this already have a Google step, and do it later, or not at all. Account. 5. Click “Next Step”. Your account username is the email address you 6. -

On the Disparity of Display Security in Mobile and Traditional Web Browsers
On the Disparity of Display Security in Mobile and Traditional Web Browsers Chaitrali Amrutkar, Kapil Singh, Arunabh Verma and Patrick Traynor Converging Infrastructure Security (CISEC) Laboratory Georgia Institute of Technology Abstract elements. The difficulty in efficiently accessing large pages Mobile web browsers now provide nearly equivalent fea- on mobile devices makes an adversary capable of abusing tures when compared to their desktop counterparts. How- the rendering of display elements particularly acute from a ever, smaller screen size and optimized features for con- security perspective. strained hardware make the web experience on mobile In this paper, we characterize a number of differences in browsers significantly different. In this paper, we present the ways mobile and desktop browsers render webpages that the first comprehensive study of the display-related security potentially allow an adversary to deceive mobile users into issues in mobile browsers. We identify two new classes of performing unwanted and potentially dangerous operations. display-related security problems in mobile browsers and de- Specifically, we examine the handling of user interaction vise a range of real world attacks against them. Addition- with overlapped display elements, the ability of malicious ally, we identify an existing security policy for display on cross-origin elements to affect the placement of honest el- desktop browsers that is inappropriate on mobile browsers. ements and the ability of malicious cross-origin elements Our analysis is comprised of eight mobile and five desktop to alter the navigation of honest parent and descendant el- browsers. We compare security policies for display in the ements. We then perform the same tests against a number candidate browsers to infer that desktop browsers are signif- of desktop browsers and find that the majority of desktop icantly more compliant with the policies as compared to mo- browsers are not vulnerable to the same rendering issues. -
Google Tightens Bonds with Youtube Users 7 May 2009
Google tightens bonds with YouTube users 7 May 2009 Google accounts provide access to iGoogle custom home pages, blog readers, text applications and other online services offered by the California firm. Google has been expected to weave YouTube, and hopefully its millions of users worldwide, into its online offerings since it bought the video-sharing site in 2006 for 1.65 billion dollars. (c) 2009 AFP YouTube webpage. People signing up for YouTube accounts automatically get matching Google accounts, YouTube software engineer James Phillips said in an official blog post on Thursday announcing the new development. Google is routing YouTube users further into the online search giant's Internet world. People signing up for YouTube accounts automatically get matching Google accounts, YouTube software engineer James Phillips said in an official blog post on Thursday announcing the new development. "We feel that by jointly connecting accounts, you can take greater advantage of our services both on YouTube and on Google," Phillips wrote. "Especially, as we start to roll out new features in the future that will be powered by Google technology." YouTube members who don't have Google accounts will still be able to use the popular online video-sharing service but might not be able to take advantage of new features that are added over time, according to Phillips. Feedback in an online forum accompanying the posting by Phillips ranged from "real cool" to "I hate it." 1 / 2 APA citation: Google tightens bonds with YouTube users (2009, May 7) retrieved 2 October 2021 from https://phys.org/news/2009-05-google-tightens-bonds-youtube-users.html This document is subject to copyright. -

Customization Features Done Correctly for the Right Reasons
Customization Features Done Correctly for the Right Reasons 46 Design Guidelines To Improve Web-based Interface and Product Customization Jen Cardello and Jakob Nielsen WWW.NNGROUP.COM 48105 WARM SPRINGS BLVD., FREMONT CA 94539–7498 USA COPYRIGHT © NIELSEN NORMAN GROUP, ALL RIGHTS RESERVED. To buy a copy, download from: http://www.nngroup.com/reports/customization About This Free Report This report is a gift for our loyal audience of UX enthusiasts. Thank you for your support over the years. We hope this information will aid your efforts to improve user experiences for everyone. The research for this report was done in 2013, however, the information presented is not just a snapshot in time. It is a compendium of professional advice based on experience gained over many years. We regularly publish new research reports that span a variety of web and UX related topics. These reports include thousands of actionable, illustrated user experience guidelines for creating and improving your web, mobile, and intranet sites. We sell our new reports to fund independent, unbiased usability research; we do not have investors, government funding, or research grants that pay for this work. Visit our reports page at https://www.nngroup.com/reports to see a complete list of these reports. HOW TO SHARE Do not link directly to the PDF file (the hosted address could change). Instead, we encourage you to distribute the following link to this reportÊs page on our website to allow people to decide whether to download it themselves: https://www.nngroup.com/reports/customization-features/ Copyright Notice Please do not post this document to the internet or to publicly available file-sharing services. -

Securing Frame Communication in Browsers by Adam Barth, Collin Jackson, and John C
DOI:10.1145/1516046.1516066 Securing Frame Communication in Browsers By Adam Barth, Collin Jackson, and John C. Mitchell Abstract map, or a photo album, the site runs the risk of incorporat- Many Web sites embed third-party content in frames, ing malicious content. Without isolation, malicious content relying on the browser’s security policy to protect against can compromise the confidentiality and integrity of the malicious content. However, frames provide insufficient user’s session with the integrator. Although the browser’s isolation in browsers that let framed content navigate well-known “same-origin policy”19 restricts script running other frames. We evaluate existing frame navigation poli- in one frame from manipulating content in another frame, cies and advocate a stricter policy, which we deploy in the browsers use a different policy to determine whether one open-source browsers. In addition to preventing undesir- frame is allowed to navigate (change the location of) another. able interactions, the browser’s strict isolation policy also Although browsers must restrict navigation to provide isola- affects communication between cooperating frames. We tion, navigation is the basis of one form of interframe com- therefore analyze two techniques for interframe communi- munication used by leading companies and navigation cation between isolated frames. The first method, fragment can be used to attack a second interframe communication identifier messaging, initially provides confidentiality with- mechanism. out authentication, which we repair using concepts from a Many recent browsers have overly permissive frame well-known network protocol. The second method, post- navigation policies that lead to a variety of attacks. To pre- Message, initially provides authentication, but we dis- vent attacks, we demonstrate against the Google AdSense cover an attack that breaches confidentiality. -
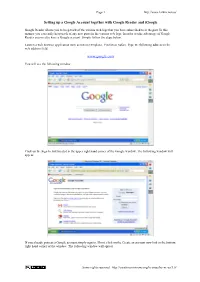
Setting up a Google Account Together with Google Reader and Igoogle
Page 1 http://www.larkin.net.au/ Setting up a Google Account together with Google Reader and iGoogle Google Reader allows you to keep track of the various web logs that you have subscribed to in the past. In this manner you can easily keep track of any new posts in the various web logs. In order to take advantage of Google Reader you need to have a Google account. Simply follow the steps below. Launch a web browser application such as Internet Explorer, Firefox or Safari. Type the following address in the web address field. www.google.com You will see the following window… Click on the Sign In link located in the upper right hand corner of the Google window. The following window will appear. If you already possess a Google account simply sign in. If not, click on the Create an account now link in the bottom right hand corner of the window. The following window will appear. Some rights reserved http://creativecommons.org/licenses/by-nc-sa/3.0/ Page 2 http://www.larkin.net.au/ Complete the details required to set up the account. Follow the instructions on each window step by step. Once you have created the account return to the main Google page at www.google.com. Are you still signed in? Some rights reserved http://creativecommons.org/licenses/by-nc-sa/3.0/ Page 3 http://www.larkin.net.au/ Setting Up Google Reader Select Reader from the more drop down menu at the top of the Google window. You will see the following window. -

Exporting Corruption?
Note: all materials under strict embargo until 06.09.2012 at 03:00 GMT EXPORTING CORRUPTION? COUNTRY ENFORCEMENT OF THE OECD ANTI-BRIBERY CONVENTION PROGRESS REPORT 2012 Note: all materials under strict embargo until 06.09.2012 at 03:00 GMT Transparency International is the global civil society organisation leading the fight against corruption. Through more than 90 chapters worldwide and an international secretariat in Berlin, we raise awareness of the damaging effects of corruption and work with partners in government, business and civil society to develop and implement effective measures to tackle it. Authors: Fritz Heimann and Gillian Dell www.transparency.org Contributors: Kelly McCarthy and Gabor Bathory Every effort has been made to verify the accuracy of the information contained in this report. All information was believed to be correct as of August 2012. Nevertheless, Transparency International cannot accept responsibility for the consequences of its use for other purposes or in other contexts. ISBN: 978-3-943497-25-0 ©2012 Transparency International. All rights reserved. Printed on 100% recycled paper. © Cover photo: Flickr/ecstaticist Note: all materials under strict embargo until 06.09.2012 at 03:00 GMT EXPORTING CORRUPTION? COUNTRY ENFORCEMENT OF THE OECD ANTI-BRIBERY CONVENTION PROGRESS REPORT 2012 Note: all materials under strict embargo until 06.09.2012 at 03:00 GMT Note: all materials under strict embargo until 06.09.2012 at 03:00 GMT TABLE OF CONTENTS I Introduction . 4 II Organisation and methodology . 5 III Conclusions and recommendations . 6 Table A: Foreign bribery enforcement in OECD Convention countries. 9 Table B: Status of foreign bribery cases. -

Web 2.0 Tutorials
Web 2.0 Tutorials This list, created by members of the RUSA MARS User Access to Services Committee, is a representative list of tutorials for some of the Web 2.0 products more commonly used in libraries. Link to delicious list (Username UASC, Password Martian1): http://delicious.com/UASC. Blogs Blogs in Plain English http://blip.tv/file/512104 The Common Craft Show Blogger Video Tutorials http://www.youtube.com/watch?v=ryb4VPSmKuo http://www.blogger.com/tour_start.g blogger.com EduBlogs Video Tutorials http://edublogs.org/videos/ Edublogs.com EduBlogs is a free blog hosting service for teaching and learning‐related blogs. Blogs come with 20 MB storage space and are listed in the EduBlogs directory. These tutorials describe how to sign up for the service and create a blog. Wikis Wikis in Plain English http://blip.tv/file/246821 The Common Craft Show Wikipedia Tutorial http://en.wikipedia.org/wiki/Wikipedia_tutorial Wikipedia.com RSS Syndication (e.g. blog or wiki content) W3 Schools RSS Tutorial http://www.w3schools.com/rss/default.asp W3 Schools Describes how to add code to a web site to syndicate its content through RSS (Rich Site Syndication). This site also includes excellent tutorials on XHTML and CSS. What is RSS? http://rss.softwaregarden.com/aboutrss.html Software Garden A basic tutorial introduction to RSS feeds and aggregators for non‐technical people. 1 Feedburner Tutorials http://www.feedburner.com/fb/a/feed101;jsessionid=01563D5FFE69D3CD555134F7280 feedburner.com Mashups Google Mashups Using Flickr and Google Earth http://library.csun.edu/seals/SEALGISBrownGoogleMashups.pdf Mitchell C. Brown, University of California Irvine Mashup Tutorials http://www.deitel.com/ResourceCenters/Web20/Mashups/MashupTutorials/tabid/985/Default.aspx Deitel & Associates VoIP/IM Services Skype Tutorials http://www.tutorpipe.com/free_cat.php?fl=1# Tutorialpipe.com Site contains numerous free tutorials on Skype, Dreamweaver and Google Apps. -

Deka Amarjyoti T 2010.Pdf (1.614Mb)
ScriptSpaces: An Isolation Abstraction for Web Browsers Amarjyoti Deka Thesis submitted to the Faculty of the Virginia Polytechnic Institute and State University in partial fulfillment of the requirements for the degree of Master of Science in Computer Science and Applications Godmar V. Back, Chair Barbara G. Ryder Eli Tilevich July 22, 2010 Blacksburg, Virginia Keywords: Web Browsers, Isolation, JavaScript, Resource Control Copyright c Amarjyoti Deka 2010 ScriptSpaces: An Isolation Abstraction for Web Browsers Amarjyoti Deka ABSTRACT Current web browsers are ill-prepared to manage execution of scripts embedded in web pages, because they treat all JavaScript code executing in a page as one unit. All code shares the same namespace, same security domain, and shares uncontrolled access to the same heap; some browsers even use the same thread for multiple tabs or windows. This lack of isola- tion frequently causes problems that range from loss of functionality to security compromises. ScriptSpace is an abstraction that provides separate, isolated execution environments for parts or all of a web page. Within each ScriptSpace, we maintain the traditional, single- threaded JavaScript environment to provide compatibility with existing code written under this assumption. Multiple ScriptSpaces within a page are isolated with respect to names- pace, CPU, and memory consumption. The user has the ability to safely terminate failing scripts without affecting the functionality of still-functional components of the page, or of other pages. We implemented a prototype of ScriptSpace based on the Firefox 3.0 browser. Rather than mapping ScriptSpaces to OS-level threads, we exploit a migrating-thread model in which threads enter and leave the ScriptSpaces associated with the respective sections of the docu- ment tree during the event dispatching process. -

Google Scholar Como Una Fuente De Evaluación Científica: Una Revisión Bibliográfica Sobre Errores De La Base De Datos
Revista Española de Documentación Científica 40(4), octubre-diciembre 2017, e185 ISSN-L:0210-0614. doi: http://dx.doi.org/10.3989/redc.2017.4.1500 ESTUDIOS / RESEARCH STUDIES Google Scholar as a source for scholarly evaluation: a bibliographic review of database errors Enrique Orduna-Malea*, Alberto Martín-Martín**, Emilio Delgado López-Cózar** * Universitat Politècnica de València e-mail: [email protected] | ORCID iD: http://orcid.org/0000-0002-1989-8477 ** Facultad de Comunicación y Documentación. Universidad de Granada e-mail: [email protected] | ORCID iD: http://orcid.org/0000-0002-0360-186X e-mail: [email protected] | ORCID iD: http://orcid.org/0000-0002-8184-551X Received: 17-07-2017; Accepted: 08-09-2017. Citation/Cómo citar este artículo: Orduna-Malea, E.; Martín-Martín, A.; Delgado López-Cózar, E. (2017). Google Scholar as a source for scholarly evaluation: a bibliographic review of database errors. Revista Española de Documentación Científica, 40(4): e185. doi: http://dx.doi.org/10.3989/redc.2017.4.1500 Abstract: Google Scholar (GS) is an academic search engine and discovery tool launched by Google (now Alphabet) in November 2004. The fact that GS provides the number of citations received by each article from all other indexed articles (regardless of their source) has led to its use in bibliometric analysis and academic assessment tasks, especially in social sciences and humanities. However, the existence of errors, sometimes of great magnitude, has provoked criticism from the academic community. The aim of this article is to carry out an exhaustive bibliographical review of all studies that provide either specific or incidental empirical evidence of the errors found in Google Scholar.