Securing Frame Communication in Browsers by Adam Barth, Collin Jackson, and John C
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

On the Incoherencies in Web Browser Access Control Policies
On the Incoherencies in Web Browser Access Control Policies Kapil Singh∗, Alexander Moshchuk†, Helen J. Wang† and Wenke Lee∗ ∗Georgia Institute of Technology, Atlanta, GA Email: {ksingh, wenke}@cc.gatech.edu †Microsoft Research, Redmond, WA Email: {alexmos, helenw}@microsoft.com Abstract—Web browsers’ access control policies have evolved Inconsistent principal labeling. Today’s browsers do piecemeal in an ad-hoc fashion with the introduction of new not have the same principal definition for all browser re- browser features. This has resulted in numerous incoherencies. sources (which include the Document Object Model (DOM), In this paper, we analyze three major access control flaws in today’s browsers: (1) principal labeling is different for different network, cookies, other persistent state, and display). For resources, raising problems when resources interplay, (2) run- example, for the DOM (memory) resource, a principal is time changes to principal identities are handled inconsistently, labeled by the origin defined in the same origin policy and (3) browsers mismanage resources belonging to the user (SOP) in the form of <protocol, domain, port> [4]; but principal. We show that such mishandling of principals leads for the cookie resource, a principal is labeled by <domain, to many access control incoherencies, presenting hurdles for > web developers to construct secure web applications. path . Different principal definitions for two resources are A unique contribution of this paper is to identify the com- benign as long as the two resources do not interplay with patibility cost of removing these unsafe browser features. To do each other. However, when they do, incoherencies arise. For this, we have built WebAnalyzer, a crawler-based framework example, when cookies became accessible through DOM’s for measuring real-world usage of browser features, and used “document” object, DOM’s access control policy, namely the it to study the top 100,000 popular web sites ranked by Alexa. -

Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing
Volume 2014, No. 1 Law Office Computing Page Puritas Springs Software Law Office Computing VOLUME 2014 NO. 1 $ 7 . 9 9 PURITAS SPRINGS SOFTWARE Best Home Pages We think the importance of the through which you accessed INSIDE THIS ISSUE: home page has been greatly the world wide web. Once 1-3 reduced due to the invention of tabbed browsers arrived on the tabbed browsers. Although scene it was possible to create 1,4,5 conceived a group of 4 earlier in 1988, home pages Digital Inklings 6,7 tabbed brows- with each page Child Support 8 ing didn’t go being able to Spousal Support 10 mainstream “specialize” in a Uniform DR Forms 12 until the re- specific area of lease of Micro- your interest. Family Law Documents 13 soft’s Windows Take the Probate Forms 14 Internet Ex- weather for Ohio Estate Tax 16 plorer 7 in example. Every U.S. Income Tax (1041) 18 2006. Until then, your Home good home page should have Ohio Fiduciary Tax 19 page was the sole portal a minimal weather information; (Continued on page 2) Ohio Adoption Forms 20 OH Guardianship Forms 21 OH Wrongful Death 22 Loan Amortizer 23 # More Law Office Tech Tips Advanced Techniques 24 Deed & Document Pro 25 Bankruptcy Forms 26 XX. Quick Launch. The patch the application that you’re Law Office Management 28 of little icons to the right of the working in is maximized. If OH Business Forms 30 Start button is called the Quick you’re interested, take a look Launch toolbar. Sure, you can at the sidebar on page XX of Business Dissolutions 31 put much-used shortcuts on this issue. -

La Promotion Du Web Ouvert a Bien Changé Mais Mozilla Est Toujours Là
La promotion du Web Ouvert a bien changé mais Mozilla est toujours là Promouvoir le Web ouvert est l’une des missions de Mozilla. Mission parfaitement assumée et réussie il y a quelques années avec l’avènement de Firefox qui obligea Internet Explorer à quitter son arrogance pour rentrer dans le rang et se montrer plus respectueux des standards et donc des internautes. Sauf qu’aujourd’hui la donne a sensiblement changé. Avec la mobilité, les stores, les apps, les navigateurs intégrés, etc. c’est en effet un Web bien plus complexe qui se présente devant nous. Un Web enthousiasmant[1] mais plein d’embûches pour ceux qui sont attachés à son ouverture et à sa neutralité. C’est tout l’objet de ce très intéressant récent billet du développeur Mozilla Robert O’Callahan. Des changements dans la façon de promouvoir le Web Ouvert Shifts In Promoting The Open Web Robert O’Callahan – 30 septembre 201 – Blog personnel (Traduction Framalang : Antistress et Goofy) Historiquement Mozilla a dépensé pas mal d’énergie pour promouvoir l’usage du « Web ouvert » plutôt que de plateformes propriétaires et de code spécifique à des navigateurs non standards (IE6). Cette évangélisation reste nécessaire mais le paysage s’est modifié et je pense que notre discours doit s’adapter. Les plateformes dont nous devons nous préoccuper ont beaucoup changé. Au lieu de WPF, Slivertlight and Flash, les outils propriétaires pour développeurs avec lesquelles il faut rivaliser dorénavant sont iOS et Android. En conséquence, les fonctionnalités que le Web doit intégrer sont à présent orientées vers la mobilité. -

Ag Ex Factsheet 8
YouTube – Set up an Account Launched in 2005, YouTube is a video-sharing website, on which users can upload, view and share videos. Unregistered users can watch videos, but if you wish to upload your won videos, or post comments on other videos, you will need to set up an account. YouTube can be found at www.youtube.com As YouTube is now owned by Google, if you have a Google account, you will be able to sign in to YouTube by entering your Google Account What is a Google Account? username and password. If you're already signed into your Google Account on a different Google service, you'll be automatically signed in Google Accounts is a when you visit YouTube as well. If you don’t have a Google account, unified sign-in system that you will need to create one, in order to sign in to YouTube. gives you access to Google products, including iGoogle, 1. To create a Google account, follow this link: Gmail, Google Groups, https://accounts.google.com/SignUp?service=youtube Picasa, Web History, 2. Choose a username and enter in your contact information YouTube, and more. 3. Click “Next Step”. If you've used any of these 4. The next step is setting up your profile. You can upload or take a products before, you photo (if you have a webcam on your computer). You can skip this already have a Google step, and do it later, or not at all. Account. 5. Click “Next Step”. Your account username is the email address you 6. -

Communications Cacm.Acm.Org of Theacm 06/2009 Vol.52 No.06
COMMUNICATIONS CACM.ACM.ORG OF THEACM 06/2009 VOL.52 NO.06 One Laptop Per Child: Vision vs. Reality Hard-Disk Drives: The Good, The Bad, and the Ugly How CS Serves The Developing World Network Front-End Processors The Claremont Report On Database Research Autonomous Helicopters Association for Computing Machinery Think Parallel..... It’s not just what we make. It’s what we make possible. Advancing Technology Curriculum Driving Software Evolution Fostering Tomorrow’s Innovators Learn more at: www.intel.com/thinkparallel ACM Ad.indd 1 4/17/2009 11:20:03 AM ABCD springer.com Noteworthy Computer Science Journals Autonomous Biological Personal and Robots Cybernetics Ubiquitous G. Sukhatme, University W. Senn, Universität Bern, Computing of Southern California, Physiologisches Institut; ACM Viterbi School of Engi- J. Rinzel, National neering, Dept. Computer Institutes of Health (NIH), P. Thomas, Univ. Coll. Science Dept. Health Education & London Interaction Centre Autonomous Robots Welfare; J. L. van Hemmen, reports on the theory and TU München, Abt. Physik Personal and Ubiquitous applications of robotic systems capable of Biological Cybernetics is an interdisciplinary Computing publishes peer-reviewed some degree of self-sufficiency. It features medium for experimental, theoretical and international research on handheld, wearable papers that include performance data on actual application-oriented aspects of information and mobile information devices and the robots in the real world. The focus is on the processing in organisms, including sensory, pervasive communications infrastructure that ability to move and be self-sufficient, not on motor, cognitive, and ecological phenomena. supports them to enable the seamless whether the system is an imitation of biology. -

Introducing HTML5.Pdf
ptg HTMLINTRODUCING 5 ptg BRUCE LAWSON REMY SHARP Introducing HTML5 Bruce Lawson and Remy Sharp New Riders 1249 Eighth Street Berkeley, CA 94710 510/524-2178 510/524-2221 (fax) Find us on the Web at: www.newriders.com To report errors, please send a note to [email protected] New Riders is an imprint of Peachpit, a division of Pearson Education Copyright © 2011 by Remy Sharp and Bruce Lawson Project Editor: Michael J. Nolan Development Editor: Jeff Riley/Box Twelve Communications Technical Editors: Patrick H. Lauke (www.splintered.co.uk), Robert Nyman (www.robertnyman.com) Production Editor: Cory Borman Copyeditor: Doug Adrianson Proofreader: Darren Meiss Compositor: Danielle Foster Indexer: Joy Dean Lee Back cover author photo: Patrick H. Lauke Notice of Rights ptg All rights reserved. No part of this book may be reproduced or transmitted in any form by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. For informa- tion on getting permission for reprints and excerpts, contact permissions@ peachpit.com. Notice of Liability The information in this book is distributed on an “As Is” basis without war- ranty. While every precaution has been taken in the preparation of the book, neither the authors nor Peachpit shall have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the instructions contained in this book or by the com- puter software and hardware products described in it. Trademarks Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. -

0321687299.Pdf
Introducing HTML5 Bruce Lawson and Remy Sharp New Riders 1249 Eighth Street Berkeley, CA 94710 510/524-2178 510/524-2221 (fax) Find us on the Web at: www.newriders.com To report errors, please send a note to [email protected] New Riders is an imprint of Peachpit, a division of Pearson Education Copyright © 2011 by Remy Sharp and Bruce Lawson Project Editor: Michael J. Nolan Development Editor: Jeff Riley/Box Twelve Communications Technical Editors: Patrick H. Lauke (www.splintered.co.uk), Robert Nyman (www.robertnyman.com) Production Editor: Cory Borman Copyeditor: Doug Adrianson Proofreader: Darren Meiss Compositor: Danielle Foster Indexer: Joy Dean Lee Back cover author photo: Patrick H. Lauke Notice of Rights All rights reserved. No part of this book may be reproduced or transmitted in any form by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. For informa- tion on getting permission for reprints and excerpts, contact permissions@ peachpit.com. Notice of Liability The information in this book is distributed on an “As Is” basis without war- ranty. While every precaution has been taken in the preparation of the book, neither the authors nor Peachpit shall have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the instructions contained in this book or by the com- puter software and hardware products described in it. Trademarks Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. Where those designations appear in this book, and Peachpit was aware of a trademark claim, the designa- tions appear as requested by the owner of the trademark. -

On the Disparity of Display Security in Mobile and Traditional Web Browsers
On the Disparity of Display Security in Mobile and Traditional Web Browsers Chaitrali Amrutkar, Kapil Singh, Arunabh Verma and Patrick Traynor Converging Infrastructure Security (CISEC) Laboratory Georgia Institute of Technology Abstract elements. The difficulty in efficiently accessing large pages Mobile web browsers now provide nearly equivalent fea- on mobile devices makes an adversary capable of abusing tures when compared to their desktop counterparts. How- the rendering of display elements particularly acute from a ever, smaller screen size and optimized features for con- security perspective. strained hardware make the web experience on mobile In this paper, we characterize a number of differences in browsers significantly different. In this paper, we present the ways mobile and desktop browsers render webpages that the first comprehensive study of the display-related security potentially allow an adversary to deceive mobile users into issues in mobile browsers. We identify two new classes of performing unwanted and potentially dangerous operations. display-related security problems in mobile browsers and de- Specifically, we examine the handling of user interaction vise a range of real world attacks against them. Addition- with overlapped display elements, the ability of malicious ally, we identify an existing security policy for display on cross-origin elements to affect the placement of honest el- desktop browsers that is inappropriate on mobile browsers. ements and the ability of malicious cross-origin elements Our analysis is comprised of eight mobile and five desktop to alter the navigation of honest parent and descendant el- browsers. We compare security policies for display in the ements. We then perform the same tests against a number candidate browsers to infer that desktop browsers are signif- of desktop browsers and find that the majority of desktop icantly more compliant with the policies as compared to mo- browsers are not vulnerable to the same rendering issues. -
Google Tightens Bonds with Youtube Users 7 May 2009
Google tightens bonds with YouTube users 7 May 2009 Google accounts provide access to iGoogle custom home pages, blog readers, text applications and other online services offered by the California firm. Google has been expected to weave YouTube, and hopefully its millions of users worldwide, into its online offerings since it bought the video-sharing site in 2006 for 1.65 billion dollars. (c) 2009 AFP YouTube webpage. People signing up for YouTube accounts automatically get matching Google accounts, YouTube software engineer James Phillips said in an official blog post on Thursday announcing the new development. Google is routing YouTube users further into the online search giant's Internet world. People signing up for YouTube accounts automatically get matching Google accounts, YouTube software engineer James Phillips said in an official blog post on Thursday announcing the new development. "We feel that by jointly connecting accounts, you can take greater advantage of our services both on YouTube and on Google," Phillips wrote. "Especially, as we start to roll out new features in the future that will be powered by Google technology." YouTube members who don't have Google accounts will still be able to use the popular online video-sharing service but might not be able to take advantage of new features that are added over time, according to Phillips. Feedback in an online forum accompanying the posting by Phillips ranged from "real cool" to "I hate it." 1 / 2 APA citation: Google tightens bonds with YouTube users (2009, May 7) retrieved 2 October 2021 from https://phys.org/news/2009-05-google-tightens-bonds-youtube-users.html This document is subject to copyright. -

Customization Features Done Correctly for the Right Reasons
Customization Features Done Correctly for the Right Reasons 46 Design Guidelines To Improve Web-based Interface and Product Customization Jen Cardello and Jakob Nielsen WWW.NNGROUP.COM 48105 WARM SPRINGS BLVD., FREMONT CA 94539–7498 USA COPYRIGHT © NIELSEN NORMAN GROUP, ALL RIGHTS RESERVED. To buy a copy, download from: http://www.nngroup.com/reports/customization About This Free Report This report is a gift for our loyal audience of UX enthusiasts. Thank you for your support over the years. We hope this information will aid your efforts to improve user experiences for everyone. The research for this report was done in 2013, however, the information presented is not just a snapshot in time. It is a compendium of professional advice based on experience gained over many years. We regularly publish new research reports that span a variety of web and UX related topics. These reports include thousands of actionable, illustrated user experience guidelines for creating and improving your web, mobile, and intranet sites. We sell our new reports to fund independent, unbiased usability research; we do not have investors, government funding, or research grants that pay for this work. Visit our reports page at https://www.nngroup.com/reports to see a complete list of these reports. HOW TO SHARE Do not link directly to the PDF file (the hosted address could change). Instead, we encourage you to distribute the following link to this reportÊs page on our website to allow people to decide whether to download it themselves: https://www.nngroup.com/reports/customization-features/ Copyright Notice Please do not post this document to the internet or to publicly available file-sharing services. -
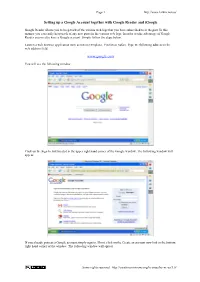
Setting up a Google Account Together with Google Reader and Igoogle
Page 1 http://www.larkin.net.au/ Setting up a Google Account together with Google Reader and iGoogle Google Reader allows you to keep track of the various web logs that you have subscribed to in the past. In this manner you can easily keep track of any new posts in the various web logs. In order to take advantage of Google Reader you need to have a Google account. Simply follow the steps below. Launch a web browser application such as Internet Explorer, Firefox or Safari. Type the following address in the web address field. www.google.com You will see the following window… Click on the Sign In link located in the upper right hand corner of the Google window. The following window will appear. If you already possess a Google account simply sign in. If not, click on the Create an account now link in the bottom right hand corner of the window. The following window will appear. Some rights reserved http://creativecommons.org/licenses/by-nc-sa/3.0/ Page 2 http://www.larkin.net.au/ Complete the details required to set up the account. Follow the instructions on each window step by step. Once you have created the account return to the main Google page at www.google.com. Are you still signed in? Some rights reserved http://creativecommons.org/licenses/by-nc-sa/3.0/ Page 3 http://www.larkin.net.au/ Setting Up Google Reader Select Reader from the more drop down menu at the top of the Google window. You will see the following window. -

Introducing HTML5 Second Edition
HTMLINTRODUCING SECOND 5EDITION BRUCE LAWSON REMY SHARP Introducing HTML5, Second Edition Bruce Lawson and Remy Sharp New Riders 1249 Eighth Street Berkeley, CA 94710 510/524-2178 510/524-2221 (fax) Find us on the Web at: www.newriders.com To report errors, please send a note to [email protected] New Riders is an imprint of Peachpit, a division of Pearson Education Copyright © 2012 by Remy Sharp and Bruce Lawson Project Editor: Michael J. Nolan Development Editor: Margaret S. Anderson/Stellarvisions Technical Editors: Patrick H. Lauke (www.splintered.co.uk), Robert Nyman (www.robertnyman.com) Production Editor: Cory Borman Copyeditor: Gretchen Dykstra Proofreader: Jan Seymour Indexer: Joy Dean Lee Compositor: Danielle Foster Cover Designer: Aren Howell Straiger Cover photo: Patrick H. Lauke (splintered.co.uk) Notice of Rights All rights reserved. No part of this book may be reproduced or transmitted in any form by any means, electronic, mechanical, photocopying, recording, or otherwise, without the prior written permission of the publisher. For informa- tion on getting permission for reprints and excerpts, contact permissions@ peachpit.com. Notice of Liability The information in this book is distributed on an “As Is” basis without war- ranty. While every precaution has been taken in the preparation of the book, neither the authors nor Peachpit shall have any liability to any person or entity with respect to any loss or damage caused or alleged to be caused directly or indirectly by the instructions contained in this book or by the com- puter software and hardware products described in it. Trademarks Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks.