Ipv6 Cheat Sheet, 09/2011
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

15-744: Computer Networking Multicast Routing Example Applications Overview
Multicast Routing • Unicast: one source to one destination • Multicast: one source to many destinations 15-744: Computer Networking • Two main functions: • Efficient data distribution • Logical naming of a group L-20 Multicast 2 Example Applications Overview • Broadcast audio/video • IP Multicast Service Basics • Push-based systems • Software distribution • Multicast Routing Basics • Web-cache updates • Teleconferencing (audio, video, shared • Overlay Multicast whiteboard, text editor) • Multi-player games • Reliability • Server/service location • Other distributed applications • Congestion Control 3 4 1 IP Multicast Architecture Multicast – Efficient Data Distribution Src Src Service model Hosts Host-to-router protocol (IGMP) Routers Multicast routing protocols (various) 5 6 Multicast Router Responsibilities IP Multicast Service Model (rfc1112) • Learn of the existence of multicast groups • Each group identified by a single IP address (through advertisement) • Groups may be of any size • Identify links with group members • Members of groups may be located anywhere in the Internet • Establish state to route packets • Members of groups can join and leave at will • Replicate packets on appropriate interfaces • Senders need not be members • Routing entry: • Group membership not known explicitly • Analogy: Src, incoming interface List of outgoing interfaces • Each multicast address is like a radio frequency, on which anyone can transmit, and to which anyone can tune-in. 7 8 2 IP Multicast Addresses Multicast Scope Control – Small TTLs • Class -

IEEE 1588 Frequency and Time & Phase Profiles at ITU-T
IEEE 1588 Frequency and Time & phase profiles at ITU-T Silvana Rodrigues, System Engineering, IDT , [email protected] WSTS - 2013, San Jose ©2009 Integrated Device Technology, Inc. Agenda ● IEEE-1588TM Profile ● ITU-T G.8265.1 – Frequency Profile ● ITU-T G.8275.1 – Time and Phase Profile ● ITU-T G.8275.2 – Time and Phase Profile with partial support from the network IEEE 1588TM is a trademark of its respective owner www.IDT.com PAGE 2 CONFIDENTIAL IEEE-1588 Profiles ● IEEE-1588 defines profile as “The set of allowed Precision Time Protocol (PTP) features applicable to a device” ● “The purpose of a PTP profile is to allow organizations to specify specific selections of attribute values and optional features of PTP that, when using the same transport protocol, inter-work and achieve a performance that meets the requirements of a particular application.” ● A PTP profile should define ● Best master clock algorithm options ● Configuration management options ● Path delay mechanisms (peer delay or delay request-response) ● The range and default values of all PTP configurable attributes and data set members ● The transport mechanisms required, permitted, or prohibited ● The node types required, permitted, or prohibited ● The options required, permitted, or prohibited * IEEE Std 1588-2008 IEEE Standard for a Precision Clock Synchronization Protocol, copyright 2008 IEEE. All right reserved. www.IDT.com PAGE 3 CONFIDENTIAL ITU-T FREQUENCY PROFILE www.IDT.com PAGE 4 CONFIDENTIAL ITU-T G.8265.1 Frequency Profile IEEE-1588 without support from -

Performance Analysis and Comparison of 6To4 Relay Implementations
(IJACSA) International Journal of Advanced Computer Science and Applications, Vol. 4, No. 9, 2013 Performance Analysis and Comparison of 6to4 Relay Implementations Gábor Lencse Sándor Répás Department of Telecommunications Department of Telecommunications Széchenyi István University Széchenyi István University Győr, Hungary Győr, Hungary Abstract—the depletion of the public IPv4 address pool may delegated the last five “/8” IPv4 address blocks to the five speed up the deployment of IPv6. The coexistence of the two Regional Internet Registries in 2011 [3]. Therefore an versions of IP requires some transition mechanisms. One of them important upcoming coexistence issue is the problem of an is 6to4 which provides a solution for the problem of an IPv6 IPv6 only client and an IPv4 only server, because internet capable device in an IPv4 only environment. From among the service providers (ISPs) can still supply the relatively small several 6to4 relay implementations, the following ones were number of new servers with IPv4 addresses from their own selected for testing: sit under Linux, stf under FreeBSD and stf pool but the huge number of new clients can get IPv6 addresses under NetBSD. Their stability and performance were investigat- only. DNS64 [4] and NAT64 [5] are the best available ed in a test network. The increasing measure of the load of the techniques that make it possible for an IPv6 only client to 6to4 relay implementations was set by incrementing the number communicate with an IPv4 only server. Another very important of the client computers that provided the traffic. The packet loss and the response time of the 6to4 relay as well as the CPU coexistence issue comes from the case when the ISP does not utilization and the memory consumption of the computer support IPv6 but the clients do and they would like to running the tested 6to4 relay implementations were measured. -

1722 Over IP
1722 over IP Kevin Gross 26 October 2010 [email protected] 1722 fields • 802.3 header • 802.1Q tag • Ethertype • Control/data • Subtype • Version • Type specific data • Stream ID • Media clock restart • Sequence number • 802.1AS timestamp • Timestamp uncertain • Gateway info • Length • Payload IP fields • IP header – Version – Header length – DSCP – Total length – ID – Flags – Fragment offset – TTL – Protocol – Header checksum – Source IP – Destination IP • UDP header – Source port number – Destination port number – Checksum – Length RTP fields • Version • Marker • Payload type • Sequence number • Timestamp • Synchronization source • Synchronization routes 1733 RTCP fields • Name • Grandmaster ID • Time base indicator • Stream ID • 802.1AS timestamp 1722 over IP • Ethernet header • 802.1Q tag • IP header – DSCP • UDP header – Length • Control/data • Subtype • Version • Type specific data • Stream ID • Media clock restart • Sequence number • 802.1AS timestamp • Timestamp uncertain • Gateway info • Length • Payload Overhead • 1722 – Ethernet – 38 (includes preamble, header, FCS and IFG) – 802.1Q tag – 4 – 1722 header – 24 – Total = 66 octets • 1733 – Ethernet – 38 – 802.1Q tag – 4 – IP header – 20 or 40 – UDP header – 8 – RTP header – 12 – Total = 82 or 102 octets • 1722 over IP – Ethernet – 38 – 802.1Q tag – 4 – IP header – 20 or 40 – UDP header – 8 – 1722 header – 24 – Total = 94 or 114 octets IP multicast • Internet Group Management Protocol (IGMP) – IPv4 group membership • Multicast Listener Discovery (MLD) – IPv6 group membership • Multicast Address Dynamic Client Allocation Protocol (MADCAP) – RFC 2730. Implemented in Microsoft DHCP servers. Not widely deployed. • Unicast-Prefix-based IPv6 Multicast Addresses – RFC 3306, 3307. Requires ZMAAP. • ZMAAP – Not in use. IETF draft ( draft-ietf-zeroconf-zmaap- 02.txt ) expired in 2003. -

Deploying Ipv6 in Fixed and Mobile Broadband Access Networks
Deploying IPv6 in Fixed and Mobile Broadband Access Networks Tomás Lynch – Ericsson Jordi Palet Mar8nez – Consulintel Ariel Weher – LACNOG Agenda (1/2) • IPv6 in Broadband Networks – Where are we? • IPv6 TransiHon Mechanisms for Broadband Networks • IPv6 Prefix Assignment • Deployment of IPv6 in Mobile Broadband Networks • Deployment of IPv6 in PPPoE & IPoE Networks • Deployment of IPv6 in Cable Networks Agenda (2/2) • Current IPv6 Deployments in Broadband Access Networks • Other Systems Involved in IPv6 Deployment • IPv6 TransiHon Planning • Useful Documents • Conclusions IPv6 in Broadband Networks Where Are We? IPv4 Yes, the IPv4 pool IPv4 with NAT But we can use IPv4 and NAT!!! Yeah, right … IPv6 Why IPv6? Move to IPv6 Now! New Business Operaonal OpportuniHes Needs Allows continuous growth Simplify service of Internet business providers operations Ready for Cloud and M2M IPv4 Address (moving towards 50 billion) Depletion Increasing government New business models regulations requiring IPv6 deployment IPv6 Readiness – No Excuses! › Laptops, pads, mobile phones, dongles, CPEs: Ready! – OS: 90% of all Operating systems are IPv6 capable – Browsers are ready! – Mobile devices: Android, IOS6, LTE devices are ready! – Mobile Apps: More than 85% with IPv6 support – CPEs: More than 45% support IPv6 IPv6 Traffic is Growing – No Excuses! In LACNIC23, May 2015 • Peru 13% • World 6% Source: Google IPv6 StasHcs - 8/16/2015 So ISP what are you doing? • You may have IPv6 in your backbone: – Dual stack backbone, 6PE, 6VPE – Easy stuff! • Loopbacks, IGP (yes, ISIS is great), we love to configure BGP! – If not, what are you waiHng for? • What about your customers? – Mobile broadband: customers change their phone more quickly than their clothes, easy stuff but those GGSN licenses are killing me. -

Ipv6 Addresses
56982_CH04II 12/12/97 3:34 PM Page 57 CHAPTER 44 IPv6 Addresses As we already saw in Chapter 1 (Section 1.2.1), the main innovation of IPv6 addresses lies in their size: 128 bits! With 128 bits, 2128 addresses are available, which is ap- proximately 1038 addresses or, more exactly, 340.282.366.920.938.463.463.374.607.431.768.211.456 addresses1. If we estimate that the earth’s surface is 511.263.971.197.990 square meters, the result is that 655.570.793.348.866.943.898.599 IPv6 addresses will be available for each square meter of earth’s surface—a number that would be sufficient considering future colo- nization of other celestial bodies! On this subject, we suggest that people seeking good hu- mor read RFC 1607, “A View From The 21st Century,” 2 which presents a “retrospective” analysis written between 2020 and 2023 on choices made by the IPv6 protocol de- signers. 56982_CH04II 12/12/97 3:34 PM Page 58 58 Chapter Four 4.1 The Addressing Space IPv6 designers decided to subdivide the IPv6 addressing space on the ba- sis of the value assumed by leading bits in the address; the variable-length field comprising these leading bits is called the Format Prefix (FP)3. The allocation scheme adopted is shown in Table 4-1. Table 4-1 Allocation Prefix (binary) Fraction of Address Space Allocation of the Reserved 0000 0000 1/256 IPv6 addressing space Unassigned 0000 0001 1/256 Reserved for NSAP 0000 001 1/128 addresses Reserved for IPX 0000 010 1/128 addresses Unassigned 0000 011 1/128 Unassigned 0000 1 1/32 Unassigned 0001 1/16 Aggregatable global 001 -

Information About Implementing Ipv6 Multicast Routing
Implementing IPv6 Multicast • Information About Implementing IPv6 Multicast Routing, on page 1 • Implementing IPv6 Multicast, on page 9 • Additional References, on page 31 • Feature Information, on page 32 Information About Implementing IPv6 Multicast Routing This chapter describes how to implement IPv6 multicast routing on the switch. Traditional IP communication allows a host to send packets to a single host (unicast transmission) or to all hosts (broadcast transmission). IPv6 multicast provides a third scheme, allowing a host to send a single data stream to a subset of all hosts (group transmission) simultaneously. IPv6 Multicast Overview An IPv6 multicast group is an arbitrary group of receivers that want to receive a particular data stream. This group has no physical or geographical boundaries--receivers can be located anywhere on the Internet or in any private network. Receivers that are interested in receiving data flowing to a particular group must join the group by signaling their local switch. This signaling is achieved with the MLD protocol. Switches use the MLD protocol to learn whether members of a group are present on their directly attached subnets. Hosts join multicast groups by sending MLD report messages. The network then delivers data to a potentially unlimited number of receivers, using only one copy of the multicast data on each subnet. IPv6 hosts that wish to receive the traffic are known as group members. Packets delivered to group members are identified by a single multicast group address. Multicast packets are delivered to a group using best-effort reliability, just like IPv6 unicast packets. The multicast environment consists of senders and receivers. -

Ipv6-Only Deployment in Broadband and Cellular Networks Ipv4 As-A-Service
IPv6-only Deployment in Broadband and Cellular Networks IPv4 as-a-Service LACNIC31 May, 2019 Punta Cana, DO @JordiPalet ([email protected]) - 1 Transition / Co-Existence Techniques • IPv6 has been designed for easing the transition and coexistence with IPv4 • Several strategies have been designed and implemented for coexisting with IPv4 hosts, grouped in three categories: – Dual stack: Simultaneous support for both IPv4 and IPv6 stacks – Tunnels: IPv6 packets encapsulated in IPv4 ones • This has been the commonest choice • Today expect IPv4 packets in IPv6 ones! – Translation: Communication of IPv4-only and IPv6- only. Initially discouraged and only “last resort” (imperfect). Today no other choice! • Expect to use them in combination! - 2 Dual-Stack Approach • When adding IPv6 to a system, do not delete IPv4 – This multi-protocol approach is familiar and well-understood (e.g., for AppleTalk, IPX, etc.) – In the majority of the cases, IPv6 is be bundled with all the OS release, not an extra-cost add-on • Applications (or libraries) choose IP version to use – when initiating, based on DNS response: • if (dest has AAAA record) use IPv6, else use IPv4 – when responding, based on version of initiating packet • This allows indefinite co-existence of IPv4 and IPv6, and gradual app-by-app upgrades to IPv6 usage • A6 record is experimental - 3 Dual-Stack Approach IPv6 IPv6 IPv4 IPv4 Application Application Application Application TCP/UDP TCP/UDP TCP/UDP IPv6 IPv6 IPv4 IPv4 IPv6-only stack Dual-stack (IPv4 & IPv6) IPv4-only stack IPv6 -

Traceroute Is One of the Key Tools Used for Network Troubleshooting and Scouting
1 Introduction Traceroute is one of the key tools used for network troubleshooting and scouting. It has been available since networking's early days. Because traceroute is based on TTL header modification, it crafts its own network packets. The goal of this assignment is to re-implement a traceroute with cutting edge techniques designed to improve its scouting capabilities and bypass SPI firewalls. In this assignment you will learn about packet injection and sniffing. The assignment also teaches about more subtle topics such as network latency, packet filtering, and Q.O.S. 1.1 Instructions This project has to be completed sequentially as each part depends on the previous ones. The required coding language is C. You should consider using libnet [1] and libpcap [2], however using raw sockets is permitted as well. Note that the exercises become progressively more difficult, with Exercise 5 likely to consume the greatest amount of effort. 1.2 Submission and Grading To compile your project, the script will use the command make, executed in the project directory. Then it will launch our tests, using an executable name "traceng" you have to make sure your make file results in this executable name, in the same project directory. Make sure that the command line options and the output format are correctly implemented as they will be used by our script during the grading process. Specific examples of how we are going to test your executable are provided later in this document, for each exercise. Your project directory should also contain a file called README which is text file describing the highlights of your solution to each exercise anything special that you did, information required in the specific exercise, what is the most interesting thing you learned in the exercise, and anything else we need to take into account. -

Introduction to IP Multicast Routing
Introduction to IP Multicast Routing by Chuck Semeria and Tom Maufer Abstract The first part of this paper describes the benefits of multicasting, the Multicast Backbone (MBONE), Class D addressing, and the operation of the Internet Group Management Protocol (IGMP). The second section explores a number of different algorithms that may potentially be employed by multicast routing protocols: - Flooding - Spanning Trees - Reverse Path Broadcasting (RPB) - Truncated Reverse Path Broadcasting (TRPB) - Reverse Path Multicasting (RPM) - Core-Based Trees The third part contains the main body of the paper. It describes how the previous algorithms are implemented in multicast routing protocols available today. - Distance Vector Multicast Routing Protocol (DVMRP) - Multicast OSPF (MOSPF) - Protocol-Independent Multicast (PIM) Introduction There are three fundamental types of IPv4 addresses: unicast, broadcast, and multicast. A unicast address is designed to transmit a packet to a single destination. A broadcast address is used to send a datagram to an entire subnetwork. A multicast address is designed to enable the delivery of datagrams to a set of hosts that have been configured as members of a multicast group in various scattered subnetworks. Multicasting is not connection oriented. A multicast datagram is delivered to destination group members with the same “best-effort” reliability as a standard unicast IP datagram. This means that a multicast datagram is not guaranteed to reach all members of the group, or arrive in the same order relative to the transmission of other packets. The only difference between a multicast IP packet and a unicast IP packet is the presence of a “group address” in the Destination Address field of the IP header. -

Guidelines for the Secure Deployment of Ipv6
Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks NIST Special Publication 800-119 Guidelines for the Secure Deployment of IPv6 Recommendations of the National Institute of Standards and Technology Sheila Frankel Richard Graveman John Pearce Mark Rooks C O M P U T E R S E C U R I T Y Computer Security Division Information Technology Laboratory National Institute of Standards and Technology Gaithersburg, MD 20899-8930 December 2010 U.S. Department of Commerce Gary Locke, Secretary National Institute of Standards and Technology Dr. Patrick D. Gallagher, Director GUIDELINES FOR THE SECURE DEPLOYMENT OF IPV6 Reports on Computer Systems Technology The Information Technology Laboratory (ITL) at the National Institute of Standards and Technology (NIST) promotes the U.S. economy and public welfare by providing technical leadership for the nation’s measurement and standards infrastructure. ITL develops tests, test methods, reference data, proof of concept implementations, and technical analysis to advance the development and productive use of information technology. ITL’s responsibilities include the development of technical, physical, administrative, and management standards and guidelines for the cost-effective security and privacy of sensitive unclassified information in Federal computer systems. This Special Publication 800-series reports on ITL’s research, guidance, and outreach efforts in computer security and its collaborative activities with industry, government, and academic organizations. National Institute of Standards and Technology Special Publication 800-119 Natl. Inst. Stand. Technol. Spec. Publ. 800-119, 188 pages (Dec. 2010) Certain commercial entities, equipment, or materials may be identified in this document in order to describe an experimental procedure or concept adequately. -
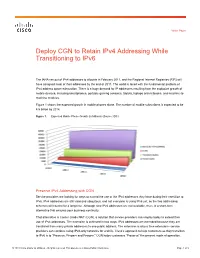
Deploy CGN to Retain Ipv4 Addressing While Transitioning to Ipv6
White Paper Deploy CGN to Retain IPv4 Addressing While Transitioning to IPv6 The IANA ran out of IPv4 addresses to allocate in February 2011, and the Regional Internet Registries (RIR) will have assigned most of their addresses by the end of 2011. The world is faced with the fundamental problem of IPv4 address space exhaustion. There is a huge demand for IP addresses resulting from the explosive growth of mobile devices, including smartphones, portable gaming consoles, tablets, laptops and netbooks, and machine-to- machine modules. Figure 1 shows the expected growth in mobile phones alone. The number of mobile subscribers is expected to be 4.5 billion by 2014. Figure 1. Expected Mobile Phone Growth (in Millions) (Source: IDC) Preserve IPv4 Addressing with CGN Service providers are looking for ways to extend the use of the IPv4 addresses they have during their transition to IPv6. IPv4 addresses are still valid and ubiquitous, and not everyone is using IPv6 yet, so the two addressing schemes will coexist for a long time. Although new IPv4 addresses are not available, there is a short-term alternative that ensures your business continuity. That alternative is Carrier Grade NAT (CGN), a solution that service providers can employ today to extend their use of IPv4 addresses. The extension is achieved in two ways: IPv4 addresses are extended because they are translated from many private addresses to one public address. The extension is also a time extension–-service providers can continue using IPv4-only networks for a while. Cisco’s approach to help customers as they transition to IPv6 is to “Preserve, Prepare and Prosper.” CGN helps customers “Preserve” the present mode of operation.