Microsoft Solutions for Security Group (MSS) Would Like to Acknowledge and Thank the Team That Produced the Windows XP Security Guide
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Internet Explorer 9 Features
m National Institute of Information Technologies NIIT White Paper On “What is New in Internet Explorer 9” Submitted by: Md. Yusuf Hasan Student ID: S093022200027 Year: 1st Quarter: 2nd Program: M.M.S Date - 08 June 2010 Dhaka - Bangladesh Internet Explorer History Abstract: In the early 90s—the dawn of history as far as the World Wide Web is concerned—relatively few users were communicating across this Internet Explorer 9 (abbreviated as IE9) is the upcoming global network. They used an assortment of shareware and other version of the Internet Explorer web browser from software for Microsoft Windows operating system. In 1995, Microsoft Microsoft. It is currently in development, but developer hosted an Internet Strategy Day and announced its commitment to adding Internet capabilities to all its products. In fulfillment of that previews have been released. announcement, Microsoft Internet Explorer arrived as both a graphical Web browser and the name for a set of technologies. IE9 will have complete or nearly complete support for all 1995: Internet Explorer 1.0: In July 1995, Microsoft released the CSS 3 selectors, border-radius CSS 3 property, faster Windows 95 operating system, which included built-in support for JavaScript and embedded ICC v2 or v4 color profiles dial-up networking and TCP/IP (Transmission Control support via Windows Color System. IE9 will feature Protocol/Internet Protocol), key technologies for connecting to the hardware accelerated graphics rendering using Direct2D, Internet. In response to the growing public interest in the Internet, Microsoft created an add-on to the operating system called Internet hardware accelerated text rendering using Direct Write, Explorer 1.0. -
CHAT Firmware Release Notes
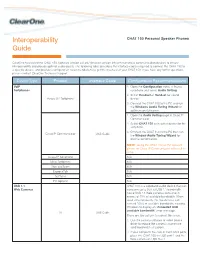
Interoperability CHAT 150 Personal Speaker Phones Guide ClearOne has tested the CHAT 150 (software version 2.0.28 / firmware version 39) with numerous communication devices to ensure interoperability and provide optimal audio quality. The following table describes the interface cables required to connect the CHAT 150 to a specific device, and provides configuration recommendations to get the most out of your CHAT 150. If you have any further questions, please contact ClearOne Technical Support. Device Type Product Interface Cable Configuration Recommendations VoIP 1. Open the Configuration menu in Avaya Softphones softphone and select Audio Setting. 2. Select Headset or Handset for sound Avaya SIP Softphone device. 3. Connect the CHAT 150 to the PC and run the Windows Audio Tuning Wizard for optimum performance. 1. Open the Audio Setting page in Cisco IP Communicator. 2. Select CHAT 150 as headset device for the softphone. 3. Connect the CHAT 150 to the PC then run Cisco IP Communicator USB Cable the Window Audio Tuning Wizard for optimal performance. NOTE: Using the CHAT 150 as the speaker phone for Cisco IP Communicator will result in echo. Avaya IP Softphone N/A Mirial Softphone N/A Xten eyeBeam N/A ExpressTalk N/A SJPhone N/A PC Gphone N/A USB 1.1 CHAT 150 is a wideband audio device that can Web Cameras consume up to 35% of USB 1.1 bandwidth. Some USB 1.1 Web cameras consume in excess of 75% of available bandwidth. When used simultaneously, the two devices can exceed 100% of available bandwidth, causing Windows to display an “Exceeded USB available bandwidth” error message. -

Quick Reference Using Microsoft Netmeeting on a SMART Board
Quick Reference ® ® Using Microsoft NetMeeting on a SMART Board™ Interactive Whiteboard This Quick Reference provides an overview of how to hold a NetMeeting data conference using a SMART Board interactive whiteboard. In a data conference, participants at multiple locations can view and collaborate on the same information at the same time. Preparing for Your Data Conference Before your conference begins, ensure that • all meeting participants are using NetMeeting 3.01 conferencing software and the same version of SMART Board software • all meeting participants are using the same screen resolution (e.g., 800 x 600) • you know the Internet protocol (IP) addresses of all computers that you will invite to join your NetMeeting session NOTE: To find the IP address for your computer, open NetMeeting and select Help, About Windows NetMeeting. Opening NetMeeting Software Open NetMeeting software from the Start menu or double-click its desktop icon. The NetMeeting window will appear. Type an IP address Press to place a call or computer name Press to end a call Press to add participants from your Address Book Press to • start or stop video • view picture-in-picture • adjust audio volume View the list of connected participants’ names Press to access • application sharing • chat • whiteboard • file transfer Placing and Accepting Calls Meeting Host To place a call, type the IP address of the computer you’d like to invite and press the Place Call button. Place Call button Remote Site The remote site must have NetMeeting software open to accept a call. Press the Accept button in the Incoming Call dialog to join the NetMeeting session. -

Software for Remote Medical Monitoring, Data Management and Teleconferencing
Software for Remote Medical Monitoring, Data Management and Teleconferencing Dr. Fatima Merchant & Dr. Deniz Gurkan, College of Technology Dr. Frank Chapman & Dr. Paul McKneely, MediCAN Systems, Inc. Description: The goal is to develop a software application to support an internet enabled mobile triage unit. The application will integrate, telecommunication and computing equipment, and medical electronics (such as digital stethoscope, blood pressure monitor, pulse-oximeter, temperature monitor, otoscope, dermascope, and electrocardiogram (ECG) machine). A high-speed network connection (wireless or land-line) will be used to provide full interactive live video and audio capacity for teleconferencing. An interface with an electronic medical records (EMR) system with allow storage and management of medical records. The software should be developed using the Java API. An open source electronic medical record (openEMR) system supporting a MySQL database will be utilized and interfaced with the software. The database will be housed on a server and programmed to enable high security and flexibility. High-speed internet (land-line or wireless) will be used to facilitate high quality videoconferencing between two sites. For video conferencing, the system will be integrated to Microsoft NetMeeting software or Apple iChat, depending on operating system. Software Development Tasks: Task 1: Develop the GUI for the nurse and the physician interface A simple yet powerful user interface is necessary to control the hardware and to configure it to perform the desired data acquisition operations in the desired sequence. It is also necessary for the reporting, and for enhanced visualization of movies and images. The software should be developed using Java, including the JFC/Swing Application Program Interface's (API) for dialogs, menus, and other basic user interface components. -

Polycom PVX Audio and Video Conferencing
® TM Polycom PVX Features and Benefits High Quality Audio and Video Premiere Video • Conforms to International Telecommunications Union (ITU) H.264 video coding standard • Strict adherence to ITU standard ensures industry- wide interoperability across Polycom and with other standard compliant manufacturers • Advanced, full-screen, full-motion video up to 30 fps • High resolution people video up to VGA (640x480) • Additional Annex support for better H.263+ video Superior Audio Performance for • Supports Polycom Siren™14 kHz audio Crisp, Natural Sounds and Voices • Receives 14kHz audio from group systems • Codes and transmits 14kHz - Requires 14kHz capable headset • G.722.1 – Wideband audio with low bandwidth consumption allows more bandwidth for higher video quality • Automatic Gain Control Extensive IP Quality of Service • Supports IP calls up to 2Mbps Support • OS determined IP Precedence and DiffServ settings for optimal video quality through network edge equipment • Video Error Concealment delivers smooth, clear video over IP networks by concealing the deteriorating effects of packet loss Integration with Microsoft® Live • Integrates directly with Microsoft® collaboration Communications Server (LCS) via infrastructure SIP • Registers and authenticates with Microsoft LCS 2005 • PVX users can be added to Microsoft Messenger's buddy list • Presence information sent to LCS indicating video buddies’ availability • Convenient dialing to email addresses Flexible Viewing Modes • Full screen mode – sit back and enjoy the video conferencing -

Assessing the Feasibility of Using Microsoft Netmeeting in Distance
Assessing the Feasibility of Using Microsoft® NetMeetingTM in Distance Education Oge Marques and Sam Hsu‡ Abstract ¾ One of the weaknesses of most Web-based distance education systems is the lack of adequate, synchronous, interac- II. DESCRIPTION OF THE PRODUCT tion between instructor and students. An easy and inexpensive solution to this problem can be obtained by using an off-the- Microsoft NetMeeting can be described as a collaboration shelf collaboration tool. In this paper we examine one of those tools, Microsoft tool that combines voice and data communications, video, NetMeeting. NetMeeting’s main technical features, pros and real-time application sharing, file transfer, a full-featured cons are presented and its suitability for educational applica- shared whiteboard, and text based chat [21]. tions is evaluated. Based on the collected facts, a recommenda- NetMeeting is targeted at home users, as well as small and tion for the decision-maker is presented at the end of the article. large organizations and claims to allow users to “take full advantage of the global reach of the Internet or corporate Index Terms ¾ Web-based education, distance learning, col- intranet for real-time communications and collaboration.” [1] laboration tools, conferencing. Connecting to other NetMeeting users is made easy with the Microsoft Internet Locator Server (ILS), enabling participants I. INTRODUCTION to call each other from a dynamic directory within Net- Meeting or from a Web page. Connections can also be estab- One of the most criticized aspects of distance education lished by calling the other party’s IP address. While con- (both conventional as well as Web-based) is the lack of syn- nected on the Internet or corporate intranet, participants can chronous, real-time, “live” interaction between instructor and communicate with audio and video, work together on virtu- students. -

An Intelligent Web Collaboration System for Virtual Engineering
VEI- AN INTELLIGENT WEB COLLABORATION SYSTEM FOR VIRTUAL ENGINEERING by Fuxin Sun M.E., Pattern Recognition and Intelligent System (1999) Tsinghua University Submitted to the Department of Civil and Environment Engineering in Partial fulfillment of the requirements for the Degree of Master of Science at the Massachusetts Institute of Technology June 2001 ©2001 Massachusetts Institute of Technology All rights reserved Signature of A uthor .................................... 1 Department of Civil and Environment Engineering May, 2001 Certified by ............... ................. 'evin Amaratunga Assistant Professor of Civil and E9,vironment Engineering Thesis Supervisor Accepted by.............. ........... Oral Buyukozturk Chairman, Departmental Committee on Graduate Studies MASSACHUSETTS INSTITUTE OF TECHNOLOGY BARKER JUN 0 4 2001 LIBRARIES VEI- AN INTELLIGENT WEB COLLABORATION SYSTEM FOR VIRTUAL ENGINEERING by Fuxin Sun Submitted to the Department of Civil and Environment Engineering On June, 2001 in Partial fulfillment of the requirements for the Degree of Master of Science ABSTRACT With the globalization of world economics, more and more globally located teams are involved in the procedure of engineering design. The teams have members working on the same project but living around the world in different time zones and thus having different working hours. The collaborations among the team members are intensive and important to the success of the project. Traditional collaboration methods, such as mail, telephone and so on, cannot fulfill the requirements of fast and efficient collaborations among the team. Virtual Engineering Initiative is an intelligent web collaboration system, which is designed to meet the collaboration needs of such teams. This thesis discusses the design and implementation of Virtual Engineering Initiative. Virtual Engineering Initiative has ten main components, which can be further classified into four functional groups: video conferencing, information publishing, instant messaging, and meeting scheduling. -

Form Number VL1133/12-01
® StingerPro II PCI Video Capture Card • Full-Motion Video Capture • 30fps @ 640x480 • Still Image Capture • 640x480 Pixels @ 16.8M Colors • Supports VFW, DirectShow™ and DirectDraw™ • TWAIN Drivers for use with Scanned Image-Eabled Applications • Videoconferencing Support • Plug and Play Compatibility Technical Features • Microsoft Media Player™ video plug-in for your browser. • RealNetworks RealProducer™ (12 for RealNetworks Video and Still Image Capture RealAudio™ and RealVideo™ content). • 640x480 pixels @ 30fps video capture. • Winnov® ActiveX Controls for embedding video into • 640x480 pixels @ 16.8M colors still image capture or scan. applications and Web pages. • Hardware video compression (up to 12:1) for saving to disk drive. • Video compression (up to 48:1) for saving to disk drive. • Scaleable video window size (80x60 to 630X480 pixels). Technical Specifications • Full-screen live video on DirectDraw Capable Graphics Cards. • TWAIN drivers for use with scanned image-enabled Video applications. Video Inputs NTSC and PAL Videoconferencing Video Formats RGB8 8-Bit RGB (256 colors) • Highest quality and performance video for RGBH 16-Bit RGB (32K colors) RGBT 24-Bit RGB (16.8M colors) videoconferencing. WINX Interframe Compression, 16:1 to 48:1 • Multiple (three) camera support for multiple (switch- WNV1 Hardware Compression, 1:1 to 12:1 able) images. WPY2 Software Compression, 8:1 to 14:1 • Works with any communication device: LAN, ISDN, YUY2 YUV 4:2:2 modem, DSL or cable modem. YV12 YUV 4:2:0 • Works with all videoconferencing protocols (H.320, YVU9 YUV 4:2:0 (Intel Indeo® RAW) H.323, and H.324). Resolution Width:80-640 Designed for Microsoft® Windows® Height: 60-480 • Windows 3.11, 9X, ME, NT4.0, 2000 and XP. -

View Publication
Distance Learning Through Distributed Collaborative Video Viewing JJ Cadiz, Anand Balachandran, Elizabeth Sanocki, Anoop Gupta, Jonathan Grudin, and Gavin Jancke May 10th, 2000 Technical Report MSR-TR-2000-42 Microsoft Research Microsoft Corporation One Microsoft Way Redmond, WA 98052 Distance Learning Through Distributed Collaborative Video Viewing JJ Cadiz, Anand Balachandran, Elizabeth Sanocki, Anoop Gupta, Jonathan Grudin, Gavin Jancke Microsoft Research, Collaboration & Multimedia Group One Microsoft Way, Redmond, WA 98052 USA +1 425 705 4824 {jjcadiz; anoop; jgrudin}@microsoft.com ABSTRACT Stanford has pursued this strategy successfully for over 25 Previous research on Tutored Video Instruction (TVI) years. However, for many working students, this shows that learning is enhanced when small groups of synchronous model of learning conflicts with their work students watch and discuss lecture videos together. Using commitments. The synchronous model is also not very specialized high-end videoconferencing systems, these scalable: even if the lecture could be broadcast to a million improved results have been shown to apply even when the people concurrently, there is little chance that interesting students are in different locations (Distributed TVI, or interaction would happen between students and instructors DTVI). In this paper, we explore two issues in making in such an environment. DTVI-like scenarios widely supported at low cost. First, The flexibility and scalability issues can be resolved by we explore design of a system that allows distributed using video streaming technologies and the Internet to individuals to collectively watch video using shared VCR create an on-demand, anytime, anywhere learning model. controls such as play, pause, seek, stop. We show how such However, research shows that learning can suffer when a system can be built on top of existing commercial students watch a lecture video individually. -

Intel® Proshare® Video System 500 Release Notes Copyright © 1999 Intel Corporation
Intel® ProShare® Video System 500 Release Notes Copyright © 1999 Intel Corporation. All rights reserved. These release notes contain the latest information available about your Intel ProShare Video System 500 and its operation. Contents Warranty Support New Camera Installation and setup – Windows* 95/98 and Windows NT* Before you install: verify supported operating systems Microsoft NetMeeting* 3.0 not supported LAN-only installation Installing Intel ProShare system from a network drive Avoid installing the ISDN/video-capture card in the last PCI slot Disabling the energy-saving "Suspend" option during setup Installing on multiple machines with the same email address Unfound files during installation Windows TEMP directory Installing on dual-boot systems Preventing the autolaunch feature Configuring dial-up networking Installing on systems with other Brooktree Bt848* devices Hardware conflict freezes system during installation Video adapter cards Installing the ProShare Video System 500 after uninstalling Intel® Video Phone or Intel® Create & Share™ software Windows NT Workstation specific install notes ProShare System not supported on NT server Log in as administrator to install under Windows NT workstation Application sharing requires Microsoft Service Pack 3 or higher Downloading Windows NT 4.0 Service Pack 3 Ordering Windows NT 4.0 Service Pack 3 Reinstalling Service Pack 3 when you add or remove software or hardware Configuring Remote Access Server ports during installation Running on multi-processor systems Connections Disabling -

Exploring Netmeeting Characteristics for Online Teaching and Learning Mathematics
2012 International Conference on Management and Education Innovation IPEDR vol.37 (2012) © (2012) IACSIT Press, Singapore Exploring NetMeeting Characteristics for Online Teaching and Learning Mathematics Ling Siew-Eng 1, Rasidah Mahdi 2, Lai Kim-Leong3, Chen Chee-Khium4 and Ling Siew-Ching5 1,2,4,5 Universiti Teknologi MARA 3 Institut Pendidikan Guru Kampus Batu Lintang Abstract. Teaching and learning process have shifted to online since the advancement of technology few decades ago. Educators need to understand the purpose and types of technology before they can effectively incorporate it into their teaching and learning. The paper explores the characteristics of NetMeeting freeware in teaching and learning mathematics online. Open ended questionnaire and in-depth interview protocol were utilized for gathering the information. The respondents were students who enrolled mathematics courses conducted using NetMeeting software online in two of the learning institutions in Malaysia. Data from the study and literature review were coded and a set of NetMeeting characteristics for online teaching and learning mathematics was elicited. Keywords: Netmeeting, Characteristics, Online Teaching and Learning 1. Introduction The advancement of technology has enhanced the teaching and learning process over the last 20 years. Since then, thousands of new educational software have been developed and used widely [1]. Among the technologies available for classrooms learning include simple tool-based learning, handheld computers and personal digital assistant -

CN5301.B.Net Conf PDF Guide 3/15/01 1:18 PM Page 1
CN5301.b.Net Conf PDF Guide 3/15/01 1:18 PM Page 1 Net Conferencing QUICK REFERENCE GUIDE CN5301.b.Net Conf PDF Guide 3/15/01 1:18 PM Page 2 WELCOME Welcome to the world of Net Conferencing from WorldComSM Conferencing. Net Conferencing lets you bring your meeting to the Internet so you can present to hundreds simultaneously or collaborate on meeting materials with others right from your computer – while discussing them via a conference call. This easy-to-use guide explains how you can: ◗ Share presentations with meeting participants by providing them with a pre-assigned URL ◗ Collaborate, edit, or revise documents or materials over the Internet in real time This multipoint Internet-based service offers: ◗ Use of your existing Internet access (LAN, dial-up, etc.) ◗ Two levels of password security ◗ The ability to have participants join the meeting with audio-only access, Internet-only access, or a combination of both ◗ The ability to record your Net conferences and provide a replay via the Internet With Net Conferencing, you can conduct electronic meetings with people across the street or around the world – enabling you to increase your company’s productivity, reduce travel costs, and make important decisions faster than ever before. Thank you for choosing WorldCom Conferencing. CN5301.b.Net Conf PDF Guide 3/15/01 1:18 PM Page 3 CONTENTS PLANNING YOUR MEETING . 2 SCHEDULING YOUR MEETING . 14 MEETING TIPS. 16 IMPORTANT NUMBERS Depending upon your needs, you can contact us at the following numbers: ◗ Reservations: U.S. 1-800-475-5000 Europe +44 (0)20 7950 9700 Hong Kong +852 2802 5100 Japan 81-3-5539-5100 Australia 1800 505 500 – Log on to http://e-meetings.wcom.com and use the Online Reservation System ◗ Customer Relations: 1-800-475-0600 ◗ For additional information on other conferencing services: 1-800-480-3600 ◗ For future reference, please record your authorization code here: ______________________________________ CN5301.b.Net Conf PDF Guide 3/15/01 1:18 PM Page 4 PLANNING YOUR MEETING Planning your Net conference is easy.