Source Code Review
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Microsoft Patches Were Evaluated up to and Including CVE-2020-1587
Honeywell Commercial Security 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2020-1587. Patches not listed below are not applicable to a Pro-Watch system. 2020 – Microsoft® Patches Tested with Pro-Watch CVE-2020-1587 Windows Ancillary Function Driver for WinSock Elevation of Privilege Vulnerability CVE-2020-1584 Windows dnsrslvr.dll Elevation of Privilege Vulnerability CVE-2020-1579 Windows Function Discovery SSDP Provider Elevation of Privilege Vulnerability CVE-2020-1578 Windows Kernel Information Disclosure Vulnerability CVE-2020-1577 DirectWrite Information Disclosure Vulnerability CVE-2020-1570 Scripting Engine Memory Corruption Vulnerability CVE-2020-1569 Microsoft Edge Memory Corruption Vulnerability CVE-2020-1568 Microsoft Edge PDF Remote Code Execution Vulnerability CVE-2020-1567 MSHTML Engine Remote Code Execution Vulnerability CVE-2020-1566 Windows Kernel Elevation of Privilege Vulnerability CVE-2020-1565 Windows Elevation of Privilege Vulnerability CVE-2020-1564 Jet Database Engine Remote Code Execution Vulnerability CVE-2020-1562 Microsoft Graphics Components Remote Code Execution Vulnerability -

Mcafee Foundstone Fsl Update
2017-SEP-12 FSL version 7.5.958 MCAFEE FOUNDSTONE FSL UPDATE To better protect your environment McAfee has created this FSL check update for the Foundstone Product Suite. The following is a detailed summary of the new and updated checks included with this release. NEW CHECKS 22374 - (MSPT-Sept2017) Microsoft Windows NetBIOS Remote Code Execution (CVE-2017-0161) Category: Windows Host Assessment -> Patches and Hotfixes (CATEGORY REQUIRES CREDENTIALS) Risk Level: High CVE: CVE-2017-0161 Description A vulnerability in some versions of Microsoft Windows could lead to remote code execution. Observation A vulnerability in some versions of Microsoft Windows could lead to remote code execution. The flaw lies in NetBIOS. Successful exploitation by a remote attacker could result in the execution of arbitrary code. 22388 - (MSPT-Sept2017) Microsoft Internet Explorer Memory Corruption Remote Code Execution (CVE-2017-8749) Category: Windows Host Assessment -> Patches and Hotfixes (CATEGORY REQUIRES CREDENTIALS) Risk Level: High CVE: CVE-2017-8749 Description A vulnerability in some versions of Microsoft Internet Explorer could lead to remote code execution. Observation A vulnerability in some versions of Microsoft Internet Explorer could lead to remote code execution. The flaw is due to a memory corruption error. Successful exploitation by a remote attacker could result in the execution of arbitrary code. The exploit requires the user to open a vulnerable website, email or document. 22404 - (MSPT-Sep2017) Microsoft Win32k Graphics Remote Code Execution Vulnerability (CVE-2017-8682) Category: Windows Host Assessment -> Patches and Hotfixes (CATEGORY REQUIRES CREDENTIALS) Risk Level: High CVE: CVE-2017-8682 Description A vulnerability in some versions of Microsoft Windows could lead to remote code execution. -
![[ EVEREST Ultimate Edition ]](https://docslib.b-cdn.net/cover/3493/everest-ultimate-edition-1573493.webp)
[ EVEREST Ultimate Edition ]
[ EVEREST Ultimate Edition ] ---------------------------------------- Versi EVEREST v4.50.1330/id Modul Pengukuran 2.3.224.0 Home page http://www.lavalys.com/ Tipe Laporan Bimbingan laporan Komputer TANSISCOTBK09K Generator Nain Sistem Operasi Microsoft Windows XP Profe ssional 5.1.2600 (WinXP Retail) Tanggal 20110510 Jam 06:23 [ Ringkasan ] ---------------------------------------- Komputer: Tipe Komputer ACPI Multiprocessor PC Sistem Operasi Microsoft Windows XP Pro fessional Paket Layanan OS Service Pack 3 Internet Explorer 6.0.2900.5512 DirectX 4.09.00.0904 (DirectX 9. 0c) Nama Komputer TANSISCOTBK09K Nama Pengguna Nain Domain Masuk TANSISCOTBK09K Tanggal / Jam 20110510 / 06:23 Motherboard: Tipe CPU Intel Pentium 4, 3000 MH z (15 x 200) Nama Motherboard Dell OptiPlex GX270 Chipset Motherboard Intel SpringdaleG i865G Memori Sistem 512 MB (DDR SDRAM) DIMM2: Infineon HYS64D32000GU7 256 MB PC2100 DDR SDRAM (2.5337 @ 142 MHz) (2.0336 @ 133 MHz) DIMM3: Hynix HYMD216 646D6JD43 128 MB PC3200 DDR SDRAM (3.0338 @ 200 MHz) (2.5337 @ 166 MHz) (2.0226 @ 133 MHz) DIMM4: Hynix HYMD216 646D6JD43 128 MB PC3200 DDR SDRAM (3.0338 @ 200 MHz) (2.5337 @ 166 MHz) (2.0226 @ 133 MHz) Tipe BIOS Phoenix (05/17/04) Port Komunikasi Communications Port (COM 1) Port Komunikasi ECP Printer Port (LPT1) Layar: Adapter Video RADEON 9600 Series Secon dary (256 MB) Adapter Video RADEON 9600 Series (256 MB) Akselerator 3D ATI Radeon 9600 (RV350) Monitor NEC V520 [15" CRT] (2Y 00657TB) Multimedia: Adapter Suara Analog Devices AD1981B(L ) @ Intel 82801EB ICH5 AC'97 Audio Controller [A2/A3] Adapter Suara BrookTree Bt878 Video Ca pture Device Audio Section Penyimpanan: Kontroler IDE Intel(R) 82801EB Ultra A TA Storage Controllers Kontroler IDE Intel(R) 82801EB Ultra A TA Storage Controllers Kontroler Penyimpanan A2222176 IDE Controller Drive Disk JetFlash Transcend 8GB U SB Device (7 GB, USB) Drive Disk Kingston DataTraveler 2. -

Towards a Computerization of the Lao Tham System of Writing
First International Conference on Lao Studies - Dekalb, 20-22 May 2005 Towards a Computerization of the Lao Tham System of Writing Grégory KOURILSKY Vincent BERMENT [email protected] [email protected] (1) (1) (2) (1) INALCO (2) GETA-CLIPS (IMAG) 2, rue de Lille BP 53 75343 Paris Cedex 7, France 38041 Grenoble Cedex 9, France http://www.inalco.fr http://www-clips.imag.fr/geta/ ABSTRACT – Although the subject of under-resourced languages is a problem often taken into consideration, one omits to make the distinction with under-resourced scripts . The Tham script of Laos, used to write Buddhist Texts, is one of the two official writing systems used in Lao P.D.R. (Laos). But if the other one – the so-called —laic“ Lao script – is now quite well computerized (numerous fonts, input software, word processors, Unicode area), the Tham script seems to have always been forsaken by modern technologies (typewriters and computers). And this phenomenon does not seem to be being reversed soon since the Unicode Standard does not integrate it in any zone. Understanding the sociological and technical reasons of this neglect, we present an approach to mend it. RÉSUMÉ – Bien que le sujet des langues peu dotées informatiquement soit un problème régulièrement abordé, on omet souvent de distinguer le cas des écritures peu dotées. L'écriture tham du Laos, employée pour noter les textes bouddhiques, est l'une des deux écritures offielles de la République Démocratique Populaire Lao (Laos). Si l'écriture lao proprement dite (appelée parfois par opposition écriture lao —laïque“ ) est aujourd‘hui relativement bien dotée informatiquement (nombreuses polices de caractères, logiciels de traitement de texte, zone Unicode), l‘écriture tham semble avoir toujours été délaissée des techniques modernes de saisie (mécanique aussi bien qu‘informatique). -

The Old New Thing: Practical Development Throughout The
Praise for The Old New Thing “Raymond Chen is the original raconteur of Windows.” —Scott Hanselman, ComputerZen.com “Raymond has been at Microsoft for many years and has seen many nuances of Windows that others could only ever hope to get a glimpse of. With this book, Raymond shares his knowledge, experience, and anecdotal stories, allowing all of us to get a better understanding of the operating system that affects millions of people every day. This book has something for everyone, is a casual read, and I highly recommend it!” —Jeffrey Richter, Author/Consultant, Cofounder of Wintellect “Very interesting read. Raymond tells the inside story of why Windows is the way it is.” —Eric Gunnerson, Program Manager, Microsoft Corporation “Absolutely essential reading for understanding the history of Windows, its intricacies and quirks, and why they came about.” —Matt Pietrek, MSDN Magazine’s Under the Hood Columnist “Raymond Chen has become something of a legend in the software industry, and in this book you’ll discover why. From his high-level reminiscences on the design of the Windows Start button to his low-level discussions of GlobalAlloc that only your inner-geek could love, The Old New Thing is a captivating collection of anecdotes that will help you to truly appreciate the difficulty inherent in designing and writing quality software.” —Stephen Toub, Technical Editor, MSDN Magazine This page intentionally left blank THE OLD NEW THING This page intentionally left blank THE OLD NEW THING Practical Development ThroughoutT the Evolution of Windows Raymond Chen Upper Saddle River, NJ • Boston • Indianapolis • San Francisco New York • Toronto • Montreal • London • Munich • Paris • Madrid Capetown • Sydney • Tokyo • Singapore • Mexico City Many of the designations used by manufacturers and sellers to distinguish their products are claimed as trademarks. -

Abstract Functions, 281 Accelerators, 215–216 Accessibility, 57, 472–480
Chen_Rev_Index 12/6/06 11:09 AM Page 497 Index Abstract functions, 281 Application Compatibility Toolkit, 287–288 Accelerators, 215–216 Application Data vs. My Documents, 450–451 Accessibility, 57, 472–480 Application Verifier, 288 Active Accessibility feature, 480 Arithmetic library for Calc, 337 AddRef method, 274 Arrows,up-down controls,354–355 Address spaces, large, 451–455 Auto-reset events, 112–114 Adjustor thunks, 274–275 Advanced Options dialog, 2–3, 57 Background operations in power management, All Programs list, 403–404 455–457 Alt key for blinking caret, 343–344 Backward compatibility, 283 Alt+Esc hotkey, 58 16-bit DOS and Windows, 288–290 Alt+Tab order, 58–59 BIOS clock, 301–302 Always on top, 58, 436 bugs in, 293–294 Analog clocks, 51 Deer Hunter, 293 Animal-named functions, 22–23 DirectX video driver, 298–299 Animations, stealing, 305 Display Control Panel, 308–309 ANSI code page, 379–390 drive letters, 292–293 converting with Unicode, 391–392 error code, 297–298 UTF-8 as, 431–432 GetWindowText, 45–46 ANSI strings, 164 hardware, 141–142 Anti-aliased fonts, 459–462 intentional crashes, 283 Anti-piracy holograms, 25–26 listview controls, 300–301 Anti-symmetry rule, 243 operating system patches, 299–300 AOL CDs, 487 Printers Control Panel, 306–307 497 Chen_Rev_Index 12/6/06 11:09 AM Page 498 498 index Backward compatibility (Continued) BS_* button styles, 232, 234 QueryInterface, 303–305 “Bug Bunny,” 494 reserved filenames, 290–292 Bug reports, whimsical, 482–483 Shell Folders key, 294–296 Bugs undocumented behavior, 286–288 -

Preparing a Computer Running Windows XP for Dzongkha
Preparing a Computer running Windows XP for Dzongkha Microsoft Windows XP does not normally support the complex text features necessary to correctly display Dzongkha script in Unicode. These features are available on Windows XP only in Microsoft Office 2003 (SP1 or above), Office 2007 or with Microsoft’s free WordViewer. It is possible to display Dzongkha script properly in other applications (e.g. web browsers, Notepad, OpenOffice and e-mail clients) only by installing a Dzongkha font, enabling complex scripts and copying the necessary support files from the Office 2003 or WordViewer program folder to your Windows system. To edit Dzongkha text in any application you will also need to install a Dzongkha keyboard. Installation procedure for Windows XP Dzongkha Unicode will work correctly in Windows XP only if certain conditions are met: First you need to have at least one Unicode compatible Dzongkha font installed. Second you need to enable Complex Script support in Windows. Third, you need to upgrade Uniscribe (USP10.DLL), he Windows complex-script shaping engine, to a version which has support for the Dzongkha script. Fourth, you should install a Dzongkha keyboard or input method to enable you to type & edit Unicode Dzongkha. Fifth you may need to configure individual applications on your computer to use Dzongkha and other complex script languages. 1. Installing Dzongkha Fonts There are currently three Dzongkha fonts available which work well with Windows and most applications that support Unicode. These are: DDC Uchen –— a tsuyig font developed by the DDC; DDC Wangdi –— a joyig font developed by the DDC; and Jomolhari — a tsuyig font, created independently by Chris Fynn based on Bhutanese examples. -

Large-Scale Thai Statistical Machine Translation
Large-Scale Thai Statistical Machine Translation Glenn Slayden, Mei-Yuh Hwang, Lee Schwartz MSR-TR-2010-41 (2008). This approach first parses the source language Abstract into a dependency tree which includes part-of-speech labels. A by-product of parsing is word breaking. For Thai language text presents unique challenges for example, John’s is parsed into John (noun) and ’s integration into large-scale multi-language statistic- (possessive). al machine translation (SMT) systems, largely During training we also break Thai sentences into stemming from the nominal lack of punctuation and tokens (Sections 2 and 3). Source and target sentences inter-word space. We review our independent solu- are lower-cased1, to be able to share the training data tions for Thai character sequence normalization, to- between different casings. Next we apply word- kenization, typed-entity identification, sentence- dependent Hidden Markov Model (WDHMM) align- breaking, and text re-spacing. We describe a gener- al maximum entropy-based classifier for sentence ment (He 2007) to learn the mapping between the breaking, whose algorithm can be easily extended source and target token streams. Given a parallel cor- to other languages such as Arabic. After integration pus with these word alignments and dependency of all components, we obtain a final translation parses, we extract both treelet translation pairs and BLEU score of 0.19 for English to Thai and 0.21 order templates. From each aligned sub-graph of the for Thai to English. source tree, we extract that sub-graph along with its translation, and collate these across the whole dataset 1 MT System Description to produce a set of treelets with their translations. -

Microsoft Patches Were Evaluated up to and Including CVE-2019-1303
Honeywell Security Group 2700 Blankenbaker Pkwy, Suite 150 Louisville, KY 40299 Phone: 1-502-297-5700 Phone: 1-800-323-4576 Fax: 1-502-666-7021 https://www.security.honeywell.com The purpose of this document is to identify the patches that have been delivered by Microsoft® which have been tested against Pro-Watch. All the below listed patches have been tested against the current shipping version of Pro-Watch with no adverse effects being observed. Microsoft Patches were evaluated up to and including CVE-2019-1303. Patches not listed below are not applicable to a Pro-Watch system. 2019 – Microsoft® Patches Tested with Pro-Watch .NET Quality Rollup for .NET Framework CVE-2019-1371 Internet Explorer Memory Corruption Vulnerability CVE-2019-1368 Windows Secure Boot Security Feature Bypass Vulnerability CVE-2019-1367 Scripting Engine Memory Corruption Vulnerability CVE-2019-1366 Chakra Scripting Engine Memory Corruption Vulnerability CVE-2019-1365 Microsoft IIS Server Elevation of Privilege Vulnerability CVE-2019-1359 Jet Database Engine Remote Code Execution Vulnerability CVE-2019-1358 Jet Database Engine Remote Code Execution Vulnerability CVE-2019-1357 Browser Spoofing Vulnerability Microsoft Edge based on Edge HTML Information Disclosure CVE-2019-1356 Vulnerability CVE-2019-1347 Windows Denial of Service Vulnerability CVE-2019-1346 Windows Denial of Service Vulnerability CVE-2019-1345 Windows Kernel Information Disclosure Vulnerability CVE-2019-1344 Windows Code Integrity Module Information Disclosure Vulnerability CVE-2019-1343 Windows -

Vigilant Ops Insight Is a Cloud-Based Platform for Creating, and Automatically Maintaining, Medical Device Cybersecurity Bill of Materials
Cybersecurity Command Center Booth 400 – 114 Vigilant Ops Insight is a cloud-based platform for creating, and automatically maintaining, medical device Cybersecurity Bill of Materials File Help Jane Doe Jane Doe Status: Basic UPGRADE Status: Premium UPGRADE DASHBOARD > CARDIOSTART XL > MICROSOFT SILVERLIGHT Welcome to the CVE-2017-0283 Cybersecurity Bill of Materials Generator Review Cybersecurity Bill of Materials Doesn’t look right? Click here to upload a different CBOM. Current Description CVSS Severity Now generating a CBOM for any device is as easy, as well… 1, 2, 3! Uniscribe in Windows Server 2008 SP2 and R2 SP1, Windows 7 SP1, Windows 8.1, v3.0: 8.8 High Windows Server 2012 Gold and R2, Windows RT 8.1, Windows 10 Gold, 1511, v2.0: 9.3 High 1607, Windows Server 2016, Microsoft Office 2007 SP3, Microsoft Office 2010 SP2, Microsoft Office Word Viewer, Microsoft Lync 2013 SP1, Skype for Business 2016, Device Name Model Version Operating System Microsoft Silverlight 5 Developer Runtime when installed on Microsoft Windows, Capture RTC CAP-RTC 3.0.1 Windows 8 and Microsoft Silverlight 5 when installed on Microsoft Windows allows a remote Device Description code execution vulnerability due to the way it handles objects in memory, aka Device allows doctors to see inside the body. It uses a combination of X-rays and a computer to create pictures of your "Windows Uniscribe Remote Code Execution Vulnerability". organs, bones, and other tissues. This CVE ID is unique from CVE-2017-8528. Impact Software Name Version Component CPE Adobe Silverlight -
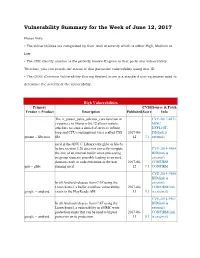
Vulnerability Summary for the Week of June 12, 2017
Vulnerability Summary for the Week of June 12, 2017 Please Note: • The vulnerabilities are categorized by their level of severity which is either High, Medium or Low. • The CVE identity number is the publicly known ID given to that particular vulnerability. Therefore, you can search the status of that particular vulnerability using that ID. • The CVSS (Common Vulnerability Scoring System) score is a standard scoring system used to determine the severity of the vulnerability. High Vulnerabilities Primary CVSS Source & Patch Vendor -- Product Description Published Score Info The cr_parser_parse_selector_core function in CVE-2017-8871 cr-parser.c in libcroco 0.6.12 allows remote MISC attackers to cause a denial of service (infinite EXPLOIT- loop and CPU consumption) via a crafted CSS 2017-06- DB(link is gnome -- libcroco file. 12 7.1 external) nscd in the GNU C Library (aka glibc or libc6) before version 2.20 does not correctly compute CVE-2014-9984 the size of an internal buffer when processing BID(link is netgroup requests, possibly leading to an nscd external) daemon crash or code execution as the user 2017-06- CONFIRM gnu -- glibc running nscd. 12 7.5 CONFIRM CVE-2014-9960 BID(link is In all Android releases from CAF using the external) Linux kernel, a buffer overflow vulnerability 2017-06- CONFIRM(link google -- android exists in the PlayReady API. 13 9.3 is external) CVE-2014-9961 In all Android releases from CAF using the BID(link is Linux kernel, a vulnerability in eMMC write external) protection exists that can be used to bypass 2017-06- CONFIRM(link google -- android power-on write protection. -

Mapxtreme 2008 V6.8.0 Release Notes
MapXtreme 2008 v6.8.0 Release Notes These Release Notes provide information on enhancements and updates made to Americas: MapXtreme 2008 v6.8.0. It also covers bug fixes, known issues, and other Phone: 518 285 6000 important information for this release. Fax: 518 285 6070 Sales: 800 327 8627 Government Sales: 800 619 2333 This document is a supplement to the MapXtreme 2008 Developer Guide. Refer Technical Support: 518 285 7283 www.mapinfo.com to this document for release specific information and to the Developer Guide for overall product information and usage. The Developer Guide is available in three © 2008 Pitney Bowes Sofware Inc. formats and from several locations, including: All rights reserved. MapInfo and the MapInfo logo are trademarks of Pitney • HTML version integrated into Visual Studio (in the Help Contents pane) Bowes Sofware Inc. and/or its affiliates. • PDF version accessible from the Start > All Programs menu under MapInfo > MapXtreme 2008 v6.8.0.0 > Learning Resources browser June 2008 • PDF version on the MapInfo website List of Topics: What’s New . 2 What’s Changed . 10 Upgrading to MapXtreme 2008 . .11 Bug Fixes . 14 Known Issues . 17 Documentation Topics . 28 What’s New What’s New MapXtreme 2008 offers the following new features in version v6.8.0: • Supported Environments • New Assemblies • Visual Studio Support • WFS Server Compliancy • Raster Reprojection • Time and DateTime Data Types • Enhanced User-Defined Metadata Support • LanguagePreference Key/Value Pair • Border Control Properties for Printing and Exporting • Contact Information Support on WMS Server • Bi-Directional String Support in Curved Labels Supported Environments This release of MapXtreme 2008 supports the following frameworks, development environments and operating systems.