Discrete Dynamics in Supply Chain Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

MAA AMC 8 Summary of Results and Awards
The Mathematical Association of America AMERICAN MatHEmatICS COMPETITIONS 2008 24th Annual MAA AMC 8 Summary of Results and Awards Learning Mathematics Through Selective Problem Solving Examinations prepared by a subcommittee of the American Mathematics Competitions and administered by the office of the Director The American Mathematics Competitions are sponsored by The Mathematical Association of America and The Akamai Foundation Contributors: Academy of Applied Sciences American Mathematical Association of Two-Year Colleges American Mathematical Society American Society of Pension Actuaries American Statistical Association Art of Problem Solving Awesome Math Canada/USA Mathcamp Casualty Actuarial Society Clay Mathematics Institute IDEA Math Institute for Operations Research and the Management Sciences L. G. Balfour Company Math Zoom Academy Mu Alpha Theta National Assessment & Testing National Council of Teachers of Mathematics Pi Mu Epsilon Society of Actuaries U.S.A. Math Talent Search W. H. Freeman and Company Wolfram Research Inc. TABLE OF CONTENTS 2008 IMO Team with their medals ................................................................... 2 Report of the Director ..........................................................................................3 I. Introduction .................................................................................................... 3 II. General Results ............................................................................................. 3 III. Statistical Analysis of Results -
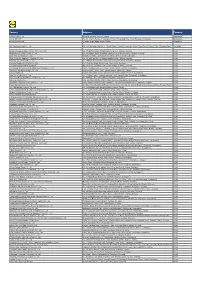
Factory Address Country
Factory Address Country Durable Plastic Ltd. Mulgaon, Kaligonj, Gazipur, Dhaka Bangladesh Lhotse (BD) Ltd. Plot No. 60&61, Sector -3, Karnaphuli Export Processing Zone, North Potenga, Chittagong Bangladesh Bengal Plastics Ltd. Yearpur, Zirabo Bazar, Savar, Dhaka Bangladesh ASF Sporting Goods Co., Ltd. Km 38.5, National Road No. 3, Thlork Village, Chonrok Commune, Korng Pisey District, Konrrg Pisey, Kampong Speu Cambodia Ningbo Zhongyuan Alljoy Fishing Tackle Co., Ltd. No. 416 Binhai Road, Hangzhou Bay New Zone, Ningbo, Zhejiang China Ningbo Energy Power Tools Co., Ltd. No. 50 Dongbei Road, Dongqiao Industrial Zone, Haishu District, Ningbo, Zhejiang China Junhe Pumps Holding Co., Ltd. Wanzhong Villiage, Jishigang Town, Haishu District, Ningbo, Zhejiang China Skybest Electric Appliance (Suzhou) Co., Ltd. No. 18 Hua Hong Street, Suzhou Industrial Park, Suzhou, Jiangsu China Zhejiang Safun Industrial Co., Ltd. No. 7 Mingyuannan Road, Economic Development Zone, Yongkang, Zhejiang China Zhejiang Dingxin Arts&Crafts Co., Ltd. No. 21 Linxian Road, Baishuiyang Town, Linhai, Zhejiang China Zhejiang Natural Outdoor Goods Inc. Xiacao Village, Pingqiao Town, Tiantai County, Taizhou, Zhejiang China Guangdong Xinbao Electrical Appliances Holdings Co., Ltd. South Zhenghe Road, Leliu Town, Shunde District, Foshan, Guangdong China Yangzhou Juli Sports Articles Co., Ltd. Fudong Village, Xiaoji Town, Jiangdu District, Yangzhou, Jiangsu China Eyarn Lighting Ltd. Yaying Gang, Shixi Village, Shishan Town, Nanhai District, Foshan, Guangdong China Lipan Gift & Lighting Co., Ltd. No. 2 Guliao Road 3, Science Industrial Zone, Tangxia Town, Dongguan, Guangdong China Zhan Jiang Kang Nian Rubber Product Co., Ltd. No. 85 Middle Shen Chuan Road, Zhanjiang, Guangdong China Ansen Electronics Co. Ning Tau Administrative District, Qiao Tau Zhen, Dongguan, Guangdong China Changshu Tongrun Auto Accessory Co., Ltd. -

Chinese New Acquisitions List (2013-2014) 澳大利亞國家圖書館中文新書簡報 (2013 年 12 月-2014 年 1 月)
Chinese New Acquisitions List (2013-2014) 澳大利亞國家圖書館中文新書簡報 (2013 年 12 月-2014 年 1 月) MONOGRAPHS (圖書), SERIALS (期刊), e-RESOURCES (電子刊物), MAPS (地圖) e-RESOURCES (電子刊物)Links to full-text e-books online: http://nla.lib.apabi.com/List.asp?lang=gb 書 名 Titles 索 書 號 Call numbers FULL CATALOGUE DESCRIPTION Liu ji wen xian ji lu pian : Xi Zhongxun / Zhong gong zhong yang dang shi yan jiu shi, CH mt 186 http://nla.gov.au/nla.cat-vn6415356 Guo jia xin wen chu ban guang dian zong ju, Zhong yang dian shi tai lian he she zhi ; Zhong yang dian shi tai ji lu pin dao cheng zhi. 六集文献纪录片 : 习仲勋 / 中共中央党史研究室, 国家新闻出版广电总局, 中央电视台联合 摄制 ; 中央电视台纪录频道承制. Hu Xiang jiu bao / Hu Xiang wen ku bian ji chu ban wei yuan hui. CH mt 187 http://nla.gov.au/nla.cat-vn6342566 湖湘旧报 / 湖湘文库编辑出版委员会. AUSTRALIANA in Chinese Language 澳大利亞館藏 – Books & Serials about Australia or by Australians 書 名 Titles 索 書 號 Call numbers FULL CATALOGUE DESCRIPTION Li shi da huang yan : wo men bu ke bu zhi dao de li shi zhen xiang = The greatest lies in CHN 001.95 C219 http://nla.gov.au/nla.cat-vn6289422 history / Alexander Canduci (Ao) Yalishanda Kanduxi zhu ; Wang Hongyan, Zhang Jing yi. 1 历史大谎言 : 我们不可不知道的历史真相 = The greatest lies in history / Alexander Canduci [澳] 亚历山大·坎杜希 著 ; 王鸿雁, 张敬 译. Ying yu guo jia gai kuang = An introduction to the English-speaking countries. Xia, Jia CHN 306.0917521 Y51 http://nla.gov.au/nla.cat-vn6382010 Nada, Aodaliya, Xinxilan, Yindu gai kuang / zhu bian Sui Mingcai ; fu zhu bian Zou Ying .. -

Full Tone to Sound Feminine: Analyzing the Role of Tonal Variants in Identity Construction
View metadata, citation and similar papers at core.ac.uk brought to you by CORE provided by Kosmopolis University of Pennsylvania Working Papers in Linguistics Volume 25 Issue 2 Selected Papers from NWAV47 Article 6 1-15-2020 Full Tone to Sound Feminine: Analyzing the Role of Tonal Variants in Identity Construction Feier Gao Indiana University, Bloomington Follow this and additional works at: https://repository.upenn.edu/pwpl Recommended Citation Gao, Feier (2020) "Full Tone to Sound Feminine: Analyzing the Role of Tonal Variants in Identity Construction," University of Pennsylvania Working Papers in Linguistics: Vol. 25 : Iss. 2 , Article 6. Available at: https://repository.upenn.edu/pwpl/vol25/iss2/6 This paper is posted at ScholarlyCommons. https://repository.upenn.edu/pwpl/vol25/iss2/6 For more information, please contact [email protected]. Full Tone to Sound Feminine: Analyzing the Role of Tonal Variants in Identity Construction Abstract Tone neutralization in Standard Mandarin requires syllables in a weakly-stressed position to be destressed and toneless (Chao, 1968), yet such a process is often incomplete in some Mandarin dialects, e.g., Taiwanese-accented Mandarin (Huang, 2012, 2018). For instance, the metrically weak syllable bai in míng2bai0 (‘to understand, clear’) is usually destressed in Standard Mandarin but fully realized as a rising tone (míng2bái2) in non-standard varieties. Recent studies have observed that Standard Mandarin speakers, especially young females, tend to performatively adopt this supraregional linguistic feature to index their “cosmopolitan” and “youthful” social personae (Zhang 2005, 2018). The current study provides a spoken-corpus analysis to address how the “cute” social persona is indexed in such prosodic variables. -

Levi Strauss & Co. Factory List
Levi Strauss & Co. Factory List Published : November 2019 Total Number of LS&Co. Parent Company Name Employees Country Factory name Alternative Name Address City State Product Type (TOE) Initiatives (Licensee factories are (Workers, Staff, (WWB) blank) Contract Staff) Argentina Accecuer SA Juan Zanella 4656 Caseros Accessories <1000 Capital Argentina Best Sox S.A. Charlone 1446 Federal Apparel <1000 Argentina Estex Argentina S.R.L. Superi, 3530 Caba Apparel <1000 Argentina Gitti SRL Italia 4043 Mar del Plata Apparel <1000 Argentina Manufactura Arrecifes S.A. Ruta Nacional 8, Kilometro 178 Arrecifes Apparel <1000 Argentina Procesadora Serviconf SRL Gobernardor Ramon Castro 4765 Vicente Lopez Apparel <1000 Capital Argentina Spring S.R.L. Darwin, 173 Federal Apparel <1000 Asamblea (101) #536, Villa Lynch Argentina TEXINTER S.A. Texinter S.A. B1672AIB, Buenos Aires Buenos Aires <1000 Argentina Underwear M&S, S.R.L Levalle 449 Avellaneda Apparel <1000 Argentina Vira Offis S.A. Virasoro, 3570 Rosario Apparel <1000 Plot # 246-249, Shiddirgonj, Bangladesh Ananta Apparels Ltd. Nazmul Hoque Narayangonj-1431 Narayangonj Apparel 1000-5000 WWB Ananta KASHPARA, NOYABARI, Bangladesh Ananta Denim Technology Ltd. Mr. Zakaria Habib Tanzil KANCHPUR Narayanganj Apparel 1000-5000 WWB Ananta Ayesha Clothing Company Ltd (Ayesha Bangobandhu Road, Tongabari, Clothing Company Ltd,Hamza Trims Ltd, Gazirchat Alia Madrasha, Ashulia, Bangladesh Hamza Clothing Ltd) Ayesha Clothing Company Ltd( Dhaka Dhaka Apparel 1000-5000 Jamgora, Post Office : Gazirchat Ayesha Clothing Company Ltd (Ayesha Ayesha Clothing Company Ltd(Unit-1)d Alia Madrasha, P.S : Savar, Bangladesh Washing Ltd.) (Ayesha Washing Ltd) Dhaka Dhaka Apparel 1000-5000 Khejur Bagan, Bara Ashulia, Bangladesh Cosmopolitan Industries PVT Ltd CIPL Savar Dhaka Apparel 1000-5000 WWB Epic Designers Ltd 1612, South Salna, Salna Bazar, Bangladesh Cutting Edge Industries Ltd. -

Chinese and Global Distribution of H9 Subtype Avian Influenza Viruses
Chinese and Global Distribution of H9 Subtype Avian Influenza Viruses Wenming Jiang., Shuo Liu., Guangyu Hou, Jinping Li, Qingye Zhuang, Suchun Wang, Peng Zhang, Jiming Chen* The Laboratory of Avian Disease Surveillance, China Animal Health and Epidemiology Center, Qingdao, China Abstract H9 subtype avian influenza viruses (AIVs) are of significance in poultry and public health, but epidemiological studies about the viruses are scarce. In this study, phylogenetic relationships of the viruses were analyzed based on 1233 previously reported sequences and 745 novel sequences of the viral hemagglutinin gene. The novel sequences were obtained through large-scale surveys conducted in 2008-2011 in China. The results revealed distinct distributions of H9 subtype AIVs in different hosts, sites and regions in China and in the world: (1) the dominant lineage of H9 subtype AIVs in China in recent years is lineage h9.4.2.5 represented by A/chicken/Guangxi/55/2005; (2) the newly emerging lineage h9.4.2.6, represented by A/chicken/Guangdong/FZH/2011, has also become prevalent in China; (3) lineages h9.3.3, h9.4.1 and h9.4.2, represented by A/duck/Hokkaido/26/99, A/quail/Hong Kong/G1/97 and A/chicken/Hong Kong/G9/97, respectively, have become globally dominant in recent years; (4) lineages h9.4.1 and h9.4.2 are likely of more risk to public health than others; (5) different lineages have different transmission features and host tropisms. This study also provided novel experimental data which indicated that the Leu-234 (H9 numbering) motif in the viral hemagglutinin gene is an important but not unique determinant in receptor-binding preference. -
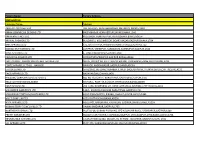
Factory Name
Factory Name Factory Address BANGLADESH Company Name Address AKH ECO APPARELS LTD 495, BALITHA, SHAH BELISHWER, DHAMRAI, DHAKA-1800 AMAN GRAPHICS & DESIGNS LTD NAZIMNAGAR HEMAYETPUR,SAVAR,DHAKA,1340 AMAN KNITTINGS LTD KULASHUR, HEMAYETPUR,SAVAR,DHAKA,BANGLADESH ARRIVAL FASHION LTD BUILDING 1, KOLOMESSOR, BOARD BAZAR,GAZIPUR,DHAKA,1704 BHIS APPARELS LTD 671, DATTA PARA, HOSSAIN MARKET,TONGI,GAZIPUR,1712 BONIAN KNIT FASHION LTD LATIFPUR, SHREEPUR, SARDAGONI,KASHIMPUR,GAZIPUR,1346 BOVS APPARELS LTD BORKAN,1, JAMUR MONIPURMUCHIPARA,DHAKA,1340 HOTAPARA, MIRZAPUR UNION, PS : CASSIOPEA FASHION LTD JOYDEVPUR,MIRZAPUR,GAZIPUR,BANGLADESH CHITTAGONG FASHION SPECIALISED TEXTILES LTD NO 26, ROAD # 04, CHITTAGONG EXPORT PROCESSING ZONE,CHITTAGONG,4223 CORTZ APPARELS LTD (1) - NAWJOR NAWJOR, KADDA BAZAR,GAZIPUR,BANGLADESH ETTADE JEANS LTD A-127-131,135-138,142-145,B-501-503,1670/2091, BUILDING NUMBER 3, WEST BSCIC SHOLASHAHAR, HOSIERY IND. ATURAR ESTATE, DEPOT,CHITTAGONG,4211 SHASAN,FATULLAH, FAKIR APPARELS LTD NARAYANGANJ,DHAKA,1400 HAESONG CORPORATION LTD. UNIT-2 NO, NO HIZAL HATI, BAROI PARA, KALIAKOIR,GAZIPUR,1705 HELA CLOTHING BANGLADESH SECTOR:1, PLOT: 53,54,66,67,CHITTAGONG,BANGLADESH KDS FASHION LTD 253 / 254, NASIRABAD I/A, AMIN JUTE MILLS, BAYEZID, CHITTAGONG,4211 MAJUMDER GARMENTS LTD. 113/1, MUDAFA PASCHIM PARA,TONGI,GAZIPUR,1711 MILLENNIUM TEXTILES (SOUTHERN) LTD PLOTBARA #RANGAMATIA, 29-32, SECTOR ZIRABO, # 3, EXPORT ASHULIA,SAVAR,DHAKA,1341 PROCESSING ZONE, CHITTAGONG- MULTI SHAF LIMITED 4223,CHITTAGONG,BANGLADESH NAFA APPARELS LTD HIJOLHATI, -

Civil-Military Change in China: Elites, Institutes, and Ideas After the 16Th Party Congress
CIVIL-MILITARY CHANGE IN CHINA: ELITES, INSTITUTES, AND IDEAS AFTER THE 16TH PARTY CONGRESS Edited by Andrew Scobell Larry Wortzel September 2004 ***** The views expressed in this report are those of the authors and do not necessarily refl ect the offi cial policy or position of the Department of the Army, the Department of Defense, or the U.S. Government. This report is cleared for public release; distribution is unlimited. ***** Comments pertaining to this report are invited and should be forwarded to: Director, Strategic Studies Institute, U.S. Army War College, 122 Forbes Ave, Carlisle, PA 17013-5244. Copies of this report may be obtained from the Publications Offi ce by calling (717) 245-4133, FAX (717) 245-3820, or by e-mail at [email protected] ***** All Strategic Studies Institute (SSI) monographs are available on the SSI Homepage for electronic dissemination. SSI’s Homepage address is: http:// www.carlisle.army.mil/ssi/ ***** The Strategic Studies Institute publishes a monthly e-mail newsletter to update the national security community on the research of our analysts, recent and forthcoming publications, and upcoming conferences sponsored by the Institute. Each newsletter also provides a strategic commentary by one of our research analysts. If you are interested in receiving this newsletter, please let us know by e-mail at [email protected] or by calling (717) 245-3133. ISBN 1-58487-165-2 ii CONTENTS Foreword Ambassador James R. Lilley............................................................................ v 1. Introduction Andrew Scobell and Larry Wortzel................................................................. 1 2. Party-Army Relations Since the 16th Party Congress: The Battle of the “Two Centers”? James C. -

Civil-Military Change in China: Elites, Institutes, and Ideas After the 16Th Party Congress
CIVIL-MILITARY CHANGE IN CHINA: ELITES, INSTITUTES, AND IDEAS AFTER THE 16TH PARTY CONGRESS Edited by Andrew Scobell Larry Wortzel September 2004 Visit our website for other free publication downloads Strategic Studies Institute Home To rate this publication click here. ***** The views expressed in this report are those of the authors and do not necessarily reflect the official policy or position of the Department of the Army, the Department of Defense, or the U.S. Government. This report is cleared for public release; distribution is unlimited. ***** Comments pertaining to this report are invited and should be forwarded to: Director, Strategic Studies Institute, U.S. Army War College, 122 Forbes Ave, Carlisle, PA 17013-5244. Copies of this report may be obtained from the Publications Office by calling (717) 245-4133, FAX (717) 245-3820, or by e-mail at [email protected] ***** All Strategic Studies Institute (SSI) monographs are available on the SSI Homepage for electronic dissemination. SSI’s Homepage address is: http:// www.carlisle.army.mil/ssi/ ***** The Strategic Studies Institute publishes a monthly e-mail newsletter to update the national security community on the research of our analysts, recent and forthcoming publications, and upcoming conferences sponsored by the Institute. Each newsletter also provides a strategic commentary by one of our research analysts. If you are interested in receiving this newsletter, please let us know by e-mail at [email protected] or by calling (717) 245-3133. ISBN 1-58487-165-2 ii CONTENTS Foreword Ambassador James R. Lilley ............................................................................ v 1. Introduction Andrew Scobell and Larry Wortzel ................................................................ -

Global Factory List As of August 3Rd, 2020
Global Factory List as of August 3rd, 2020 Target is committed to providing increased supply chain transparency. To meet this objective, Target publishes a list of all tier one factories that produce our owned-brand products, national brand products where Target is the importer of record, as well as tier two apparel textile mills and wet processing facilities. Target partners with its vendors and suppliers to maintain an accurate factory list. The list below represents factories as of August 3rd, 2020. This list is subject to change and updates will be provided on a quarterly basis. Factory Name State/Province City Address AMERICAN SAMOA American Samoa Plant Pago Pago 368 Route 1,Tutuila Island ARGENTINA Angel Estrada Cla. S.A, Buenos Aires Ciudad de Buenos Aires Ruta Nacional N 38 Km. 1,155,Provincia de La Rioja AUSTRIA Tiroler Glashuette GmbH Werk: Schneegattern Oberosterreich Lengau Kobernauserwaldstrase 25, BAHRAIN WestPoint Home Bahrain W.L.L. Al Manamah (Al Asimah) Riffa Building #1912, Road # 5146, Block 951,South Alba Industrial Area, Askar BANGLADESH Campex (BD) Limited Chittagong zila Chattogram Building-FS SFB#06, Sector#01, Road#02, Chittagong Export Processing Zone,, Canvas Garments (Pvt.) Ltd Chittagong zila Chattogram 301, North Baizid Bostami Road,,Nasirabad I/A, Canvas Building Chittagong Asian Apparels Chittagong zila Chattogram 132 Nasirabad Indstrial Area,Chattogram Clifton Cotton Mills Ltd Chittagong zila Chattogram CDA plot no-D28,28-d/2 Char Ragmatia Kalurghat, Clifton Textile Chittagong zila Chattogram 180 Nasirabad Industrial Area,Baizid Bostami Road Fashion Watch Limited Chittagong zila Chattogram 1363/A 1364 Askarabad, D.T. Road,Doublemoring, Chattogram, Bangladesh Fortune Apparels Ltd Chittagong zila Chattogram 135/142 Nasirabad Industrial Area,Chattogram KDS Garment Industries Ltd. -

Study of Symbolic Expressions in Peking Opera'scostumes and Lyrics
University of Central Florida STARS Electronic Theses and Dissertations, 2004-2019 2008 Study Of Symbolic Expressions In Peking Opera'scostumes And Lyrics Yiman Li University of Central Florida Part of the Communication Commons Find similar works at: https://stars.library.ucf.edu/etd University of Central Florida Libraries http://library.ucf.edu This Masters Thesis (Open Access) is brought to you for free and open access by STARS. It has been accepted for inclusion in Electronic Theses and Dissertations, 2004-2019 by an authorized administrator of STARS. For more information, please contact [email protected]. STARS Citation Li, Yiman, "Study Of Symbolic Expressions In Peking Opera'scostumes And Lyrics" (2008). Electronic Theses and Dissertations, 2004-2019. 3487. https://stars.library.ucf.edu/etd/3487 STUDY OF SYMBOLIC EXPRESSIONS IN PEKING OPERA’S COSTUMES AND LYRICS by YIMAN LI B.A. Capital University of Economics and Business, 2003 A thesis submitted in partial fulfillment of the requirements for the degree of Master of Arts in the Nicholson School of Communication in the College of Sciences at the University of Central Florida Orlando, Florida Spring Term 2008 ABSTRACT This thesis represents an analysis of symbolic expressions used to convey traditional Chinese cultural values in marital relations as expressed through costumes and lyrics in Peking Opera plays and performances. Two symbols, dragon and phoenix, were selected from the costume collection. Four symbols—bird, tiger, wild goose, and dragon—were selected from compilations of lyrics. These symbols were selected because they expressed Chinese core cultural values, an imperial ideology based on Confucian thoughts, which were practiced rigidly during Qing Dynasty (1644-1911). -

Download Article
Advances in Social Science, Education and Humanities Research, volume 284 2nd International Conference on Art Studies: Science, Experience, Education (ICASSEE 2018) The Artistic Multidimensional Performance of Red and Green Porcelain in Jin Dynasty Shandan Ms. Xiaosong Zou* Jingdezhen Ceramic Institute Jingdezhen Ceramic Institute Jingdezhen, China Jingdezhen, China *Corresponding Author Abstract—Red and green porcelain is a glazed painted such as the statue of the “goddess” of the pottery sculpture porcelain created in Cizhou kiln during the middle and late Jin discovered at the Niuheliang site of Hongshan Culture, which Dynasty. It is a kind of multi-color porcelain which applies is the earliest figure statue discovered so far in China. After paintings with red, green and yellow colors on the already entering the civilized society, the types and materials of finished white porcelain, and then applies the second high sculptures have become more and more abundant, the temperature bake in kiln. The red and green porcelains of Jin technology also has been continuously improved. The Tang Dynasty embody the extraordinary decorative arts and cultural and Song Dynasties were the mature period of the implications with brilliant colors, vivid shapes and smooth development of Chinese sculpture art, especially the stone brushwork, which also occupy an important position in the carvings, pottery figurines and decorative sculptures of the history of Chinese porcelain. This paper attempts to explain the Tang Dynasty, which occupied a very important position in the main reasons for its outstanding achievements by analyzing the influence of various art forms such as sculpture, painting and history of Chinese sculpture art.