Border Control Management
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

The Antitrust Implications of Computer Reservations Systems (CRS's) Derek Saunders
Journal of Air Law and Commerce Volume 51 | Issue 1 Article 5 1985 The Antitrust Implications of Computer Reservations Systems (CRS's) Derek Saunders Follow this and additional works at: https://scholar.smu.edu/jalc Recommended Citation Derek Saunders, The Antitrust Implications of Computer Reservations Systems (CRS's), 51 J. Air L. & Com. 157 (1985) https://scholar.smu.edu/jalc/vol51/iss1/5 This Comment is brought to you for free and open access by the Law Journals at SMU Scholar. It has been accepted for inclusion in Journal of Air Law and Commerce by an authorized administrator of SMU Scholar. For more information, please visit http://digitalrepository.smu.edu. THE ANTITRUST IMPLICATIONS OF COMPUTER RESERVATIONS SYSTEMS (CRS's) DEREK SAUNDERS THE PASSAGE of the Airline Deregulation Act' dramat- ically altered the airline industry. Market forces, rather than government agencies, 2 began to regulate the indus- try. The transition, however, has not been an easy one. Procedures and relationships well suited to a regulated in- dustry are now viewed as outdated, onerous, and even anticompetitive. The current conflict over carrier-owned computer res- ervation systems (CRS's) represents one instance of these problems.3 The air transportation distribution system re- lies heavily on the use of CRS's, particularly since deregu- lation and the resulting increase in airline activity. 4 One I Pub. L. No. 95-504, 92 Stat. 1705 (codified at 49 U.S.C.A. § 1401 (Supp. 1984)). 2 Competitive Market Investigation, CAB Docket 36,595 (Dec. 16, 1982) at 3. For a discussion of deregulation in general and antitrust problems specifically, see Beane, The Antitrust Implications of Airline Deregulation, 45 J. -

AVIATION Disaster Litigation and Investigations
AVIATION Disaster Litigation and Investigations Attorney Advertising Our attorneys litigate diverse and complex cases for plane crash victims and their families throughout the world and injured crash survivors, as well as people who have suffered as a result of aviation security, safety, or passenger rights violations. At Motley Rice, our goal is not only to seek justice and compensation for our clients, but we also seek accountability from defendants and improvements in aviation safety and security standards. We give our clients a voice when they feel the most vulnerable. MARY F. SCHIAVO Licensed in DC, FL, MD, MO, SC JAMES R. BRAUCHLE Licensed in SC Our Approach At Motley Rice, our goal is not only to seek improvements in aviation safety and security standards through our civil justice system but also to give our clients a voice at a time in their lives when they feel the most vulnerable and to win for them the compensation they are owed and the changes they deserve. At Motley Rice, we work to help aviation disaster COMPASSION, GUIDANCE AND SUPPORT survivors and victims’ families, as well as victims We understand the pain, confusion and questions that of passenger rights violations and other safety and often follow tragic events and know that many clients security violations. feel overwhelmed by the emotional circumstances Our aviation attorneys have experience handling a which brought them to us. While coping with the loss wide variety of aviation cases. We recognize that of a loved one or the devastation of a permanent injury, survivors and family members of victims have many survivors and family members face numerous other concerns following an aviation disaster and may face obstacles such as medical expenses, loss of income considerations of complex legal rights and actions. -

Flight Inspection History Written by Scott Thompson - Sacramento Flight Inspection Office (May 2008)
Flight Inspection History Written by Scott Thompson - Sacramento Flight Inspection Office (May 2008) Through the brief but brilliant span of aviation history, the United States has been at the leading edge of advancing technology, from airframe and engines to navigation aids and avionics. One key component of American aviation progress has always been the airway and navigation system that today makes all-weather transcontinental flight unremarkable and routine. From the initial, tentative efforts aimed at supporting the infant air mail service of the early 1920s and the establishment of the airline industry in the 1930s and 1940s, air navigation later guided aviation into the jet age and now looks to satellite technology for direction. Today, the U.S. Federal Aviation Administration (FAA) provides, as one of many services, the management and maintenance of the American airway system. A little-seen but still important element of that maintenance process is airborne flight inspection. Flight inspection has long been a vital part of providing a safe air transportation system. The concept is almost as old as the airways themselves. The first flight inspectors flew war surplus open-cockpit biplanes, bouncing around with airmail pilots and watching over a steadily growing airway system predicated on airway light beacons to provide navigational guidance. The advent of radio navigation brought an increased importance to the flight inspector, as his was the only platform that could evaluate the radio transmitters from where they were used: in the air. With the development of the Instrument Landing System (ILS) and the Very High Frequency Omni-directional Range (VOR), flight inspection became an essential element to verify the accuracy of the system. -

42Genno44.Pdf
U.S. Customs and Border Protection CBP Decisions [USCBP 2007–0061; CBP Dec. No. 08–26] RIN 1651–AA69 8 CFR Parts 212 and 235 DEPARTMENT OF STATE 22 CFR Parts 41 and 53 Documents Required for Travelers Departing From or Arriving in the United States at Sea and Land Ports-of-Entry From Within the Western Hemisphere AGENCIES: U.S. Customs and Border Protection, Department of Homeland Security; Bureau of Consular Affairs, Department of State. ACTION: Final rule. SUMMARY: This rule finalizes the second phase of a joint Depart- ment of Homeland Security and Department of State plan, known as the Western Hemisphere Travel Initiative, to implement new docu- mentation requirements for U.S. citizens and certain nonimmigrant aliens entering the United States. This final rule details the docu- ments U.S. citizens1 and nonimmigrant citizens of Canada, Ber- muda, and Mexico will be required to present when entering the United States from within the Western Hemisphere at sea and land ports-of-entry. DATES: This final rule is effective on June 1, 2009. FOR FURTHER INFORMATION CONTACT: Department of Homeland Security: Colleen Manaher, WHTI, Office of Field Operations, U.S. Customs and Border Protection, 1300 1 ‘‘U.S. citizens’’ as used in this rule refers to both U.S. citizens and U.S. non-citizen na- tionals. 1 2 CUSTOMS BULLETIN AND DECISIONS, VOL. 42, NO. 44, OCTOBER 23, 2008 Pennsylvania Avenue, NW., Room 5.4–D, Washington, DC 20229, telephone number (202) 344–1220. Department of State: Consuelo Pachon, Office of Passport Policy, Planning and Advisory Services, Bureau of Consular Affairs, tele- phone number (202) 663–2662. -

Hindenburg: Last of The1 2 Gtaihi
www.PDHcenter.com www.PDHonline.org Table of Contents Slide/s Part Description 1N/ATitle 2 N/A Table of Contents 3~96 1 Exceeding the Grasp 97~184 2 Biggest Birds That Ever Flew 185~281 3 Triumph and Tragedy 282~354 4 Made in America 355~444 5 The Future is Now 445~541 6 LZ-129 542~594 7 Flight Operations 595~646 8 Magic Carpet Ride 647~759 9 Oh, The Humanity! 760~800 10 Back to the Future Hindenburg: Last of the1 2 GtAihi Part 1 “Ah, but a man’s reach should exceed his grasp, or what’s a heaven for?”for? Robert Browning, Poet Exceeding the Grasp 3 4 “...as by certain mechanical art and power to fly; The Dreams of Inventors so nicely was it balanced by weights and put in motion by hidden and enclosed air” Archytas of Tarentura, 400 B.C. 5 6 © J.M. Syken 1 www.PDHcenter.com www.PDHonline.org “…Then we are told of a monk who attempted a flight with wings from the top of a tower in Spain. He broke his legs, and wasafterwardburnedasasorcerer. Another similar trial was made from St. Mark’s steeple in Venice; another in Nuremberg;andsoonԝ - legs or arms were usually broken, occasionally a neck. In the sixteenth century we read of a certain Italian who went to the court of James IV of Scotland, and attempted to fly from the walls of Sterling Castle to France. His thig h was bkbroken; btbut,asareasonfor the failure, he asserted that some of the feathers used in constructing his wings “…Many other trials have there been of the same character. -
CBP Traveler Entry Forms CBP Declaration, I-94, and I-94W Welcome to the United States
CBP Traveler Entry Forms CBP Declaration, I-94, and I-94W Welcome to the United States Whether you are a visitor to the United States or U.S. citizen, each individual arriving into the United States must complete one or more of U.S. Customs and Border Protection’s (CBP) entry forms. This publication will provide you with detailed instructions on filling out those entry forms. Every traveler must complete the CBP Declaration Form 6059B. This form provides CBP with basic information about who you are and what you are bringing into the country, such as agriculture products and whether or not you have visited a farm prior to traveling to the United States. If you are traveling with other immediate family members, you can complete one form for your entire family. Some travelers will need to complete a CBP Form I-94. This form must be completed by all travelers except U.S. citizens, returning resident aliens, aliens with immigrant visas, and Canadian citizens who are visiting or in transit. Nonimmigrant visitors who are seeking entry to the United States under the Visa Waiver Program must fill out the CBP Form I-94W. If you have questions about your form that are not answered in this publication, please don’t hesitate to ask a CBP officer for help. CBP Declaration Form (6059B) Smith mona L 1 5 0 5 5 6 2 151 main Street Greenville IN USa 123456789 USa itaLy dL 33 x x x x x x x x 1,800.00 Mona L. Smith 16/12/02 (see next page for side 2) CBP Traveler Entry Forms 1 CBP Declaration Form (side 2) 2 CBP Declaration Form Instructions Side 1 1. -

Electronic Identification (E-ID)
EXPLAINING INTERNATIONAL IT APPLICATION LEADERSHIP: Electronic Identification Daniel Castro | September 2011 Explaining International Leadership: Electronic Identification Systems BY DANIEL CASTRO SEPTEMBER 2011 ITIF ALSO EXTENDS A SPECIAL THANKS TO THE SLOAN FOUNDATION FOR ITS GENEROUS SUPPORT FOR THIS SERIES. SEPTEMBER 2011 THE INFORMATION TECHNOLOGY & INNOVATION FOUNDATION | SEPTEMBER 2011 PAGE II TABLE OF CONTENTS Executive Summary ........................................................................................................ V Introduction..................................................................................................................... 1 Background ....................................................................................................................... 1 Box 1: Electronic Passports ............................................................................................. 3 Terminology and Technology ........................................................................................... 3 Electronic Signatures, Digital Signatures and Digital Certificates ............................... 3 Identification, Authentication and Signing ................................................................ 4 Benefits of e-ID Systems ............................................................................................ 5 Electronic Identification Systems: Deployment and Use .............................................. 6 Country Profiles ............................................................................................................. -
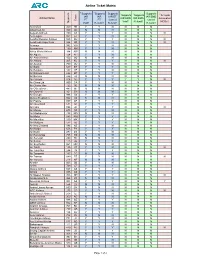
08-06-2021 Airline Ticket Matrix (Doc 141)
Airline Ticket Matrix 1 Supports 1 Supports Supports Supports 1 Supports 1 Supports 2 Accepts IAR IAR IAR ET IAR EMD Airline Name IAR EMD IAR EMD Automated ET ET Cancel Cancel Code Void? Refund? MCOs? Numeric Void? Refund? Refund? Refund? AccesRail 450 9B Y Y N N N N Advanced Air 360 AN N N N N N N Aegean Airlines 390 A3 Y Y Y N N N N Aer Lingus 053 EI Y Y N N N N Aeroflot Russian Airlines 555 SU Y Y Y N N N N Aerolineas Argentinas 044 AR Y Y N N N N N Aeromar 942 VW Y Y N N N N Aeromexico 139 AM Y Y N N N N Africa World Airlines 394 AW N N N N N N Air Algerie 124 AH Y Y N N N N Air Arabia Maroc 452 3O N N N N N N Air Astana 465 KC Y Y Y N N N N Air Austral 760 UU Y Y N N N N Air Baltic 657 BT Y Y Y N N N Air Belgium 142 KF Y Y N N N N Air Botswana Ltd 636 BP Y Y Y N N N Air Burkina 226 2J N N N N N N Air Canada 014 AC Y Y Y Y Y N N Air China Ltd. 999 CA Y Y N N N N Air Choice One 122 3E N N N N N N Air Côte d'Ivoire 483 HF N N N N N N Air Dolomiti 101 EN N N N N N N Air Europa 996 UX Y Y Y N N N Alaska Seaplanes 042 X4 N N N N N N Air France 057 AF Y Y Y N N N Air Greenland 631 GL Y Y Y N N N Air India 098 AI Y Y Y N N N N Air Macau 675 NX Y Y N N N N Air Madagascar 258 MD N N N N N N Air Malta 643 KM Y Y Y N N N Air Mauritius 239 MK Y Y Y N N N Air Moldova 572 9U Y Y Y N N N Air New Zealand 086 NZ Y Y N N N N Air Niugini 656 PX Y Y Y N N N Air North 287 4N Y Y N N N N Air Rarotonga 755 GZ N N N N N N Air Senegal 490 HC N N N N N N Air Serbia 115 JU Y Y Y N N N Air Seychelles 061 HM N N N N N N Air Tahiti 135 VT Y Y N N N N N Air Tahiti Nui 244 TN Y Y Y N N N Air Tanzania 197 TC N N N N N N Air Transat 649 TS Y Y N N N N N Air Vanuatu 218 NF N N N N N N Aircalin 063 SB Y Y N N N N Airlink 749 4Z Y Y Y N N N Alaska Airlines 027 AS Y Y Y N N N Alitalia 055 AZ Y Y Y N N N All Nippon Airways 205 NH Y Y Y N N N N Amaszonas S.A. -

Identity Documents Act (2000, Amended 2017)
Issuer: Riigikogu Type: act In force from: 01.04.2017 In force until: 30.06.2017 Translation published: 28.03.2017 Identity Documents Act1 Passed 15.02.1999 RT I 1999, 25, 365 Entry into force 01.01.2000 Amended by the following acts Passed Published Entry into force 08.03.2000 RT I 2000, 26, 150 15.12.2000 21.03.2000 RT I 2000, 25, 148 29.03.2000 17.05.2000 RT I 2000, 40, 254 01.08.2000 08.11.2000 RT I 2000, 86, 550 02.12.2000 17.01.2001 RT I 2001, 16, 68 16.02.2001 07.03.2001 RT I 2001, 31, 173 07.04.2001 12.06.2001 RT I 2001, 56, 338 07.07.2001 19.06.2002 RT I 2002, 61, 375 01.08.2002 19.06.2002 RT I 2002, 63, 387 01.09.2002 15.10.2002 RT I 2002, 90, 516 01.12.2002 15.01.2003 RT I 2003, 13, 65 01.05.2003 22.01.2003 RT I 2003, 15, 87 27.02.2003 03.12.2003 RT I 2003, 78, 527 01.01.2004 17.12.2003 RT I 2004, 2, 4 16.01.2004 14.04.2004 RT I 2004, 28, 189 01.05.2004 14.12.2005 RT I 2006, 2, 3 01.07.2006 15.02.2006 RT I 2006, 12, 79 01.04.2006 17.05.2006 RT I 2006, 26, 191 01.08.2006 10.05.2006 RT I 2006, 26, 193 01.01.2007 07.06.2006 RT I 2006, 29, 221 28.08.2006, partially02.01.2007 14.11.2007 RT I 2007, 62, 394 Entry into force upon accession of Estonia to the European Union common visa space partially 21.12.2007 and partially 30.03.2008. -

Vietnam Border Management > Case Study
Vietnam border management > Case study Vietnam’s airports experience improved border security with Rockwell Collins solution. A CRITICAL BALANCE CHALLENGE: Governments everywhere know that national security threats are > Significant growth in air passenger travel combined with manual out there, but being able to recognize who and what constitutes a processes created potential increases in airport security risks. threat – and to contain it before it reaches the border – is critical to securing a country’s citizens, infrastructure and economy. SOLUTION: > With the Rockwell Collins solution, Vietnam has improved its Governments of countries like Vietnam, with its air traffic ability to counter threats by pre-screening passenger/crew data passenger numbers surging (up 29 percent to 52 million in 20161), before arrival at immigration checkpoints as well as improved understand the potential issues this increase in travelers poses to passenger flow at airports. its security. Government officials in Vietnam are working hard to balance the ability to protect its borders and detect threats with RESULTS: the economic benefits associated with tourism and the growth > As a result of the implementation of the Rockwell Collins’ ARINC of the country’s aviation industry. Border Management Solution (ABMS), Vietnam’s international airports have seen a 90 percent improvement in passenger processing times and a 95 percent improvement in data quality compared with the previous manually handled data. rockwellcollins.com/airports As a result of pre-clearance of passenger details, Vietnam’s international airports have seen a 90 percent improvement in passenger processing times and a 95 percent improvement in data quality compared with the previous manually-handled data. -

Why Some Airport-Rail Links Get Built and Others Do Not: the Role of Institutions, Equity and Financing
Why some airport-rail links get built and others do not: the role of institutions, equity and financing by Julia Nickel S.M. in Engineering Systems- Massachusetts Institute of Technology, 2010 Vordiplom in Wirtschaftsingenieurwesen- Universität Karlsruhe, 2007 Submitted to the Department of Political Science in partial fulfillment of the requirements for the degree of Master of Science in Political Science at the MASSACHUSETTS INSTITUTE OF TECHNOLOGY February 2011 © Massachusetts Institute of Technology 2011. All rights reserved. Author . Department of Political Science October 12, 2010 Certified by . Kenneth Oye Associate Professor of Political Science Thesis Supervisor Accepted by . Roger Peterson Arthur and Ruth Sloan Professor of Political Science Chair, Graduate Program Committee 1 Why some airport-rail links get built and others do not: the role of institutions, equity and financing by Julia Nickel Submitted to the Department of Political Science On October 12, 2010, in partial fulfillment of the Requirements for the Degree of Master of Science in Political Science Abstract The thesis seeks to provide an understanding of reasons for different outcomes of airport ground access projects. Five in-depth case studies (Hongkong, Tokyo-Narita, London- Heathrow, Chicago- O’Hare and Paris-Charles de Gaulle) and eight smaller case studies (Kuala Lumpur, Seoul, Shanghai-Pudong, Bangkok, Beijing, Rome- Fiumicino, Istanbul-Atatürk and Munich- Franz Josef Strauss) are conducted. The thesis builds on existing literature that compares airport-rail links by explicitly considering the influence of the institutional environment of an airport on its ground access situation and by paying special attention to recently opened dedicated airport expresses in Asia. -

U.S. Customs and Border Protection * Volume 4, Issue 3
U.S. Customs and Border Protection H Volume 4, Issue 3 SPECIAL 9 / 11 EDITION In Memoriam H H H In honor of CBP employees who have died in the line of duty 2011 Hector R. Clark Eduardo Rojas Jr. 2010 Charles F. Collins II Michael V. Gallagher Brian A. Terry Mark F. Van Doren John R. Zykas 2009 Nathaniel A. Afolayan Cruz C. McGuire Trena R. McLaughlin Robert W. Rosas Jr. 2008 Luis A. Aguilar Jarod Dittman 2007 Julio E. Baray Eric Cabral Richard Goldstein Ramon Nevarez Jr. Robert Smith Clinton B. Thrasher David J. Tourscher 2006 Nicholas D. Greenig David N. Webb 2004 Travis Attaway George DeBates Jeremy Wilson 2003 James P. Epling H H H For a historic listing honoring federal personnel who gave their lives while securing U.S. borders, please visit CBP.gov Vol 4, Issue 3 CONTENTS H FEATURES VOL 4, ISSUE 3 4 A Day Like No Other SEPTEMBER 11, 2011 In the difficult hours and days after the SECRETARY OF HOMELAND SECURITY Sept. 11 attacks, confusion and fear Janet Napolitano turned to commitment and resolve as COMMISSIONER, the agencies that eventually would form 4 U.S. CUSTOMS AND BORDER PROTECTION CBP responded to protect America. Alan D. Bersin ASSISTANT COMMISSIONER, 16 Collective Memory OFFICE OF PUBLIC AFFAIRS Melanie Roe CBP employees look back on the day that united an agency… and a nation. EDITOR Laurel Smith 16 CONTRIBUTING EDITORS 41 Attacks Redefine Eric Blum Border Security Susan Holliday Marcy Mason CBP responds to challenge by coming Jay Mayfield together to build layers of security Jason McCammack extending around the globe, upgrading its ability to keep dangerous people PRODUCTION MANAGER Tracie Parker and things out of the homeland.