Baseband Attacks: Remote Exploitation of Memory Corruptions in Cellular Protocol Stacks
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-

Case Studies
Case studies November 2006 Buyouts Chorion New investment - UK - Media In May 2006, 3i and funds completed the This strong relationship with Waheed Alli acquisition of Chorion, a UK-based coupled with 3i’s in-depth media sector intellectual property owning, brand creation knowledge, through deals such as and management business, in a €198 Sparrowhawk Media and Pinewood million public to private transaction. Shepperton, secured the investment opportunity. Chorion, previously listed on AIM, generates revenue by charging royalties on The investment in Chorion represented an toy merchandising, book publishing and TV. opportunity to acquire a portfolio of high-quality It operates on a global basis, with a brands which have a proven track record of portfolio which includes well recognised publishing success and which are ripe for classic children’s brands such as Noddy, further development. Chorion has an excellent Famous Five, and the Mr Men, as well as platform from which to expand into new the works of crime writers such as Agatha geographic markets, and a proven Christie (Miss Marple and Poirot) and management team which is well placed to Georges Simenon (Maigret). capitalise on this opportunity with the strategic support and financial backing of 3i. 3i worked exclusively with Chorion’s Chairman Waheed Alli and the incumbent management team, responsible for almost trebling the value of the business since 2002, for nearly a year before the deal completed. Buyouts Azzurri Communications Realisation - UK - Technology During the six years that 3i was invested Azzurri made 15 strategic acquisitions and, combined with strong organic growth, a business with revenues of £115 million (for the year to June 2006) was built as a result. -
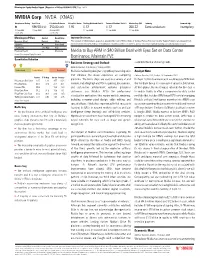
NVIDIA Corp NVDA (XNAS)
Morningstar Equity Analyst Report | Report as of 14 Sep 2020 04:02, UTC | Page 1 of 14 NVIDIA Corp NVDA (XNAS) Morningstar Rating Last Price Fair Value Estimate Price/Fair Value Trailing Dividend Yield % Forward Dividend Yield % Market Cap (Bil) Industry Stewardship Q 486.58 USD 250.00 USD 1.95 0.13 0.13 300.22 Semiconductors Exemplary 11 Sep 2020 11 Sep 2020 20 Aug 2020 11 Sep 2020 11 Sep 2020 11 Sep 2020 21:37, UTC 01:27, UTC Morningstar Pillars Analyst Quantitative Important Disclosure: Economic Moat Narrow Wide The conduct of Morningstar’s analysts is governed by Code of Ethics/Code of Conduct Policy, Personal Security Trading Policy (or an equivalent of), Valuation Q Overvalued and Investment Research Policy. For information regarding conflicts of interest, please visit http://global.morningstar.com/equitydisclosures Uncertainty Very High High Financial Health — Moderate Nvidia to Buy ARM in $40 Billion Deal with Eyes Set on Data Center Source: Morningstar Equity Research Dominance; Maintain FVE Quantitative Valuation NVDA Business Strategy and Outlook could limit Nvidia’s future growth. a USA Abhinav Davuluri, CFA, Analyst, 19 August 2020 Undervalued Fairly Valued Overvalued Nvidia is the leading designer of graphics processing units Analyst Note that enhance the visual experience on computing Abhinav Davuluri, CFA, Analyst, 13 September 2020 Current 5-Yr Avg Sector Country Price/Quant Fair Value 1.67 1.43 0.77 0.83 platforms. The firm's chips are used in a variety of end On Sept. 13, Nvidia announced it would acquire ARM from Price/Earnings 89.3 37.0 21.4 20.1 markets, including high-end PCs for gaming, data centers, the SoftBank Group in a transaction valued at $40 billion. -

QUALCOMM Incorporated (Exact Name of Registrant As Specified in Its Charter)
UNITED STATES SECURITIES AND EXCHANGE COMMISSION WASHINGTON, D.C. 20549 _____________________ FORM 10-Q _____________________ (Mark one) x QUARTERLY REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the quarterly period ended December 25, 2016 OR o TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the transition period from to . Commission File Number 0-19528 QUALCOMM Incorporated (Exact name of registrant as specified in its charter) Delaware 95-3685934 (State or Other Jurisdiction of (I.R.S. Employer Incorporation or Organization) Identification No.) 5775 Morehouse Dr., San Diego, California 92121-1714 (Address of Principal Executive Offices) (Zip Code) (858) 587-1121 (Registrant’s telephone number, including area code) Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. Yes x No o Indicate by check mark whether the registrant has submitted electronically and posted on its corporate Web site, if any, every Interactive Data File required to be submitted and posted pursuant to Rule 405 of Regulation S-T (§ 232.405 of this chapter) during the preceding 12 months (or for such shorter period that the registrant was required to submit and post such files). Yes x No o Indicate by check mark whether the registrant is a large accelerated filer, an accelerated filer, a non-accelerated filer, or a smaller reporting company. -

Proceedings First Annual Palo Alto Conference
PROCEEDINGS OF THE FIRST ANNUAL PALO ALTO CONFERENCE An International Conference on the Mexican-American War and its Causes and Consequences with Participants from Mexico and the United States. Brownsville, Texas, May 6-9, 1993 Palo Alto Battlefield National Historic Site Southwest Region National Park Service I Cover Illustration: "Plan of the Country to the North East of the City of Matamoros, 1846" in Albert I C. Ramsey, trans., The Other Side: Or, Notes for the History of the War Between Mexico and the I United States (New York: John Wiley, 1850). 1i L9 37 PROCEEDINGS OF THE FIRST ANNUAL PALO ALTO CONFERENCE Edited by Aaron P. Mahr Yafiez National Park Service Palo Alto Battlefield National Historic Site P.O. Box 1832 Brownsville, Texas 78522 United States Department of the Interior 1994 In order to meet the challenges of the future, human understanding, cooperation, and respect must transcend aggression. We cannot learn from the future, we can only learn from the past and the present. I feel the proceedings of this conference illustrate that a step has been taken in the right direction. John E. Cook Regional Director Southwest Region National Park Service TABLE OF CONTENTS Introduction. A.N. Zavaleta vii General Mariano Arista at the Battle of Palo Alto, Texas, 1846: Military Realist or Failure? Joseph P. Sanchez 1 A Fanatical Patriot With Good Intentions: Reflections on the Activities of Valentin GOmez Farfas During the Mexican-American War. Pedro Santoni 19 El contexto mexicano: angulo desconocido de la guerra. Josefina Zoraida Vazquez 29 Could the Mexican-American War Have Been Avoided? Miguel Soto 35 Confederate Imperial Designs on Northwestern Mexico. -

Paradigm Shift: the Winners Are
PARADIGM SHIFT: THE WINNERS ARE Dr. Jeremy Wang Asia Pacific Executive Director, GSA July 30, 2008 GSA Mission Accelerate the growth and increase the return on invested capital of the global semiconductor industry by fostering a more effective fabless ecosystem through collaboration, integration and innovation. GSA Board of Directors Dwight Decker Sanjay Jha Jodi Shelton Danny Biran Rick Cassidy Guillame Aart de Geus Conexant Qualcomm Altera TSMC North d’Eyssautier Synopsys, America picoChip Inc. Jack Harding Colin Harris Kenneth Joyce Fu Tai Liou Steven Longoria Dr. Nicky Lu Chris eSilicon Corp PMC-Sierra, Amkor UMC IBM Etron Malachowsky Inc. Technology, Inc. NVIDIA Vahid Manian Michael Rekuc Walden Rhines Naveed Vincent Tong Dr. Albert Wu Dr. Tien Wu Broadcom Chartered Mentor Graphics Sherwani Xilinx Marvell ASE, Inc. Corporation Open-Silicon Asia-Pacific Leadership Council Chairman Dr. Chintay Shih Xiaolang Yan Ming Kai Tsai H.P. Lin Qin-Sheng Wang K.C. Shih Dr. Nicky Lu Special Advisor College of MediaTek Faraday IC China Semiconductor Global Unichip Etron Information Industry Association Science and Engineering Zhejiang University Special Advisor Gordon Gau Chou-Chye Wen-Chi Chen Dr. Woodward Dr. Zhonghan Dr. Shaojun Wei Holtek Huang VIA Yang (John) Deng Phoenix Sunplus Silicon7 Vimicro Microelectronics Jordan Wu Dr. Ki Soo Lun Zhao Dr. Ping Wu Himax Hwang Datang Spreadtrum Technologies Core Logic, Inc. Microelectronics Communications Inc. EMEA Leadership Council David Milne Jalal Bagherli David Baillie Kobi Ben-Zvi Stan Boland Wolfson Dialog CamSemi Wintegra Icera Microelectronics Semiconductor Warren East Guillame d’Eyssautier Danny Hachoen Gennady Krasnikov Chris Ladas ARM, Inc. picoChip DSP Group Mikron JSC CSR Key Topics •Analog/Mixed Signal •Wireless •Automotive Eric Mayer John Schmitz Infineon NXP Semiconductor VC Advisory Council Wayne Cantwell Steve Domenik Phillip T. -

Undercover Marine Reconnaisance Units Help to Retake Saudi City from Iraqis
`Does' sharpen readiness . just in case Milestones of Afro-American Page A-2 heritage recognized Investigation verifies Iraqi cruelty Page B1 -1 Local family makes MWR way of life Page A-5 Vol. 20, No. 5 Published at MCAS Kaneohe Bay. Also serving 1st MEB, Camp H.M. Smith and Marine Barracks, Hawaii. February 7, le Undercover Marine reconnaisance units help to retake Saudi city from Iraqis By Set. Brad Mitzeden awakening if they had come up enemy troops. Reports on Saudi KHAFJI, Saudi Arabia after us," Brown said. and Qatari losses were sketchy Saudi and Qatari forces largely Apart from keeping their at best, but indications are that fought the allied battle for this heads down, the Marines also they were light to moderate. border city. However, two recon- took other precautions such as "Those Saudis have a lot of naissance teams from the let burning all personal and offi- heart," Ingraham said. "They Marine Division worked under- cial documents and using spe- had the hard job. They came cover to help retake Khafji from cial communications procedures in and went for broke. They an armored Iraqi force which to avoid detection. made themselves targets in order invaded early Jan. 29. All in all, according to Ingra- to find the Iraqis." The Marines remained hidden ham, it was a classic reconnais- Admire said that perhaps too from the enemy during two days sance mission, albeit unplanned much attention has been given of heavy fighting, which was and particularly unnerving. to the fact that the allies pulled supported by Marine air and "I never expected that kind of back after a previous attempt artillery. -

Nombre: Fernando Vegas López-Manzanares Fecha: Febrero De 2016
Comisión Interministerial de Ciencia y Tecnología Curriculum vitae Nombre: Fernando Vegas López-Manzanares Fecha: febrero de 2016 Contiene: 148 páginas 1 Apellidos: Vegas López-Manzanares Nombre: Fernando DNI: 19848898-J Fecha de nacimiento : 29-06-64 Sexo: H Situación profesional actual Organismo: Universidad Politécnica de Valencia Facultad, Escuela o Instituto: Escuela Técnica Superior de Arquitectura Depto./Secc./Unidad estr.: Departamento de Composición Arquitectónica Dirección postal: Camino de Vera s/n – 46022 - Valencia Teléfono (indicar prefijo, número y extensión): +34.96.3877440 Fax: +34.96.3877440 Correo electrónico: [email protected] Especialización (Códigos UNESCO): 620199 Categoria profesional: TITULAR DE UNIVERSIDAD Fecha de inicio: 01-09-2003 Situación administrativa Plantilla Contratado Interino Becario Otras situaciones especificar: Dedicación A tiempo completo A tiempo parcial Líneas de investigación Breve descripción, por medio de palabras claves, de la especialización y líneas de investigación actuales. ARQUITECTURA, RESTAURACIÓN ARQUITECTÓNICA, ESTUDIOS PREVIOS A LA RESTAURACIÓN, INVESTIGACIÓN HISTÓRICA, ARQUEOLOGÍA DE LA ARQUITECTURA, HISTORIA MATERIAL DE MONUMENTOS, ARQUITECTURA TRADICIONAL Y VERNÁCULA TRAMOS DE INVESTIGACIÓN CONCEDIDOS: 2 SEXENIOS (1998-2004 y 2004-2010) ACREDITADO A PLAZA DE PROFESOR CATEDRÁTICO: FEBRERO 2016 Formación Académica Titulación Superior Centro Fecha ARQUITECTO ESP. EDIFICACIÓN UNIVERSIDAD POLITÉCNICA DE VALENCIA 26-03-1990 ARQUITECTO ESP. URBANISMO UNIVERSIDAD POLITÉCNICA DE VALENCIA -

Selected Issues for Boards of Directors in 2020 — January 2020 London London São Paulo São Paulo Brussels Milan
Selected Issues for Boards of Directors in 2020 — January 2020 London London São Paulo São Paulo Brussels Milan Rome Rome Washinton, D.C.Washington, D.C. Hong Kong Milan Beijing Beijing Brussels Buenos Aires Buenos Aires Abu Dhabi Abu Dhabi Cologne Cologne Moscow New York Frankfurt Moscow New York Frankfurt Paris Seoul Paris Seoul Table of Contents 1 Auditing and Accounting: What’s New in 2020 5 Corporate Purpose, Human Capital and Compensation Considerations 9 Board Composition and Shareholder Proposal Highlights 13 The Evolving Privacy Landscape at a Glance: Compliance Considerations for a New Decade 16 Cybersecurity: What Keeps Us Up at Night 20 CFIUS Jurisdiction Continues to Expand 22 Shareholder Engagement Trends and Considerations 26 Navigating the ESG Landscape Recent changes in political climates, legal reforms and social 29 SEC Disclosure and Proxy norms have had varying (and sometimes conflicting) impacts Guidance and Proposals on how companies are run; however, they have all contributed 33 Shareholder Activism in 2020: to a growing demand that companies expand their focus New Risks and Opportunities beyond shareholder value creation. Environmental, social for Boards of Directors and governance concerns dominate shareholder proposals and engagement efforts, and discussions of corporate purpose 36 Priorities, Trends and Developments have moved beyond the academic realm. The external threat in Enforcement and Compliance of activism has evolved, with companies facing pressure 40 View from the UK: Recent Developments from social activists and institutional investors as well as in Brexit and Corporate Governance “traditional” activists. The disruption of business practices through advances in technology and societal shifts has raised 44 International Tax: Choppy Waters new issues and questions from shareholders. -

Vodafone Mobile Broadband Readme
Vodafone Mobile Broadband Release 10.5.5.53045 RC1 ReadMe Vodafone Mobile Broadband ReadMe Contents Summary ......................................................................................................................................................................................... 3 What’s new in this release ............................................................................................................................................................ 3 Installation notes ............................................................................................................................................................................ 3 Determining which version is installed ........................................................................................................................................ 3 Requirements ................................................................................................................................................................................. 4 Supported operating systems .................................................................................................................................................. 4 Supported devices ......................................................................................................................................................................... 4 Supported external devices (VMB Full)................................................................................................................................. -

Form 10-K Nvidia Corporation
Table of Contents UNITED STATES SECURITIES AND EXCHANGE COMMISSION Washington, D.C. 20549 ____________________________________________________________________________________________ FORM 10-K [x] ANNUAL REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 For the fiscal year ended January 27, 2019 OR [_] TRANSITION REPORT PURSUANT TO SECTION 13 OR 15(d) OF THE SECURITIES EXCHANGE ACT OF 1934 Commission file number: 0-23985 NVIDIA CORPORATION (Exact name of registrant as specified in its charter) Delaware 94-3177549 (State or other jurisdiction of (I.R.S. Employer Incorporation or Organization) Identification No.) 2788 San Tomas Expressway Santa Clara, California 95051 (408) 486-2000 (Address, including zip code, and telephone number, including area code, of principal executive offices) Securities registered pursuant to Section 12(b) of the Act: Title of each class Name of each exchange on which registered Common Stock, $0.001 par value per share The Nasdaq Global Select Market Securities registered pursuant to Section 12(g) of the Act: None Indicate by check mark if the registrant is a well-known seasoned issuer, as defined in Rule 405 of the Securities Act. Yes ý No o Indicate by check mark if the registrant is not required to file reports pursuant to Section 13 or Section 15(d) of the Act. Yes o No ý Indicate by check mark whether the registrant (1) has filed all reports required to be filed by Section 13 or 15(d) of the Securities Exchange Act of 1934 during the preceding 12 months (or for such shorter period that the registrant was required to file such reports), and (2) has been subject to such filing requirements for the past 90 days. -

USCIS - H-1B Approved Petitioners Fis…
5/4/2010 USCIS - H-1B Approved Petitioners Fis… H-1B Approved Petitioners Fiscal Year 2009 The file below is a list of petitioners who received an approval in fiscal year 2009 (October 1, 2008 through September 30, 2009) of Form I-129, Petition for a Nonimmigrant Worker, requesting initial H- 1B status for the beneficiary, regardless of when the petition was filed with USCIS. Please note that approximately 3,000 initial H- 1B petitions are not accounted for on this list due to missing petitioner tax ID numbers. Related Files H-1B Approved Petitioners FY 2009 (1KB CSV) Last updated:01/22/2010 AILA InfoNet Doc. No. 10042060. (Posted 04/20/10) uscis.gov/…/menuitem.5af9bb95919f3… 1/1 5/4/2010 http://www.uscis.gov/USCIS/Resource… NUMBER OF H-1B PETITIONS APPROVED BY USCIS IN FY 2009 FOR INITIAL BENEFICIARIES, EMPLOYER,INITIAL BENEFICIARIES WIPRO LIMITED,"1,964" MICROSOFT CORP,"1,318" INTEL CORP,723 IBM INDIA PRIVATE LIMITED,695 PATNI AMERICAS INC,609 LARSEN & TOUBRO INFOTECH LIMITED,602 ERNST & YOUNG LLP,481 INFOSYS TECHNOLOGIES LIMITED,440 UST GLOBAL INC,344 DELOITTE CONSULTING LLP,328 QUALCOMM INCORPORATED,320 CISCO SYSTEMS INC,308 ACCENTURE TECHNOLOGY SOLUTIONS,287 KPMG LLP,287 ORACLE USA INC,272 POLARIS SOFTWARE LAB INDIA LTD,254 RITE AID CORPORATION,240 GOLDMAN SACHS & CO,236 DELOITTE & TOUCHE LLP,235 COGNIZANT TECH SOLUTIONS US CORP,233 MPHASIS CORPORATION,229 SATYAM COMPUTER SERVICES LIMITED,219 BLOOMBERG,217 MOTOROLA INC,213 GOOGLE INC,211 BALTIMORE CITY PUBLIC SCH SYSTEM,187 UNIVERSITY OF MARYLAND,185 UNIV OF MICHIGAN,183 YAHOO INC,183 -

December 12, 2012 the Honorable Lisa R. Barton Acting Secretary U.S. International Trade Commission 500 E Street, SW Washington
quinn emanuel trial lawyers | washington, dc 1299 Pennsylvania Avenue NW, Suite 825, Washington, District of Columbia 20004-2400 | TEL: (202) 538-8000 FAX: (202) 538-8100 WRITER'S DIRECT DIAL NO. (202) 538-8104 WRITER'S INTERNET ADDRESS [email protected] December 12, 2012 VIA ELECTRONIC FILING The Honorable Lisa R. Barton Acting Secretary U.S. International Trade Commission 500 E Street, SW Washington, DC 20436 Re: Certain Electronic Devices, Including Wireless Communication Devices, Portable Music and Data Processing Devices, and Tablet Computers; Inv. No. 337-TA-794 Dear Acting Secretary Barton: On behalf of Complainants Samsung Electronics Co., Ltd. and Samsung Telecommunications America, LLC, enclosed please find a public version of Samsung's Initial Submission in Response to Commission Notice of Review. Please contact me with any questions you may have regarding this filing. Respectfully submitted, /s/ S. Alex Lasher Counsel for Complainants Samsung Electronics Co., Ltd. and Samsung Telecommunications America, LLC quinn emanuel urquhart & sullivan, llp LOS ANGELES | 865 South Figueroa Street, 10th Floor, Los Angeles, California 90017-2543 | TEL (213) 443-3000 FAX (213) 443-3100 NEW YORK | 51 Madison Avenue, 22nd Floor, New York, New York 10010-1601 | TEL (212) 849-7000 FAX (212) 849-7100 SAN FRANCISCO | 50 California Street, 22nd Floor, San Francisco, California 94111-4788 | TEL (415) 875-6600 FAX (415) 875-6700 SILICON VALLEY | 555 Twin Dolphin Drive, 5th Floor, Redwood Shores, California 94065-2139 | TEL (650) 801-5000