2018 Embedded Systems Safety & Security Survey
Total Page:16
File Type:pdf, Size:1020Kb
Load more
Recommended publications
-
System Manual Pdm360smart Monitor CR1070 CR1071 Codesys® V2.3 Target V05 English
System Manual PDM360smart monitor CR1070 CR1071 CoDeSys® V2.3 Target V05 English 7390674_01_UK 2012-05-16 2012-05-16 7390674_01_UK ifm System Manual ecomatmobile PDM360smart (CR1070, CR1071) Target V05 2012-05-16 Contents Contents 1 About this manual 7 1.1 What do the symbols and formats mean? ......................................................................7 1.2 How is this manual structured?.......................................................................................8 2 Safety instructions 9 2.1 Important!........................................................................................................................9 2.2 What previous knowledge is required?.........................................................................10 3 System description 11 3.1 Information concerning the device................................................................................11 3.2 Information concerning the software.............................................................................11 3.3 PLC configuration .........................................................................................................12 4 Configurations 13 4.1 Set device parameters (setup)......................................................................................13 4.1.1 Start set-up ..............................................................................................................14 4.1.2 Show the current device settings.............................................................................15 4.1.3 Change -

Catalog of GA Control Systems
GA automation technology product catalog Contact information GEBHARDT Automation GmbH Thüngenfeld 3 D- 58256 Ennepetal Germany Tel.: +49 2333 7908 - 0 available during working hours, Mo to Fr, from 800 to 1700 (5 pm) central european time (CET, GMT+1). FAX: +49 2333 7908 - 24 Web: www.gebhardt-automation.de Support [email protected] Information [email protected] Date: 10/2012 GA catalog_Rev 02.01_2012-10-09 en.doc page 2 of 40 Contents GA BlueLine Systems ............................................................................................................4 Redundancy, fault tolerance and voting...............................................................................................5 Machinery Monitoring Systems............................................................................................................6 Monitoring Capabilities.........................................................................................................................7 GA TMR/10-S.......................................................................................................................................8 GA TMR SMART-S ..............................................................................................................................9 GA DUPLEX/7-S ................................................................................................................................10 GA DUPLEX SMART-S .....................................................................................................................11 -

SAFE TORQUE OFF a Guide to the Application of the Control Techniques Safe Torque Off Safety Function and Its Compliance with IEC 61800-5-2 SAFE TORQUE OFF
SAFE TORQUE OFF A guide to the application of the Control Techniques Safe Torque Off safety function and its compliance with IEC 61800-5-2 SAFE TORQUE OFF 1. Purpose of this guide This application guide gives general explanations, advice and guidance for the use of the Safe Torque Off (STO) feature which is provided in many of Control Techniques’ variable speed drive products. It supplements the specific product information given in the product Technical Guides. In the event of any discrepancy the product Technical Guide takes precedence. Most of the information is general in nature and applies to all models. Some model- specific information is given in Annex 1. Important warnings The design of safety-related systems requires specialist knowledge. To ensure that a complete control system is safe it is necessary for the whole system to be designed according to recognised safety principles. The use of individual sub-systems such as drives with Safe Torque Off functions, which are intended for safety- related applications, does not in itself ensure that the complete system is safe. The information given in this publication gives guidance on the application of Control Techniques Safe Torque Off, and also some general background material on the design of safety-related systems for machinery control. This publication is not intended to form a complete guide to the subject. Some more detailed references are given at the end of the guide. The information provided is believed to be correct and to reflect accepted practice at the time of writing. It is the responsibility of the designer of the end product or application to ensure that it is safe and in compliance with the relevant regulations. -

Components DISTRIBUTOR
The REGION’S LARGEST Essential Components DISTRIBUTOR www.cbtcompany.com Why essential components? Get the right components, at the right price, right when you need them. CBT offers you quality Allen-Bradley® essential components with 110 years of time-tested quality and durability. This catalog is your initial guide to selecting the best components to meet your specific appli- cation requirements. With Allen-Bradley®’s product portfolio, you will find the highest quality components at a fair price, an intuitive product selection, and fast delivery. Additionally, you will receive components that perform to your specifications, accompanied by the professional knowledge and support of CBT’s industry special- ists, you will receive components that perform to your specifications and make up the complete system you need. Smart devices include: Variable Frequency Servo Motor Condition Drives Drives Starters Monitoring Smart devices make data-driven productivity improvements using smart devices At its most basic level, The Connected Enterprise is about enabling the equipment, machinery, and devices in a manufacturing plant to provide real-time information that can help optimize plant operations. Rockwell Automation smart devices help you: • Increase productivity • Produce higher-quality products at lower costs • Support regulatory compliance • Identify and address worker-safety issues • Optimize supply chains Smart devices are the foundation of integrated control and information, providing seamless connectivity and the raw data for your Connected -

Standards Publications
IRISH STANDARDS PUBLISHED BASED ON CEN/CENELEC STANDARDS 1. I.S. 178:1973 Date published 28 SEPTEMBER 2005 Extruded Rigid PVC Corrugated Sheeting 2. I.S. EN 60835-1-2:1993 Date published 1 JUNE 2005 Methods of measurement for equipment used in digital microwave radio transmission systems -- Part 1: Measurements common to terrestrial radio-relay systems and satellite earth stations -- Section 2: Basic characteristics (IEC 60835-1-2:1992 (EQV)) 3. I.S. EN 160000:1993/A1:1996 Date published 1 JUNE 2005 Generic Specification: Modular electronic units 4. I.S. EN 61595-1:1999 Date published 1 JUNE 2005 Multichannel digital audio tape recorder (DATR), reel-to-reel system, for professional use -- Part 1: Format A (IEC 61595-1:1997 (EQV)) 5. I.S. EN 1990:2002+NA:2010 Date published 24 MARCH 2005 Eurocode - Basis of structural design (including Irish National Annex) 6. I.S. EN ISO 14122-4:2004 Date published 23 FEBRUARY 2005 Safety of machinery - Permanent means of access to machinery - Part 4: Fixed ladders (ISO 14122-4:2004) 7. I.S. EN 13877-1:2004 Date published 23 SEPTEMBER 2005 Concrete pavements - Part 1: Materials 8. I.S. EN 13877-2:2004 Date published 23 SEPTEMBER 2005 Concrete pavements - Part 2: Functional requirements for concrete pavements 9. I.S. EN 12843:2004 Date published 4 MARCH 2005 Precast concrete products - Masts and poles 10. I.S. EN 13225:2005 Date published 4 MARCH 2005 Precast concrete products - Linear structural elements 11. I.S. EN 13693:2004 Date published 4 MARCH 2005 Precast concrete products - Special roof elements 12. -

Safety Guide for the Americas
Safety Guide for the Americas Six steps to a safe machine Contents Six steps to a safe machine Six steps to a safe machine Contents Six steps to a safe machine Laws, directives, standards, liability g §-1 • Regulatory requirements g §-1 • European directives g §-4 • Obligations of the machine manufacturer g §-5 • Standards g §-9 § • International/European standards g §-11 • Nationally recognized testing labs g §-14 • Test bodies, insurance providers, and authorities g §-15 Risk assessment g 1-1 • The risk assessment process g 1-1 • Functions of the machine g 1-3 • Identification of tasks and hazards g 1-4 1 • Risk estimation and risk evaluation g 1-5 • Documentation g 1-6 Safe design g 2-3 • Mechanical design g 2-3 • Operating and maintenance concept g 2-4 • Electrical installation g 2-5 • Enclosure ratings g 2-8 • Lock-out/tag-out g 2-10 2 • Stop functions g 2-11 g • Electromagnetic compatibility (EMC) 2-12 2-1 • Fluid technology g 2-14 g g • Use in potentially explosive atmospheres 2-15 c Design of the safety function g 3-1 Technical protective measures • Development of the safety concept g 3-13 g • Selection of the protective devices g 3-18 a Definition of the safety functions 3-2 g b Determination of the required g 3-9 • Positioning and dimensioning of 3-44 safety level protective devices • Integration of protective devices into g 3-65 3 the control system Implementation of the safety functions • Product overview for safeguarding g 3-76 d Verification of the safety function g 3-79 e Validation of all safety functions g 3-95 Risk reduction -

Safety Bock I/O Module TBPN-L1-FDIO1-2IOL
Your Global Automation Partner TBPN-L1-FDIO1-2IOL Safety Block I/O Module Safety manual - Translation 2 Hans Turck GmbH & Co. KG | T +49 208 4952-0 | F +49 208 4952-264 | [email protected] | www.turck.com Table of Content 1 About this document 5 2 Scope 5 3 Safety Integrity Level/Performance Level/Category 5 4 Product description 6 4.1 Intended use 6 4.1.1 Foreseeable misuse 6 4.2 Device overview 6 4.3 Type plate 7 4.4 Switches and connectors 7 4.5 Block diagram 7 5 Safety function 8 5.1 Safe status 8 5.2 Fatal Error 8 6 Safety planning 8 6.1 Prerequisites 8 6.2 Reaction time 8 6.3 Safety characteristic data 9 7 Operating instructions 9 7.1 General 9 7.2 Before operation 10 7.2.1 Mounting 10 7.2.2 Connection 11 7.2.3 Address assignment 12 7.2.4 Configuring 12 7.3 Operation 13 7.3.1 Indication elements 13 7.3.2 Output error behavior 14 7.3.3 Decommissioning 14 8 Appendix: Wiring diagram 14 8.1 Ethernet 14 8.2 Power supply 14 8.3 Safety inputs 14 8.4 Safety in-/outputs 15 8.5 DXP 15 8.6 IO-Link 15 9 Appendix: Connection examples 16 9.1 Inputs 16 9.2 Outputs 16 V2.0 | 2018/01 3 10 Appendix: Designations and abbreviations 17 11 Appendix: Function tests 17 12 Appendix: Document history 17 13 Appendix: Technical data 18 14 Appendix: Declaration of Conformity 20 4 Hans Turck GmbH & Co. -
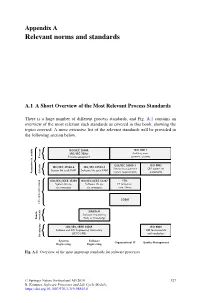
Relevant Norms and Standards
Appendix A Relevant norms and standards A.1 A Short Overview of the Most Relevant Process Standards There is a huge number of different process standards, and Fig. A.1 contains an overview of the most relevant such standards as covered in this book, showing the topics covered. A more extensive list of the relevant standards will be provided in the following section below. ISO/IEC 15504, ISO 19011 ISO/IEC 330xx Auditing man- agement systems Process Process assessment ISO/IEC 20000-1 ISO 9001 ISO/IEC 15504-6 ISO/IEC 15504-5 Service management QM system re- System life cycle PAM Software life cycle PAM Assessments, audits Criteria system requirements quirements ISO/IEC/IEEE 15288 ISO/IEC/IEEE 12207 ITIL System life cy- Software life cy- IT Infrastruc- cle processes cle processes ture Library COBIT Life cycle processes SWEBoK Software engineering Funda- Body of Knowledge mentals ISO/IEC/IEEE 24765 ISO 9000 Systems and SW Engineering Vocabulary QM fundamentals (SEVOCAB) and vocabulary Vocabulary Systems Software Organzational IT Quality Management Engineering Engineering Fig. A.1 Overview of the most important standards for software processes © Springer Nature Switzerland AG 2018 327 R. Kneuper, Software Processes and Life Cycle Models, https://doi.org/10.1007/978-3-319-98845-0 328 A Relevant norms and standards A.2 ISO and IEC Standards The International Organization for Standardization (ISO) is the main international standard-setting organisation, working with representatives from many national standard-setting organisations. Standards referring to electrical, electronic and re- lated technologies, including software, are often published jointly with its sister organisation, the International Electrotechnical Commission (IEC), but IEC also publishes a number of standards on their own. -

CIP Safety Protocol Training Session 0: Overview of Functional Safety and Safety Networks
CIP Safety Protocol Training Session 0: Overview of Functional Safety and Safety Networks Virtual Training Courses Before We Begin • Introductions • All attendees are automatically muted with no video connection as a default. • Please use the Q&A to ask questions, not the chat. We will address questions as they come in. • At the end if there is time, we will take questions verbally from the attendees. We will advise if and when there is time for you to “raise your hand” if you have a question. • Please complete the 4 question post session survey. The survey will launch when you close out of the webinar. PUB00303R6, CIP Safety Protocol Training, © 2021 ODVA 2 Overview of Functional Safety Standards Jim Grosskreuz Rockwell Automation Evolution of Factory Safety In early factories, workers were encouraged to act in unsafe ways to meet production goals. Industry 2.0 and 3.0 gave us increased focus improved safety by focusing on human factors and developing best practices. Industry 4.0 requires flexibility, ease of use, human-machine collaboration, and interoperability between vendors. PUB00303R6, CIP Safety Protocol Training, © 2021 ODVA 4 Machinery Builder & Operator Responsibilities • European Union – Machinery Directive • Prescriptive approach to machinery safety • Mandates risk assessments and safe machines • United States – OSHA • Less prescriptive approach to machinery safety • Introduces fines for violations – Litigious Culture • OEMs and System Integrators aren’t protected from litigation • Elsewhere – Mixed legal and cultural environments -

How to Design Safe Machine Control Systems – a Guideline to EN ISO 13849-1
How to design safe machine control systems – a guideline to EN ISO 13849-1 SP Technical Research Institute of Sweden Our work is concentrated on innovation and the development of value-adding technology. Using Johan Hedberg Sweden’s most extensive and advanced resources for technical evaluation, measurement technolo- Andreas Söderberg gy, research and development, we make an important contribution to the competitiveness and sus- Jan Tegehall tainable development of industry. Research is carried out in close conjunction with universities and institutes of technology, to the benefit of a customer base of about 10 000 organisations, ranging from start-up companies developing new technologies or new ideas to international groups. SP Technical Research Institute of Sweden SP Technical SP Technical Research Institute of Sweden Box 857, SE-501 15 Borås, SWEDEN Telephone: +46 10 516 50 00 SP Electronics Telefax: +46 33 13 55 02 SP REPORT 2011:81 E-mail: [email protected] ISBN 978-91-87017-14-8 www.sp.se ISSN 0284-5172 SP Electronics More information about publications published by SP: www.sp.se/publ SP REPORT 2011:81 How to design safe machine control systems – a guideline to EN ISO 13849-1 Johan Hedberg Andreas Söderberg Jan Tegehall 4 5 Abstract The aim of this report is to give guidance when applying EN ISO 13849-1:2008 in projects, both for companies developing subsystems and for companies that are developing complete machines. The report will give support in different areas in EN ISO 13849-1:2008 that are difficult to understand or parts that are described briefly. -

Introduction and Terminology for Functional Safety of Machines and Systems Reference Manual
Introduction 1 Regulations and standards 2 3 Safety Integrated Terms Attachment 4 Introduction and Terminology for Functional Safety of Machines and Systems Reference Manual 09/2020 E86060-T1813-A101-A6-7600 Legal information Warning notice system This manual contains notices you have to observe in order to ensure your personal safety, as well as to prevent damage to property. The notices referring to your personal safety are highlighted in the manual by a safety alert symbol, notices referring only to property damage have no safety alert symbol. These notices shown below are graded according to the degree of danger. DANGER indicates that death or severe personal injury will result if proper precautions are not taken. WARNING indicates that death or severe personal injury may result if proper precautions are not taken. CAUTION indicates that minor personal injury can result if proper precautions are not taken. NOTICE indicates that property damage can result if proper precautions are not taken. If more than one degree of danger is present, the warning notice representing the highest degree of danger will be used. A notice warning of injury to persons with a safety alert symbol may also include a warning relating to property damage. Qualified Personnel The product/system described in this documentation may be operated only by personnel qualified for the specific task in accordance with the relevant documentation, in particular its warning notices and safety instructions. Qualified personnel are those who, based on their training and experience, are capable of identifying risks and avoiding potential hazards when working with these products/systems. -

IEC 61784-3-3 ® Edition 2.0 2010-06 INTERNATIONAL STANDARD
This is a preview - click here to buy the full publication IEC 61784-3-3 ® Edition 2.0 2010-06 INTERNATIONAL STANDARD colour inside Industrial communication networks – Profiles – Part 3-3: Functional safety fieldbuses – Additional specifications for CPF 3 INTERNATIONAL ELECTROTECHNICAL COMMISSION PRICE CODE XF ICS 25.040.40; 35.100.05 ISBN 978-2-88910-978-4 ® Registered trademark of the International Electrotechnical Commission This is a preview - click here to buy the full publication – 2 – 61784-3-3 © IEC:2010(E) CONTENTS FOREWORD...........................................................................................................................8 0 Introduction .................................................................................................................... 10 0.1 General .................................................................................................................10 0.2 Patent declaration .................................................................................................12 1 Scope.............................................................................................................................13 2 Normative references .....................................................................................................13 3 Terms, definitions, symbols, abbreviated terms and conventions ....................................15 3.1 Terms and definitions ............................................................................................15 3.1.1 Common terms and definitions